Community IT’s Chief Technology Officer and security expert Matt Eshleman emphasizes that good security is a never-ending journey. Today’s best practices respond to today’s threats; tomorrow’s threats will require new and improved policies, user education, services, and so on.
2024 saw the emergence of a new threat that has required us to update our best practices around multi-factor authentication (MFA). That threat is called “Attacker in the Middle” (AiTM.) We started seeing compromises of Microsoft 365 user accounts in which the user had multi-factor authentication in place.
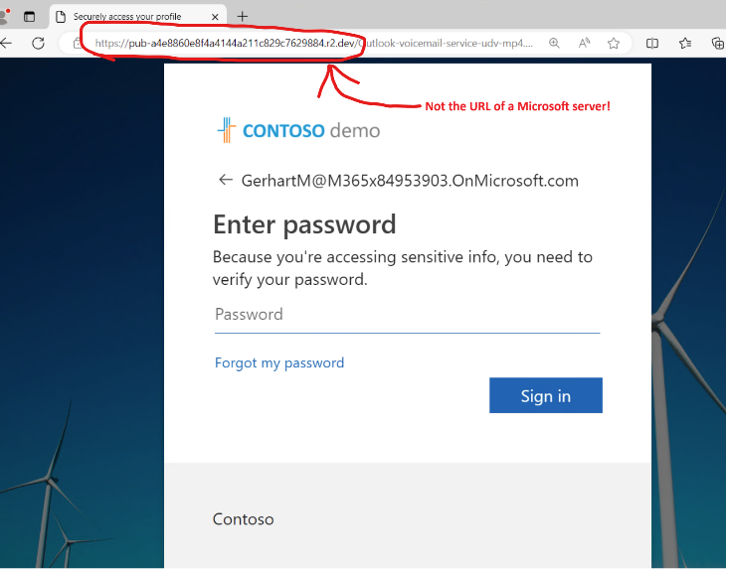
How were these accounts getting compromised? We discovered the user got a phishing email with a purported link to a Microsoft 365 document. Clicking on the link opened a browser window to a Microsoft 365 logon page. It didn’t just “look like” a Microsoft 365 logon page, it was a Microsoft 365 logon page. But the browser wasn’t pointing at a Microsoft server. The bad link took the user to a bad actor’s server, and that server passed traffic through to a real Microsoft server thereby retrieving an actual Microsoft 365 logon page. But when the user logged on, since their logon was actually coming from a bad actor’s server, the bad actor collected the “access token” issued by Microsoft. The bad actor could now do whatever they wanted with the compromised user account for the token’s life – including setting up backdoors with no expiration.
It didn’t matter that the user had number matching MFA. They were authenticating to a real Microsoft server with their MFA. The trick was that they didn’t realize they were authenticating for a bad actor’s server, not their own computer.
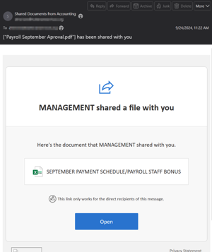
Because of this new thread, Community IT recommends “phish-resistant” MFA, which are forms of MFA that only work when the MFA method is physically proximate to the computer doing the authenticating.
By using phish-resistant MFA, AiTM is thwarted since the bad actor’s “in the middle” server is not in physical proximity to the user who is completing the MFA process. These forms of MFA include:
It’s not here yet, but Apple and Microsoft promised a MacOS equivalent to Windows Hello for Business in 2025.
It’s worth noting that the value of phish-resistant MFA for Microsoft 365 identity validation is compounded when organizations enable single-sign-on (SSO) so that other cloud apps are also protected by Microsoft 365’s identity validation.
Adding phish-resistant MFA, at least for executives and staff handling high-value data like HR, Finance, and IT, is a critical improvement in organizations’ never-ending IT security journeys.
We’ve found that many nonprofit organizations deal with more IT issues than they should have to. Resources are tight. Systems are unreliable, responses are too slow, and repairs are too expensive. Sometimes nonprofits don’t even realize how bad things are until something big breaks and their mission is derailed.
Our process is based on decades of exclusively serving nonprofits. Our technicians have certifications across all major platforms, and we constantly research and evaluate new solutions to ensure that you get cutting-edge solutions that are tailored to the needs of your organization.
We regularly present webinars at Community IT about nonprofit technology issues, and we work hard to keep our nonprofit technology community informed and engaged in best practices.
You may be interested in our free download Cybersecurity Readiness for Nonprofits Playbook to help set your nonprofit up for success in protecting your mission and your people.
If you have more questions about nonprofit IT, just ask.
Wednesday February 25th at 3pm Eastern join Matt Eshleman to learn how to use AI tools more securely at your nonprofit.
Fill out the form below to request a quote. We’ll be in touch shortly to discuss your needs and take the first step toward better nonprofit IT.