View Video
Listen to Podcast
Part 1 covers the cybersecurity landscape and types of threats facing nonprofits, our framework for how to think about cybersecurity and where staff training fits in your strategy, and the basic philosophy of security awareness training. Pt 2 gets into the details and examples of a typical cybersecurity training program, and Matt answers audience Q&A.
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Are your staff as ready as they can be for the next attack?
Our cybersecurity training team manages hundreds of clients and shares our knowledge on what works to keep your staff prepared, not just scared. Matt Eshleman, our CTO and cybersecurity expert answers your questions on how to manage frequent, timely, and engaging training.
Cybersecurity Awareness Training Tips
We often say that staff training is a foundation for cybersecurity protections. As the risks are always evolving, your training needs to be current too. Gone are the days when your staff could be adequately protected by watching an hour long video with a quiz once a year.
But managing more frequent training is difficult. We will discuss the tool we use, KnowBe4, which makes it easy to stay up to date and administer training to all staff. There are other training tools out there that work for nonprofit staff – the most important tip is to commit to training and to prioritize it as a team. Your staff and leadership are your best defense of the organization you care about.
In addition, with new auditing requirements SAS145 your auditor must assess IT risks to your financial processes – and it will be necessary to demonstrate staff cybersecurity training in your audits.
Learn about these issues and more with our experts! If you’ve been putting off implementing a comprehensive cybersecurity awareness training regime, don’t wait any longer.
Join CTO Matthew Eshleman and host Carolyn Woodard to learn how to implement an up-to-date and flexible cybersecurity awareness training program this year.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT is proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community. There are multiple cybersecurity awareness training vendors with products that work for nonprofits. We will be discussing the tool we have selected and use, KnowBe4, which offers nonprofit discounts, but our insights and tips will be useful no matter what training program you are using, or if you want to create and run cybersecurity awareness training in house.
Many questions asked at registration or live at the virtual event will be answered in the transcript. Check back after the webinar for additional resources.
Presenters:

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert.
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response. You can view Matt’s free cybersecurity videos from past webinars here.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She is happy to be moderating this webinar.
Check back for additional resources if you miss this webinar on cybersecurity training awareness tips.
Transcript
Carolyn Woodard: Welcome, everyone, to the Community IT Innovators webinar on cybersecurity awareness training tips.
Do you know how to keep your staff trained in identifying phishing emails?
Do your staff know what to do when they see something suspicious?
Did you know that many insurance policies and nonprofit auditors are asking for proof of staff training in cybersecurity?
Today, we have two experts in managing cybersecurity training who are going to give us tips to keep your program current, engaging and up to standards. Correction, we had two experts. My name is Carolyn Woodard. I’m the Outreach Director for Community IT. I’ll be the moderator today. And unfortunately, Ana Zambrano was feeling under the weather, so, I’m also going to be stepping in for her with her notes.
But I’m very happy to hear from our resident cybersecurity expert. So Matt, would you like to introduce yourself?
Matt Eshleman: Great. Thanks. It’s great to be with you all here today to talk about security awareness training, which I think is an absolutely critical part of any effective cybersecurity program.
My name is Matt Eshleman, and I just celebrated my 23rd anniversary at Community IT. I spent 23 years full-time and have a little bit of extra time before that as an intern. I’ve done a lot of different things in my time here at Community IT and spend a lot of time now focusing on cybersecurity and strategy and just helping to protect organizations against the myriad of threats that exist out there against nonprofit organizations.
Learning Objectives
Carolyn Woodard: I’m going to talk about our learning objectives. We’re going to go over the cybersecurity landscape, why it’s important to pay attention to cybersecurity training and protecting your nonprofit. We’re going to give a little overview of our cybersecurity framework, talk about the importance of the training, and then give a little example of training and practice.
About Community IT Innovators and Outsourced IT Support for Nonprofits
Before we begin, if you’re not familiar with Community IT, a little bit about us. We are a 100% employee-owned managed services provider. We provide outsourced IT support. We work exclusively with nonprofit organizations, and we help nonprofits accomplish their missions through the effective use of technology. We serve nonprofits across the United States. We’ve been doing this for over 20 years, and we are technology experts and are consistently given the MSP 501 recognition for being a top MSP, which is an honor we received again in 2024.
I want to remind everyone that for these presentations, Community IT is vendor agnostic. We only make recommendations to our clients and only based on their specific business needs. We never try to get a client into a product because we get an incentive or benefit from that. We do consider ourselves a best of breed IT provider. It’s our job to know the landscape, what tools are available, reputable, and widely used. and we make recommendations on that basis for our clients based on their business needs, priorities, and budget.
Today, we’re going to be talking about a specific training tool that we use with our clients and that we use ourselves called KnowBe4. There are a lot of training tools out there. We’ve selected this one because we think it is the best available. And we’re going to talk a little bit about the features that weighed into our thinking on that.
Today is not a KnowBe4 demo. You can find that on their site, if you’re interested in it. Today, we’re going to be talking about the ways this tool fits into an overall strategy that places training your people at a foundational level in your cybersecurity strategy and planning.
A little bit more about us. Our mission is to create value for the nonprofit sector through well-managed IT. We also identify four key values as employee owners that define our company: trust, knowledge, service, and balance. We seek to always treat people with respect and fairness, to empower our staff, clients, and sector to understand and use technology effectively, to be helpful with our talents, and we recognize that the health of our communities is vital to our well-being and that work is only a part of our lives.
Audience Questions: What Kind of Cybersecurity Incident Did You Have in the Past Year?
One thing that can really throw you out of balance is feeling the stress of experiencing a cybersecurity incident. We know from experience with our clients that even if you do avoid the worst circumstances, just having a close call can be incredibly stressful to all of your staff. So, we’re going to launch a quick poll, which is what kind of cybersecurity incident did you have in the past year? And this is multiple choice.
- You can choose none.
- Phishing, which is an email trying to get something from you.
- Smishing, which is a spam text trying to get something from you, get you to do something.
- A malicious browser pop-up.
- Attempted gift card fraud.
- Ransomware.
- Attempted wire fraud where the money was not sent. You found it in time and were able to not send money.
