In today’s fast-paced, cloud-first world, the topic of cybersecurity can feel overwhelming, especially for nonprofit executives and staff focused on mission delivery. If you’ve ever felt intimidated by jargon or uncertain about where to start, you are not alone.
Community IT recently hosted a webinar, “What Are Cybersecurity Essentials for Nonprofits,” featuring our own Chief Technology Officer, Matthew Eshleman, and Ian Gottesman, CEO of NGO ISAC. Their core message was clear: you don’t have to do everything all at once. By focusing on a few fundamental practices, your organization can immediately block at least 80% of cyberattacks and build a sustainable culture of security.
Here is a breakdown of the nonprofit cybersecurity essentials that every leader and staff member needs to know.
The Foundation: Building a Culture of Security
Cybersecurity is often viewed as a purely technical task for the IT department, but it is, in reality, a people and policy challenge that affects everyone. As Matt Eshleman points out, security is a journey, not a destination—you will never be “finished” with security, but you can always take the next step toward better security.
The Cybersecurity Philosophy
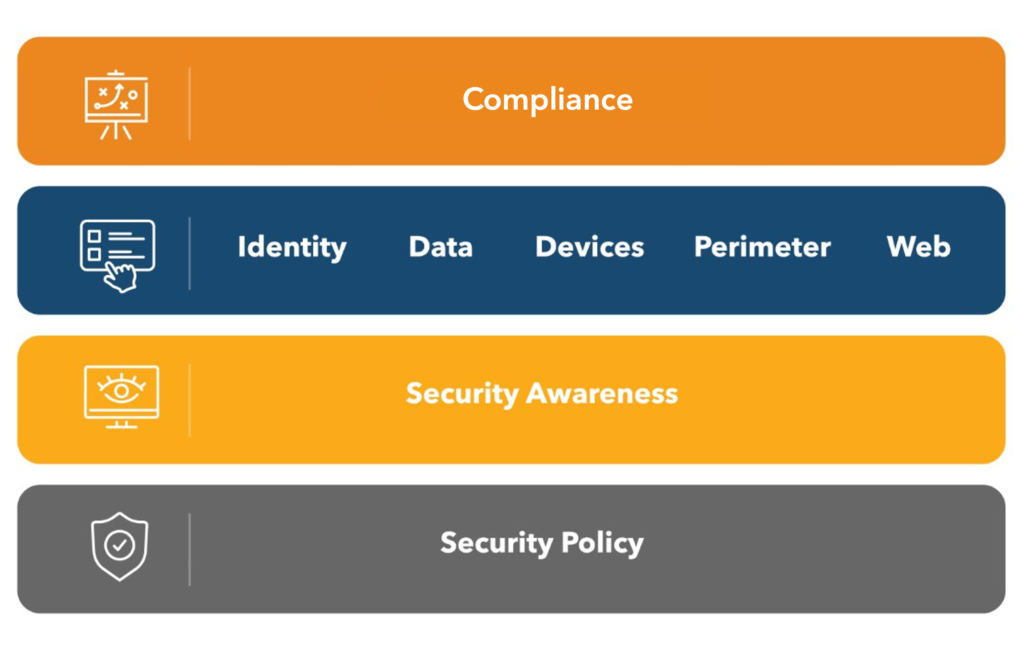
Before diving into technology tools, it is crucial to establish a strong base. Community IT views cybersecurity for nonprofits as a layered approach, starting from the ground up:
- Policy Foundation: Establish clear, plain-language nonprofit IT security policies. These are common instructions that address practical questions like: What is our password policy? Where do we store sensitive data? How do we handle personal devices (BYOD)? Starting with this foundation helps make other security decisions easier.
- Engaged and Trained Users: This is the best investment a nonprofit can make. Staff, volunteers, and board members must understand their role in protecting the organization’s data and mission.
- Technology Tools: Tools (like firewalls, endpoint management, and backups) are layered on top to provide technical protection.
- Compliance: This layer addresses specific requirements driven by audits or government funding (like adherence to CIS Controls). While important, it often comes after the basics are in place.
Stop 80% of Attacks: Focus on the Core Three
If your nonprofit has limited time and resources, Ian Gottesman and Matthew Eshleman recommend concentrating efforts on the following three pillars. These basic cybersecurity for nonprofits are repeatedly identified by experts as the most effective countermeasures against common threats.
1. Anti-Phishing Training
The Threat: Almost all account compromises and wire fraud incidents begin with a malicious email, known as phishing. The attacker attempts to deceive the user by obfuscating the sender’s identity or the link’s true intent to steal credentials. The most common form of internet fraud is Business Email Compromise (BEC), where an attacker intercepts a conversation (often with a vendor or grant-maker) to misdirect funds.
The Solution: Continuous Training
- Make it Frequent and Short: Instead of one long annual training, adopt shorter but more frequent sessions.
- Make it Engaging: Use different methods, such as mini-series style video content (available through platforms like KnowBe4), to make the training more engaging.
- Foster an Open Culture: Encourage staff to ask questions and share suspicious emails without fear. This collective vigilance is critical.
- Free Resources: Utilize resources from organizations like CISA and Take9, which encourages users to pause for nine seconds before clicking on suspicious messages.
2. Perform All Updates
The Threat: Unpatched devices are massive targets. Threat actors often scan networks looking for systems with known, unpatched vulnerabilities to exploit.
The Solution: Keep Systems Current Keeping your devices current is a simple yet often-overlooked defense in nonprofit IT security.
- Automate Everything: Ensure automatic updates are turned on for all laptops and phones that access company data.
