Community IT CEO Johan Hammerstrom moderates a presentation from Steve Longenecker and Pat Sprehe about Community IT’s approach to outsourced IT for nonprofits and how clients can benefit from our IT Business Manager model. They give tips and offer examples on maximizing the relationship with IT experts who can help you match the IT you need with your business strategy.
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Spotify, Google, Stitcher, Pandora, and more. Or ask your smart speaker.

As Director of IT Consulting, Steve Longenecker divides his time at Community IT primarily between managing the company’s Projects Team and consulting with clients on IT planning. Steve brings a deep background in IT support and strategic IT management experience to his work with clients. His thoughtful and empathetic demeanor helps non-technical nonprofit leaders manage their IT projects and understand the Community IT partnership approach.
Steve also specializes in Information Architecture and migrations, implementations, file-sharing platforms, collaboration tools, and Google Workspace support. His knowledge of nonprofit budgeting and management styles make him an invaluable partner in technology projects.
Steve’s appreciation for working at Community IT Innovators is rooted in respect for the company’s vision, and for his excellent colleagues. Before joining Community IT, Steve was an 8th grade science teacher at Takoma Park Middle School, and – though that was a long time ago now – he still draws on lessons learned in that first career.
Steve is MCSE certified. He has a B.A. in Biology from Earlham College in Richmond, IN and a Masters in the Art of Teaching from Tufts University in Massachusetts.

Patrick Sprehe is now Director of Information Systems and Technology, after serving as the IT Business Manager Team Lead. As that team lead he managed the team that guides our clients’ IT roadmaps and provides help with overcoming nonprofit technology challenges.
Patrick brings a deep knowledge of technical support, an interest in new technology uses at nonprofits, and experience implementing and maintaining established platforms and systems for large and mid-sized nonprofit clients to his role as Director of Information Systems and Technology at Community IT.
Patrick joined Community IT in 2010 and has provided technical support to a variety of clients on a variety of issues. His capable approach helps the ITBM team tackle strategic planning with clients with calm expertise.
Patrick graduated from University of Maryland, University College with a B.S. in Information Technology. Patrick is also a certified BRM (Business Relationship Management) Professional.

Johan Hammerstrom’s focus and expertise are in nonprofit IT leadership, governance practices, and nonprofit IT strategy. In addition to deep experience supporting hundreds of nonprofit clients for over 20 years, Johan has a technical background as a computer engineer and a strong servant-leadership style as the head of an employee-owned small service business. After advising and strategizing with nonprofit clients over the years, he has gained a wealth of insight into the budget and decision-making culture at nonprofits – a culture that enables creative IT management but can place constraints on strategies and implementation.
As CEO, Johan provides high-level direction and leadership in client partnerships. He also guides Community IT’s relationship to its Board and ESOP employee-owners. Johan is also instrumental in building a Community IT value of giving back to the sector by sharing resources and knowledge through free website materials, monthly webinars, and external speaking engagements.
Johan Hammerstrom: Thank you for joining us for today’s webinar on working with an outsourced IT Business Manager. My name is Johan Hammerstrom and I’m the CEO of Community IT.
We have Steve Longenecker, who is our Director of IT Consulting.
And we have Patrick Sprehe, who is one of our IT business managers.
Steve Longenecker: All right. Yes, this is Steve. So our agenda is, we’re going to talk about the context of IT management broadly, then how we see IT Management fitting into a managed service provider’s suite of services, which is who we are; we’re a managed service provider. So how does IT management fit into that?
At the biggest picture, the highest level view, the digital landscape has definitely changed. And everyone’s aware of the fact that it has. There’s been a bit of a revolution. We sometimes talk about it as the consumerization of IT. Users now think about how IT works for them in a different way, expectations are higher, success is measured differently and there needs to be more alignment between IT and business needs. And as a result, there needs to be a more sophisticated, involved approach. And that, in a nutshell, is one of the ways in which we think IT management fills that gap.
