2023 Nonprofit Cybersecurity Incident Report:
Emerging Trends, Practical Advice
View Video
Listen to Podcast
Part 1 includes an introduction and overview of cybersecurity for nonprofits. Part 2 covers the analysis of the 2022 data and what it means for your nonprofit. Both parts include audience Q&A.
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
View or Download the 2023 Incident Report
Is your nonprofit prepared?
Drawn from data from the calendar year 2022 of cybersecurity incidents across our small and mid-sized nonprofit client users, this report shows changes in attacks and emerging threats.
Using this real and timely data, Matt walks through recommendations and outlines the practical steps your organization can take to prevent the most frequent attacks.
He covers new threats and ways to think about continual training for your nonprofit staff around evolving cybersecurity issues.
You may also be interested in downloading the free Cybersecurity Readiness for Nonprofits Playbook to review a framework for focusing on your cybersecurity fundamentals.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT is proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community.
Presenters:

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She was happy to moderate this webinar.
Transcript
Carolyn Woodard: Welcome very much to the Community IT webinar, our annual nonprofit cybersecurity incident report. We’re really happy to be able to share this up-to-date data with you on the types of incidents we’re seeing among the clients that we manage, which can help you be more prepared and able to prevent the most common attacks.
Our learning objectives for today are for you to:
- understand the cybersecurity landscape for nonprofits
- understand the Community IT approach to cybersecurity
- be familiar with the instant types and data from our 2023 report, which is data from 2022
- learn basic steps to take to secure your nonprofit.
About Community IT
And before we begin, if you’re not familiar with Community IT a little bit about us. We’re a 100% employee owned, managed services provider. We provide outsourced IT support and we work exclusively with nonprofit organizations. Our mission is to help nonprofits accomplish their missions through the effective use of technology. And we are big, big fans of what well-managed IT can do for your nonprofit. We serve nonprofits across the United States, and we’ve been doing this for over 20 years. We are technology experts and we are consistently given the MSP 501 recognition for being a top MSP, which is an honour we received again in 2022.
Let’s get started with this discussion of the cybersecurity incidents we’ve seen over the past year, I’ll start by introducing myself. My name is Carolyn Woodard and I am the marketing director at Community IT. I will be monitoring the Q and A and helping Matt with his presentation. So Matt, you want to introduce yourself?
Matthew Eshleman: Yes. Great. Thank you for the introduction, all the background. I’m really looking forward to today’s webinar as this is our fifth annual nonprofit cybersecurity incident report. As Carolyn mentioned, my name is Matthew Eshleman and I’m the Chief Technology Officer at Community IT.
In my role here I am responsible for two main areas. So, one is to oversee our centralized services platform, which we use to support over 200 organizations and nearly 7,000 endpoints. And then also responsible for working with organizations for their technology strategy. A lot of cloud transformation and cybersecurity. So, I’m really looking forward to the conversation today. Make this a valuable time and answer any questions that you may have about cybersecurity at your organization.
Carolyn Woodard: Great. So, on our next slide, we have information. The 2023 Nonprofit Cybersecurity Incident Report is coming. I was hoping to have it published today so you can download it on your way home. But probably next week that will be available for you to download at about the same time that we’ll have the slides available, the podcast and the video.
I also wanted to make sure to mention that we have a playbook available on our website, Cybersecurity Readiness for Nonprofits.
So, those are some resources that we have already on our site, and we will have the incident report available for download, too.
Poll 1: Cyber Insurance
All right, so now we are going to start with a poll.
Does your organization have cybersecurity insurance?
So, you can choose yes, no, planning on getting it or not really applicable.
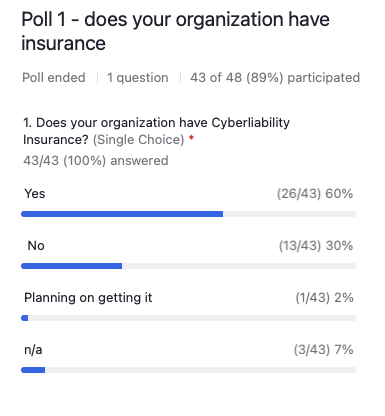
Matt, can you see that?
Matthew Eshleman: It looks like of the respondents here today, the majority do.
About 60% of respondents say yes that they have cyber liability insurance with about 30% saying no, and then the remainder saying not applicable.
