Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
In pt 1, Matt and Carolyn go over what a tabletop exercise is and how they fit into your cybersecurity planning for your nonprofit. In pt 2, Matt describes 3 scenarios specific to nonprofits that you can use, and reviews general lessons learned and best practices from his work with clients.
Community IT Chief Technology Officer and resident cybersecurity guru Matthew Eshleman explains how to carry out a cybersecurity tabletop exercise for your nonprofit and why this type of active testing is so valuable to your security planning.
Make regular cybersecurity tabletop exercises part of your nonprofit incident response plan using this guide.
If you haven’t had a cybersecurity incident yet, count yourself lucky. If you have, you probably encountered some questions you wish you had had the answers to before the incident began to unfold.
That’s where a cybersecurity tabletop exercise for nonprofit has enormous value. A cybersecurity tabletop exercise simulates a cybersecurity incident in a controlled environment so you can practice your response and discover weaknesses before they become damaging.
For example, a staff member alerts you that they clicked on a malicious link in an email and now their laptop is “acting funny.” Do you have a phone tree of the people you need to contact? What if someone important is on vacation, who do you contact then? What if everyone’s laptops are frozen, can you still access important contacts? What do you do next?
Cybersecurity tabletop exercises can be elaborate or simple, run by a consultant or run from within. It is surprising how many nonprofits that regularly review and evaluate their programming never use the same principles to evaluate their basic cybersecurity preparedness.
If you’ve never walked through a cybersecurity tabletop exercise at your nonprofit, you may be intimidated at the prospect or have trouble prioritizing it and carving out time on everyone’s calendar. In this webinar, Matt introduces some popular resources, describes common examples of tabletop exercises, and explains how to adapt this skill-building exercise for nonprofits.
Matt Eshleman has run through cybersecurity tabletop exercises with many nonprofit clients and guides you through best practices and first steps to get started. Don’t wait to introduce this valuable training tool to learn where you can strengthen your practices and better protect your organization in these challenging times.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT is proudly vendor-agnostic, and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community.

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 23 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at the Technology Association of Grantmakers, Jitasa, Nonprofit Learning Lab, NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert.
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, incident response, and cybersecurity tabletop exercises for nonprofits.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty-five years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She was happy to learn more about cybersecurity tabletop exercises for nonprofits with Matt Eshleman.
From the webinar and reddit/r/NonprofitITManagement/ after the webinar:
Q: What is the difference between staff training, like KnowBe4 training against phishing, and a Tabletop exercise?
Matt Eshleman: Staff training through KnowBe4 is an important part of the organization’s overall cybersecurity plan. It’s really focused on providing education for staff to detect, identify and report security threats that they may notice. The Tabletop exercise is a way for the entire executive team to test out the organization’s incident response plan.
Q: What are some good ways to impress upon less-tech-savvy staff the importance of MFA, if they have not had an incident yet?
Matt Eshleman: I think that these stats from Microsoft are impressive, “We’ve found that more than 99.9% of compromised accounts don’t have MFA”. https://learn.microsoft.com/en-us/partner-center/security/security-at-your-organization. If you want to protect your account and your organization’s data then taking basic steps like enforcing MFA is critical.
Q: If you are a nonprofit with a small staff but a lot of volunteers, how do you involve the volunteers using your IT in a training program or tabletop exercise, depending on the scenario? How do you suggest getting the leaders of the volunteer program to start requiring security training and processes?
Matt Eshleman: I think that this is related to the first question. Everyone that has an account to an organization’s IT system should be using MFA and also should be taking security awareness training! The tabletop exercise is something that the organization’s executive leadership needs to take ownership of since it is tied directly to the risk and financial liablity that the organization takes on.
Q: (from the exit survey) Should organizations document when minor incidents happen like when someone clicks on a link or a single email account gets compromised but it’s resolved right away?
Matt Eshleman: I think that you can define the level of severity for your own organization. It would be overkill to have a full incident response for every phishing message that comes into the organization. I do think that recording serious incidents like compromised accounts is important, as you can get a sense of which users or roles are targeted. For more serious cases where a compromised account wasn’t detected for several days, or led to data loss or financial loss, then a more detailed record should be kept.
Carolyn Woodard: Welcome everyone to this Community IT webinar, Cybersecurity Tabletop Exercise for Nonprofits with Matthew Eshleman, who is going to explain how to carry out a cybersecurity tabletop exercise for your nonprofit, and why this type of active testing is so valuable to your security planning. It doesn’t have to be expensive. You don’t have to hire consultants to do it, although you can if you want to. If you think that would be helpful to your organization to get it done.
We include this advice in all of our cybersecurity webinars all the time. I’m excited today to be able to share some of the how-to advice with you.
My name is Carolyn Woodard. I’m the Outreach Director for Community IT. I’ll be the moderator today. I’m very happy to hear from our cybersecurity expert, Matt.
But first, I’m going to go over our learning objectives. By the end of the session today, we hope that you will learn
what a tabletop exercise is,
learn why regularly doing tabletop exercises is a valuable and inexpensive way to strengthen your nonprofit emergency response plan,
walk through a sample tabletop exercise with us and
discuss the lessons learned and next steps for introducing or improving tabletop exercises at your nonprofit.
Matt, would you like to introduce yourself?
Matthew Eshleman: Thanks for the introduction, Carolyn. I’m really looking forward to this webinar today.
We talk a lot about various technology solutions in our different webinars and the content that we produce, and so I’m looking forward to today’s session and really being able to bring it all together.
As Carolyn mentioned, my name is Matt Eshleman. I’m the Chief Technology Officer here at Community IT, and I was reminded by a little calendar pop-up that I actually started as an intern at Community IT 25 years ago in the summer of 2000. It’s pretty exciting to continue to be here and be able to engage with so many great organizations and talk about cybersecurity.