- A successful wire fraud attack where you did, in fact, wire the money to the hacker’s account. Compromised account, which is the credentials were either suspected or confirmed to have been hacked. So, someone got access to one of your accounts for one of your subscriptions or your email was able to send emails either from you or from within your organization.
- Something else, which if you had something else happen, go ahead and put it in the chat if you are comfortable doing that and then not applicable.
- So, if you’re joining us, maybe not from a nonprofit or don’t really know if something happened, maybe you’re brand new at your nonprofit, you can go ahead and choose not applicable.
I’m going to end the poll and share the results. And Matt, can you see that?
Matt Eshleman: Yes. Thanks to everyone who responded. Always curious. We kind of know what the metrics are for our clients. They’re always curious to see what the broader experience is.
So about 20 percent of folks said none, none at all, which I do think I would be suspicious of that given that everybody gets spam messages and I would say most organizations are having staff that are getting those weird or strange text messages to their personal phones.
The majority of folks did say, yes, they had experienced phishing.
Almost half of the respondents said that they had received those spam texts. And I’ll say we’re seeing that probably started about a year and a half, maybe two years ago, but that is a really common method of ways to create engagement. And then the hackers go on from there.
Malicious browser pop-ups, a few people have reported. About a third of the participants have said that they have been on the receiving end of maybe some attempted gift card fraud.
No ransomware, which is great to see, and again, aligns with what we see across our clients that we support. Ransomware seems to be something that targets larger organizations with a lot more of that server infrastructure.
21% that attempted wire fraud or it was caught in time, so that’s great. We see that as a big risk to organizations.
About 17% have said they experienced confirmed account compromise, which again is something that we again see, unfortunately, with a lot of regularity, even as more and more accounts are protected with MFA.
Thanks for sharing and participating as we just learn more about each other.
Carolyn Woodard: Yeah, that is great. Thank you, everyone, for coming out. We did have somebody that mentioned in the chat that emails were sent to their staff about verifying Zelle information, but luckily, they don’t use Zelle, so they were able to identify those pretty quickly. But yeah, I think those types of phishing, they’re just hoping that they’re going to choose some tool that you do use, and then you’ll think, oh, I need to verify that.
And we have a quick question, Matt.
What is your opinion on an executive telling IT to allow local admin rights for a staff member to take a bar exam on an organization-owned laptop?
Matt Eshleman: I think the standard practice would be staff should just have standard permissions and not need to take that additional step. I think usually whenever we have cases where there’s some sort of testing software or proctoring software, there end up being a lot of extra special cases that need to happen. We understand there might be some special one-off cases, if it’s possible to install that software and then remove the admin permissions, that would be preferable. But again, just be flexible and be able to manage and report it. It’s not a long-term solution.
Carolyn Woodard: Yeah, I would guess it would be case by case. I also think that hopefully is something that’s in your acceptable use policies. So, if it’s they’re taking the bar exam because you are a legal organization and that’s part of their job, then that might be covered by your policies.
But if it’s not, then, or if it’s some other testing that really doesn’t have anything to do with their job, but they just want to use their company owned laptop, then that might be something to just make sure to look at your policies about. But I agree that if you do give them that kind of admin, you’d want to make sure to take it away from them before things got out of control.
So Matt, I think you are going to talk a little bit more about why this is so important.
Cybersecurity Landscape for Nonprofits
Matt Eshleman: Yeah. With all these cybersecurity presentations, I think it’s helpful to understand just the operating environment that we all find ourselves in.
I think the big takeaway (from this slide) is that the amount of cyber-crime and cyber threats that are facing all sorts of organizations, nonprofits included, is really going up over time. As much as we’d like to say we’ve reached the peak, we’re going to see a receding of cyberattacks and this malicious activity, that is just not the case.
I think now, especially with how prevalent AI type solutions are, that just gives the hackers even more tools to have well-crafted e-mails, perhaps generate more malicious code that’s more effective. So, it is kind of a dangerous world that we’re operating in, and the FBI stats certainly support that in terms of just the amount of crime types that are being reported. Maybe some moderation from back in 2022 or 2021, but still just a staggering number of direct losses, right?
The FBI numbers here that you can see in that chart on the bottom left-hand side, is $37.4 billion is lost to cybercrime, and that impacts every type of organization and individual. So again, it’s a serious crime, a serious impact across all sectors of our economy.
Maybe the one good spot is the actual ransomware amount is paid (is going down.) This chart now has some 2024 data from a vendor called Chain Analysis. They do a bunch of blockchain analysis and related services, but they were tracking ransomware payment, and that amount has fallen and fallen significantly now to its second-lowest level in the last five years.
Ransomware is something that makes the news, gets a lot of mind space, but is generally targeting organizations that have a lot more physical server infrastructure. For many of the organizations that we work with, that under-200-seat-class, most of that infrastructure is in the cloud, software-as-a-service applications. There aren’t really servers to infiltrate or firewalls to attack. The attack surface has changed quite a bit.
And we have not seen it, asterisks, yet, but in terms of ransomware, attacking Google Workspace or SharePoint, it’s not to say it’s not going to come, but I think we have other threats that we’re concerned about. Mostly they’re going to be targeting your users through email. So hence all the focus on security awareness training.
Maybe just a little bit of a preview for some data to come at our April webinar on our Incident Reports. At Community IT, we support about 200 nonprofit organizations. We have a fantastic help desk. We categorize all the incidents that are reported to us. This represents the last several years of that data. Again, reiterating that the amount of spam that our clients are reporting, the amount of spear phishing and phishing messages that are reporting, the number of account compromises continues to go up year over year.
And unfortunately, we’re not seeing that re-seed yet. And it’s a call that we need to continue to escalate our protections that we have in place, the education that we provide to our staff, and the tools that we have in place to protect our organization from the never-ending barrage of cyberattacks.
Cybersecurity Framework
And then in terms of how we look at or think about cyber security and talk about it with organizations and leadership is through this graphic.
