Is your data safe? All your data?
View Video
Subscribe to our Youtube Channel here
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Data Cybersecurity for Nonprofits
Join Community IT CTO Matt Eshleman and Build Consulting Partner David Deal for a presentation on data cybersecurity for nonprofits. You may have invested in your basic cybersecurity, but how do you know if your data is as secure as it needs to be? Do you know all the tools you use that store crucial data and how that data is protected?
Explore best practices to protect data, wherever it lives,
in business applications such as ERP, CRM, Program Management, etc.
Learn new threats to watch for
Plan to enhance your data governance and security
Matt and David held a deep discussion of data security in applications such as ERP (Enterprise Resource Planning), CRM (Client Relationship Management) and other tools you use, plus some tips and strategies for data cybersecurity at nonprofits.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT and Build Consulting are proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community. In this webinar we will be sharing our advice and insights based on what we are seeing among our clients and in the community.
Presenters:

David co-founded Build Consulting in 2015, building on over 20 years of deep experience in the nonprofit technology sector. His work for Build’s clients has a broad focus spanning many operational areas including fundraising, program and case management, human resources, accounting, and many others. Internally, David leads efforts to develop and grow relationships with service partners, vendors, independent contractors, and prospective employees.
Before joining Build Consulting, David Deal was the founder and CEO of Community IT Innovators, which provides technology guidance and services to nonprofits. David guided Community IT from a start-up to an established employee-owned company with more than 45 staff members, serving more than 1,000 nonprofits. He personally worked with over 100 nonprofits to provide everything from hands-on application development and network engineering to technology strategy and guidance. David continues to serve as the Chair of the Community IT Board.

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert.
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response. You can view Matt’s free cybersecurity videos from past webinars here.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She is happy to be moderating this webinar.
Check back here after the webinar for the transcript, video and podcast in case you miss this webinar on data cybersecurity for nonprofits.
Transcription
Carolyn Woodard: Welcome to the Community IT Innovators presentation on Data Cybersecurity at Nonprofits. Today we’re going to talk specifically about a subsection of cybersecurity and keeping your data secure in all the tools that you use that store the data that is important to your organization.
Hopefully, you have all taken some steps around cybersecurity at your organization in general, and if you need a refresher we have many videos, podcasts and articles on our website about cybersecurity including a Nonprofit Framework Playbook that you can download for free.
But today, I’m excited to be talking with our experts about additional steps and policies you need to take to secure data in all the tools that you use, some you may not even have thought we’re at risk.
My name is Carolyn Woodard I’m the Outreach Director for Community IT and I’m the moderator today. And I’m very happy to hear from our experts. Matt, would you like to introduce yourself?
Matthew Eshleman: Thanks, Carolyn. It’s great to be here in October, Cybersecurity Month. My name is Matthew Eshleman, and I’m the Chief Technology Officer at Community IT. In my role at Community IT I’m responsible for two areas, one is the back-end systems that we use to manage our nearly 7,000 endpoints, and I also work with clients on their solutions architecture and cybersecurity planning and I’m happy to be joined by my colleague, David Deal.
David Deal: Thank you, Matt. Thank you, Carolyn. I’m a Founding Partner at Build Consulting where I’ve been since 2015. My work is as a virtual CIO for mid-sized and large nonprofits. One of the things I focus on in that role is cybersecurity. Build works exclusively with nonprofits: mid-sized and large nonprofits mostly across the U.S., a little bit internationally. Build is passionately independent of any vendors. So although we keep close tabs on what Microsoft and Salesforce and Blackbaud and Bonterra and others are doing, we are not partners with any of them and don’t receive money from any of these vendors. So we really sit on our clients’ side of the fence in making technology decisions.
We do a lot of technology and data strategy work, virtual CIO work that I mentioned, and really combine deep technology experience with an appreciation for an understanding of organizational change management, which is really important for everything technology related, but also cybersecurity, because so much of cybersecurity is about behavior and policies and processes as much as it is technology.
Carolyn Woodard: Thanks so much, David. I’m so glad you could join us today and share your expertise. So before we begin, if you’re not familiar with Community IT, I’m going to tell you a little bit about us. We are a 100% employee-owned, managed services provider (MSP). We provide outsourced IT support and we work exclusively with nonprofit organizations, and our mission is to help nonprofits accomplish their missions through the effective use of technology. We are big fans of what well-managed IT can do for your nonprofit.
We serve nonprofits across the United States. We’ve been doing this for over 20 years. We are technology experts, and we are consistently given the MSP 501 recognition for being a top MSP, which is an honor we received again in 2023.