Carolyn Woodard: Oh my gosh, Matt. Congratulations.
Before we begin, if you’re not familiar with us, with Community IT, a little bit more about us. We are a 100 percent employee-owned managed services provider. We provide outsourced IT support, and we work exclusively with nonprofit organizations.
Our mission is to help nonprofits accomplish their missions through the effective use of technology. We are big fans of what well-managed IT can do for your nonprofit. We serve nonprofits across the US.
We’ve been doing this for 25 years, over 25 years, but we’re coming up on our actual 25th year anniversary next year.
We are technology experts and are consistently given an MSP 501 recognition for being a top MSP, which is an honor we just received again in 2025. We’re checking the current list, but in the past, we have been the only MSP on the list serving nonprofits exclusively.
I want to remind everyone that for these presentations; Community IT is vendor agnostic. We only make recommendations to our clients, and we only do that based on their specific business needs. We never try to get a client into a product because we get an incentive or benefit from that.
We do consider ourselves a best of breed IT provider. It’s our job to know the landscape, the tools that are available, reputable and widely used, and we make recommendations on that basis for our clients based on their business needs, priorities and budget.
And we did get a ton of great questions at registration. We’re going to try and answer as many of them as we can, but anything we can’t get to, I’ll give Matt to give us some written thoughts, and I’ll append those to the transcript. You can check back after the webinar if we didn’t get to your question.
And a new thing this month, we just started a community over on Reddit. It’s r/nonprofitITmanagement. We’re going to answer some questions over there without naming names. And if you have questions and you’re on Reddit, you can join us over there. Matt’s going to pop on and off for the next couple of days and just answer any questions that come up in there.
And a little bit more about us, our mission, as I said, is to create value for the nonprofit sector through well-managed IT. We also identify four key values as employee owners that define our company, trust, knowledge, service, and balance.
We seek always to treat people with respect and fairness, to empower our staff, clients, and sector to understand and use technology effectively, to be helpful with our talents, and we recognize that the health of communities is vital to our well-being, and that work is only a part of our lives.
With that, we’re going to tell you, we’re a little bit curious how many of you have cyber liability insurance and have had to comply with requirements. I’m going to go ahead and launch that poll now, and I hope that you can see that.
The answers are, no, not yet. We don’t have cybersecurity yet. We’re not sure. It could not be part of your job description, so that’s fine. Yes, you have cybersecurity liability insurance and not applicable or other. Matt, can you see that?
Matthew Eshleman: Yes, I can. For the question of, do you have cyber liability insurance for your organization? I’ll jump ahead and say about 56 or almost 60 percent say yes, and then about 20 percent say no, not yet. Another 20 percent are not sure, and then a few folks were saying not applicable.
So that’s really good to see. I think that probably mirrors our experience in supporting our clients.
I will just say kind of anecdotally; we have seen the cyber liability insurance market change pretty dramatically. Six, seven years ago when this got started, cyber liability insurance was cheap, easy to obtain, and didn’t really require much other than filling out the application.
Then over the next couple of years, the costs certainly rose along with the requirements.
And I think now where we’re at is the cost is still increasing, although at smaller rates than before. But certainly, the number of requirements that are coming along with the cyber liability insurance have increased as well.
Carolyn Woodard: And I just want to mention, we did ask at registration how many people had had an incident in the last year, and it was a pretty sizable chunk of people registering. If you don’t have that cybersecurity liability insurance yet, you might want to think about it. And some funders, I think, also require it. It’s something that we have a lot of resources on our website about that insurance. So that’s something to look into.
And then we have a second poll, which is, have you already done a tabletop exercise? The answers are no, not yet, not sure. Yes, it went great. Yes, but it could have gone better and not applicable or other.
Again, we’ve got some pretty good response. And I don’t know if this is going to surprise you, Matt, but I’m going to go ahead and share. Can you see that?
Matthew Eshleman: Yes. So, yeah, I mean, maybe not surprising, but yeah, the vast majority of respondents, so 80% said no, not yet. And then, you know, 12% here had said yes, and some for another with just 5% saying yes, it went great.
If you’re in that category of yes, it went great. I’d really love to be able to hear what, you know, what made it go well as we go along, and as Carolyn said, we should have time for questions and some more conversation towards the end of our session today. So that’s great.
Carolyn Woodard: All right, sounds great. Thank you, everyone, for participating. That really helps us.
And now I think, Matt, you’re going to talk a little bit more just kind of a baseline framework grounding on how we look at cybersecurity and where this kind of exercise would fall in this rubric that we use.