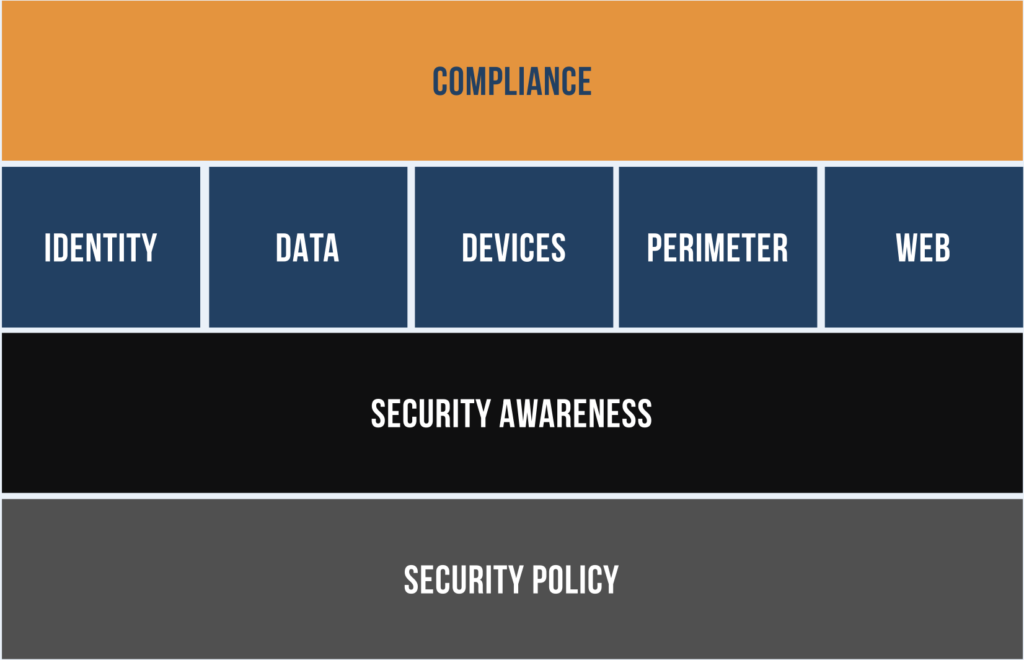
I put this together because I wanted to highlight the fact that while the technology tools really get a lot of the marketing dollars, and it’s really fun to look at all of that stuff, while it’s not as exciting, it’s much more important to start with a good foundation of security policy. Set the ground rules so that your organization has a common understanding about what is acceptable, what’s not. Answer those questions, for example can I use my personal phone? Can I use my personal computer to access work resources? Maybe that question we had earlier, “hey, I want to take an exam using my work computer. Is that allowed? Is it not?”
So just having that policy foundation is really important.
There’s lots of great templates that are out there. We do find that the templates tend to be geared towards large and complex organizations. So, they do require some tailoring to make sure that they’re relevant for the small to mid-size nonprofit. And what I mean by that would be that 20-to-100-person organization.
Right on top of security policy is really that security awareness. I’m the CTO. I’ve been the CTO for a long time. I love all the tech stuff. It’s fantastic. But if I had to make choices in terms of where I was investing my IT spend, it would be investing in training for users. Technology tools can fail. You can have all these different solutions in place. Having an engaged program with your staff, where there’s a trusted relationship with IT is really important. And I think training provides a tremendous return on investment for those limited IT dollars that I know many of us have.
Once you have a good policy foundation, you have a good security awareness training program in place, then you’ll probably start to receive more benefit from some of the specific technical solutions to protect your digital identity, to make sure your data is backed up, protect your devices with patching and antivirus. Build that network perimeter. Again, if it’s maybe your home is now the network perimeter, or maybe if you’re making a transition back into the office, and you need to make some updates from technology that hasn’t been updated since 2020, that’s important.
And then the web, right? And I’ll maybe say a little bit more about this just because we are seeing in today’s contentious political environment that staff and organizations are being targeted simply because of where they work and who they are. The bigger digital footprint that you have, that’s visible on your site, the easier for those malicious actors to find out more about you and the organization, who works there, and really target them. We are seeing organizations be much more intentional and focused on what information they are putting up on their website to make publicly available, communicate the mission of the organization, that kind of thing. Maybe pull some of that staff information down just to reduce their overall attack surface and try to help protect some of the digital identity for their staff.
And then finally, the compliance layer on top. We see organizations investing in this whenever they’re oftentimes getting funding requirements that say, you need to be NISC compliant or CISV8, you need to maintain controls that are in line with that. So that’s probably the last thing that you do. But if you’re doing all the things under there, you’re well on your way to meeting that compliance requirement.
Carolyn Woodard: And I like how compliance wraps back around to the policies. So, you can have all of the policies in your acceptable use manual or in your employee manual. But if nobody’s checking, then do you even really have the policies? If nobody reads them and nobody’s doing them, for example where you might have staff who have left, and it may be part of your offboarding policy that you need to disable their accounts. But if no one’s checking that those accounts did get disabled, then you still have this pretty big risk of hopefully they didn’t leave in a huff. But in any case, you don’t want to have somebody who doesn’t work for your organization who still has access to those accounts.
So that compliance piece wraps back around with leadership to your policies and making sure that those policies are being carried out.
How Effective are VPNs for Remote Workers?
We have a quick question in chat, Matt. How effective are VPNs for remote workers? Are we still saying that people should use a VPN? If your tools are in the cloud, what do we recommend?
Matt Eshleman: I mean, the VPN conversation is interesting because there’s lots of VPN services that pitch it as hey, it’s secure and you’re going to make your access protected.
I would say in general, if you have an office and you have staff who are largely working out of their homes, a VPN is not necessarily required. Because, as Carolyn said, mostly we’re just accessing cloud resources.
VPNs can be helpful whenever maybe you have staff who are traveling internationally and you need to provide some consistency. If you are often working from untrusted or kind of unreliable internet cafes, that kind of thing, that could be a reason where you may want to have a VPN.
But I would take it a step further and say, if you are going to have a VPN solution, it is really important to invest in something that’s business grade or business class.
Because one of the challenges that we have faced in supporting organizations that have users that are using VPNs, is that it makes security monitoring very complicated and adds in a lot of overhead. Because people are using personal not business-like class solutions. They might be in Virginia, but they turn their VPN on. And all of a sudden, it looks like they’re in Colorado. Then that sets off all kinds of alarms. And then, we have to track back and say, well, is this trusted? Is this approved? Is this the right location?
