What IT policies do you need? What are the best ways to create them? How do you roll them out to all staff?
View Video
Listen to Podcast
In pt 1 Jeff and Nura explain and define the basic essential policies and discuss the process to create or revise them. In pt 2 they delve into implementation and roll out, common barriers to starting or completing the project, and take audience questions. In the bonus podcast pt 3 (including transcript), they explore more on the topics of roll out and barriers to successfully implementing new policies, in more depth than they had time for in the webinar.
Want to skip right to our blog post of free resources on free templates and frameworks for creating IT Policies for nonprofits?
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Community IT Senior Consultant Nura Aboki and guest Jeff Gibson from Build Consulting took your questions on where to find nonprofit IT policy templates, how to overcome barriers and modify the templates to your organizational needs and strategic goals, and how to get the stakeholders on board and roll out training on the new policies to all staff.
If you are feeling paralyzed about starting this project to create or revise your policies, this discussion will give you a roadmap on how to move forward. Learn about making IT governance work for your nonprofit.
Is your nonprofit protected?
In our work with clients over the twenty years we have been providing outsourced IT services, Community IT has frequently run into clients with no Acceptable Use Policy at all. In addition to protecting your organization from employee misuse of equipment, IT governance policies are strategic documents that need regular review to stay in alignment with your nonprofit’s goals and tactics.
If your organization has no IT governance documents or they haven’t been updated in a while, this webinar teaches how and where to start creating these vital documents. Our panelists also shared their experiences and successful strategies to roll out these policies to all staff, and gave ideas on updating your training on these policies to be fun and engaging. The key takeaway? Collaborating: the IT department needs to work with other teams to incorporate various needs and insights.
Your organization’s protection from cyber crime and multiple legal issues rests on your staff understanding and following your IT policies. Don’t get caught without policies you can rely on and refer back to when situations with cyber attacks or disgruntled employees arise.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT and Build Consulting are proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community.
Presenters:

Nura is a Senior Consultant at Community IT. In that role, he proactively oversees technology infrastructure for select clients, providing strategic IT advice, recommending IT solutions and solution design to meet business objectives, and then overseeing solution implementations. Nura provides leadership and guidance for strategic planning and solutions architecting with clients who have sophisticated technical and business requirements. He gathers core business, technical and IT service management requirements through a variety of activities including key stakeholder interviews, document review and technical assessments.
Nura started his career at Community IT as a Network Administrator. In 2012, he was promoted to Network Engineer and assumed a supervisory role in IT service operations, then became an IT Business Manager, where he has guided some of our largest clients through complex implementation of effective technology investments and utilizing efficient IT services in direct support of their missions. He has a lot of experience in making IT governance work for your nonprofit.
Prior to joining Community IT Innovators, Nura served as a member of the technical support team at George Washington University and held a Network Specialist role at the Economic Community of West African States (ECOWAS) Parliament in Abuja, Nigeria. Nura holds a Bachelor of Science in Computer Engineering and Master of Science in Electrical Engineering, both from George Washington University.

With over 25 years of experience, Jeff Gibson has led key initiatives in various sectors, including non-profits, government, startups, and in corporate settings. He has a proven track record of improving operations and managing costs to support growth in both large organizations and small enterprises.
Build Consulting only works with nonprofits, foundations, associations, and higher education organizations, bringing unmatched experience leading nonprofit technology transformation to their clients. Working with nonprofit organizations is their exclusive focus and over the years their team members have performed assessments and created technology roadmaps for more than 500 local, national, and global nonprofit organizations.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She was happy to moderate this webinar and learn more on making IT governance work for your nonprofit.
Transcription
This transcript covers the webinar material from podcast parts 1 & 2. Find the transcript from the podcast pt 3 here.
Carolyn Woodard: Welcome, everyone, to the Community IT webinar. This one is Making IT Governance Work for Your Nonprofit. Today we’re going to be addressing some questions that seem fairly simple:
- What IT policies do you need and what are the best ways to create them?
- How do you roll them out to staff?
- Are there barriers that are keeping you from doing this project?
We know that if creating or updating these policies were simple, we wouldn’t have to have this panel discussion today with our experts. We would already have our policies.
So if you are feeling paralyzed about starting the project to create or revise your policy, our experts today are going to
- take questions on where to find nonprofit IT policy templates,
- how to overcome these barriers
- and modify the templates to your organizational needs and your strategic goals,
- and how to get your stakeholders on board
- and roll out training on new policies to all of your staff.
My name is Carolyn Woodard. I’m the Outreach Director for Community IT and the moderator today. I’m very happy to hear from our guest speakers, Jeff Gibson from Build Consulting and Nura Aboki from Community IT.
But first, I’m going to go over our learning objectives today.
Learning Objectives
By the end of today, we hope you’ll be able to:
- Discuss essential IT policy documentation for nonprofits and what should be prioritized.