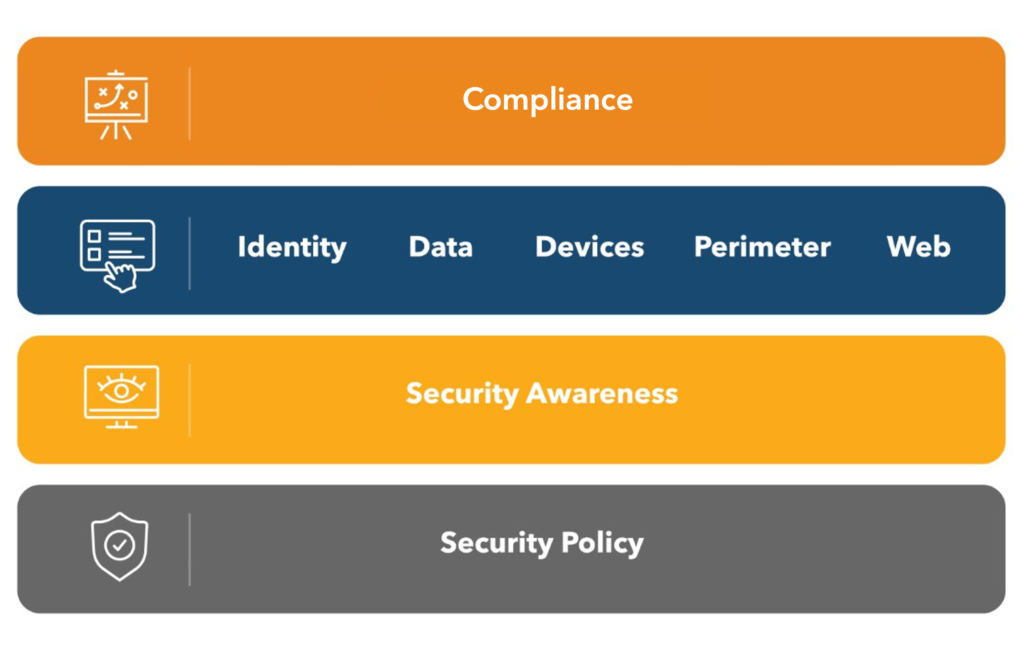
Matthew Eshleman: Yeah, for sure. This is a graphic that that I use quite often just to help think through how we’re organizing and aligning around cybersecurity.
Things like those foundational concepts such as policy really provide that foundational guidance for the technical solutions that we’re building on top.
You’ll notice we don’t jump straight from policy into technology but really have that layer of security awareness training as a key element. As most of the attacks that we see in this kind of small to mid-sized nonprofit space that we support are initiated by people clicking on something that they shouldn’t have, or by getting tricked into updating payment information, or buying gift cards, or updating information for somebody that’s obfuscating their identity.
What we’re going to be doing today is a special type of training, maybe an incident response where we’re going to practice ahead of time, what you and your staff would do in the event of that tech emergency, whether someone knows they clicked on the wrong thing, or somebody on your staff sees something suspicious, or maybe your IT team has identified a breach.
In the rest of the graphic there is the blue line is really the range of technical solutions that we would add in to provide meaningful protection. But again, technology in and of itself isn’t going to be a perfect solution without that policy and staff training element as well.
At the very top, we have this compliance layer, which represents some external requirements that you have, either from external funders or other board sources that say, hey, we really need to apply these policies or these procedures as a result of some external requirements.
At the end of the day, the IT department can help support that compliance, but it’s really an exercise that the entire staff needs to be on board with the policy implementation of those controls. We’ll spend the most of our time today talking about how to actually play those things out.
Carolyn Woodard: And I did put the link to download that playbook in the chat. It’ll be in the transcript as well. And we have some other resources around that playbook on our website, so go ahead and look for those.
But Matt, can you set the stage for us? Why are nonprofits hearing about and interested in tabletop exercises at this moment?
Matthew Eshleman: Yeah, so I think it’s a great question. I’m really excited that we’re actually at this point and being able to talk about doing a tabletop exercise. We’ve been talking about cybersecurity for quite a while. We have tended to be focused on specific technologies or specific solutions or specific policies, right? We talk about an IT acceptable use policy. We talk about the importance of MFA and why it’s so critical.
We talk about security awareness training. We’ve done a lot talking about why we’re doing all of these specific elements.
And I think now we’re really at a place where a lot of organizations have made significant investments and improvements in their cybersecurity controls. With all of these pieces in place, now organizations say, hey, well, we’ve already done the basics. Maybe we followed that playbook from you all. We’ve done all these pieces.
How do we need to test it to make sure that the things that we thought were in place and the controls that we think are working are in fact doing the things that we expect them to do?
I think organizations have invested a lot over time, and I think it’s now working. And it’s listed on here. If you’ve got the basics in place, now it’s an excellent time to put your plan to the test. Is it in fact doing all the things that you expect it to do?
Being able to test it can help identify those gaps and maybe surface some weaknesses in your existing policy or controls and really help to identify, okay, so what’s the next thing that we need to take?
Whenever we do have a security incident, we’re really ready to respond and do so in an efficient way.
Carolyn Woodard: And I did put in a link to how to create that incident response plan if you don’t have one. And it used to be just for like, oh, those sprinklers went off in our office and the whole thing got flooded and we had to figure out where our laptops were and all of that sort of thing. And now, a large part of it is, if there’s a cybersecurity incident, how would you respond?
So Matt, I think you’re going to tell us a little bit more about what a tabletop exercise is.
Matthew Eshleman: Yeah, maybe we should have put this at the beginning of the slide before we asked everybody if they did one.
The way that I’m choosing to define a tabletop exercise, really it is a way to practice the implementation of your organization’s incident response policy.
The incident response policy defines the different systems that your organization has.
It talks about if something happens, how are we going to respond as an organization? What is the IT department’s response? Is there a communications department response? Do we have a legal duty to report things?
The incident response plan itself can be pretty detailed. And the tabletop exercise is really an opportunity to test that out and to put it through its paces to make sure that it holds up.
It makes sense to do it using some realistic scenarios. I’m sure as soon as I mentioned testing out your incident response plan, maybe something horrible popped into your mind of like, oh my gosh, our website goes down or our executive director’s account gets compromised. Those are all real scenarios that happen to organizations just like yours.
It’s a chance to test how would we respond or react in those situations and does our plan and our procedure actually make sense and give us the level of comfort and control that we really need.
I think the big thing is that the incident or the tabletop exercise itself is not really something that is just done by the IT department in a vacuum.
It really should, in kind of its best ways, be a dedicated exercise that involves everybody who’s identified in the incident response document, in a room together, either in person or virtually kind of working together and working through the scenario that’s identified.