And so, if you are going to use a VPN, it makes sense to look at something where you can say, here’s our corporate VPN solution. We’re going to make some approved IPs and say, hey, we’re going to allow traffic to come through our corporate VPN network.
And it’s actually a way to use and manage access to applications so that, if you’re an organization that maybe has heightened security requirements, you can say, well, we really want to vet all the traffic. We don’t want just anybody in the world able to try to log into our Office 365 environment, our Google Workspace environment. We want to funnel that all through a trusted VPN solution that we can verify the user, maybe even verify the device that they’re coming from. And then after that happens, then we’ll let them connect.
So, in general, you don’t need a VPN. If you have some specific heightened security requirements, then that’s something to look into, and look into a business class or enterprise grade system, where you can provide a lot more controls and specificity around who’s connecting, how they’re connecting, and build that into the program.
Carolyn Woodard: I will say we did a podcast a couple months ago about cloud services and how almost everything that you would have had on a physical server that you really would need to VPN into, that’s physically in your office and you’re working from home, almost all of those services are now available in the cloud. So that might also be a case for somebody needs to get into an accounts database or something like that. But if you aren’t in the cloud, it might be something to think about doing, because then you can have all of that cloud security on it and not have to do the VPN.
All right. Thank you so much, Matt, for going over those issues. We have another poll for the participants. We have two questions in the same poll.
Audience Questions: How Do You Train Staff? How Often?
The first question is, how do you train staff?
And you’ll find the first five answers are,
- We have no plan, no formal training.
- We do ad hoc training.
- We have a free tool for our HR system or something related to that, like a backend office system.
- We have a managed training campaign through a vendor
- Something else, something other.
So please choose one of those.
And then for the second column, we have a second question, which is, how often do you do training?
- Never. It’s fine. There’s no shame. We’re not judging you.
- You have an ad hoc schedule, so do training when something happens and you are made aware of it.
- Annual training, that used to be the gold standard, right? You had to do the video once a year and answer the quiz.
- Quarterly training,
- Something other.
So Matt, can you see that?
Matt Eshleman: Yes, I can. All right. It’s good everybody’s here today.
So about 30% of folks don’t have any plan or no formal training in place. And another 30% are just doing ad hoc training. So hopefully you’ll get something to take away. A small number doing a free tool through HR, and then about another 30% of folks are doing a managed campaign through a vendor. So, an even distribution there between non-ad hoc and then managed training.
And then of the folks who are doing training, it looks like the most common response is quarterly. About a little over a third of folks are doing it quarterly. And maybe I’m curious if that other training schedule, the 15%, is weekly, daily, monthly?
Carolyn Woodard: I’m very happy to see nobody said never, that that’s their training cadence. Thank you so much again for joining and for sharing that information with us.
Basics of Cybersecurity Awareness Training for Nonprofits
Okay, we are going to go ahead and move on to talking about security awareness training. At Community IT, we recommend as part of a minimum standard that in general, you want to have a deliberate and well-communicated plan that has executive buy-in. It’s always a lot better for staff and executives when there’s an executive leading the charge and also doing the trainings.
Our goal for a security awareness training program is to effectively communicate information, build that relationship between the staff and the IT team, and improve the language and how we talk about cybersecurity threats and how we incorporate everyone in being aware and seeing themselves as being able to protect the organization. Training is intended to be positive and educational and not punitive.
KnowBe4 is the tool that we use. It provides a full range of resources that are available to users.
New Staff Training/Onboarding
Matt Eshleman: We really want to make sure, particularly, that new staff are included in training, basically as part of their onboarding, because what we see from the other side of the Security Awareness Training program that we have is basically a test phishing campaign to see who’s clicking, what are they clicking on, what are the trends there? And it is very clear that new staff are much, much more likely to click on these phishing messages than staff who’ve been at the organization for a while, who know their culture and who have received training previously.
New staff are the ones that are targeted by these malicious actors. Gift card fraud is particularly focused on them, because they don’t know maybe the organization norms yet. They want to fit in. They don’t want to push back. Whenever we do have cases where there’s a gift card fraud, it is often a newer staff person or a more junior person who maybe doesn’t want to push back on their executive or their director asking them to buy a gift card.
We want to make sure that new staff have training as part of their onboarding. It’s just built into the plan.
Quarterly Trainings
And then for all the other staff, then we take an approach of doing quarterly trainings. That comes out through our platform automatically. Typically, those trainings, that new staff orientation, right, is about 15 to 20 minutes of content, with quizzes and videos and interactive elements there.
And then whenever we move to the quarterly trainings, those end up being a little bit shorter and typically more focused on a specific topic. For example, learning about smishing, learning about link construction and how the phishing messages are actually put together. Good practices for working from home, right? The quarterly trainings tend to be focused more on a specific topic.
And quarterly trainings can become more tailored to the season. I know often towards the end of the year we typically provide some more training around shipping and gift cards and all the fraud that seems to ramp up at the end of the year whenever people are waiting for a package. The fraudsters will use those messages to basically get people to click. And I’ve had those conversations. They say, “oh, I thought that was real. I was waiting for a FedEx email. And one showed up in my inbox. And so, I clicked on it.”
Point In Time Training
So, well, we can say that was a test phishing message. And so, here’s what to look for. For the folks that do click, we implement something through the KnowBe4 platform. That’s point in time training, right? So you click on something and immediately you get the window with the message that you clicked on and the things highlighted that you should have been paying attention to. I think that’s pretty effective to kind of get that reinforcement, maybe that slap on the wrist right when it occurs. We call that point in time trainings.
And then for some organizations, we are ramping up and doing monthly trainings just to build that relationship, build the rhythm. We see through our data that having content that is more frequent but shorter in duration leads to better engagement and better results overall.
For those folks, for the organizations, and if you’re in IT, you probably can already think of, oh, that person, the one that’s always clicking on stuff, or they always need extra support, and that’s probably true in cybersecurity as well. For folks that really do need that extra support training, the KnowBe4 platform allows us to build some custom training plans that say, oh, somebody’s clicked on three messages in the last six, here’s some extra training for those folks to do.