- Learn how to create or update these IT governance policies and we’re going to share templates.
- Learn tactics and strategies to roll out policies to all of your staff and understand barriers to implementing IT governance and how to overcome those barriers.
Presenters
So now I’d like to turn it over to our panel to introduce themselves. Jeff, would you like to go first and also tell us about Build Consulting?
Jeff Gibson: Absolutely. Hi, I’m Jeff Gibson. I’m with Build Consulting.
I’ve spent about the last 25 years in the nonprofit and private sector, focusing primarily on analytics and implementing those results into an operational model that’s manageable. Trying to take the theory out of things like governance and putting them into practical applications. Build Consulting is a consultancy focused exclusively on nonprofits, and we are highly agnostic to vendors or other partnerships.
We focus on the strategy and the sort of approach to technology, project leadership, change management. We tend to focus on the situation rather than the technology and managing change management from an organizational perspective, and then relating it to the technology itself.
We have a large variety of consultants with very diverse subject matter expertise, and we can pretty much find someone that has a deeper knowledge base for any problem you might run into.
I’m happy to be here, by the way.
Carolyn Woodard: Oh, I’m so glad you’re here too, Jeff. This is the first time for Jeff on the webinar, but hopefully not the last. Yes, I think we did a webinar with Build a while back, and something struck me that you often say, which is the technology decision should be last. When you’re thinking about the problem you’re trying to solve, there’s a whole bunch of work that comes first before you choose which platform or tool you’re going to go with. And I just love that approach.
Nura, would you like to introduce yourself?
Nura Aboki: Hi, I’m Nuradeen Aboki, Community IT Consultant. I’ve been at Community IT for about 15 years helping clients with their IT management strategies, IT planning, budgeting, IT road mapping of their network infrastructure, as well as working on developing IT policies for our nonprofit clients.
Over the past 15 years, I’ve seen quite an evolution in the management of IT infrastructure from on-premises to the cloud. So I’m really excited here to talk about governance, IT governance in general, and how it’s been quite interesting watching our clients over the past 15 years.
Carolyn Woodard: Yes, I feel like we’ve said for maybe a couple of years now that we should do a webinar on governance, because we always say governance is so important. And those policies are the bedrock of what you’re going to do with IT. But I’m really happy that we’re finally doing it.
Before we begin, if you’re not familiar with Community IT, I’m going to tell you a little bit about us. We are a 100% employee-owned managed services provider. We provide outsourced IT support exclusively to nonprofit organizations.
And our mission is to help nonprofits accomplish their missions through the effective use of technology. We are big fans of what well-managed IT can do for your nonprofit. We serve nonprofits across the United States.
We’ve been doing this for over 20 years. And we are technology experts who are consistently given the MSP 501 recognition for being a top MSP. And that’s an honor we received again in 2023.
I want to remind everyone, for these presentations Community IT is vendor agnostic. So we only make recommendations to our clients and only based on their specific business needs. We never try to get a client into a product because we get an incentive or benefit from that. But we do consider ourselves a best of breed IT provider. It’s our job to know the landscape, the tools that are available, reputable and widely used, and we make recommendations on that basis for our clients based on their business needs, priorities and budget.
Poll 1: Does Your Organization Have an Acceptable Use Policy?
And now we would like to go on to our first poll.
Does your organization have an acceptable use policy?
And the options to answer are:
- Yes, and we know how to use it.
- Yes, but we don’t really use it.
- Not sure.
- Not applicable or other.
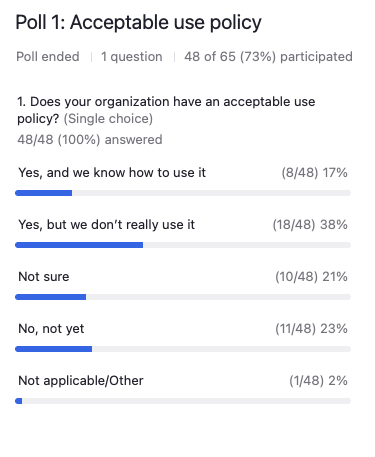
So we know we have lots of different people on the presentation from different types of nonprofits, large ones, small ones.
Nura, can you see the answer?
Nura Aboki: Yes, about 38% said they have it, but they don’t really use it. And about, let’s say, 23% said, not yet. So there seems to be organizations that wanted to start.
Some are not sure. Then followed by the ones that have it, and we know how to use it, which is quite impressive. Eight people responded to that. And then lastly, one person said it’s not applicable or other.
Carolyn Woodard: Thank you, everyone, for sharing that with us. There’s no shame, right? You’re in the right place.
If you don’t have one or you’re not sure, that’s what this webinar is about.
Essential IT Policies at Nonprofits
So our first topic is to explain what are the essential IT policy documents nonprofits need to have? And why? What are the priorities if you have to start with one before the other?