- Address End-of-Life Systems: Devices running outdated operating systems, like Windows 10, are no longer receiving essential security updates and should be upgraded or replaced immediately.
- Inventory: Start with a good asset inventory of all computers and phones to ensure they are all included in your update processes.
3. Prioritize Identity Management
The Threat: Without strong identity controls, an unauthorized person can impersonate a staff member to misdirect funds or compromise sensitive data.
The Solution: Since nonprofits are increasingly operating in a remote, cloud-first world, robust identity management is paramount.
- Use a Password Manager: Start with a free or low-cost password locker to ensure all staff use unique, strong passwords.
- Enable MFA/Two-Factor Authentication (2FA): This adds a second layer of defense. While app-based authentication is good, consider upgrading to the highest protection level for key personnel.
- Upgrade to Physical Keys (For Key Staff): Highly targeted staff in finance, operations, or IT should switch from app-based MFA to a physical security key (often called a YubiKey or FIDO key). This robust approach prevents sophisticated session-stealing attacks. This is a critical step for identity management nonprofit leaders should consider, especially for roles with access to financial systems. YubiKey offers a Secure It Forward grant program to help nonprofits acquire these keys at little or no cost.
Overcoming Barriers and Addressing Risk
It’s far better to take a single step than to remain frozen by fear. The first step is often the hardest, which is why organizations like NGO ISAC and Community IT exist to help.
Understanding Your Risk
Cybersecurity should not be driven by fear. Leaders should conduct a realistic risk assessment to determine their organization’s most likely threats.
- Financial Fraud: The biggest risk for most small to mid-size nonprofits is cybercrime targeting financesperpetrated through fraudulent email (BEC).
- Actionable Steps: Use your cyber liability insurance application as a guide. If the application asks for controls you don’t have, pick one or two controls and start there to build momentum.
- Report Cybercrime Immediately: If you become a victim of a cybercrime, report it immediately to the FBI’s IC3 website. The FBI has an approximately 80% recovery rate for misdirected funds if reported within 72 hours. Do not be ashamed—you are the victim of a crime.
Addressing AI
The consensus among experts is that AI makes phishing attacks more believable, authentic, and cheaper for threat actors to execute. However, if you have strong fundamentals—trained staff and patched systems—AI is just another way for attackers to execute a threat that you are already prepared to defend against. The core work remains the same: focus on the basic cybersecurity for nonprofits.
Links and Resources Shared
Here are the links and resources shared by our experts to help you take your next steps in cybersecurity essentials for nonprofits.
Community IT
Cybersecurity Playbook – Free download detailing layered security philosophy and actionable steps for nonprofits. https://communityit.com/cybersecurity-playbook/
Cybersecurity Library – Articles, past webinars (including Cyber Insurance), and free resources on nonprofit cybersecurity essentials. https://communityit.com/library/
Services – Overview of Community IT’s full range of cybersecurity offerings for nonprofits. https://communityit.com/cybersecurity/
Other Resources
NGO ISAC – Coalition helping nonprofits improve cybersecurity; offers weekly briefings, an online community, and an annual conference. Pay What You Can to join. https://ngoisac.org/
CIS Controls – Security standards from the Center for Internet Security used to measure and audit organizational security maturity. https://www.cisecurity.org/controls
YubiKey Secure It Forward – Grant program providing free or low-cost physical security keys to nonprofits. https://www.yubico.com/secure-it-forward/
CISA – U.S. government agency offering free training resources, essential for phishing training for nonprofits. https://www.cisa.gov/resources-tools/training
Take9 – Free online tool teaching users how to pause and identify malicious activity. https://pausetake9.org
CyberPeace Institute – Free, self-directed security assessment and volunteer support to fix issues. https://cyberpeaceinstitute.org/services-and-tools/
FBI IC3 – Internet Crime Complaint Center for reporting cybercrime incidents (especially BEC) and initiating fund recovery. https://www.ic3.gov/
Basic Cybersecurity for Nonprofits
Getting strategic about basic cybersecurity doesn’t require a massive budget or a dedicated department of experts—it requires commitment to these fundamentals: strong identity management, consistent updates, and continuous staff training.
You are already accomplishing incredibly complicated, mission-driven work; cybersecurity is simply a manageable risk that requires a few clear, repeatable actions. If you aren’t sure where to take your first or next step, don’t feel alone. Contact Community IT today to schedule a conversation about your organization’s unique risk profile and how we can help you implement these essential practices to protect your mission.
Ready to get strategic about your IT?
Community IT has been serving nonprofits exclusively for almost twenty-five years. We offer Managed IT support services for nonprofits that want to outsource all or part of their IT support and hosted services. For a fixed monthly fee, we provide unlimited remote and on-site help desk support, proactive network management, and ongoing IT planning from a dedicated team of experts in nonprofit-focused IT. And our clients benefit from our IT Business Managers team who will work with you to plan your IT investments and technology roadmap if you don’t have an in-house IT Director.
We also offer nonprofit managed security services – proactive cybersecurity tactics that drastically reduce the risk of damage during a cyberattack. If you have questions about cybersecurity, incident response planing, or business continuity, you can learn more about our approach and client services and contact us here.
We think your IT vendor should be able to explain everything without jargon or lingo. If you can’t understand your IT management strategy to your own satisfaction, keep asking your questions until you find an outsourced IT provider who will partner with you for well-managed IT.
If you’re ready to gain peace of mind about your IT support, let’s talk.
As advocates for using technology to work smarter, we’re practicing what we recommend. This article was drafted with the assistance of an AI, but the content was reviewed, edited, and finalized by a human editor to ensure accuracy and relevance.