Patrick Sprehe: So along with us recognizing the need among our own clients, there’s also been just a general recognition in the industry and in business and organizations in general about this rise of the need of IT management and what’s called BRM, or business relationship management. It is defined according to Wikipedia as “a formal approach to understanding, defining and supporting business activities related to business networking or business IT.”
And so all of this started back in essentially 2007. The ITIL, which is the IT Infrastructure Library, which is just a framework for how to run an IT department or a managed service provider like us, it’s what we use. They formally recognized BRM processes as a best practice in their version 3 library. If you remember, 2007 was also the year that the iPhone came out. Facebook came out, I think, just the year before. Android followed in 2008. So that was really when this consumerization of IT that Steve mentioned kicked off. Coming out of 2007, BRM became more important in this recognition of the need to align business and IT. And so the BRM Institute was established. More recently, just a couple years ago, there’s now international standards about business relationship management systems.
All that history being said, the real purpose of BRM is to align the technology, the IT infrastructure and services with the needs of the business, to be the liaison between the IT and the business.
So BRM is really responsible for
Now, what’s particularly interesting about this, when working with an outsourced IT manager, is that you’re working with an expert in the IT field, who should be able to understand the best practices, the immediate and future risks that you might be facing, when it comes to IT emerging technology and trends. But they are an outsourced consultant; they’re an outside consultant.
And so you [and your nonprofit leadership] have to step in and provide them the business context, the reference to the business needs that will help them to best help you manage your IT.
Steve Longenecker: So that’s the context for IT management in the digital landscape writ large among our own clients, and then the history of BRM.
Business Relationship Management (BRM) was conceived of and is still largely thought of, as something that is done in a corporate environment where IT is serving other parts of the corporation and there needs to be someone in IT that has their eye on the ball knowing – How is the IT department serving the larger business needs? Not just doing things in a vacuum in terms of “this is the best practice, how IT should be done,” and not asking, how that works.
Now, that’s important because the context of a Managed Service Provider (MSP) is slightly different.
A managed service provider – these are oftentimes generally smaller organizations that contract with an outsourced organization to provide some or all of their IT services to them. And that’s what Community IT is. We’re a managed service provider. And so we provide managed IT services, support and so forth to our clients and we can look at how that looks.
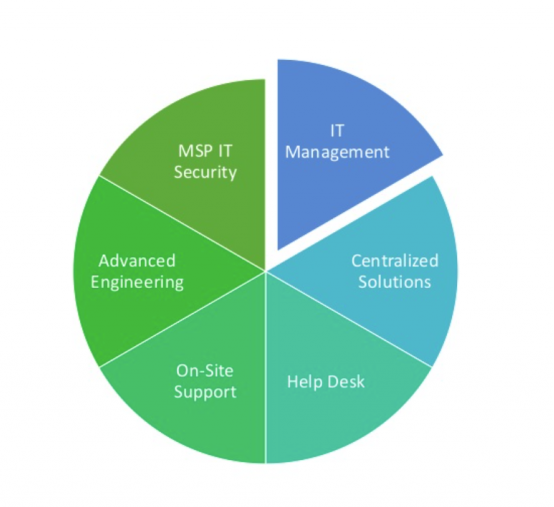
So this is how we think of what we deliver to our clients.
We have MSP IT security, which we put the word MSP in front of it to distinguish from the fact that there might be higher levels of IT security that would be provided by what’s called a managed service security provider, but basic levels of IT security that we would be responsible for.
Centralized solutions is things like patching. There’s overlap here. Centralized solutions at Community IT includes making sure that antivirus is on all of our computers that we manage and that it’s up to date and has the latest definitions and so on, the overlap between centralized services and IT security. There’s overlap between all of these things, frankly.
The help desk is the people that answer the phone or the chat, ticket requests that come in and that we take care of.