I think that’s a high rate, maybe I would’ve expected a little bit higher. Maybe a follow up question in the chat, you could respond. How much has your cyber liability insurance gone up in the last couple years?
I know as a managed service provider, rate renewals went up pretty significantly. Hopefully that increase looks like it’s slowing down over time, but it is a challenge for organizations to receive effective coverage in this area.
Poll 2: What cybersecurity controls have you put in place?
Carolyn Woodard: Okay, so the next poll is:
What cybersecurity controls do you have? So if you have insurance, you probably know that you have to go through this whole long questionnaire of what you’re doing. And this is a multiple choice question. So, any of these things that you’ve implemented.
Multifactor authentication, MFA, you have security awareness training, you have endpoint detection and response. You have SOC/SE, SIEM, you have MSSP, you have penetration testing, you have SSO single sign-on, you have MDM or none of the above.
If you don’t know what this terminology is, that’s fine. These are common things that are asked on those cyber liability questions. So, we just wanted to know if you know that you have these or don’t have this.
And we have a question in the chat, Matt, while we’re letting people continue to fill this in. What does cyber liability insurance cover?
Matthew Eshleman: Cyber liability insurance I would say one, it’s different from liability insurance. If something gets stolen at your business or something happens to property at your business, there’s property and liability insurance for that.
Cyber liability insurance really covers loss related to cybercrime. If you have ransomware, if your website is hacked, if your files are encrypted and you have to pay ransom to get it back, those are all things that cyber liability insurance would cover. And so that would cover paying for things like legal representation, incident response teams to go in and evaluate what happened. It may cover PR if you need to have interaction with the public about things. It may also cover things like breach notification if you need to tell all of your members that their data was stolen and they may be at a higher risk for identity theft. So, those are the kinds of things that cyber liability insurance would cover.
Carolyn Woodard: And cyber liability insurance, if you have, would step in when you have that incident. So, it’ll give you who you’re supposed to talk to. There are some entities that you’re not allowed to interact with, if they’re some foreign states or terrorist organizations, if that is what you have succumbed to. So, they’re very helpful at that stage. If you do have an incident, they’re probably the first people that you’re going to call to respond to it.
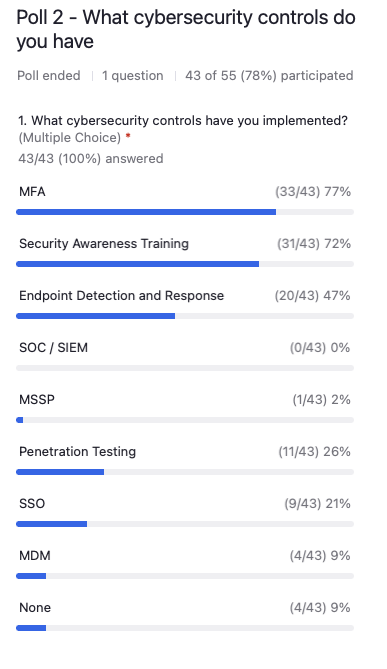
Okay. So, Matt, can you see that?
Matthew Eshleman: Yes, I can. And it’s great. I’m really encouraged that 77% of respondents have implemented multi-factor authentication or MFA, so that’s great. Hopefully by the end of this presentation people will be encouraged to get that number up to a hundred percent.
Same thing with security awareness training, very good adoption there at 72%. And then the next highest number of folks implementing controls will be endpoint detection and response. And I would say this is really an evolution of traditional antivirus solutions. So again, there’s a lot of great sophisticated tools out there that can protect the endpoint.
After that we have penetration testing or pen testing. So, we see that as a common security control or feature that people will follow. And that’s people trying to hack your network to highlight those vulnerabilities that organizations may need to patch.
And then we have about 20% of people implementing single sign-on which is a way to access multiple cloud resources with one set of credentials, giving a better managed way to access information.
And then less than 10% of folks have implemented MDM or Mobile Device Management solutions, or are using an MSSP, so a Managed Security Service Provider that is just focused on security tools and it doesn’t look like anybody has implemented a SOC or a SIM. Those are more sophisticated management platforms that allow typically a vendor to take log information from your endpoints from Office 365, from Salesforce, from Box, bring it all into one platform, correlate all that data and then be able to identify if there’s threats that are moving through the system. So, again great to see that information and thank you so much for sharing that.
Carolyn Woodard: I just want to reassure everyone, if you don’t know what all those acronyms are it’s probably some of the things that Matt was talking about for really large organizations, very sophisticated organizations.