You can build these dynamic campaigns so that, hey, if you’re being attentive, following the trainings, not following through all the fake phishing messages, hey, you just do the basics. But, if you’re in a category where you’re having lots of trouble identifying those phishing messages, then maybe you need some additional support or education. So, through these training programs, and I’m sure others can do it as well, but basically you can build some special campaigns for those staff that need more support.
Phish Alert and Reporting to IT
The final piece on here is a specific KnowBe4 tool. They call it Phish Alert. You can basically report messages or instruct your staff to report messages that they think are suspicious. If it comes from KnowBe4, if it’s one of those fake messages, they get a little green checkbox that says, hey, good job, you identified the right message.
If the suspicious message didn’t come from KnowBe4, it’ll get removed out of their inbox and submitted to an email address that you define. I think we like that because it helps us communicate with staff, build that relationship, and show them that, hey, IT will be there to review and vet those messages that are being reported. And also helps us look for trends again.
Is this message, one person reported it? This is really suspicious. Did anybody else get it but maybe didn’t report it? The Phish Alert tool gives us some insight in terms of what types of messages are being targeted at our staff.
Carolyn Woodard: Can I tell my funny new staff story? I was a contractor with Community IT for years before I came on as a staff member, and Matt, my first day with an official account, I got an email from HR at Community IT. And I’d never seen that email before, but I said, “yay, I’m official now,” and I clicked on it. And no, that email does not exist at Community IT. It was from KnowBe4. So, it was a good illustration of how you can think that you’re pretty savvy, but new staff, all the time, you’re trying to do the right thing, and you’ve got a ton of new emails coming at you. It’s definitely great that KnowBe4 has built in to give those tests right away the first couple of days. I definitely fell for it.
Carolyn Woodard: KnowBe4 is the tool that we use. It provides a full range of resources that are available to users. So, Matt, would you like to talk about KnowBe4?
Matt Eshelman: Yeah, so, as Carolyn said, we use KnowBe4. It gives us a lot of tools to automate and really streamline the training process.
Levels of Cybersecurity Approaches
For the folks that are in that no training or an ad hoc approach, you’re in that level one, maybe low level of maturity.There is the likelihood that risk for your organization is a lot higher. Because most organizations are in the cloud the risk of ransomware is relatively low, but the risk for account compromises, which are often initiated through clicking on a malicious link that’s stealing your credentials, that’s very high.
Organizations are getting those wire fraud messages or you’re interacting with maybe a compromised account on the other end from somebody you know and you trust, that verification process and looking at all of the other email recipients can be missed.
So, starting off at that basic level of compliance, the risk of the organization is a lot higher.
I think as you move into those categories where if you can make cybersecurity something that the organization is working at intentionally, having a formal program for new staff, or as Carolyn said, unfortunately, you’ve got a good example to share that, hey, this happened to me (on my first day,) watch out. And I think that can be really effective as a tool for other new staff to hear, oh, yeah, this is not just the video, but it’s my colleagues also reminding me.
But then that can build into these more mature levels that are identified here from having more robust scheduled trainings, maybe tailored trainings based on the work role, who’s clicking on stuff.
And then that feedback loop, I think is important. So, it’s not just IT that makes everybody take all these trainings, but IT is really a partner in keeping the organization secure and staff are helping IT by reporting suspicious behavior, reporting those weird messages that make it through the spam filters, because the technical solutions are imperfect. And it’s an important way to build culture, to build relationship from the staff and the IT services.
You can work towards building that overall sustainable security culture, where it’s something everybody’s working together. It’s NOT just operation staff and executives don’t have to participate, but it’s really building a culture across the organization to make sure that the entire organization is secure.
Carolyn Woodard: Building on that idea of education, improving your training standards, and helping to improve the overall cybersecurity maturity of your organization. These are some helpful tips to increase the effectiveness of your program. Of course, each organization, every nonprofit is a special flower and has its own unique culture. There are a range of tools and trainings that you can find. But these are some of our tips.
Cybersecurity Training Tips
Providing kudos, we know executive involvement is key.
You want the training to be focused on positive things to do. It helps improve the organization’s security. So always approaching it in that message rather than “I’m going to have to do this because it’s required, but I think it’s a massive waste of time.” Trying instead to encourage the staff to feel that they’re protecting this organization, that they care enough about to work for. So, putting them all in the same army, protecting your organization.
Every organization is different. There may be a mandated baseline training, but you may find that your organization is really competitive. So having quizzes or having some kind of leaderboard might work for you. Or if your organization is more co-operative, having games or having mini trainings is better because your schedule is so hectic all the time.So, trying to identify the culture and the style is helpful.
Remedial training, of course, calling it remedial may be difficult, but it should be quick, it should be relevant, it should be instant. As Matt said before, when you click on the thing, immediately getting some information and education about what was wrong with that email, that was a fake phishing attempt and what you could have looked at to see and just so that you’ll know next time. That really helps benefit the people who are the clickers.
And then practice, practice, practice. Familiarity with the types of attacks and scams is more than half the battle.Doing those micro trainings, having the phishing emails come right to your email, doing frequent trainings also helps you introduce new scams as they’re kind of coming online, so hopefully you can train your staff before they get a real one from the wilds that’s that new scam that they don’t know about.
A couple of months ago, last summer, we did a webinar on being a learning organization that I think was just really helpful.
We’re going to move along and go into analyzing a suspicious email. So Matt, you were going to talk a little bit more about phishing.
Analyzing a Suspicious Email
Matt Eshleman: Yeah, so I think some of the terminology is important. We’ll talk about the specific steps that you can take to critically look at a message, check for those red flags, and then an encouragement always to be able to ask someone or submit a ticket. That feedback loop and that engagement with IT is a really important aspect of the whole process.
Carolyn Woodard: You never want to make it so that people feel afraid to tell you that they’ve clicked on something wrong or made a mistake, because the longer it lasts, the worse it’s going to be.