We provide on-site support to some of our clients, where people actually go to our clients and are there on a regular basis. Some of our clients get to know our technicians quite well, because they see them on a weekly basis and that is a different kind of support.
And then we have our advanced engineering team.
In addition to that we provide other things. We have consulting that we do, and we do projects.
The piece that sort of pulled out there is the IT management piece.
And so what is the context for what IT management does when the IT management is being delivered by not someone within the organization, but from an outsourced entity?
Patrick Sprehe: A lot of what the IT management team does is they act as an interface between the client and our services.
So we provide reporting, which includes both reporting on IT service – help desk tickets, what kinds of tickets, the resolution time – and also reporting on the network as a whole – how many computers are there? What is the patching status, antivirus, priority alerts from system logs, that kind of thing.
On top of that, when there is an IT service issue, we help to manage the IT service issue, so if you need someone to handle an escalation or priority issue, someone you can reach out to for just a question on how service works, on what is the status of a specific ticket or issue. You know, that’s one of the things that the IT manager is often called on to do – to provide that help.
What we call IT Lifecycle Management, I’ve seen called infrastructure management elsewhere. And this is just keeping an eye on the network, on the computers and networking equipment, making sure that they’re replaced regularly, that things are up to date and working properly. That the network is clean and old accounts have been removed from the network. Old files and folders have been cleaned up and that kind of thing. And then also just being a resource to go to for advice.
So beyond the standard deliverables of IT management, there’s more advanced deliverables. They really have to do with strategic planning and consulting around technology.
Looking forward over the next few years or getting deeper, things like, you’re talking about implementing a CRM and Salesforce with certain workflows from SharePoint and that kind of thing. You definitely need to go much deeper than your standard IT management.
Additionally, there can be various kinds of IT assessments, maybe a capacity assessment.
IT security planning, Community IT has certainly seen a spike in security incidents.
IT Policy Development, Business Continuity Planning, just knowing what your acceptable use policy is.
Do you have a Mobile Device Policy or Bring Your Own Device Policy? Do you have any kind of device management? Part of what an IT manager does is help you plan around these kinds of more strategic initiatives.
Steve Longenecker: The stuff on this list is the stuff that we think of more as the IT manager is a gateway to, or the IT manager has expertise in some of these areas. Perhaps the IT manager helps coordinate bringing in another expert, whether it’s from the same MSP or perhaps from partner organizations or help identify another consultant kind of thing.
So these are not things that we think of as the basic services. I mean, that word “advanced” gives it away, but if you have an outsourced IT manager, and you’re asking them to do advanced business continuity planning, and they’re not giving you quite what you want, that you’ve necessarily got, bad IT management, I think this is definitely the next level up.
Patrick Sprehe: Exactly, right.
Steve Longenecker: So now shifting to our approach. Now we’re pulling back the curtain and talking about how we do things at Community IT for our nonprofit customers. Pat and I have been part of the leadership team that’s really been thinking hard about the IT managers at Community IT and the team that they’re on and how we want to deliver that service to our clients.
And so we came up with the values that we think are important to our team. Transparent. Professional. Respect.
Transparent definitely works for the culture of Community IT and what our clients want from us. I do think this is important to our success. It certainly is very important to our success for our clients to trust us. Disclosure and transparency are important to us.
Obviously, being professional is helpful in almost any context.
And I think a big part of our success on the IT management team is our respect. We deal with clients of varying sophistication in terms of IT and one of the things that our clients look to us to provide is expertise they can go to without feeling stupid or condescended to. It’s very important to us that if a client has a question, that that question is treated respectfully so that the door is never closed on them and there’s no need to apologize for asking a question or seeking advice on something. We want to be able to provide that service to our clients.
Patrick Sprehe : Starting from when we first start working with the client, the first thing we want to do is we want to build the relationship. We want to become a trusted strategic partner.