Matthew Eshleman: I just wanted to start off with a little bit of an infographic here actually from Microsoft. This is from Microsoft’s 2022 Digital Defense Report. I think this highlights how think tanks and NGOs are relatively highly targeted by really sophisticated hackers, what would be called nation state hackers.
This is an important realization for nonprofit organizations to understand is just because you do really good work, or just because you have a great mission, or just because you don’t have that much money or that many resources, doesn’t mean you’re going to be immune from cyber-attacks.
And so this is something where the data from vendors like Microsoft really show how much organizations are targeted, particularly in that think tank and NGO space.
This is something that we really see born out in our interactions with the FBI. Nation state actors are not particularly interested in your organization’s research and white papers, which are ultimately going to be published. These nation state actors are really interested in research and information about the staff that you have that could be used potentially later on as part of an influence operation. Again this was a helpful realization for me to come to understand why threat actors are targeting these nonprofit organizations in government adjacent positions. Because they know that if you’re a researcher at a think tank or a nonprofit, in a couple years when the administration changes, you’re now going to be in the government.
And so they’re interested in getting information about you as an individual that could be then used later on as part of a leverage or influence peddling.
It’s really interesting reading and continues to build our understanding in terms of what organizations are targeted and the method of that targeting and how it’s happening.
Carolyn Woodard: With this landscape in mind of these kinds of threats against our sector,
What did you see broadly in 2022 that impacted the landscape and the way people are responding?
Matthew Eshleman: Community IT has been working with nonprofits in their IT support for over 20 years. This is the fifth year that I’ve written this report that looks specifically at the cybersecurity data that’s coming in from those 200 clients. And so I think we’ve developed some good metrics and views on the types of attacks that are targeting the nonprofit sector. I think there is a lot of fear, uncertainty, and doubt out there that kind of makes us all anxious. And so it is important to understand what’s actually happening with small to midsize nonprofit organizations so that we can design and respond to these threats appropriately in a way that makes sense, that’s cost effective, and addressing the highest risk.
A lot of the stuff is automated with the evolution of AI and how that’s being brought into the tech space, right? That’s only going to accelerate these kinds of automated attacks. That’s going to make it easier and cheaper for hackers to design tools to target us.
And the same thing on the security side, right? We see a lot of those automated attacks, viruses, malware, all of that stuff is blocked, right? There’s a tremendous amount of stuff that doesn’t get to you because a lot of these anti-spam tools, antivirus tools, are doing a pretty good job of preventing stuff from making its way to your computer.
I would say one of the things that we noted in our data from last year is that we saw a number of incidents where it wasn’t just the organizational account that was targeted, but it was a user’s personal account.
And then that personal account was used to gain backdoor access into other systems. A personal Gmail account was maybe used as the password reset email for an organization’s LinkedIn account or somebody’s Facebook account. It was used for their organization, but that got hacked through their personal account.
And so we’re seeing really a blurring of boundaries between work resources, personal resources and so the same controls that you want to put on your work accounts really need to extend to those personal accounts as well.
And then I would say those account compromises, the email spoofing, the phishing, it just continues unabated. I think we’ve seen some flattening out of the number of attacks reported. And I think we’ll look at that data a little bit later on, but I think we continue to improve the tools that we use, which helps reduce that. But unfortunately it’s not dropping significantly and it’s still occurring at a relatively high rate.
Other things in the sector that are driving a lot of the kind of discussion around cybersecurity is cyber liability insurance. Part of our question was how many people have it.
Over that five years, at the beginning of our incident report, it was very easy to get cyber liability insurance, one page application. You didn’t even have to say that you had enrolled in anything, and you could get very affordable coverage that would be pretty comprehensive. Nowadays we’re seeing policy renewals go up by 50%, 75%, organizations not being able to get coverage, and then also needing to actually implement all of those different security controls, multifactor on everything, multifactor on your servers in your office, incident response plans, backup plans, disconnected and encrypted backups.
The market has really just tightened up because of how common cyber-attacks have become and how expensive it is to respond to them. And so the cyber liability insurance providers themselves are really tightening up the underwriting requirements.
Remote and hybrid work requires updates to policies and training. Again, I think we’re now firmly in a hybrid work world for most of the organizations that we’re working with. We see a lot of organizations that are a hundred percent remote now. I would say the majority of our clients are probably in that hybrid environment, two or three days in the office, working remotely. And I think the policy side of things hasn’t really caught up to that. And so, organizations are still kind of grappling with how to manage that from a policy standpoint.