Carolyn Woodard: You remember we had someone tell us about the phone tree, like who you’re supposed to call next. Unfortunately, their client, when they had the response, everything was frozen. If they had done an incident response plan tabletop exercise, they would have realized they needed a paper copy so that they could call the next person on the list. But as it was, they were running around like, who are we supposed to call? That was all on the laptop that’s now frozen. Good to know.
In your tabletop exercises, I think these are kind of key pieces of advice that you would give to an organization.
Matthew Eshleman: Yeah, for sure. I think the top bullet point here really is important.
Planning is the key to success. Planning a tabletop exercise does not just mean throwing a calendar invite on a bunch of people’s calendars a week from now and expecting them to show up and be ready to go.
I think whoever is leading or organizing the tabletop exercise should come planned with some of the scenarios that we’re talking about in the next couple of slides.
I think it’s helpful to identify what are the goals of this process. What do we expect to be able to say at the end of our time together?
Then also making sure that who’s available. I just talked about; a tabletop exercise is not just something for the IT department to initiate and do on their own. Often the best ones that I’ve been a part of are actually even led by external legal counsel. They involve the executive leadership of the organization. It’s a department, it’s a director level meeting. It is a high-level meeting.
As a result, it can be a very expensive meeting if you think about it, because of all of the senior staff time that is required to be there, to be engaged and to participate for a sustained amount of time.
With all of that investment, we want to make sure we’ve got clear goals. We have all the engaged parties are able to participate, and we can have a clear sense of what we expect to get out of this process together.
Carolyn Woodard: And I think we would say, don’t try to squish it into 15 minutes of a staff meeting, like an all-staff meeting. You really need to have some dedicated time to it. It may take longer than an hour. It may take a couple of hours to really work through everything you need to talk about.
Getting that time on those people’s calendars can be difficult. But if it’s a small organization, it may be, in addition to an all staff meeting, you just set aside a couple of hours for everyone on staff, like all six of you to get together and just talk about what’s your response plan, who’s responsible for what, and how do you cover it if that person’s on vacation, that sort of thing.
So next we’re going to do this thought question. If you could put in the chat your answer to this, is your nonprofit open to the idea of doing a tabletop exercise? I know we had several of you in the previous poll who say you haven’t done one yet.
We just want to kind of take a little temperature of is that because people are not open to it or you haven’t found the time, that sort of thing, or you don’t know how. So hopefully this webinar will help you with that.
And if you can also put in the chat, like, what are the barriers to getting started?
I just mentioned a couple like time, organization, making it a priority. We’d love to hear from you as we go on and talk in the next couple of slides. If you want to put in to chat, is your nonprofit open to the idea of doing it, and what are your barriers to getting started? Because that’ll help us answer you as well.
And someone’s already jumped in with time, getting the right people in the room, right? That’s something. Having a small organization, just two people makes it seem not as pressing, maybe just the two of you are going to cover it, whatever happens.
So please go ahead and keep putting those in chat. We’re going to move on to the next slide, which I think, Matt, you’re going to talk a little bit about really defining those goals a little bit more.
Matthew Eshleman: I think the number one goal of the tabletop exercise is to test that incident response plan.
As Carolyn provided, we have some resources to help put that together. But essentially, the incident response plan defines for your organization who is responsible for responding when you think there may have been a security incident occurs.
There is some variability ranging from maybe a single account compromise, maybe an intern, that’s going to obviously have a very different response associated with it than maybe if the executive director’s account is compromised, or maybe your director of finance.
Often the incident response plans will have a couple of different scenarios outlines. In this case, here’s what we do. In this case, here’s what we do. And so, it’s a way to test that out.
Another goal really is to use it as a roadmap to ensure that it works, right? Are there weaknesses in your incident response plan? Does it rely entirely upon one person of your organization to manage, coordinate, execute the response? Does it maybe call for vendors? Does it have a relationship with you no longer?
These documents get created, they tend to get put on a shelf, and so the incident response, this tabletop exercise is really an opportunity to take it off the shelf, review it, walk through it, and see if what you define for yourself really still holds up.
It’s also an opportunity to include those stakeholders to build buy-in and identify unknown gaps. Community IT is a managed service provider. We have our organization’s incident response plan. We know what we’re going to do whenever somebody (a client) tells us they have a security issue, but the organization itself needs to know. We’re just one part of the bigger puzzle for an organization.
The incident response plan is not just an IT initiative, there could be communications, executive leadership, maybe the board has a role.
Everybody who has a role defined should participate as part of the tabletop exercise to make sure that that coordination and communication is really available there.
An example: I know as an incident response or tabletop exercise, we were a part of, we had our primary contact.
But then in their plan, they had a couple of other people identified as having key roles.
But we didn’t really have a strong connection with those folks. As an outcome of the tabletop exercise, we got some additional contact information, had additional relationships so that we can respond appropriately to the people that have the response roles at our clients.
Carolyn Woodard: There’s always going to be something in a response that’s not going to go right. There are so many things moving and it’s different from anything that you’ve had to respond to before, each time. It’s hard to find out in that moment, this isn’t the right contact person for that organization or whatever it is.
And I was also just thinking when we were preparing for this, nonprofits usually spend a lot of time on their programs evaluating what went right, what didn’t go right, what could we do differently next time. There’s a lot of program evaluation going on, even informally, as we’re thinking about our jobs.
And so maybe one way to think about this is to take that same mindset, but just apply it to this cybersecurity incident response plan, right? How could you do it better testing it, probing it, you know, running through it to see where there’s some weaknesses is a good way to look at it.
Carolyn Woodard: Now I think we’re going to go on and the moment you’ve all been waiting for, actually talk about how you would do it.