I would like to remind everyone that for these presentations, Community IT is also vendor agnostic. We only make recommendations to our clients, and only based on their specific business needs. We never try to get a client into a product because we get an incentive or benefit from that.
We do consider ourselves a best-of-breed IT provider. So it’s our job to know the landscape, what tools are available, reputable, and widely used. And we make recommendations on that basis for our clients based on their business needs, priorities, and budget.
Learning Objectives
I wanted to talk a little bit about our learning objectives for today. At the end of the presentation today, we hope that you will
- understand what nonprofits need to do to secure your data,
- learn the common risks,
- learn best practices for data security,
- understand data governance,
- be familiar with cybersecurity technology, terms, and concepts.
Poll 1
Where do you store data?
You may have a
- Custom database with SQL, Airtable or other custom databases.
- You may store data in spreadsheets. I’m guilty of that right here.
- You may store data in an enterprise resource planning tool,
- Customer relationship management tool, those are often also called CRM.
- You may have an HR information system or HRIS.
- You might be storing your data in SharePoint and Google Drive.
- You may have a data warehouse.
- You may have something else completely where you’re storing your data, but it’s a different system than the above,
- or it might not be applicable to you. You’re either not at a nonprofit, you don’t have any data.
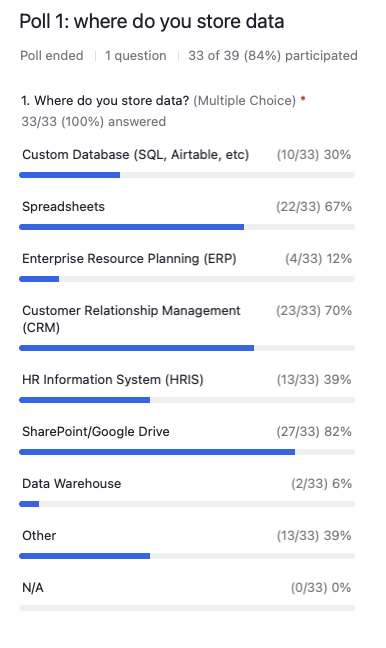
David Deal: One of the lowest ones on the list is data warehouse, only 6% of respondents. Next lowest was ERPs, Enterprise User Planning System. However, I bet if you apply the ERP label to financial accounting systems, even things like QuickBooks, that would be 100%. Let’s see, the next lowest was custom databases, weighing in at 30%. And some others were spreadsheets, about two-thirds of people. CRM about 70%, HRIS about 39%, and SharePoint, Google Drive 82%, presumably the others using Box, Drop Box, something like that. And then there’s also a very few people who weighed in for other, as well.
David Deal: I think the key point here is it’s a little bit of a trick question. We expected most people to check most of these boxes. Most organizations have really most of these types of systems, perhaps with the exception of custom databases and data warehouses, which are a little less common these days.
The main point is data is everywhere. It’s in all of these systems, and it’s in a lot of other systems as well.
Securing Data
Carolyn Woodard: Which leads us into our first topic. We wanted to give a little bit of an intro into what nonprofits need to do to secure their data and what practices should be in place in all instances, and then maybe some additional practices that should be considered for the most sensitive data. And I think David, you also wanted to talk a little bit about what we’re considering data and the systems that we’re talking about.
David Deal: A couple points I wanted to make at the beginning. We’re really designing this webinar for people who are either IT practitioners who don’t have much of a focus on cybersecurity yet or perhaps non-IT leaders who are responsible for IT. And really our focus is on some of the things you should be considering for your cybersecurity measures.
We’re not going very much into a deep dive into any of them. It’s more of a broad scan of the types of technologies, practices, processes you should be considering.
Second thing I’ll say is this is primarily not about network infrastructure and securing infrastructure and devices. The idea behind this webinar is that there’s something that often falls in the gap between what nonprofit staff are responsible for, and what a nonprofit’s managed IT services provider is responsible for. And we wanted to focus on how nonprofits are addressing that.
Carolyn Woodard: Yeah, thank you for that. I would say that if you are a cybersecurity expert, it would make sense to follow David and Matt on LinkedIn, because I’m sure you’ll have a lot to talk about.
But yes, for this webinar we wanted to make sure to make it accessible to people who need to manage security at whatever level of security experience they have. All right, so Matt, I think you were going to ask David about some of these items.
Matthew Eshleman: Yeah, so David, I think it was a good overview to frame security about data as separate and distinct from the traditional view of network security and file and folder level security.