Want to skip right to our blog post of free resources on free templates and frameworks for creating IT Policies for nonprofits?
So Jeff, would you like to weigh in on some of these policies?
Jeff Gibson: Absolutely. The biggest ones are the obvious ones, disaster recovery and data retention.Those are becoming obvious, but there may be something in particular to your type of organization that you have to prioritize other things.
AI also, depending on the usage internally, could be promoted to the top of that list depending on what your situation is.
Data retention probably is the newest leader in that game because of the lowered cost of lower point of entry for AI tools and malicious actors. Data repositories tend to make a pretty big target for a malicious actor, but it is particularly your organization. But the obvious ones, I think, are data security and the overall organizational disaster recovery.
Carolyn Woodard: Nura, I know we often say that an acceptable use policy that we just asked about is one of the bedrock policies that you should have. Can you talk a little bit about what that is for anyone who doesn’t know?
Nura Aboki: Yeah, it is the foundation of most IT organizations’ IT policy. Acceptable use is their foundation policy, a basic policy that governs what staff is allowed to do and not allowed to do with their devices and software. And it usually defines the use of equipment, computing services and lays out security expectations.
Organizations are thinking of IT policy, thinking it may be challenging or they don’t have resources.
One quick one to actually roll out, and there are several templates out there. I know resources can be shared during this webinar for the acceptable use policy. It’s one way to start because that’s the policy that impacts the staff most immediately.
If you provide devices to them, then they need to know what to do with those devices. The applications that they use at work, they need to know the applications for productivity and if there’s any room for other applications, or maybe it’s quite strict and there’s no room to use any other application.
That is the one that we call the bedrock, it’s definitely foundational for all organizations. Along with that, there is BYOD or Bring Your Own Device. Some organizations allow for staff to bring their own device to work and having a policy around the use of that BYOD device and applications can go alongside with the acceptable use policy.
Process to Create or Update IT Governance Policies at Nonprofits
Carolyn Woodard: I want to move on to the process.
We just published a blog post about a bunch of different types of policies and links to some templates that you can use, including some that are on our site and examples. That website address is communityit.com/governance.
But once you know that you need an acceptable use policy, for example, or disaster recovery policy or data retention policy, what’s the process?
How do you identify the stakeholders and make them part of the process? Is your policy strategic? Is it tactical? And how do you create an implementation plan? And if you already have a policy, are there different steps that you might take?
I’m going to turn it over to you, Jeff. Do you want to talk a little bit about being successful at a process to develop or revise your policies?
Identify Stakeholders and Get Buy-In
Jeff Gibson: The easy identification would be any group that holds, uses or retains data. Whether that’s end user data, customer data, constituent data, those folks have to have a meaningful bit of input into how data is stored and accessed and what data they need to have access to and what data can be manipulated.
They also need to, if possible, get buy-in and sign-off on your draft policies, especially the data retention policies.
One that gets forgotten a lot is data sharing policies. What do different departments share with outside vendors that frequently gets lost in the shuffle?
And really, an organization that does share a fair amount of user data, constituent data for outside vendor analytics or whatever, they really need to craft at least a policy for the vendor to sign once they’ve been thoroughly vetted on data destruction, data sharing with their particular partners, etc. That one gets missed a lot, but it’s critical because once that data leaves your organization, you have no control over what occurs with it.
I saw in some of the questions that came in before the webinar question how to get buy-in.
Of course, getting buy-in from leadership is one of the toughest things to do and getting leadership to prioritize your ever-shrinking timeframes to actually craft these policies. One trick I’ve used in the past is through risk analysis, putting it into terms non-technical leadership will understand, GDPR (General Data Protection Regulation) is a great example. The first fine associated with GDPR violation could be as much as $40,000, and most organizations can’t take that hit.
And those are per-incident fines. So, framing it like that rather than giving a technical explanation, or here’s the risk to the organization, here’s the financial risk, here’s the risk to our continued operations. Those are good ways to get buy-in.
And then once you do garner that buy-in, or even if it’s partial, always encourage the leadership to be consistent and persistent in their messaging to the larger staff.
Three months into this project, they’re going to need that refresher like, hey, VP X is very into this and we have to do this for the security of the organization. So we need you to prioritize this within your own department, your own team, or within your own timeline.
It’s never easy, but again, frame it in a way that non-technical folks will understand.
Carolyn Woodard: That’s great advice.
Form the Policy Team
Nura, can you talk a little bit more about forming that team? Do you always need to have someone from the executive team as part of the leadership driving the process forward to create the policy or revise it?
Nura Aboki: Yeah, I think it’s important to have an executive in terms of stakeholders, management team, executive team, and also the board. If you have a board, you could have an executive or governance committee in the board, and that governance committee could have influence to effectively convince the executive team to work on this, making it a priority.