And so we want to understand the client and understand the business needs of the organization. From there, we move on to focusing on the business needs and make sure that we all understand the purpose of the technology.
We sometimes like to say that, we’re not a technology company, we’re a customer service company that works with technology.
The purpose of the technology is to support the needs of the business. It’s not there because it’s cool or because it’s neat or because it’s the latest fad or whatever. It needs to have a business reason before we’re going to recommend it.
We have in the past tried to talk clients, sometimes successfully, sometimes not successfully, out of doing certain projects because they didn’t necessarily make sense or there was a better or less expensive way to accomplish it.
Steve Longenecker: Do we make IT just fix the problem and make IT just work? or do we focus on finding out the business need first? Sometimes, with a new client, there’s broken IT that needs to be fixed right away before you can even start asking about business needs.
But even here, the example we talked about, was a new client, just on-boarded. They’re really struggling with wireless and it’s just killing them. And they’re like: “We need to fix the wireless!” And we do need to fix the wireless if there’s a business need for it. But even that conversation, it’s not like it has to be a long, drawn out process. So what do you need wireless for? And where is it not working? There is still a conversation about business needs, even on basic things like that.
Not that we’re trying to discourage our clients from having good wireless! Because we want them to have good wireless, but understanding exactly what that wireless is being used for: Is it being used for webinars or is it being used for phones…?
Patrick Sprehe & Steve Longenecker: …Would it need to support a guest network? Do you need some wireless outside? We have some clients that are schools, that have a playground, that need wireless outside. Yeah, yeah. So there definitely would be security regulations that apply to all that stuff. Yeah, yeah.
Patrick Sprehe: Typically, a conversation like that is, as Steve said, very short, just a few questions, but it still needs to be taken into account.
And then, of course, beyond discussing the business need, we want to basically make IT work. We want to fix any problems that are there, patch any risks. Remove distractions – we’re talking about getting rid of old equipment, clearing out old accounts, making sure we know what we have in inventory, that kind of stuff, to just make IT work.
Beyond that, we start to look forward. And so we want to talk about looking ahead and modernizing IT. It’s very common to recommend moving up to the cloud.
We work exclusively with nonprofits and nonprofits receive a lot of discounts in cloud services from Microsoft, from Google, and from other organizations.
And even beyond that, when we do move forward, we want to make sure we’re picking the right solution. You know, we don’t want to recommend the priciest fancy solution. We want the correct solution.
So digging in a little bit to Making IT Just Work.
And very often this is where an organization is willing to just stop, especially some of our smaller organizations. Once IT is working for them, that’s all they really need. All of the actual business tends to be just a question of outreach, of meeting and talking and working on the computers.
So there’s not a whole lot of strategic discussion that goes on beyond this kind of thing. Maybe they adopt certain best practices; two factor authentication is standard best practice, but sometimes this is where organizations are happy to just stop.
Steve Longenecker: Pat, “Making IT Just Work.” Is that something that, if we onboard a new client, they should expect to have done in two weeks, two months or is there no [standard timeframe]…? What’s your sense of that?
Patrick Sprehe: That’s a good question. There’s not really a set timeframe. Generally, even just talking about building a relationship, that’s not something that happens overnight in and of itself. So very often that can take a few months. Some of this, it’s not like you do one then the next, then the next. It’s kind of an ongoing process.
In terms of making IT just work, I would say that that’s something that can take months, it can take a couple years, it kind of depends what the capacity for change is at the organization and how much needs to be changed.
Steve Longenecker: Yeah, that was my thought, too, is that often, clients come to us because IT is not working. We often are on-boarding clients that have collected what we call “IT debt.” There has been a lot of underinvestment and that speaks to the capacity that you just said, that sometimes it’s clear what the way forward is to making IT just work, but it’s expensive. If everyone’s running computers that are six years old, step one might be to replace all those computers. And that’s not something that cash flow necessarily allows an organization to do in the first four weeks of a relationship.