I was wondering if you could talk a little bit more about that distinction and how threats to business applications may be a little bit different than threats to your network infrastructure.
David Deal: Yeah, so we’ve outlined a few threats that we find in business applications here. One of the most well-known is ransomware. Although, I’ll say most ransomware deals with file systems, your Google Drive, your SharePoint, and encrypting files of that nature. So in all likelihood, that is something that an MSP is probably helping you with.
When we think about business applications, data corruption is one of the things that can happen, both intentionally or unintentionally. For example, accidental data deletion or intentional data deletion, from a departing disgruntled employee. Most of these cloud systems only retain data for 30 days, so if something gets deleted, you don’t recognize it for 30 days, what recourse do you have?
Other possibilities include things like an errant upload or import of data that can also corrupt data in your database or application.
Another common threat to business applications is really that sensitive data will be stolen. I was the victim of this myself when DC Health Exchange had a big data breach. It caused all kinds of troubles from data being stolen from a database from a business application. And I think that is one of the big security risks there.
Something else that is really on my mind these days is AI. AI offers some great possibilities and opportunities to all of us in different ways. But it’s a tool that can be used just as easily by hackers and people who are up to no good and trying to get into your systems. So I think in part because of AI, and because of other reasons as well, the threat to nonprofits and cybersecurity continues to increase. Deep fakes are better. Scanning for and exploiting vulnerabilities is faster, more automated.
AI and Cyberhacking
Really I have a question for you here, Matt, which is: with hackers using AI, what do you think that means for the cybersecurity measures that nonprofits should take? Is this a game changer for nonprofits and their cybersecurity?
Matthew Eshleman: I don’t know that I would go so far as saying it’s a game changer, but I do think that it’s another step in the ongoing efficiency improvement and focus of what it means to be a victim of cyber crime.
I use the term cyber crime intentionally, because I think it’s important for organizations to understand that every organization is vulnerable. Every organization has data that could be used or manipulated. And so, these attackers are using the tools that are available to automate and speed their way into that financial aspect of crime.
Now, I think there are certainly some organizations that may be at a higher risk for what we call advanced threat actors that are really looking to get embedded in the organization and see what’s going on.
But for the vast majority of cyber criminals, they’re trying to target your systems, encrypt the data, exfiltrate data, use it as a hostage so that they can ultimately get paid.
Understanding that financial dimension of cybercrime is important. And yeah, I think these AI tools are only going to make it easier and faster for these exploits as they become more commoditized and commercialized. And so, those resources become widely available, just as we’re using tools to speed and automate our response on the other side as well.
David Deal: Thank you for that, Matt. The other point I wanted to make about the risks to business applications is the proliferation of applications and data. It’s extraordinary when we go into organizations and inventory the applications they’re using or the places they’re storing data. Ten, 20 years ago, it was a quarter of what it is now.
But it’s so easy to spin up a new application for a few users that data is everywhere. That creates complexity in cybersecurity because you have a vastly increased surface area for attacks. You have many more places where that data is stored and that data is vulnerable. It isn’t just on servers on your network. It’s across numerous cloud applications, multiple backup solutions. One of the tactics for dealing with this and managing it is really data governance and having a data inventory. We’ll talk a little bit more about that later in the presentation.
Maybe we could look a little bit at some of the best practices here.
Data Cybersecurity Best Practices
Matt, you’ve started to talk just a little bit about it, but what do you consider to be the things that every nonprofit should be doing?
And then what are some things nonprofits who want stronger cybersecurity should be considering?
Matthew Eshleman: I’ll dovetail into what you said in terms of starting with a data inventory. If you don’t know what you have, it becomes very difficult to protect it.
One of the things we see whenever we do security assessments is understanding how many different user accounts you have and what systems do they have access to? With this proliferation of data, you can have sensitive data in systems that IT isn’t aware of or old user accounts that are still active in systems that have sensitive data, because the off-boarding request never made it back to IT, or maybe that’s a disconnected system and IT doesn’t even manage access to those accounts.
Having that data systems inventory, understanding which users have access to which systems and which systems may require extra protection is really foundational.
The other foundational element and one of the reasons why we like Single Sign On so much is that it helps to funnel down and give you a better way to manage and audit user access. So instead of trying to look at sign-in logs for 10 or 15 or 20 different systems, through the use of Single Sign On, you can look at that all through a single pane of glass, ensuring that MFA is in place and well protected for the user as they’re entering those applications as opposed to having multi-factor authentication and a separate username and password for 10 or 15 or 20 different systems.