Unfortunately, we cannot do breakout rooms today in this webinar and actually have you sit and do it.
And also, that probably wouldn’t be something that you would do with strangers from other organizations. It’s something really that within your organization, you need to identify those stakeholders, identify the key players and have them all in the room together.
I tried to find some scenarios available online if you don’t know where to start. And it’s really hard to find them for nonprofits specifically. The scenarios that are out there just don’t seem to really fit a lot of what we’re seeing and what our organizations do.
So, we prepared a few, they’re here, or you can create your own. It’s actually probably a good thing for nonprofit organizations to be mindful and surface things that they’re really concerned about, and you can create a scenario out of that.
If you’ve got something that keeps you up at night or you’re wondering about, what if I clicked on the wrong thing in that e-mail? Do that as a scenario and find out if your response plan can handle it.
And you could get people from other departments involved, the stakeholders thinking about like the things that they worry about.
Being creative can help get your conversation started.
Usually this would be around a tabletop. You would have a meeting room or a Zoom call with the stakeholders and representatives. You give them a scenario and a time limit and have them try to respond.
So Matt, do you want to read through some of these scenarios?
Matthew Eshleman: We have a couple of scenarios that we’ve identified that certainly give me heart palpitations. And as Carolyn said, this is a good opportunity to really test out those scenarios, right? The proverbial question like what keeps you up at night? Those can be great places to start to say, okay, well, what if this happens? How do we go ahead and respond?
This is under the heading of cybersecurity. We have a scenario here, some of which may have been initiated by a malicious external actor, and some may be done accidentally. The first one is files in the HR library are unavailable.
In that scenario, what does that mean for your organization? Is this kind of something that you have defined in your incident response plan? How severe is it? What type of response does this dictate?
Loss of access to information; you can fill in the blanks. This could be files in the HR library are unavailable. Why is that? Maybe the permissions are just missing, or maybe they have been deleted, or maybe it’s been encrypted.
I think for the tabletop exercise, it’s actually good to start with a relatively basic top-level description, and it provides the opportunity to discuss some of the different scenarios that may be contributed to this case.
In that discovery, you may have different responses. A data unavailability issue. That’s one scenario to talk through.
Another scenario, and we can see this sometimes, you’re contacted by a threat actor who claims to have accessed and downloaded a copy of your CRM database.
So obviously, that raises all kinds of red flags, ranging from how do we confirm that is in fact true?
Maybe we need to verify the type of information that they claim to have. If we’ve done a good system inventory, we would know what kind of data is in there. Do we have any personally identifiable information? Are we keeping social security numbers as part of our CRM, or driver’s license, or banking information?
You can kind of build it out to your unique scenario to decide how big of a deal is this?
This is maybe a scenario where if this is in fact confirmed, you actually need to contact and provide disclosure to all of those constituents that, hey, we lost your data and here’s what we’re going to do as part of that response.
Maybe you have a reporting requirement in your jurisdiction. So again, loss of data, right? We know this is out there. It happens.
And then a third scenario that is probably not that in common, but maybe a compromised account at your organization. And that account is now sending phishing emails out to everybody on their contact list.
We have a known threat actor, has taken over an account that’s trusted, and now that account is sending well-crafted messages to everyone in their contact list. And that number is in the thousands.
The incident response plan ideally would have some guidance in terms of what those initial steps would be for various levels of severity of potential cybersecurity incidents.
Carolyn Woodard: I know when we do these as an actual exercise, you usually add a twist, right?
Matthew Eshleman: Yeah. It’s never as easy as it first seems. I think adding the twist, and I think this goes to the preparation for these scenarios and thinking through what are some likely or maybe extra challenging scenarios to highlight.
So maybe in your first scenario is, oh, we lost our HR data, that’s no problem. Here’s our backup and disaster recovery plan. We’re going to follow that.
It’s all detailed in our incident response plan. But hey, what if the twist is, well, wait, it’s actually not just the HR files that are missing, but we actually realize our whole policy library is now gone or inaccessible.
And that’s where the incident response document was. Does this document exist anywhere else, right? Do we even know who to contact because we had our insurance provider on there and we needed to reach out, but now we actually don’t know what that number is because we don’t talk to them that much.
Adding a little bit of a twist can help to surface weaknesses in a plan or identify areas that maybe aren’t fully complete.
You know, kind of in that second scenario where we said that we lost the CRM data, or the CRM information is no longer available. It turns out the director of the development department that manages that platform is away on vacation. Who has the backup, you know, what if other directors are unavailable? Is there any redundancy or resiliency in the plan?
Or does your incident response plan really hinge upon maybe one key person? And if that person is unavailable, how does communication flow? Are there other people that are aware of what needs to happen next?
Are there other people in the organization that have the relationships and connections with maybe external partners that would be a resource to help in this case?
Then the third scenario here is that, well, it turns out that it’s not just a compromised account for our executive director, but we’re locked out organizationally.
It turns out the executive director was also a global admin, so they have permissions to the whole tenant, and the hacker just locked everybody out of the whole Office 365 environment and so now, instead of relying on maybe Teams messaging to chat and coordinate a response, we’re locked out.
So as an organization, do you have the ability to contact staff through other means? Is that something that you have access to outside of your primary system?
A couple of these little twists can help identify weaknesses in the plan and maybe areas for improvement or revision.
Carolyn Woodard: I think also I’ve seen it where that time limit you give people; you’ve only got 10 minutes to respond now that we’ve added this twist. You give people a little bit of an urgency in playing the game or doing this response, trying to work through, strategize what you’re going to do and how you’re going to do it. And that gives people just that extra like, oh, now what do we do? And I think it can help.