Spam Vs Phishing
Spam versus phishing, we’re going to talk a little bit about spam being those unwanted communications for goods or services. They’re sent in bulk, you’re just on a list, you’re getting something from a legitimate company where they’re hoping that you’re going to order something from them or what have you, versus phishing, which is a type of social engineering in which the attacker pretends to be someone you know, to gain access to something you have.
Often with phishing there is a link, there’s something that they’re trying to get you to click on or give your information to them so that then they can use it for something else.
Matt Eshleman: Thanks for providing that definition. I think a lot of stuff gets blobbed together, but it is pretty clear.
Spam is just unwanted messages, it’s pretty clear who it’s from, you just don’t want it. It’s okay to unsubscribe, it’s okay to delete. All those things are important steps to take.
With phishing, there’s often these red flags that you can see in the message, and that should trick your spidey sense to analyze the message and look at it in more detail. There’s often this appeal to human emotions, a sense of urgency, maybe that authority gap, maybe some threatening language or maybe even unrealistic promises or free money. “Hey, this great deal, click on this, this limited time offer, right?”
We see these techniques in a range of engagement messages that we get. But I think the phishing messages particularly use this technique because they’re relying on us to take that action.
There’s often this vague or generic greeting, or maybe a formal greeting, if they’re scraping your information off of LinkedIn, maybe they’re going to refer to you as Matthew, not Matt, or dear user, or just “greetings.”
Go over the misspellings and grammatical errors, this still does happen, although I must say, with the advent of all these AI tools that are free and easy to use, well-crafted, sophisticated messages with good tone and proper grammar are the rule now. And some of those things we used to be able to rely on just aren’t the case anymore.
Then, obviously look for suspicious attachments. What we are seeing often is that there will be some kind of… The link itself isn’t maybe malicious, but the link goes to a document, and in the document, then there’s another link to go to or some other instructions to follow. And so, it avoids the virus scanners that are in your email tools, but then takes you to another location, maybe that isn’t as well protected. And then, they’re going to try to get access to your information through there.
The things that we’ll really look at, and we have some examples here in the next slide or two, is the information that doesn’t match right at the sender’s name, email address, or the logos, URLs. You know, those are really the bedrock techniques to really understand, is this message coming from who I think it is or who it says it is?
And then the follow up, right? Click on the link and sign in, all those requests, those call for actions, really, are the beginnings of many scams to try to intercept your credit cards, your password information, to take those next steps down towards a financial attack.
Carolyn Woodard: So, here’s an example.
Hover Over the Links
Matt Eshleman: I’ve used this in a couple of presentations, right? This was sent to me. It was actually a while ago at this point. Online Invoices is a real company. This is their branding. Everything looks correct. All the links in this message are accurate.
Except for if you hover over the “view invoice,” instead of it going to Online Invoices, it’s actually going to corporatecatererscleveland.com, which is not Online Invoices.
And then if you notice up in the from field, the display name is Online Invoices, Inc, all rights reserved. Very formal. The actual reply email address is yourinvoiceatmedsdirectinc.com.
So, what that tells me is that perhaps there’s problems both with corporate caters cleveland.com, right? Their website maybe has been compromised and these threat actors are now using it to host a malicious web page. And at the same time, medsdirectinc.com, maybe that’s a domain the hacker set up, maybe it’s a compromised account, but they are using that obfuscation to target me.
I pay a lot of bills. I get a lot of invoices, right? And so, it wouldn’t be unusual for me to get an email from Online Invoices. But in this case, because of hovering over the links and looking at the reply-to address, we can determine that this is indeed a phishing email that’s designed to take me down the road of making a payment to a vendor that doesn’t exist.
No Links but Still Suspicious
What about when you don’t have links to look at, right? This is something that we see on and on. It’s really frustrating that these things sneak in through the spam filters, but there’s just not that much to go on, right, for a spam filter to analyze this.
So, this is an example, right? “I need you to run a quick task. Let me know if you’re available.”
Again, we see those elements of a sense of urgency. There’s a little bit of that authority power dynamic, where the executive director is asking a subordinate to do something. “Don’t bother me. I’m in a meeting, do a quick task.”
But if you would interact with this, then there’s probably a call for “Hey, I’m out. I’m in a meeting. I need some gift cards for this purpose or that purpose. Can you just do it? I’ll reimburse you, or you’ll get reimbursed whenever you get back into the office.” And then away goes the gift card money.
Wire Fraud
And then again, the same thing, moving up from gift card scam, which is often denominated in the hundreds of dollars, the wire transfer fraud is really prolific. The bad guys figured out it’s way easier just to ask you for $50,000 than to write a sophisticated virus that needs to be deployed on a system and encrypt your files, and you got to buy Bitcoin. And so, it’s just easier to say, “Hey, can you process a wire? Here’s the updated information. We’re having tax issues with our bank.”
IRS Fraud
I would completely foresee that in the very near future, the bad guys are going to know, right? 8,000 IRS workers have been axed. You’re going to get a whole bunch of emails that say, “Hey, we’re having problems. I’m from the IRS. We’re having problems processing your tax information. There’s been a problem. We’re understaffed. Here’s the updated information to make your payment.”
I guarantee you that those messages are going to start landing in your inbox soon. Again, the bad guys know it’s just a lot easier to ask. Again, the wire transfer, that sense of urgency.
Prevention: Follow Your Established Procedures
So, it’s important to have these pre-established systems in place. How does your organization change? Make wire transfers, who’s authorized? How do you verify the destination that you’re sending it to? Is it trusted and is it legitimate?
And that really should involve something other than email. Because it’s very likely that even if the sender address, even if this Tom person is from an organization that you know, it’s possible that their account is compromised.
We see that being a technique that the threat actors use, is that they will compromise an account and then they will use that compromised account to reach out to trusted organizations in your address book, that you know, on your website, they know who you interact with. And so, it’s important to have those pre-established processes in place.
I think we have a whole webinar about financial fraud.
Carolyn Woodard: Yeah, I was just going to add in, don’t do those workarounds. Make sure you follow the processes that you have. They’re there for a reason.
Matt Eshleman: And then here, finally, so this is an example of the message from the KnowBe4 platform. In the platform, you can toggle to see the red flags. And if we would do that here, you can see that right from it says Microsoft, it’s actually from microsoftsecure.net, right?