So I like Jeff’s tactics and approach with using the risks analysis to get buy-in. As well as getting stakeholders from across the organization so you can have a spectrum of perspective. You want your policy to be as holistic as possible.
Taking a few steps back, more and more we have seen the need arising from cyber liability insuranceapplications. If you want to get coverage, you have to have certain policies in place.
More importantly for non-profit organizations, some funders require certain IT policies and IT governance policies to be in place. Those are key drivers of convincing the executive team to actually create the time to make this a priority.
Carolyn Woodard: Thank you so much for that.
Strategy Vs Tactics – IT Policies
I want to get into strategic or tactical policies and if that impacts who needs to be involved leading the process. So I suppose a more tactical policy might be some of the things you were talking about, Jeff, around the vendor, like you needing to interact with the vendor in a certain way.
So having to have a policy around that versus perhaps the acceptable use policy is a more strategic high level. This is kind of a blanket policy of how we’re going to go forward. Jeff, do you have some more ideas on a process when it is a tactical policy need of how to get those stakeholders engaged?
It might be per vendor or per platform. Is that true?
Jeff Gibson: Yeah, part of it. I would almost argue that every policy needs to be tactical in some respect, because one thing that does get short shrift is we made this policy. It’s beautiful. We already signed off on it. It was a lot of work, but we’re all happy we got it done and then it becomes shelfware.
How do we implement these policies? The users who need to execute or escalate on a policy infringement, what do they do next? What are their next steps?
I ran operations for the last 20 years and you’d be surprised no matter how much we craft the DR (Disaster Recovery) policy, the actual execution, the first three-hour execution, that’s critical to the success or failure of your plan. But a lot of folks don’t get trained on it even within IT organizations.
With something like GDPR, you have 72 hours to resolve the issue. If the person in your development department doesn’t know anything about GDPR or our process, that could be a problem.
The strategic stuff can be prioritized based on the strategic plan of the organization and you can weight things within your prioritization process for projects, et cetera. But on the tactical front, especially things like COVID, things like changes in legislation, CCPA or the California Privacy Act, those have forced a lot of these things to be of greater import. Formerly back burner, relatively safe back burner policy issues are now at the forefront because of right to be forgotten laws across the globe.
Turning it into tactical, with leadership, you have to have that conversation that tactical resources need to be applied to this and Project X is now suddenly very important because of state, local, federal compliance issues or a new compliance issue related to our industry or our space.
Therefore, explaining to leadership, not only here’s why we have that buy-in, here are the urgent issues, but then also what’s not going to be done. And then managing those expectations that there are. Again, every organization I’ve ever been in, especially in the nonprofit space, is just taxed for time and resources.
There’s a finite amount of work in the week if you want to keep your staff. Strategically measuring tactical problems is more of an art than a science, but there are some tools to help you do that.
Carolyn Woodard: Thank you.
Updating IT Governance Policies Vs Starting From Scratch
I want to get back to this question also that some places may already have a policy, but it’s really outdated. Maybe they haven’t updated it since people were working remotely or since everything was in the cloud or since the advent of AI.
Is it easier, Nura, to update an existing policy or do you recommend that they just start over, start from scratch? What’s better?
Nura Aboki: Well, a review of the existing policy might be easier, given that they have somewhere to start. But, there are several templates out there. So even if you don’t have one, you can reach out to partners, vendors, to get samples of templates that you can work with.
But if you have an existing policy, you will need to determine whether a change is required in your organization. This is where the assessment comes into play. If you have an assessment done, you may notice transformation in technology has happened and where your outdated policies need to change.
So it needs to be reworded to cover the new technologies that you’re currently using, or even some regulatory requirements that have come about, given the changes that the world or your environment has gone through, your organization needs.
Then there’s another question about this. When you’re updating this IT policy, you really want to also focus on the communication.
How are you going to make sure you communicate the changes to the policies to all your employees and provide necessary training to them? And then periodically, you need to have a way to regularly check for any compliance with the policy and address any issues or violations that may come about.
Carolyn Woodard: That’s right. One of the reasons you have a policy is so if an employee does something that’s against what the policy says, you have some standing there.
Can IT Policies Build In Some Flexibility?
How do you create IT policies that allow for flexibility as IT continues to rapidly evolve, especially as Gen Z is joining the workforce?
I have a quick little anecdote on that. I was at a conference and a bunch of people my age were sitting around saying, oh, we don’t need an AI policy because we’ve just told people they can’t use it. And I asked, are you never going to hire anyone ever again? Because I guarantee every 20-year-old coming in to work at your organization will be using AI for practically everything.
So do you have advice, Nura or Jeff, on making policies that can be flexible? Is it just a matter of revising them often enough?
Jeff Gibson: I think it simply comes down to that. It’s not very clever, but literally putting time on a yearly or bi-yearly basis or quarterly, depending on how rampant change is in your organization. But yeah, something like AI is the perfect example.