So having a good sense of the applications that are in use, having a sense of which users need to have access. Those are foundational elements. Once you go beyond that, then we’re starting to look at more detailed audit and reporting controls, so you can answer the question, who had access to what data when and be able to have some stronger audit and reporting controls.
As David mentioned previously, some of the most likely causes of data loss of an organization are end-user driven, either intentionally or unintentionally. And unless those tools and systems are put in place at the beginning, it’s very hard to go back and get that information out of a system. If you want to know, which user went and looked at all the donation history of the top donors, and is that something they need to do for their job? So I think once you get these systems established, having more granular access roles, being able to be a little bit more precise in terms of granting access, those are the things that we see being important.
Also having clear data retention requirements. Organizations have now gotten to a point where they understand that the data they have is not just an asset, but it also represents a liability as well.
And so, if there’s not a good reason to keep some data in your organization, it’s a good practice to develop a data retention policy. You can say, we absorb this information and we use it and then at some point, if we don’t have a legitimate use for it, we’re going to move it on so that, if and when we do get compromised, we only have to do reporting against the users in our system that we’re actively engaged with and not people that we may have contacted 20 years ago.
And then I think the other piece around that data retention requirement is really driving into the backups and the recovery piece. Ransomware and encryption gets a lot of headlines, but at the end of the day, you’re relying on a recovery strategy to be able to restore access to those systems. Make sure that those systems and processes are in place.
With a lot of cloud systems, there may be limitations on what you can do as a customer and you’re relying on the vendor to provide that. So having a clear understanding of what happens in these scenarios and the service level agreements are very important steps. It’s a different mindset from, I got my data on the server and I’m going to restore that. You may be relying on vendors.
And then again, there’s an advent of a lot of pretty sophisticated security tools that can help run on this concept of DLP or Data Loss Prevention as a way to ensure that sensitive data isn’t exported or your systems are protected against people accidentally sending credit card information or maybe social security numbers, birthday information for people that are in the database. But it really starts rooted in some of that policy and planning framework. And then that can help inform the technology solutions that you choose to implement.

Carolyn Woodard: There were a couple of questions in the Q&A.
Can you give us a basic explanation of third party backups? What does it mean when you say that?
Matthew Eshleman: A third party backup would be a way to get information out of your primary system into a separate cloud. A common example is an Office 365 backup of email or SharePoint data.
Microsoft is providing some protections of your data, but if something is deleted and you don’t discover it for three months, that data might not be available to be recovered. And so having that data in a third party system gives you a way to recover it, restore it if that’s required for general productivity or maybe there’s a legal case that requires you to have access to that data. So again, having data outside of your primary system so that you’re able to get it back because the vendor’s likely not keeping it for as long as you want or think they should.
Carolyn Woodard: So that’s a third party vendor that you sync to regularly?
David Deal: Yeah, there are a couple of methods. Really any cloud system, including CRM, Salesforce, Dynamics, any system you’re using, out of the box, you’re depending upon that vendor’s backup to keep it running.
For the most part, it’s a lot more reliable than servers used to be when they were on nonprofits’ networks, but they’re not perfect. Data gets deleted, files get lost, etcetera. And the vendor backups are usually only good for a relatively short period of time. That’s why you really need to consider when a third party backup is warranted.
This is not just in the domain of really large organizations to do this. Even a small nonprofit, even if you’re not using a third party backup tool, you might periodically do a manual export from your CRM just to have another copy of that data somewhere secure.
Carolyn Woodard:
A little bit more about Single Sign On and what is the size that Single Sign On makes sense for, as a tool?
Matthew Eshleman: So Single Sign On is a way that you can use your primary identity. You’re logging into Office 365 or Google Workplace and then you can use that identity to then access other systems that have this ability to be integrated.
So you don’t have to have a separate username and password to access Salesforce, for example. Salesforce trusts Google to authenticate you into that system. Unfortunately, the system configuration takes the same amount of time to set up whether you’re a 10 person organization or a 100 person organization. So it can be a little bit expensive to justify if you’re a 10 person organization.
At that size, we typically see organizations using password managers, which are helpful because they give you the ability to have strong, unique passwords for all those different applications.
So, starting with a password manager is a good idea. Maybe at 25 people or larger, or if you have a lot of different cloud applications, then Single Sign On becomes easier to justify.
Carolyn Woodard: Now, that seems like good advice. There are a lot of password managers out there, and you can get a pretty good one for what you need until you get a little bit bigger. Thank you, Matt.