Matthew Eshleman: Oftentimes, initial scenarios are probably things you thought about before, that probably has a clear next step that you’ve also already thought about. Adding in a little bit of a twist or additional bump in the road can help jar some of those static assumptions aside and give you maybe a new perspective on how you’d respond, especially if maybe you were the person that wrote the Incident Response Plan, and you were thinking about things in one way. Having something come out of the blue to really challenge those starting assumptions can be helpful in just making sure you’ve got a more complete view of the overall situation.
Carolyn Woodard: Especially finding those single points of failure, where there really is one person that you’re expecting to be able to do it all, and that person can never go on vacation then.
We’re going to hit a few of the lessons learned. If you want to share with each other, if you’re new to this idea, what is it making you think of?
Are you already taking away maybe some lessons that you’re newly thinking about?
Matt, you’re going to tell us about some common learnings. There’s no one size that fits all. The value of the tabletop exercise is to your organization, your specific risks, your staff and how they would respond, your response time, your response plan, your insurance broker, who you’re going to, who’s on your phone lists, all of those different things.
We do these types of exercises with our clients a lot. So Matt, you were going to tell us some of the things that come up a lot when we did these exercises.
Matthew Eshleman: Having gone through these a number of times, I think some of the common weaknesses that we see in an organization’s incident response plan is that often, it’s too narrow in scope. They think of IT issues as just maybe a few well-defined scenarios, a compromised account or if you did a ransomware. I think the full breadth of the organization’s data is often not included in these incident response plans, I think particularly if they are rooted in the IT department doing it all.
Make sure that the incident response plan itself encompasses really responding to all of the organization’s information systems, not just an IT email files, that kind of thing. Making sure that the incident response plan covers a variety of scenarios and really the full breadth of the organization’s data.
As Carolyn kind of connected the dots there, often the incident response plans have lots of single points of failure. There is one contact, the office manager or the operations director, they do everything.
And so, if that’s the case, and they’re on vacation or they’re out of the office or they’re not reachable for whatever reason, if the entire incident response plan really hinges on one person who has the relationship with the internal IT department or the vendor, if you use a managed services provider or the insurance provider. Yeah, so lots of cases.
For organizations that are small to mid-size, it is hard to build in that redundancy and resiliency in a plan.
But again, think through – that could be your twist. The one person that is really responsible for everything, yeah, they’re unavailable. What do you do next? And maybe some time framing around that is an important thing to include.
Again, maybe the plan relies too heavily on outside partners. As I mentioned it before, Community IT, as a Managed Services Provider, we have an incident response role for an organization, but we are not our client’s incident response plan.
We’re a part of it. We don’t do it all. Organizations need to have the different roles that they need to have filled right in terms of communication, maybe a cyber liability insurance provider has a role, maybe a data team has a role, maybe the board or oversight has a role.
And the answer can still be, well, we’re going to contact our MSP partner and they’re going to do the technical remediation. And then our communications team is going to handle the public messaging. And here’s how we’re going to keep our board up to date, and here’s how we’re going to keep the cyber liability insurance provider up to date.
All of those different elements should be included as part of the incident response plan. Doesn’t have to be hundreds of pages of documents, but it should be a pretty clear and concise way of engaging with all the different roles that are required whenever you’re responding to a security incident.
And then again, some challenges with those plans.
The roles aren’t clearly defined, or maybe that the person whose name is associated with the task doesn’t really understand or maybe can’t fulfill those requirements. And so that can be another challenge. If you find your name on an incident response plan document for your org, hopefully that’s not a surprise to you.
And so that can just be going through this tabletop exercise and say, hey, all right, Carolyn, if this happens, here’s your responsibility. And you can say, oh, I knew that, that was really clear. I’m well prepared. Or, wait a minute, I didn’t realize I was supposed to do that. It could be an opportunity for that conversation to occur.
Carolyn Woodard: I love that. I love that in the course of doing the exercise, you can be strengthening that response plan. That’s really good to think about it.
We’re going to talk a little bit about some of the common incident flow that we see when we have incidents that we have to respond to at clients. And again, just say, this is kind of the generic overview of what the flow might look like generally. And we have a flow chart on the next slide showing it as well.
But when we respond to incidents, Matt, do you want to say a little bit about how it usually tends to happen?
Matthew Eshleman: We’ve got the incident identified. That could be something, again, a person at the organization noticed like, oh, I’m getting all these bounce backs. People ask me why I’m sending them this message, or maybe you have some proactive security tools that have identified and maybe block that, so we know something has happened that really shouldn’t.
Then there’s often an internal scoping or boundary of, here’s the scope of the issue that we’re aware of right now.
The next step often is to contact the IT partner, if that’s you, as part of an internal IT resource, or maybe you have an external IT partner to help, I think, confirm or affirm whatever the project scope is.
For us at Community IT, we’re able to go in, and identify the scope. Is it, yeah, it turns out it’s just this one person’s email that was compromised. We can identify that it was compromised 30 minutes ago. We know they sent seven messages. They didn’t log in anything else, right?
And we can say, all right, this is self-contained and we’re going to reset the credentials, reset the MFA, evict the bad guy, make sure everything’s locked down, reach out to the people that were emailed and say, hey, this was sent in error, please don’t open it, right?
That could be the extent of it.
But in the case of, maybe your IT partner gets involved, maybe you’re an organization that has, for example, a HIPAA compliance requirement and the data involves disclosure of a privilege or personally identifiable information. Well, now we have a whole different scenario on our hands.
And so then at that point, after doing that initial analysis, we say, this account was compromised. The compromised account access, person identifiable information. This looks like a data breach.
We need to bring in our legal counsel to help scope this and handle a more comprehensive response that’s going to involve cyber liability insurance, maybe an incident response vendor.