That’s not the correct thing. We see that call to action, “Here’s a QR code, right? Scan this link, take this additional step.”
All those are some red flags that would call us to be critical in terms of evaluating the message and its legitimacy.
Carolyn Woodard: So, we only have a little bit of time left. I think we’re going to have to go quickly through this so we can get to a couple of Q&A. But we did want to talk about what do you do after you find a suspicious email?
What Next After You Find a Suspicious Email?
How do you make staff aware of the resources they have and what their next steps should be? Remembering that the cover-up is always worse than the crime. Staff should always feel safe reporting mistakes and they should know not to try and fix the problem themselves.
Matt Eshleman: I think that’s exactly right. I think having a trusted relationship between IT and the staff is really important. Again, if somebody clicked, it’s okay. IT wants to know about it so we can remediate it. Often, we reset passwords, maybe we’re going to scan the computer, we’re going to look at some other things just to verify that that click didn’t turn into access. There’s a couple of different tools.
We use KnowBe4, which gives us a super easy and integrated way to use what they call the official button, so that staff can be instructed to just click official alert, and then it gets submitted to an email address that you define. For in-house IT departments, we would just suggest making that a separate mailbox that gets reviewed or checked once a day, just to verify and see what’s going on. It gives you that ability to engage with your staff, see what they’re seeing, identify what’s being reported, what’s being sent, and maybe what’s not being reported.
This is something KnowBe4does really well, and I’m sure that there’s other tools available from other vendors that have a similar style. If you’re just getting started and you don’t have a way to programmatically do this, the ability to forward as attachment is actually on that slide, right? So, you can forward a message, instruct your staff to forward an attachment, and that will preserve the message and its headers. As an IT person, you can evaluate that message, just to get a little bit more information for future investigation.
Whenever we have our clients submit that phish alert, we want to make sure that it’s suspicious for review. It’s not a way for your staff to send you all their junk mail instead of unsubscribing it, you know? It’s an educational piece, right?It’s defining (for staff,) hey, there’s spam, and it’s benign, let’s unsubscribe, let’s clean it up or mark it as junk.
If it’s suspicious and you want somebody to review it or evaluate it or report it because it may have impacted other folks, then that phishing classification is justified.
And so finally, think before you click. If you’re unsure about who an email is from, don’t click on it as links or attachments found in the message.
For those of you that are just getting started, there are lots of great free resources. Staysafeonline.org is a federal resource. I think it’s still up, but it’s a great resource for some of those security awareness trainings as you’re just getting ramped up.
If you’ve done the free stuff, maybe you need a bit more integrated tools. There’s a lot of different security awareness training platforms out there that will help automate and streamline a lot of these processes.
As you’re reflecting on your own program and all the stuff, I would just encourage you to do one more thing, right? If you are in a category, where maybe you’re annually doing training, maybe be more intentional about giving your staff a way to report suspicious messages to IT.
If you already have KnowBe4, using that official or button can be great.
If you’ve already got that in place and you’re only doing monthly or annual training, I really think that quarterly cadence is probably a good next step, it’s our minimum, right? The quarterly cadence just to get in a rhythm of reviewing, evaluating, and learning new stuff.
If you’ve already done that, start a monthly newsletter, maybe a staff meeting moment for IT, that can be a great way to get engaged or go all the way up to doing monthly trainings that really are in line with your organization’s culture. Maybe it’s fun games, maybe you want to use the mini-series option, which is in KnowBe4, which is a surprisingly fun thing that we’re getting feedback on.
But again, I would just encourage whatever you’re doing right now, look at taking one more advanced step or maybe two to get more engagement with your staff and more fully embrace the security awareness training platform at your organization.
Carolyn Woodard: To learn more about Community IT’s cybersecurity offerings and schedule time to talk with Matt for a free assessment or just to ask him more of your questions, please go to communityit.com/cybersecurity and you’ll find more information there. We also have a lot of cybersecurity resources on our website, including a free download Cybersecurity Playbook for Nonprofits that talks more about how we think about cybersecurity and where staff training fits in your cybersecurity strategic planning.
Q&A
We had a couple of questions.
Compliance Requirements for Nonprofits
One that I thought was maybe we could get to is that from a compliance point of view, are there specific legal requirements for nonprofits, compared to banks, healthcare, insurance companies which all have very specific compliance that they have to go through? Do nonprofits have anything like that in the United States?
Matt Eshleman: I mean, probably the short answer is no, although we are starting to see more compliance requirements come through the financial audit aspect. So, if any formal compliance requirement exists, it’s going to be coming through that angle right now.
Carolyn Woodard: Here is a podcast that we did not very long ago on that new auditing requirement. It’s called SAS 145. So, you can find out a lot more about it there.
Matt, we have a couple more questions.
Using VPNs Securely
One was about VPNs. We are an orchestra. We use a VPN when logging into our ticketing software, which also processes credit cards. Our other process is to use Square whenever we’re at a concert. So people, I guess, can buy the ticket right there.
So, which is better? Do they have to choose or does that sound like a pretty good setup?
Matt Eshleman: I mean, I think that sounds like a good setup. I think with credit cards now you get into what’s called PCI compliance. One of the aspects of PCI compliance is that basically any interaction with the card data holder environment needs to come under additional scrutiny.
Using a VPN may be a way to funnel down which systems need to be scanned or help to meet some of that PCI requirements. As with all things PCI, consult your own policy and legal guidance for that. But again, certainly with some of those security standards, that could be a good use case for the use of a VPN.
Again, I would just make sure that if you are using a VPN, it’s not a consumer grade product, because that can bounce you around and just make it complicated to monitor. You want a business class system, maybe you’re buying a dedicated IP that’s always assigned to your organization. That can be an effective way to clearly articulate that traffic from this address, this IP, that’s valid going to these systems.
Carolyn Woodard: That sounds good, especially where there’s money involved in people’s credit card information.
How to Report Junk Mail Vs Unsubscribing
We have another question that asks, it’s always best to report as junk instead of unsubscribing, correct? When you unsubscribe, can that lead to a connection to a scammer?
Matt Eshleman: I know that this goes back and forth and some of the guidance is don’t unsubscribe. That just confirms the bad guys.