The other thing I would highlight at the very end is we noticed in our data that there was a really big spike in wire fraud incidents. And that to me just highlights that fundamentally this is cyber-crime.
For most organizations, if you’re not into the think tank space, your highest risk is really going to be targeted towards wire fraud, gift card fraud, and updating payroll information for employees.
And that can be really significant. And the response to that is not just an IT cybersecurity response, but it involves other aspects of your organization in terms of your finance controls interacting with your bank, the vendors that you use. And so that does require a coordinated effort across many different departments at the organization. But it is something that’s really critical because of the actual financial loss that that can represent. I would say it’s not uncommon to see six figure losses in this area if your organization falls victim to a wire fraud campaign,
Our Approach to Cybersecurity
Carolyn Woodard: Yeah, in the news, you’ve seen some nonprofits that just wired the payment to the wrong bank, and then it’s gone. This is the chart of our approach to cybersecurity. I want to remind everyone that this is in the playbook, which is available on our website, and I just put the link into the chat so you can download that for yourself.
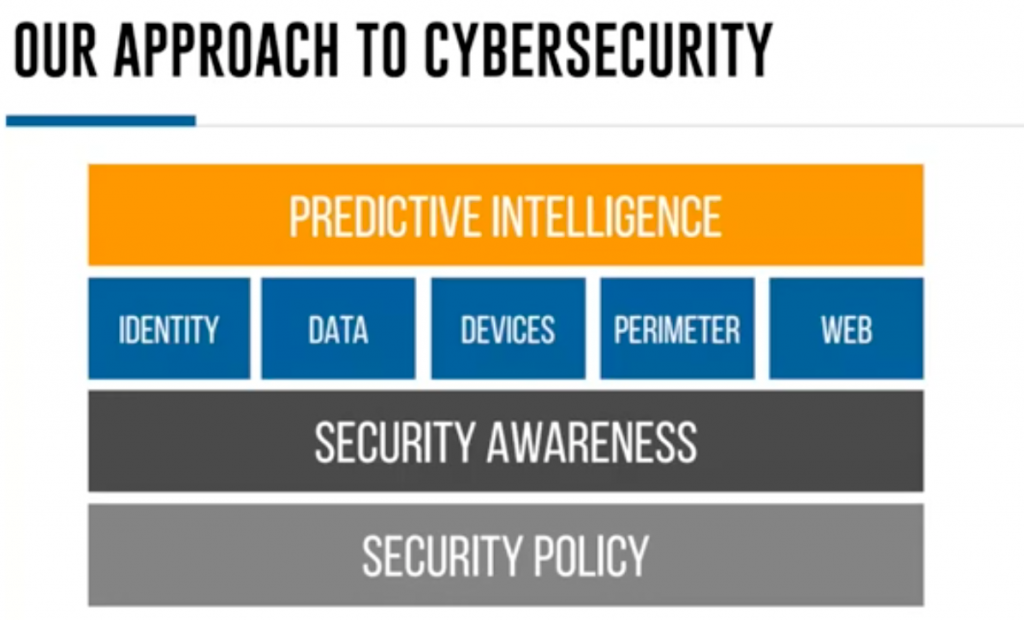
I’ll just run through the layers here.
We start with your security policies and your documentation as that lowest layer such as your acceptable use policy which should be part of your employee handbook and should be regularly updated.
Matt was just mentioning hybrid work environments. If you have not updated your acceptable use policy after going hybrid or going remote, that is definitely something that you need to look at as soon as you can.
There’s a layer on top of that of security awareness and staff training. We often say that your staff are your eyes and ears. They’re the ones who are going to see if there’s something unusual happening, or something’s just not the way it’s supposed to be, or they’re the ones that are going to be asked to make the bank deposit to the wrong numbers. So, they definitely need to have up-to-date training.
There’s the layer of things that your IT department or your outsourced IT should be taking care of. These are all ways to lower your vulnerability using common tools and automation, as Matt was saying earlier.
And then that top layer is needed if you’re working in a specific advocacy space that may make you more of a target. If you’re a larger organization, you may want to invest in testing your system. Those tools are quite expensive, and they can be overkill for the types of hacking attempts that most of you on this webinar will be facing. So, hopefully that’s a little bit of a reassurance, but that’s how our approach to cybersecurity goes.