Poll 2
At your organization, who is in charge of your cybersecurity?
- It’s unclear, or no one. And please don’t be embarrassed or ashamed to click that as your answer, because we’re all here for you and you’ve come to the right place. You’re in a webinar around cybersecurity so you know that you need to do it and a lot of people are in that same boat.
- The second option is, the application owners. So if you have Salesforce or something like that that’s owned by a staff member, a role or a department then that is where the cybersecurity for that tool would lie.
- The third option is a CIO, a CISO, VCIO or a similar title that’s the Chief Information Officer or a Virtual Chief Information Officer. Someone at a high executive level is responsible for your cybersecurity.
- The fourth answer is an MSP, Managed Services Provider or IT provider such as Community IT. So outsourced IT is in charge of your cybersecurity at your nonprofit.
- An MSSP is the next option. That’s a Managed Security Services Provider, specifically around security.
- Another option is other
- and then the final option is not applicable.
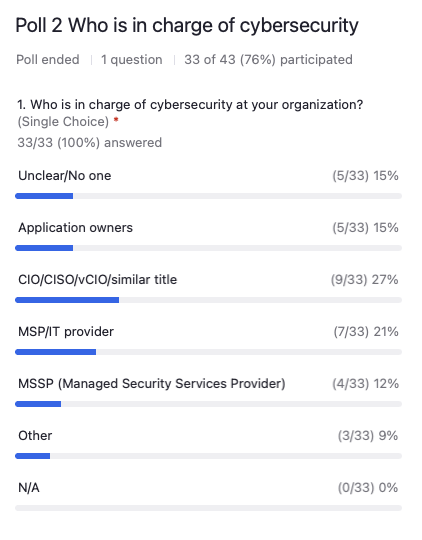
Matthew Eshleman: About 15% of folks said unclear or no one. So I’m glad you’re here at this webinar. Maybe it could be some inspiration to go and follow that up. About a quarter of the audience says senior level at the CIO, so that’s great. Then another 21% pushing it on to the MSP or the IT provider and then a smaller proportion, 12% saying that they actually had a managed security services provider. Then we’ve got about 15% saying the application owners themselves are in charge of cybersecurity, followed by other. So all over the place in terms of where that responsibility lies within the organization, which mirrors our experience as well.
Carolyn Woodard: We often say when working with nonprofits, you can make some generalizations, but so many nonprofits operate in different sizes, different environments, have different technical needs and complexity. So it’s not unusual to see a wide range. Also, we would say there’s no universal way you should always do [cybersecurity responsibilities], like “It should always be at the C-level” or “it should always be at the outsourced level.” So I think that’s reflective of our experience, for sure.
And that leads us into our next topic.
Governance
We want to take a little bit of a deeper dive into governance and training best practices and expand a little bit on that framework that we talked about briefly in the first half of the webinar, go a little deeper into what policies and governance you need, and then some ideas on training.
Matthew Eshleman: It’s not just technology solutions here.
So from your perspective, having that CIO role with a lot of different organizations, what are examples of good data governance and how is that carried out at an organization?
David Deal: Well, I think that organizations that do this the best have some policies, some statements around the data that they want to collect, because it’s really easy to just keep adding over the months and years to the data you want to collect and not really using it. And so both for that reason and also, think about data that you absolutely don’t want to retain in your system – social security numbers, credit cards, things like that. Do you have policies making it clear that that’s not the type of information that you’ll gather?
So really, that’s part of being clear about what data we’re going to collect for what purpose and revisiting that periodically to stop collecting things that you’re not using. That is important.
Being clear on retention requirements, what data are we going to keep for how long? Don’t keep all data forever. There’s certain compliance requirements for how long you need to keep financial data and some things like that. But otherwise, it probably doesn’t benefit you and probably just creates risk to keep data around for a really long time.
The data inventory is something we mentioned earlier to talk a little bit more about. The things I look for, and this is one of those spreadsheets I’m glad to see, where is their data stored? What data is there at the very least? Who is the business person who’s responsible for that data? What sort of backup and retention methods are in place for that data? But just being clear on that governance piece of who’s responsible for it can be really helpful.
Governance really includes things like user administration or what I might call identity and access management – who should be able to access what, especially as an organization grows? You need to start to think about how convenient it is for everyone to have access to everything. You really need to start to apply some privilege techniques to who can access what and really limit people to the things that they need to access to be able to do their job. So role-based access controls and your programs begin to enter the picture there.