It is helpful, especially if you’re in organizations that have more sophisticated compliance requirements, to understand where those levels are. Because it can be pretty significant gap between walking out a compromised account to maybe having the disclosure of person identifiable information.
Carolyn Woodard: Something that I didn’t know until we did that webinar about cyber insurance, cyber liability insurance is that often, your cyber liability insurance broker is one of your resources, and they see this throughout their clients, and they also know the next steps that you need to take, how you assess, how serious it is, when you have to alert authorities, all those steps, and they have resources that are available to you. It’s part of what your insurance pays for, so make sure that you use them.
We have a few additional resources, Matt, you were going to talk about. We covered a lot very quickly today. If you do want to pursue doing this exercise with your organization but you have some more questions, there’s some additional resources. Matt, you were going to talk about this.
Matthew Eshleman: I think just to maybe put a final point on some of those external resources. Again, another, I would say, common lesson learned is that organizations, maybe they have the cyber liability insurance piece, but maybe they don’t have an incident response retainer, or if something really, really bad happens, the capacity to respond to that incident may exceed what your in-house IT team or even your IT partner can do, right?
Community IT, we’re a great managed services provider. We can do really good first-order response, but we can’t do everything. If there’s a really serious breach, our clients would work with their cyber liability insurance vendor to get another incident response in place.
And depending on the contracting at your organization, that may be something that you identify as our contracting process takes six weeks to complete. If something really bad happened, we want to have some of those business relationships in place ahead of time. And so that whenever we have an incident, we have a clear process, we already have the business relationships in place that will help us handle that and respond fully.
External Legal Counsel can be a great resource and often have extensive experience in this area. Some of the best tabletop exercises that I’ve been a part of, I did not lead but was a participant that was led by Legal Counsel because as something that really involves the entire executive leadership of the company, they have that external, that gravitas that can really be helpful in these scenarios.
Taking advantage of your Cyberliability Insurance Providers, they may provide this as a service or they may have, again, some resources and toolkits available to help you get started to make that a really meaningful and productive time together.
There are other resources, right? CISA has a whole bunch of resources. It’s pretty big, it’s pretty broad, but again, can be good to help cherry pick some of their content to help design a scenario on your own.
And then if you’re on the IT side, Backdoors and Breaches is a kind of a gamification version of this, and that can be a fun way for IT teams to kind of play through different scenarios. There’s kind of an online card game; there’s physical decks that can be used. That can help you think of these different scenarios, think of how your organization would kind of respond, or particularly if you’re an IT team, how your IT team would respond, think about how they include some of the randomness, right? There’s kind of a dice roll as part of it to be like, oh, like, we’re going to go to backup. You can roll the dice. Oh, our backups aren’t available, or oh, we’re going to go to the logs to see what happened. Oh, you have log files, now you can investigate.
Backdoors and Breaches is probably more focused on the IT team specifically but can be a good way to just kind of think through different scenarios, making sure that you’ve got all of those pieces in place to be able to respond effectively. So again, a great resource to use.
Carolyn Woodard: Susan had put in the chat a resource that they did a gamification, the Inside Man New Recruits game. I mentioned that as well. She said it was a great resource.
And if you remember back to that graphic that we showed at the beginning about how we think about cybersecurity, that security awareness training for staff is a really big, important pillar of that, layer of that.
They are the other half of the incident response plan, right? Or the initial part is, do your staff recognize that something weird is happening? Or if they get an email and they do click on it, and they, sometimes you instantly are like, oh, I shouldn’t have clicked on that. Do they know how to tell? Because, right, that’s going to be the incident, the real-life incident, that then is going to start everything in motion with your response plan.
It is kind of a related piece of it, of making sure that staff have that training.
I want to go on and let people know what our cybersecurity offerings are. You can find more information on our cybersecurity services at communityit.com/cybersecurity.
You can find all of our previous webinars, our downloads, our articles on cybersecurity on our site, including information on insurance controls, the downloadable cybersecurity playbook that we mentioned, resources on training your staff.
Right now, I want to make sure that we have some time for Matt to answer a couple of questions. But if you don’t get to your question or you just have more, or more specific questions that aren’t appropriate really in a webinar, you want to talk to him specifically, you can schedule a free assessment with him.
And like I said, we just started our Reddit Community, so you can go over there and ask your question too. But Matt, you want to tell us a little bit about this slide and what the sort of things that we do for clients are.
Matthew Eshleman: I’m glad you highlighted a lot of our online resources. I think a lot of the content that we put out really is rooted in what we’re sharing with our clients. I definitely-
Carolyn Woodard: It’s free. It’s free on our site.
Matthew Eshleman: Yes. We do have some free resources to get started.
If you need to assess your organization’s cybersecurity readiness, we do have a free online security survey that uses the NIST framework. That can be a great place to get started for organizations that are really maybe new to developing some of these cybersecurity practices.
We also do much more in-depth cybersecurity assessments to help build out some of those roadmaps and identify maybe security controls to put in place.
Community IT has also built out a full range of managed cybersecurity services that are aligned with a lot of the controls that we see at a foundational level, complying with the cyber liability insurance applications. That’s a consistent set of recommendations that those entities are making. We’ve tried to align our services to help organizations be able to check the yes box for a lot of those things. Beyond just being able to check the box, they do make a real difference to the security that organizations are able to protect their staff and their organization data.
Then we also have a pretty well-defined and effective managed cybersecurity training for staff. I did recognize that Insider Man, that’s I think a KnowBe4 specific training. That’s a great way to engage staff on some different cybersecurity topics.
I would say that’s part of your overall security plan is to have training that engages, and then hopefully work towards being able to bring all those pieces together and finally, run through some scenarios to test it out, to make sure that everybody is aware of and is able to respond to an incident whenever it does occur.