This is sometimes a question of a longer process that is about prioritizing, and what are the things that are hurting us the most? That are the lowest hanging fruit that we can resolve and it is iterative, and it takes a while.
Patrick Sprehe: That’s right, that’s exactly right.
So beyond making IT just work, we try to look forward.
We pull from our Solutions Menu. So this is essentially a menu of solutions that we keep track of that we’ve used to solve different problems that either our clients have brought to us and that we’ve helped resolve or when we have seen an issue and we’ve reached out and found a solution that we can share with our clients.
Steve Longenecker: The IT management team, we’re responsible for maintaining the Solutions Menu and making sure that it’s kept up to date.
If we decide that a particular firewall isn’t as good, maybe the company that made it got bought and the quality of the service of the support has declined, and we no longer really feel like we should continue to recommend that solution, we’re going to find a new one.
We find a new device manufacturer and we test it, we try it, we test it in a number of situations and we feel like it’s really good, then we add that to our solutions menu and remove the old one. And that’s a big part of our ability to deliver goods and services that we’re constantly keeping track of and collecting data from a wide range of clients on what works and what doesn’t work.
Patrick Sprehe: Yeah, that’s just part of our ability to serve these solutions. It also makes our service better if we know the technology that we’re working on.
Alongside our solutions menu is our Service Catalog. And these are the services that we offer.
We work with vendors to provide things like spam filtering, cyber security awareness training, server or workstation backup, Cloud Service backup for backing up things like Office 365 or Box or Dropbox and we work with a lot of these vendors, because they are able to work with an MSP. We can centrally manage and monitor a number of clients and keep the client data separate and secure.
Within the IT management team itself, we also do executive business reviews [EBR] for our clients. This is an ongoing strategic level discussion with leadership about what IT initiatives should be pursued.
And this is really one of the main ways we try to align, at a very strategic level, the business of the organization with the IT. We start going back as far as looking at the mission of the organization and what the strategic objectives of the organizations are to determine what the strategic IT objectives should be. And then from there, what the IT initiatives should be.
On top of that, we can provide assessments and recommendations.
You know, we want recommendations that are executable and that are appropriate for the client. And then the budgeting and planning along with the assessments and the EBR should all align with the strategic planning for the organization.
Steve Longenecker: So if you are working with your outsourced Community IT manager, understanding your own organizational culture is critical to helping us succeed. All of us succeeding together can include anything from understanding how deftly your users respond to IT changes, how sophisticated they are and how quick they are to pick things up, to how decisions are made and what the process is to make sure that IT gets its share of investment, and so on.
Being open to the partnership goes without saying, but I think this goes back to having a certain degree of trust and hopefully the transparency and respect and professionalism that we show helps that grow and fosters it.
But you know, it’s going to be hard for an outsourced IT manager to be successful if the client contact they’re working with is reluctant to trust their outsourced IT manager and there needs to be a degree of ownership of IT.
IT cannot just be owned by your outsourced IT manager and your managed service provider. There has to be a degree of ownership by the organization itself and understand that they’re making choices and investments and have ownership of that.
Believing in IT’s return on investment is also important.
Pat is right that oftentimes, some of our clients make quite a few investments, have come to us in a lot of pain. They make investments, they pay down their IT debt, so to speak. We make some changes. Because technologies change, you no longer need to have email on your server, or you can move your files to the cloud. And you can leverage cloud services and so forth. And you make some changes, you implement multi factor authentication and tighten up your security practices, start doing training. I’m listing all the things that we recommend.
And at some point, you might get to the place where you feel like you’ve really achieved a level of stability and you’re always ready to ask, what’s the next thing that I can invest in that will deliver a return?
But we do believe that it is okay to have the answers for a given year. Being, “We can stay the course right now. You’ve done a lot of things, and I think right now, we’ll wait and see if something new develops in the next year. But for now, it looks like you’ve done the things you need to do.”