If you have a timed quarterly or bi-annually review of certain documents, that’s the best way to just block off that time. I’m talking at a very logistical level here, but with the hustle bustle of every day and ever-shifting priorities, knowing that there’s a time where these five stakeholders get together and say, has anything changed since our last meeting? And documenting those changes.
Nura talked about it a little bit earlier. I started life as a tech writer. Having a section at the tail end of a document with significant changes, version controls, revisions in the document just to archive those changes. And then also making sure that maybe new groups need to be involved, if you have a new department that’s utilizing something like AI.
And then the other thing from the IT leadership perspective is you have to have an awareness. You have to have an awareness of everything new going on and imagining ways in which departments you don’t oversee could potentially be backdooring things like AI tools into the environment.
And also not just your policies, but updating your trainings as well and maybe calling new training. If you’re on a schedule of yearly IT training that gives everybody 15 minutes and they have to take a CBT or something, that’s one thing. But specialized, focused training on emerging trends or changes to the workspace that you exist in, you have to have that in your tool bag and don’t be afraid to have a training specifically associated with a significant change in the workplace.
Carolyn Woodard: That makes sense. I think that’s another way to get people’s attention. If there’s something new and exciting like AI, you can invite them to a meeting about it and then work in the policy as well. Here’s what our rules are going to be and here’s how you can help contribute, etc.
Poll 2: What Is Your Organization’s Communication Style?
I’m going to move on to our next poll which is communication style.
You could have an organization in communication style that’s
- Top-down, that you like to have rules to follow.
- You might be a more entrepreneurial or collaborative organization.
- It might be small team-based where you need consensus or just your culture. Consensus is very important for you. Everybody is on the same page.
- It could be only you at your nonprofit. So in that case, your communication style is to yourself.
- Other communication styles, there’s a whole bunch of other ones. I just chose some of the bigger ones.
There’s no judgment, styles are styles. No one of these styles is better than the other or more effective.
I think the most important thing about knowing your communication style at your organization is self-awareness. Knowing the communication style helps you communicate in ways that are effective, following your regular process.
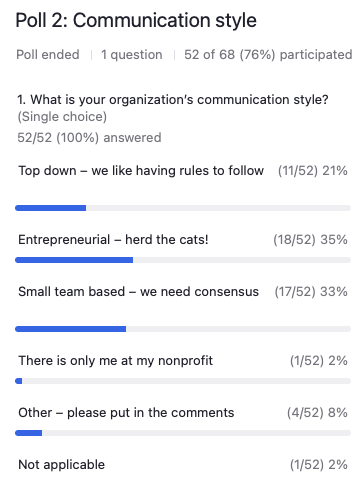
If you’re a top-down, liking to have rules, then you don’t want to throw that out of whack with having a collaboration and having everybody come together and put their say in.
Jeff Gibson: Top-downs, 21%. Entrepreneurial, 35%. Small team-based, 33%.
There is only me at my nonprofit, 2%. And 8% for other and 2% for non-applicable.
Carolyn Woodard: Great, someone did put in the chat their different styles. “A fractal messaging process, updating the higher level folks so they understand and can support their direct reports and then we update all of the staff.” That’s an interesting strategy.
“We’re moving from entrepreneurial and small team to more top-down.” Good luck with the change management. That can be tricky.
“We like rules, but herding cats is how we operate.”
And “We’re in a period of growth and looking at policies across the board.” That’s very clever to do that for sure.
And “A combination.” I think with most people and organizations, there’s a combination. And sometimes it depends on the person, right?
Rolling Out the Policies
How do you roll out policies to new and existing staff? We have some ideas here.
You can work with HR for new hires and at performance review opportunities. I think a lot of us are familiar with how you get the HR employee handbook on the first day or the first week of work and it has the acceptable use policy in there and probably a bunch of other policies, whether or not you can absorb it at that time.
So working with HR to make sure that those policies are re-rolled out periodically. What’s effective to roll out to existing staff and are there tactics that work?
So Nura, would you like to take a first try at this?
Nura Aboki: Yeah, sure. Thank you. Part of the rollout process is to initially get the stakeholders to agree on the implementation of the policy itself.
We have agreed that we are going to do, for instance, an acceptable use policy. We’ve agreed on the final version. Now it’s time to roll it out.
Then having a launch plan is something that an organization should have in place. That launch plan will
- outline the roles and timetable.
- Also this needs to be circulated to all the parties that are involved for agreement. The role players need to know and the timetable to actually go for launch.
Then the one key important thing is to have a communication plan because as you’ve seen, a variety of organizations have different modes of communicating with their staff and different channels. So usually an organization should use the appropriate channels, messaging to make sure that everyone that is part of this policy has received the policy or will be receiving the policy appropriately.
And there needs to also be leadership involvement, since we agreed that the stakeholder participation should include leadership.