Carolyn Woodard: I wanted to jump in and mention too that there’s a new piece of nonprofit auditing what you may have heard of, the SAS 145, which is new guidelines on the annual audit that your nonprofit needs to go through for financial reasons.
Starting this year, actually, I think it started last year, but this is the first year they’re going to actually check on it, is they have to also assess your IT risk, because we know that that’s a financial risk. If you click on the wrong thing, wire the money to the wrong place, or have to respond to an incident and you have to use that insurance, those are all financial risks. You may be getting questions around that as well. Your tabletop exercise could help you say, we have an incident response plan, and it is robust. We know what we’re doing if something happens. That’s always something that you can do.
One question was how to describe a tabletop exercise for a small nonprofit or a nonprofit that has never done one and doesn’t really know what it is. I feel like we’ve hit that pretty strongly, but I wondered, Matt, if you could talk a little bit more about ways to talk about it that don’t scare people and that help them overcome those barriers of having the time, making it a priority.
What do you say to clients when they’re trying to get this going?
Matthew Eshleman: Yeah, I think time together as an organization, especially executive leadership, is really precious. We’re all really busy and doing the work to support the mission of the organization.
I think some ways to frame this is in that proactive way of making sure that we have our bases covered, so that whenever that security incident does happen, and we know it’s not a question of if it’s going to happen, but when, that we’re able to be proactive and respond as opposed to really be reactive and scrambling.
I think at its highest level, appealing to the proactive and planning nature of organizations can be helpful.
Sometimes organizations need to be maybe shocked or jarred into action. It’s also okay to use current new scenarios. I just saw in the news that there was a Minnesota Housing Nonprofit that basically had to liquidate because they had wire fraud that took all $800,000 of their organizational assets and got disappeared.
It’s also helpful maybe to point to other organizations, hey, this organization had this happened to them, like how would we respond? What would we do?
Maybe some organizations respond a little bit more to the stick approach. Then then kind of the planning approach, but, you know, so I think framing it in a way that says, hey, like we really need to take this step because we care about our organization. We care about the staff that work here. We care about the people that we work with. And we just want to make sure that we’re as protected as we can be using the resources that we have available as a way to address that.
Carolyn Woodard: I was talking with Jenny Huftalen, who also deals with a lot of clients, and she used the metaphor that it’s a lot more expensive to go to the ER than just go see your doctor every year. I think that that might be another way to think about is, you’re going to save money compared to if you had to respond to an incident.
I want to go back over our learning objectives and whether we covered everything.
We wanted to learn what a tabletop exercise is. I hope you have a better grasp of how it works now.
Learn why regularly doing a tabletop exercise is so valuable. Like I said, it’s inexpensive compared to having an incident that you don’t respond to well.
Walking through a sample tabletop exercise, Matt walked us through a couple of scenarios and how you would add that twist and maybe add some other time limits on it, and then
Discuss the lessons learned and next steps for introducing or improving tabletop exercises at your nonprofit. We know it’s hard. If it were easy, we wouldn’t even have this webinar because everybody would be like, oh yeah, I just did that last week. It was super easy.
The fact that you’re here in this webinar and trying to learn more about it and being able to do it at your nonprofit, you should be proud of that and you’re taking a step.
We hope that we gave you some information and some examples that you can use to go back to your nonprofit and talk about doing it for real.
I’m happy to announce that next month, we are going to learn how to non-profit AI with a special guest, Brenda Foster from Vanguard Communications.
She and I did a podcast together about a month ago, and I immediately invited her back to do a full webinar. I wanted to share some of her experience, her hands-on advice on how to use AI tools at nonprofits. She’s going to dig in with a lot of use cases.
She has hundreds of nonprofit clients, so she’s seeing what they’re doing and how they’re using it. She’s going to share some of that with us. Also, what she’s doing herself and how she’s been teaching herself AI, better prompts, other things it can do, how it can summarize, how it can do this, how it can do that.
This webinar is going to be pretty hands-on around actually using these tools and practical, and I hope that you’ll join us for that as well. It’ll be at 3 PM Eastern, noon Pacific on Wednesday, August 27th. You can, in fact, register for it right now.
I just published it today on our website, so I’m going to share that link with you here in the chat, and it will be on our website, of course, communityit.com.
If you want to join us on Reddit, we’re going to be there for a few minutes now, and then over the next couple of days, so that’s at Nonprofit IT Management, and I will share that link with you too if you’re on Reddit. If you’re not on Reddit, I’m brand new to it, so we’ll learn more about it together.
And then I just want to thank you, Matt, for sharing all of this expertise and information with us. You know, we had so many people answer that poll that they had not done this yet, so I hope everyone on this webinar, you feel empowered, you feel like you can go out there and do this.
Of course, get in touch with us if you have more questions or want more resources. We have all of our links here that you can reach us on. And you know, your time today, an hour of your time today was a gift. We really appreciate you spending that time with us when you have tons of other things to be thinking about and doing, but maybe by prioritizing this time to do the webinar today, you can help your organization prioritize the time to do the tabletop exercise.
We wish you luck, we wish you success in doing it. And Matt, just thank you again so much for helping us think through it.
Matthew Eshleman: Yes, thank you. It’s great to be able to be here. And finally, start talking about the stuff where we really put it all together. It’s great.
Carolyn Woodard: Thank you.
Photo by Nika Benedictova on Unsplash
Wednesday January 21st, 2026, at 3pm Eastern join our experts to explore trends in AI, cybersecurity, and essential IT for nonprofits.
Fill out the form below to request a quote. We’ll be in touch shortly to discuss your needs and take the first step toward better nonprofit IT.