I will say, I mean, our experience has been in general, if you’re receiving, I don’t know, legitimate spam, and in most cases, right, it’s that you signed up for something a long time ago and you forgot about it. I mean, my experience has been pretty good that clicking the unsubscribe button within a message does in fact, remove my address from those lists.
If you’re getting something that seems extremely scammy, like misspelled Viagra ads, maybe that unsubscribe is not going to work. But if you’re getting marketing newsletters for stuff that you’re not really interested or relevant anymore, the unsubscribe stuff, I think, works fairly well there.
I mean, I know on the other side, sending newsletters, the bar is pretty high to make sure that the tools that we’re using include a valid and active unsubscribe process. If you’re receiving mail from HubSpot, MailChimp, all those big mail services, those unsubscribe processes are going to work and be effective.
Carolyn Woodard: Yeah, those are required by law in the United States, at least, that you have to be allowed to unsubscribe. It has to be pretty easy and obvious. I would say also that if you do try to unsubscribe from something and it turns out not to be a real unsubscribe, the block button is your friend. You can block that address and then if you get more that are associated with it, just go ahead and block those too because now you know.
Training Templates for Staff Training
Someone says, where can I find information to use as training materials for staff? Do we have training templates that clients use?
That resource that we gave earlier, the Stay Safe Online, do they have any information on training or do you have any free resources that might be? We do not have any on our website, so I’m just wondering if there’s somewhere else that people can find those sorts of things.
Matt Eshleman: Yeah, I mean, Stay Safe Online, that’s the National Cybersecurity Alliance, has some good foundational resources to help you get started. I think that’s a great place.
Techsoup.org. I’m not sure if it’s free anymore, but I did a two-part Security Awareness Training course for them that was free for quite a while. But again, there could be some additional free resources there.
I think if you use Google Searching, you’re going to find free resources to get started.
I think the benefit of getting a Security Awareness Training platform is that it ends up automating a lot of that, and it’s not going to be relatively that expensive to do. Even if you have no money at all, there’s free resources out there.
But again, getting Security Awareness Training automated plan is again, a pretty affordable thing in the grand scheme of things.
Carolyn Woodard: Yeah. Now that makes sense. We have another question.
Can KnowBe4 Send Test Text Messages
KnowBe4 can perform testing with the email attachment, there’s URLs, QR codes. I believe the question is, can KnowBe4 send a test SMS message to see if they can get people to click on it and then give them the training?
Matt Eshleman: No, not anymore. They actually used to have it as a module. You could load up all these, vishing or voicemail, they would call or text messaging.
But they actually don’t or can’t do that anymore. There are some FCC regulations about unsolicited texting. So KnowBe4 is a company that follows the rules, they don’t (text anymore.) I know that we’ve worked with some specific pen testers that will build some custom stuff and do it. But in terms of whatever commercial off the shelf, security awareness training tools, I think that’s one thing that isn’t really available anymore because of some of the other federal regulations about communication standards.
Carolyn Woodard: So, you can just do those micro trainings on, “if you were to get this kind of text to your phone, this is how you would handle it to click on it.”
Where to Get the Presentation?
Eric is asking, where can I find the presentation? So, this has been recorded and it will be a video available on our website.
I also put it out as a podcast, so there will be a transcript from that. And then the transcript I will also put up within about a week usually. It takes a little bit longer to get the transcript up, but the video should be up within a day or two. All of our webinars are available there. There’s no paywall. You don’t have to sign in or anything.
We really believe that helping our community have these resources and you can search for all different topics. There’s a ton of cybersecurity stuff there, but there’s also webinars on leadership. We’re doing this one on Microsoft versus Google Workspace.
So just have a look at our resources and hopefully that can help you. Okay, we have one more question. I think this will be the last one.
Are Soft Phones (VOIP) Secure?
What about the use of soft phones that are installed on a laptop but need connection to the PC to manage calls? Is that a voice over IP thing?
Matt Eshleman: I’m not sure. I know a while ago, especially the receptionist phones, some of the soft phone software was kind of antiquated. We had to maintain several older versions of Java to support the local attendant console. But hopefully, I mean, there’s lots of great cloud-based solutions that can do all of that in a secure manner.
Carolyn Woodard: So, I would guess if you’re using an official voice mail system for your voice over IP for your organization, that they would have security built in because they’re a vendor and you’re subscribed. But it would be something maybe to look at that vendor and just ask them about the security or if there are vulnerabilities.
So, I think that’s it. Thank you so much, Matt, for your time. Thanks for staying on a minute or two later. Thanks for everybody who stayed with us for an extra few minutes to get these questions in. And as I said, they will be in the transcript.
Learning Objectives
I’m going to go ahead and go over our learning objectives quickly. We went over the cybersecurity landscape and framework, why it’s so important, the importance of training, and then we gave a couple of examples of training and practice.
Next Webinar
I want to make sure to mention that next month, we are going to be answering this perpetual question of whether Microsoft or Google Workspace is a better platform for nonprofits. If you are going to start a nonprofit from scratch tomorrow, which should you choose? What are reasons to switch platforms? Can you manage a hybrid of the two platforms together, or is that a recipe for disaster?
Join us next month on March 19th at 3 p.m. Eastern, noon Pacific, when our CEO, Johan Hammerstrom, and our Director of IT Consulting, Steve Longenecker, are going to draw on their experience to talk about these two platforms. And you can register for that now on our website.
And Matt, thank you so much for making us smarter today about training. We really do believe that your staff are your eyes and ears. They’re the ones that are going to be the first to be attacked in this way with phishing emails or these other kinds of social engineering scams. So, making sure that they know what to do is really a very basic thing that you can do. And it doesn’t have to be expensive, but it does have to be intentional. You have to have leadership involved and really make that a learning environment, not punitive “you’re going to get in trouble,” that sort of thing. Trying to get everybody on the same page to protect your organization, I think, would be our overall tips.
And then we really just like this tool that we like to manage. It’s called KnowBe4, but there are other tools out there. So Matt, thank you so much again for your time today.
Matt Eshleman: Great. Thank you.
Carolyn Woodard: Thank you, everyone.