Leading by example is going to be a key way to get this roll out possible. Setting up positive examples for employees to demonstrate compliance with the organization IT practices or policy, giving those examples will show that this policy could work. I can see myself complying with this policy. It’s not just one way – the policy here is the policy, follow it – but having a conversation about how this policy actually helps with the mission of the organization.
And then setting milestones to communicate the IT policy and just to make sure people are not overwhelmed. So if you put a milestone, you can basically just track all those milestones in the plan. That way, it’s not too many changes at once.
Make sure each policy is rolled out timely, appropriately, making sure people have the bandwidth to receive it well.
And also ask questions and provide feedback that way you can kind of measure the success of the IT rollout policy.
I know that Jeff mentioned something about leveraging trends. You want to have a protocol to ensure that you’re encouraging people to follow the compliance that is outlined in the IT policy. So if there is any new advancement in technology, you want to make sure that after a review of the policy, you go back to your communication plan.
You also think of examples that you can share to motivate people, but maybe the adoption of a new AI, acceptable use policy, for instance.
So that kind of continuous improvement and continuous review is going to be helpful in having the rollout be successful.
I would add just two more points here.
- Explaining the importance and the significance of the IT policy, just making sure it is thoroughly explained that there is no chance for misinterpretation and people understand what they are signing up for.
- Make sure it’s distributed, accessible. It’s not buried in a handbook somewhere.
Make sure it’s readily available, accessible, and put it in as part of your commitment to ensuring that these IT policies are clearly explained to staff, either in all staff meetings periodically, or referenced at least once a year, so people are aware. They easily can get forgotten because of other priorities that the organization may have. So those are the steps that would summarize.
Roll-Out Strategies for IT Policy at Nonprofits
Carolyn Woodard: Thank you. There was a great comment in the chat from Michelle, who says that with IT policy changes, we roll out to the operations team first because that team is the most tech savvy and the least change adverse. So it seems like they get their champions, the people that are going to be most excited and least frightened by the change first, and they help them work out the kinks.
Once we work out the kinks, we put together documentation and roll out to all staff. And then she says she also puts a couple of preemptive 15-minute meetings on the calendar for folks who need more assistance. So that’s really smart and strategic to identify the people that will be the most resistant and give them that extra help to understand the new policy.
And sometimes with the new policy, really, you don’t have to change anything. You have to know it, but you don’t have to change what you’re doing. But if there are changes that are going to have to happen, make sure that you give them that extra hand holding. Thank you, Michelle, for that comment.
Jeff, do you have other examples of ways that you can roll this out? And is it different getting the attention of new staff and getting the attention of existing staff? Do you have different strategies?
Jeff Gibson: I do. Back to an earlier point that was made, is calendaring the change. This is tough for organizations, but use as much sway as you have on HR to have a yearly review with all necessary people in that review of the employee handbook.
And then the other thing that I always want to consider at that level is, are there discipline-specific or subject matter expertise policies that need to be reviewed? Acknowledge that they are reviewed in terms of if you have a database administrator, that’s a much more buttoned up policy adherence than data handling than your average staff member is.
Does the financial department need to have more in-depth training on financial handling, vendor management, et cetera? The policies page on an intranet is a great idea, because it’s all in one place. You can set a reminder, review that, and you get folks in the habit of going there.
And then especially for new employees, you don’t remember much from that first couple of days. So it’s a place for your new employees to refer to and they know they can look at it when they have a chance to take a breath.
If you have an HRIS (Human Resource Information System) system or your cyber provider may have plugins for training on certain policies, then you can also end up negotiating. If I get 90% of my staff to review this CBT (Computer Based Training) with a successful passage of it, can I get some money knocked off of my cyber insurance? I’ve used that several times to where if they know your staff is well-trained and there are policies in place, they will give you a reduction.
I’m not guaranteeing it, but at least it’s a place to start negotiating. And then if it’s CBT-based, you can also focus even deeper on, maybe some folks didn’t do well on the CBTs, they’ve scored under an acceptable margin. Then that’s the time to target them for focused in-person training, one-on-one training because these folks are usually in critical roles and some of these processes and policies require 100% compliance for the success of the organization.
A lot of organizations will have something in their HR management system, or an outside third-party vendor can come in and there’s a subscription and you can kind of dictate what trainings you want and ones that you can customize.
And they’re usually fairly affordable. I know money’s tight everywhere, but it’s a really good way to get a handle on your overall organization with some data behind it and let you target where you need to train or communicate better or what departments need more specialized training.
Overcoming Barriers
Carolyn Woodard: Nura, would you like to talk about some of the biggest barriers to creating these governance policies?
Nura Aboki: One of the main ones we’ve seen is prioritization. Oftentimes, an organization, especially nonprofit organizations, are focused on their mission and they just want to achieve their mission. And that takes priority over spending the resources and time on IT governance or IT policies.