Foundational Security Practices
Matthew Eshleman: It’s important really to start with that foundational piece of policy and people. There’s lots of technology things that can be done, but if you don’t have those foundational elements in place, it’s really hard to build an effective cybersecurity program.
Speaking of some of those foundational pieces, I just want to talk a little bit about foundational practices that every organization should have in place.
IT policy, I saw there are some questions around if we have any templates, and I would say yes, we do. So, if you drop that note in, I can follow up and provide our IT acceptable use policy template. That does include a section around BYOD, that’s bring your own device, or what’s the practice around having staff use personal devices to access work resources? That’s an organizational decision that needs to be made.
Security awareness training. I was really glad to see that high response rate. I think the best money that you can spend in terms of securing your organization is if you can train and educate your staff so that they know how to identify those malicious emails. Honestly, the vast majority of threats that organizations are going to see are malicious messages that are going to trick you into clicking a link, sharing your password, or maybe giving away your MFA information. And so, educating staff is just absolutely critical and provides a lot of value.
Then there’s some boring stuff, right? Operating system and third party patching, this has been a foundational recommendation for a long, long time and having a regular routine update to be able to deploy those changes and ensure that they’re actually happening is an important element of an effective program along.
Add good antivirus or endpoint detection response tools web filtering and MFA.
These are all things that Community IT provides as part of our device management. So, for all those 7,000 devices, we are making sure that all these things are happening because security is really a game of fundamentals. And these attackers are really going to exploit the weakest link.
If your operating system isn’t up to date or you aren’t updating your iPhone, you’re at risk of being exploited by those different threat actors that are using malware to get onto devices. So again, make sure that for your organization, you can say, yes, we’re doing all of these things. And then once that’s in place then you can move on to some of the higher level security controls.
Carolyn Woodard: I wanted to break in just quickly and say there have been a lot of people asking about templates for documents and I have put Matt’s contact information in the chat. It’s also in one of the slides at the very end, so don’t worry if you missed it. But you can get in touch with him for some of these templates. And we are working on a resource library area of our website. So, we’re hoping to get some of these templates up there too. They’re just not quite on our site yet.
Matthew Eshleman: Great. Well, Carolyn, do you want to talk a little bit about that shift for organizations?
Cybersecurity Impacted by Remote/Flexible Work/AI Tools
Carolyn Woodard: Yes. You had mentioned earlier that the pandemic and that shift to remote and flexible work environments has impacted so much of our nonprofit work life, and of course also our personal lives.
Can you tell us what you’re seeing in cybersecurity with relation to downsizing an office, getting rid of an office, working flexibly, working remotely?
Matthew Eshleman: Yes. Increasing spear fishing, targeting personal accounts, your home network, that work boundary is now basically wherever you are. And so, we’ve seen personal accounts be targeted and then used to exploit work resources. There’s some pretty famous recent accounts with LastPass. That whole breach occurred because a senior developer’s home device was compromised. We’re probably not all dealing with that sensitive of information, but I think it is a good object lesson. That just shows how connected our technology lives are. The hacker knows your work email address, they know your home, your personal email address as well. And so they will go after both; there’s no respect for our work and home boundary.
I will also say here that finance teams seem really both targeted and susceptible to fraud working remotely. I think some of that interpersonal connection we lose, a lot of that increased automation is also exploited by hackers. “Update those wire payments. I’m having a problem with my bank.” These are all stories that we’ve experienced ourselves and the hackers are using that in order to extract financial gain from us.
I talked about it a little bit before, but this explosion of AI that’s come across all of our inboxes really accelerates innovation for all. So, it’s not just going to help us write better emails or fundraising appeals, but it’s also going to help the hackers write a more convincing email to get you to click on a link that looks like it comes from a partner organization.
It’s going to help them improve the scripting that they’re using to build some of the tools. It’s probably also going to help inform the security systems that are available.This increasing sophistication, we’re going to see in the security threats as well.
As I said we have really good tools in place and available. The tools themselves are great. I have a lot of confidence in endpoint protection. There’s a lot of great stuff out there, but it still needs to be set up and needs to be configured, and it needs to be managed. There’s not a lot of systems where you can just set it and forget it. These technology platforms are really sophisticated and require staff that know how to use it, know how to follow up. And it’s often a challenge for smaller organizations to kind of maintain all of that skill set in-house to use the tools effectively.