For identity and access management, I want to put in a plug for SSO, Single Sign On, that you mentioned earlier. I can’t tell you how much easier that makes it both from the IT administration side, but also the end user side.
When we’re dealing with things like CRM adoption, just having Single Sign On, I think people would be surprised what a big difference that makes in people’s inclination to use it to capture activities, for example. Plus, it’s a big plus when managing cybersecurity risk, being able to get people out of systems when they leave the organization and things like that.
And then, finally, data quality and looking at data quality is also a part of data governance. It’s maybe not as much of a cybersecurity consideration, but are you keeping your data tidy? I’ll bet the organizations that are doing that are probably the same ones that have a data inventory and are paying attention to that type of thing.
Matthew Eshleman: Yeah, I would say I really like that. The user administration piece just piggybacks on that. The role-based access controls, all those are ways for the organization to think about it, put it down on paper and have an intentional approach so that not everybody has access to everything. And organizations have made pretty big strides in this area, from what I’ve seen, in being intentional about and specific on access rules.
Cybersecurity Training
David Deal: Continuing along the lines of things that aren’t specifically about technology, we talked a little bit about the importance of training, and so much of cybersecurity is about the behavior of staff members.
So, Matt, what is Community IT doing, and what are you seeing your clients do for cybersecurity training?
Matthew Eshleman: From the cybersecurity perspective, most security issues or compromises that we see are still coming through email, password attacks or account compromise on the primary system. I’ll say, knock on wood, we have not yet seen a case where a database user account was compromised. But typically there’s an incursion through the primary system.
Going back to the fundamentals, having security awareness training practice for staff to keep those topics front of mind, is absolutely essential.
We use KnowBe4. I think they have a good product. There’s a lot of other security awareness training platforms out there. But from our perspective, we like to do a mix of test phishing to see how staff are performing, who’s susceptible, who may need some extra education, combined with relatively short, but frequent training engagements.
Our approach typically is to have quarterly trainings to get different and new concepts in front of staff. It doesn’t take a lot of time, but we really want security to be at the top of mind for folks. That’s the approach we’ve taken.
I would certainly encourage other organizations to adopt that intentional training approach. Focus on the fundamentals of general security awareness training, then start looking at some specific training for how the application is configured and used.
So Dave, maybe you can talk more specifically about some of the training resources that are available at the application level.
To wrap up, it’s really important for organizations to have some policies and procedures in place to identify what they are going to do as an organization.
- When we think we have a problem, how are we going to go about that?
- Who do we talk to?
- Who’s responsible on our side?
- How do we interact with our stakeholders?
And make sure that that is defined and tested in advance, because the common thread is it’s not a question of IF you’re going to have a compromise or a breach, it’s a question of when.
Being able to test and define those policies and procedures in advance of a crisis is really important, because it can give you a lot more confidence, and it may even be a requirement if you are procuring cyber liability insurance. Some things are expectations of those policies. That’s the foundational elements that we talk about or think about when we’re looking at designing an effective security awareness and security training program for an organization.
David Deal: I think specifically from the business application perspective, both administrator training and end user training comes to mind. And what I mean by administrator training, number one, making sure that for any application you have, there is an application owner. Someone who understands that by putting the organization’s data in an application, they need to take responsibility for or work with a CISO or some person who does have responsibility for the cybersecurity of that data.
And they need to be looking at things for that application, like is two factor authentication available? Do we have it turned on? Who’s using it? What do they have access to? What can they export? Getting back to this idea of data loss prevention.
As I think about an HR information system, for example, how many HR people do you know who are exporting full staff lists with salaries and/or social security numbers or things like that to a spreadsheet that then sits in their One Drive or their Google Drive, or worse their local hard drive? So there’s some end user training. I’m not going to say there’s never a business need to do an export of sensitive data, but if you’re going to do it, there’s certain ways to handle it to make sure that you’re treating it securely and not leaving copies of data sitting around everywhere.
But there’s no generic security training that I know of for really general use of business applications, because it really depends upon the business application. So the nonprofit itself and whoever’s responsible for that application and cybersecurity for that application really need to think about how they need to train the administrators and the end users to be responsible with this data.
Technology Terms & Trends
Carolyn Woodard: That’s a great segue into our next topic on the technology involved. I know, David, as Build always says, “the technology comes last” in an organization around what you’re trying to do. You want to find the technology that will do that thing instead of choosing the technology first and doing whatever the technology says.