Another aspect of this is just the lack of resources or limited resources. Many nonprofits operate with limited resources, which can make it difficult to allocate sufficient time and personnel to IT policy development.
Also some may have a different mindset altogether, where nonprofits often focus almost exclusively on the mission and goals, which can lead to IT being overlooked and undervalued.
So those are some of the factors. But there are ways to overcome these barriers. But I want to hear from Jeff if there are more barriers that Jeff might have.
Garnering that leadership buy-in and that communication of leadership buy-in. Having your leadership communicate to the general staff is another.
And then the time.
I wish I had a magical response to the time thing. Harkening back to what we were saying earlier, you have to prioritize based on the urgent needs of the organization. And there will be times where you have to have difficult conversations with leadership and department heads and other staff, that we just can’t do X right now because this new situation caused us to refocus.
When you’re communicating things like that, it’s important to set a time frame and to stick to that time frame. Most folks will give you some grace if you have a date attached to something. You know, saying, we’ll get back to you. IT, the famous black box of information, we have to change that perspective.
And then one of the things that I learned every time I had a different assignment, or a different job is you have to break out of the IT barrier. “We’ll call you if something horrible happens. Otherwise, you know, you don’t need to talk to us, we won’t bother you.”
But IT has to be outward-facing and communicative. Really speaking to users about their respective concerns and what you’re doing as an IT organization will help them, ease their job, secure their job, improve the success rate of whatever the discipline they’re executing on.
IT just generally has to get outside of being looked at as the plumber. IT has to be looked at as an enabler, you know, especially given how invasive technology has become, even in the last 10 years, much less five years.
There’s not many organizations or groups within an organization that aren’t impacted by IT. And they have to be informed on how to use that IT to enable and better their mission, but also sort of the risks that are associated with these new, very powerful tools. AI is a perfect example.
And then the timing is critical. It’s much harder to limit usage to non-IT teams of a new tool if it’s already on their PC. You need to have that just-in-time sort of approach of policy training.
Get the policy there before the tool is sitting on the finance guy’s desk who is playing around with AI. He has no idea if it’s a public LLM (Large Language Model) or a private one or whatever, or the risk to the organization associated with just putting up organizational IP out into the greater model.
Some of it’s just diligence, sticking with leadership, explaining to them on their level, explaining risks of not refocusing the rest of the staff on behaviors.
Carolyn Woodard: I think you hit on something that I hadn’t really thought about before, about IT being outward, and making connections with some departments or teams that wouldn’t necessarily think they had an IT interest.
One example is that HR might have their own systems that are pretty walled off usually from everybody else’s, but involving them in a performance review, helping the person in that review explain that they understand the acceptable use policies or the new AI policy or whatever it is that has changed and get their buy in and collaboration. That’s a really interesting tactic.
We had someone also ask about being able to convey the risk to leadership if it’s something that’s going along, going along and not seen, not prioritized because it isn’t seen as a huge risk. Be able to communicate that to them, which is something IT often can do, especially if they’re working on the cybersecurity aspect.
Q and A
Where do we check for compliance?
For me, I was thinking something you said earlier, Nura, about you have a policy and then are the people who are under that policy complying with the policy?
If your policy is you can’t use ChatGPT, how do you know that people are and how do you manage those expectations? Do you guys have some examples or ideas?
Nura Aboki: What comes to mind are setting security controls or technical tools that would allow for enforcement of policies. So because we are vendor agnostic, if you have an email system, you have files in the cloud, some of the cloud providers will have a governance tool, for instance, that will set certain classifications for documents, sensitivity, confidentiality, and a certain group of people in the organization should only have access. If someone tries to delete or copy a file from one section of the file system to another, perhaps that could be a violation.
Tools that are monitoring the devices that people have or have been assigned, whether they are installing third-party applications. Even some of these tools prevent the installation of third-party applications and changing the configuration of the device that is issued to staff. So there are tools that allow for the enforcement of these policies that may help with compliance tracking.
Having the policy is one thing and enforcement is another challenge, but at least having a policy is a good start for your organization.
Carolyn Woodard: Especially at nonprofits because we’re very friendly, team-oriented. It can be difficult to lay down the law.
Would an IT disaster response policy normally be part of a larger organizational DR (Disaster Recovery) policy?
Jeff Gibson: Yes, absolutely. It’s integral. Outside of ensuring quick, fast enablement of communication from the organization to the outside world, the DR piece is critical. I mean, you can’t pay your people anymore if you can’t find your files anymore.
I would almost argue that DR from an IT perspective is becoming equally as important as the rest of the organization. An organization can shut down for a day or two. If an organization loses all of its data, you’re starting from scratch.
If an organization can’t pay its people, you’re really starting from scratch and you’re going to have a myriad of other issues that are going to result from that. But absolutely.