So we’re not saying that you have to constantly be spending money, investing in IT, over and above what you need to keep things running.
We do believe strongly in lifecycle management and replacing things that are old and so on.
But we also have clients that, despite our entreaties, don’t really believe that. They think of IT purely as a cost center and not as an opportunity to spend a little bit of money to get a lot of returns in terms of operational efficiency and effectiveness.
We also really appreciate when our contact – it is helpful when our contact on the client side is not the assistant to the operational assistant. Having some efficacy within the organization is really helpful, because we can make recommendations and we can have our client contact agree that those recommendations sound really good to him or her and there can be a high degree of trust with that person. But if they don’t really have any pull in the organization to get things done, then we do come to a dead end sometimes.
Patrick Sprehe: Yeah, I think a lot of this is that we’re talking about, IT management as a strategic benefit, a strategic resource, and so if we’re talking to an intern who doesn’t have any insight into the strategy of the organization…
Steve Longenecker: Yeah, thanks for adding that. Yeah.
Patrick Sprehe: …it’s basically just, you know, spinning our wheels in some ways.
Steve Longenecker: Thinking about IT strategically and realizing that, in fact, IT should meet business needs and that it’s no longer just doing things the way IT thinks it should be done, but reflecting on your business needs.
That is a question to always ask yourself and in particular in the context of IT management at your organization, whether it’s outsourced or internally managed.
If you do have outsourced IT management or you have an MSP and you are hoping that they’re providing IT management and you’d like to check on that, asking for an IT roadmap seems like a really helpful thing, from our perspective, to do and something that we are glad to provide for our clients.
It’s not something that is done in five minutes. So depending on the way services are paid for, it might cost a little bit of money. But it also is a really helpful process to not just think about IT of where it is now, but thinking about a three to five year plan for where IT might go. Then that set of recommendations, you should look at it and be able to see where the business needs fit within that roadmap and where it gets you.
Johan Hammerstrom: All right.
So with that, we go to questions, we have a question here. So they’ve had an issue, this organization, this person has had an issue with revolving-door techs. My assumption is that the MSP sends in different techs every time and it’s resulted in real inconsistency and loss of confidence that the people they’re sending in are actually solving the issues.
So that’s the problem. And the question is, is that the norm? Is that what should be expected when working with an MSP and do you have any suggestions for how they can avoid that situation?
Patrick Sprehe: I’ll start by taking a stab at this. So broadly speaking, we recognized not this specific issue, we’re very fortunate that you know, generally the techs who work with Community IT, like working with Community IT, so people tend to stay around for a long time.
So, our techs tend to stick around, but we did find that we were having an issue with, it’s very difficult to get knowledge about a client out of somebody’s head, so we implemented a documentation system, which has been a very great help in that kind of work.
So it might be worth asking your MSP, do they have a documentation system?
How do they share knowledge on your network with their techs? How do they make sure that their technicians know what they’re walking into, and have that kind of conversation.
I know that we also offer on-site supports [in the Washington DC area and suburbs], so we offer just recurring on-site support if you want to have someone coming in weekly or monthly or something like that that might be worth asking as well. [Nationally, we work with many clients who don’t need on-site support, just remote IT support.]
Steve Longenecker: So yeah, that’s really great thoughts, Pat – the IT management team and IT managers individually also have been sources of continuity.
We are fortunate, I don’t know what the industry looks like in terms of numbers, but my impression is that there is a lot of job hopping and so I do think that perhaps technicians can be viewed as almost a commodity and technician jobs from technicians’ perspective are always available and so you jump around after a few years. So, there probably is more turnover than Community IT experiences on a staffing side and that’s a tough nut to crack for an IT service provider. We do have less of that than I think a lot of firms do. At the same time, we also have staffing turnover, but in a different way than maybe we’ve just been discussing. We have staffing turnover when people get new jobs within the company.