In a topic like cybersecurity, your organization will probably have a lot of vendors reaching out, trying to sell new tools before you’ve done an assessment around what you really need. And as we’ve said today, I think several times, within the tool or platform that you’re using there may be security specific to that, so you don’t need an additional tool or you might need something like the third party backups that we talked about today.
I wanted to use some of the time we had left to review some of the terms that nonprofit staff might come across in how some of these tools work.
We have a question about Okta. I’m hoping that you can touch on that and maybe some of the other tools. Matt, this is one of your areas of expertise.
Matthew Eshleman: Okta, which is a Single Sign On vendor. Okta is actually a scientific term. It’s a way to measure the degree of cloud cover. So whoever named that for your cloud Single Sign On was pretty smart.
But that gives you a way to easily sign on and have access to all these Single Sign On applications. It is what we called a third party vendor, which would be distinct from Microsoft with their Azure or Entra ID, which also gives you the ability to do Single Sign On. Same thing with Google Workplace. You can use that as a Single Sign On platform.
I would say the majority of customers that we’re working with are using the native tools. Primarily, I would say, for cost reasons. There are some organizations that have chosen to implement third party Single Sign On solutions and identity providers. Okta is probably the biggest name, one of them, but One Login, there are others.
My sense is that there can be some benefits with usability to going to the third party providers, although that introduces some complexity and yet another vendor that you need to rely on for uptime. And identity is very, very critical, because if you have an outage, then it takes out access to all of your applications. I tend to stick with the core vendors for that reason, just because if Okta has an outage, One Login has an outage, that has a pretty outsized impact on your access.
Uptime and availability is the number one feature of those solutions. I think both Microsoft and Google have made improvements in terms of the usability of those tools and so I would stick with the main vendors there.
David Deal: Matt, I would say the two I see the most are Okta and Azure AD or now Entra ID, and I’m sure Microsoft will change the name again next year too, right? But traditionally, my thought on the argument for Okta was both the usability side and users found it more usable than, say Azure AD. Also the number of applications and the level of how easy it was to connect with more applications. So I think that’s why some organizations will pay for the not small bucks to get a third party solution like Okta.
Carolyn Woodard:
Part of the question was around open source solutions as well. Do you have thoughts on that?
Matthew Eshleman: I’m not familiar with the company that was mentioned. I will say that the standards that are used for SSO integration are technically open standards.
The other piece that was raised in another question was to acknowledge that for some vendors Single Sign On is a premium add-on. So it could be, if you have Slack as an organization, unless you’ve got the business version or the upper tier, you may not be able to do Single Sign On with integration with that application.
I think it’s something that vendors should make free and include as a core part of the product, because from a security perspective it’s so vital. But that is something to be aware of – to access the SSO feature, that may be another couple of dollars a month or a different tier.
David Deal: I would just add the importance of that. I would really advocate for organizations to spend a little bit more money for increased usability and increased cybersecurity. That’s probably one of the better investments you can make and a pretty solid return on that investment for usually not that much more.
Carolyn Woodard: We said we would talk about terms, so I wanted to make sure to touch on some of these things. I know multifactor authentication we’ve talked about elsewhere and we have some stuff on our website about it.
MFA MultiFactor Authentication
Matt, you wanted to talk a little bit about authentication versus SMS. And also, security keys, the actual physical key that you can use. Do you have advice on that?
Matthew Eshleman: Actually, this is something Microsoft is driving right now, removing the ability to use text messaging as a secondary MFA source.
Multi-factor authentication combines something that you know, which is your password, along with something you have. Microsoft now is saying, “Hey, the Microsoft Authenticator app on your phone would be a good option.”
Security keys are becoming more and more popular, and I will make a pitch for them. There’s some open standards, FIDO security key, you may see it named as. But this is the best method of multi-factor authentication, because it is very hard for a key to be spoofed.
We have started seeing some very, very sophisticated hacking attacks or web proxy attacks that actually can steal the multi-factor authentication token from your phone. It cannot steal it from this physical key. So for organizations that are very concerned about their identity and access management piece, I think these physical security keys are a good way to provide a really high level of security. It also has the benefit that you don’t have to ask your staff to install an app on their phone. That raises some BYOD concerns, but again, multi-factor authentication is critical.
A good solution is certainly to use the Microsoft Authenticator app for those of you in Office 365. And for $20 to $30, you can get a physical security key and really up your game for protecting your identity against those sophisticated attacks.
Encryption
Carolyn Woodard: So I know we’ve talked a little bit about Single Sign On and backups. But we haven’t hit as much on encryption. Can you talk a little bit more about that, Matt? About HTTPS, which I think a lot of us know, but what do nonprofits in general need to know about encryption?