Carolyn Woodard: And it could be a non-hacking disaster. It could be a flood in your office. With everything in the cloud, it’s less likely. Although it could be internet is down on the East Coast for 24 hours, or what have you.
Jeff Gibson: There are still a frightening number of nonprofits that just don’t have the ability to finance a move to the cloud. I see a lot of on-prem systems still, a lot of backed up data on large terabyte drives, things like that.
I think it’s just a matter of having a DR policy and a DR mitigation plan on a budget. Even if you have nothing to spend, thinking it through and doing tabletop exercises, making sure documentation is available offline. It calls back to the old days, but that big three ring binder with up-to-date information, that’s always going to be sitting there.
You might not have access to a knowledge base that you’ve crafted over a decade, but a lot of the old school stuff is still out there. It’s just hard with the cost of cloud and the cost of some of the AI tools and enabling a lot of the DR stuff.
Carolyn Woodard: We did a webinar on cyber liability insurance a couple of years ago that’s still very valid and appropriate. One of the things that our guest said was to have just the phone numbers of your insurance provider and the police for when you do suffer a malware or they have encrypted everything. She had had a client where the number to call the insurance provider was encrypted, they couldn’t get it. It was very difficult for her and she said, yeah, just a piece of paper that has those important phone numbers on it is important.
Jeff Gibson: One thing to tap into is the insurance providers. Insurance providers can help and can and will help you create disaster recovery policies usually included as part of the cost of your coverage.
They don’t want you to have a cyber incident either. It’s much more expensive for them. So, they’ll hook you up with auditors, resources at their disposal that won’t cost you anything and that can really help you kind of point out the weakest parts of your plan or your organization. So don’t forget to leverage those.
Carolyn Woodard: Exactly. We’ve done a couple of webinars. You can find them on our site about disaster response and how to create those plans.
As you said, Jeff, it doesn’t have to be a very expensive exercise. It can be just your leadership team figuring out who’s going to do what in the event that something is inaccessible.
I want you each to tell me one thing that you would say to convince the board of a nonprofit of the importance of policies. So who wants to go first? You can only say one thing.
What’s the most important thing to be convincing to your stakeholders?
Jeff Gibson: It’s easy, but it literally can impact the continuation of the organization, the business. It is a business continuity concern.
You’re not overstating it when you say, this could be the end of it from a financial or a data perspective.
Nura Aboki: I agree with Jeff, and I would add the reputation of your organization at this stage.
Having good technology policies protects your organization’s data and reputation by providing clear guidance on what is acceptable and how to manage risky situations.
Carolyn Woodard: I want to jump in and say that both of you are available to take more questions. You can get in touch with us through our websites: www.buildconsulting.com for Jeff and communityit.com for Nura or myself.
Learning Objectives
I wanted to go back over our learning objectives. I hope that after this presentation, you
- understand the essential IT policy documentation for nonprofits and how to prioritize. We have a bunch of priorities, right? We have the acceptable use policy, and then also disaster recovery and data retention necessities.
- We hope that you have learned how to create or update these IT policies, and we shared some templates. I shared the link to our website where we have a bunch of other links to templates that you can use.
- Learn tactics and strategies to roll out policies to all staff. I want to thank both of our experts for sharing your experience and anecdotes and ideas on that. As you said, it’s not easy, so don’t worry that you haven’t been able to do it, but hopefully we gave you some ideas to try.
- And then of course, understanding the barriers to implementing IT governance and how to overcome those barriers.
I think when we were talking about this presentation, one thing we kept coming back to was people’s emotional response to the idea that they have to do this project, right?
You might have an intellectual understanding that this could be the end of your nonprofit, that the risks are very real, and that you need to have these policies in place. But if you put an hour aside and you start working on it, either you can’t find your old policy, or you can’t find a good template. It just seems overwhelming. And you say to yourself, well, I’m not going to do that, even though I know that I need to. So, a tactic is to overcome those kinds of emotional responses and just make small changes, make it into smaller tasks that you can do that are going to lead up to your big accomplishment.
I love your idea, Jeff, of putting stuff on the calendar, making time and just setting reminders. And then in the future, once you’ve got your policies, setting those reminders so they don’t get out of control and out of date again. Annually, quarterly, whatever works for your organization, putting that reminder on your calendar, setting those meetings and bringing the people, stakeholders back together, your leadership, to just revise them.
It’s so much easier to revise it and just say, oh, no, nothing’s changed. We’re good for another quarter. Or, this AI is really growing, and we need to incorporate that. So let’s change a couple of these other things.
Those are all such good pieces of advice.
I want to thank everyone for joining us today. We know you have a lot of other things that you want to be doing.
And Nura and Jeff, I want to thank you both so much for sharing your expertise with us today. Thank you.
Jeff Gibson: Thank you for having me.
Nura Aboki: We’re happy to be here. Thank you.