We always want our clients to feel a sense of continuity and that the people that are coming to them know who they are, and can instill confidence in our clients that they’re able to come in and do their jobs well.
Johan do you have thoughts on it? I mean, you obviously see the big picture.
Johan Hammerstrom: Yeah, looking at this question from another angle, at the risk of getting into the weeds with ITIL (IT Infrastructure Library), one of the real valuable components of the ITIL framework is how it classifies IT issues into three different categories.
And one category are incidents, which is an interruption of expected service. Another category is service requests, which is a change to existing service and a third category are what are called problems.
And the value of categorizing IT issues into those three buckets means that you can really adjust your level of effort appropriately, because it would be very expensive to have the same person always available to solve every problem that comes up.
So there’s a lot of value in having an outsourced help desk do account provisioning and password resets and changes to folder permissions, which are all service requests that don’t really require special knowledge of the organization or the network and sometimes quick incidents need to be solved quickly.
But at the same time, you do need someone who owns the whole thing and can look at particularly systemic issues that are affecting a large number of staff in the organization that may not seem related on the surface, but once you look at it, if you have a different technician working on it a unique problem each time, and no one looking at the big picture they may not see that there’s a pattern there.
So that’s called Problem Management and typically, that’s something that an IT manager would keep an eye on and that allows you to both economically resolve the incidents and service requests as they come up, while at the same time having someone who’s able to identify these broader systemic issues.
And I think what we found is that, if you’re addressing that question of ownership of the different layers: who owns creating new accounts? Who owns responding to interruptions to service? Who owns the problems? Then all of those get resolved more effectively and then it no longer impacts the staff’s experience of IT.
I think what I heard in the question is, obviously, it’s great to see the same person every time and getting that familiarity is wonderful.
But I think the bigger issue is that having the rotating cast of characters coming in to fix issues means that those systemic issues aren’t really getting resolved and the wheel is having to be reinvented every time.
So what I would suggest is when you’re working with your MSP, ask them about that. Do you use ITIL? What framework are you using to manage the IT systems? Do you have a problem management framework in place? Who takes ownership of the network as a whole? And make sure that those systemic issues are being addressed. So those are the questions that I would pose to the MSP. [Community IT did a webinar on 12 Questions to Ask Your MSP, which you can use to help vet your current or prospective MSP.]
There isn’t a way to get them to retain staff, or necessarily dedicate one person to your organization, but I think if you can question them about the methods that they’re using for solving problems, that might yield a positive outcome.
All right, I want to thank everyone for their attention today. Have a great afternoon. Thank you.
Community IT has been serving nonprofits exclusively for twenty years. We offer Managed IT support services for nonprofits that want to outsource all or part of their IT support and hosted services. For a fixed monthly fee, we provide unlimited remote and on-site help desk support, proactive network management, and ongoing IT planning from a dedicated team of experts in nonprofit-focused IT. And our clients benefit from our IT Business Managers team who will work with you to plan your IT investments and technology roadmap, if you don’t have an in-house IT Director. When you need technology change management, our ITBM team can help you communicate what the change is, why your organization is doing it, and discover who it will impact.
We constantly research and evaluate new technology to ensure that you get cutting-edge solutions that are tailored to your organization, using standard industry tech tools that don’t lock you into a single vendor or consultant. And we don’t treat any aspect of nonprofit IT as if it is too complicated for you to understand.
We think your IT vendor should be able to explain everything without jargon or lingo. If you can’t understand your IT management strategy to your own satisfaction, keep asking your questions until you find an outsourced IT provider who will partner with you for well-managed IT.
If you’re ready to gain peace of mind about your IT support, let’s talk.
Wednesday March 25th at 3pm Eastern join Hugo Castro and Gozi Egbuonu to learn how to make the transition.
Fill out the form below to request a quote. We’ll be in touch shortly to discuss your needs and take the first step toward better nonprofit IT.