Matthew Eshleman: I think the good news is that encryption in transit is where a lot of these cloud solutions are already provided. So that’s the SSL or TLS. You see the lock in the website whenever you’re accessing your Salesforce database. That means that as the data goes from your computer to their servers, that data can’t be spied on by anybody else that may be in the network. So those things are pretty widespread now. And if you’re filling out your cyber liability insurance applications, it’s easy to say yes: end-to-end encryption, or in-transit encryption is enabled.
What may not be quite as apparent is encryption at rest. That’s really talking about when the data is saved somewhere, is that encrypted at rest? For a lot of the cloud hosted systems, again, that answer is yes. But if you have a database or an application that you are still hosting yourself, you need to take extra steps to make sure that that data, when it’s saved on the server or the computer, is encrypted. Bit Locker is a term on the Windows side or File Vault for the Mac side that will encrypt your hard drive. So that if your device is lost or stolen, if somebody takes your hard drive and tries to get data off of it, it’s going to be unrecognizable.
David, maybe you can provide some insight. There are some tools within products like Salesforce that do more encryption within the database itself.
David Deal: Yeah. For example, in the Salesforce world, there’s Salesforce Shield that helps with everything from encryption to monitoring who’s doing what in the system and is a really helpful cybersecurity tool.
VPN for Cybersecurity?
I did want to ask, since on virtually every website you go to now you’ll see the HTTPS at the front of the website name and every web application you’re using, almost all of them are using that. Is a VPN really as necessary anymore for anything other than connecting back to a local network?
Matthew Eshleman: I must admit, I’ve never been a huge fan of VPNs to provide secure internet. I think it’s a good idea if you have security and privacy concerns that you should just travel with your own hotspot and rely on that for connectivity.
I think VPNs do have a case. I will say, as somebody that looks through lots and lots of security logs, VPNs can be super problematic because, especially if it’s not a corporate VPN service, it can make you appear like you’re connecting from Oregon, and then you’re connecting from Montana, and then you’re connecting from New York. And then all of a sudden, all these rules that we have in place to look at unusual travel or location all go haywire.
So VPNs certainly do have a place. I think if you have an organization that says, we really need to provide trusted internet access and we’re going to be really defined about where we allow people to connect from, having a corporate VPN solution that allows you to do that is good. But just having a VPN to protect your internet traffic at your Starbucks may not be as beneficial as it used to be.
Carolyn Woodard: We have one more term on this slide – the data leak or loss prevention. I know we touched on it earlier. I got the sense from you both that this was more of a policy issue if you have more sensitive data or maybe you’re operating in a sector in which you have more privacy concerns.
Data Loss Prevention
Would you talk a little bit about DLP? Matt or Dave?
Matthew Eshleman: Sure. So DLP, or Data Loss Prevention is typically described as a way to provide some automated security. This may be the use of AI, right? There are systems that are built into Google and Office 365 that basically can read or look through the content of your file systems and flag things that look like credit card numbers or Social Security numbers or a banking account or routing information and then they can take actions.
A common control is to say, we’re going to block anything that looks like a credit card from being sent in an email outside the organization. Maybe your HR person has an export of all the staff with their Social Security numbers, they hit attached on that file.
The DLP rules all of a sudden will trigger and say, Hey, this looks like it has sensitive information, are you sure you want to send that? Or, they can block it. It’s a way to provide some technology controls that can help support the policy choices that an organization has made.
If they said, yes, we have sensitive information on our database. You can’t export that and save it on your computer; you can’t save it on the network. The DLP rules can help be that technology enforcement on the policy decisions of the organization.
David Deal: I’ll just quickly add one thing about DLP. You really need to be thinking about the different ways that data might exit your system or your organization. So certainly email. But also, now we have Slack and Teams that are used for external collaboration a lot, or maybe someone’s just doing a big export from a CRM database and taking that spreadsheet with them, things like that. There are DLP solutions built into many products that can help with this. And then there are also third party DLP solutions to be considered if you want a more comprehensive approach to it.
Carolyn Woodard: Thank you guys both so much for taking us through that. I really appreciate it.
I’m going to head right to our learning objectives and just to recap for people. We wanted to help you understand what you’d need to do to secure your data at your nonprofit, learn some risks, learn some best practices, understand data governance and policies and be familiar with cybersecurity technology terms and concepts. I think we did pretty well at that.
Matt and David, I just wanted to thank you again so much for your time sharing your experience and expertise with us today. Thank you.