Carolyn mentioned this policy foundation, it’s a continuing struggle and battle to keep those policy documents up to date. But it really is important to being able to effectively manage and support your organization as the work style changes, work locations change and the technology to support all of that continues to evolve. So, the technology is there but it’s our policy and operations that really need to catch up.
Carolyn Woodard: Also in the transcript we’ll have all of these tools and links included as well.
Poll 3: Are you prepared?
After hearing Matt’s brief overview in the first half of this webinar,
How well do you feel your organization is prepared?
We’re as on top of cybersecurity as an organization can be, we’re doing a pretty good job and we know it’s important. So, those are both pretty big hurdles.
The third choice is, we know it’s important, but we don’t know if we’re doing enough and the fourth choice, if this is you, we see you – it’s overwhelming, we haven’t done much, but close our eyes and hope. And then the fifth choice is, it’s not really applicable.
We had a quick question Matt, in the Q and A about tools for training. And I don’t know if you were going to talk a little bit later about KnowBe4. I put the link in the chat because that is a great way that you can be prepared at your organization.
Matthew Eshleman: Security awareness training in general is really important. We did a webinar on this to talk about some different tools a while ago.
There’s three things that you can do to take it on your own. We use a tool called KnowBe4 to manage security awareness training. And I really like it because we can do both test phishing to see how folks are doing, who’s clicking on what and do some scoring there. And it also gives you a really good library of online training resources that range anywhere from a three minute interactive game to 15 minute short training to little mini-series that talk about different cybersecurity topics. And so, all of that is kind of wrapped up in their learning management system that gives staff online access to those different training resources so you can track progress and just ensure that it’s happening. We really see progress over time after organizations have made the decision to implement that tool.
Carolyn Woodard: Okay. I am sharing the poll.
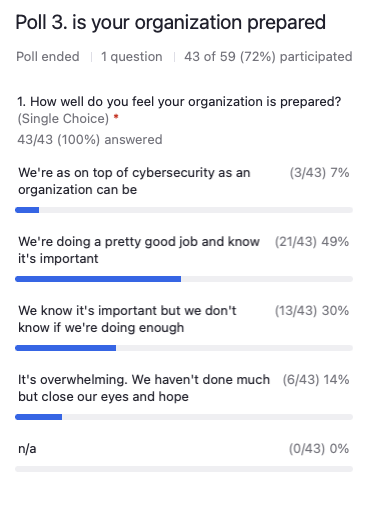
Matthew Eshleman: It looks like we have a little bit of a bell curve here. So, almost 50% feel like they’re doing a good job, and 30% feel it’s important, followed by 30% say we know it’s important, but we don’t know if we’re doing enough. And then kind of on the ends there, we’ve got 14% of folks saying it’s overwhelming and we haven’t done much, but close our eyes and hope followed by 7% of folks saying, Hey, we’re doing all that we can and we’re pretty confident in our abilities.
So, no matter where you are in the cybersecurity world, there’s always something new to do and there’s always another change to make. There’s always some new threat to respond to. So it’s certainly a living and breathing process.
Carolyn Woodard: But you’re in this webinar, so already taking steps. So, you should feel good about that.
Definitions
Matthew Eshleman: All right maybe we should have had this in the beginning part of the webinar, but just a little bit about the definitions we talk about in our report.
Threat actor, that’s the person, and I think it’s helpful to think of it that way, right? It’s not just some nameless entity. They’re actually people on the other side of the computer that are sending you those spear phishing messages that are financially motivated to get you to pay something. So, I think it’s important to understand that’s what we talk about.
We have the security incident. So, that’s whenever we have the makings of an issue. That’s something that could potentially compromise the integrity, confidentiality or availability of an information asset.
Whereas the breach is actually a confirmation that something bad has actually happened.
MFA, that’s Multifactor Authentication. Again, that combines something that you know which is your password, along with something that you have which is often an app on a smartphone or it may be something like a physical security key that could count as multifactor authentication.
Single sign-on gives us a managed and secure way to have one really well protected username, password, MFA combination that allows us by policy then to get into the applications that we need. At larger organizations, this can be great because it also helps remove access to applications. As staff are on-boarded, they’re granted applications when they leave, there’s one place to remove access to applications.
We have spear phishing. Those are targeted messages that combine some unique information about you and your organization and where the sender is obfuscated. We don’t know who’s actually sending the message.
Spoofing would be similar, perhaps used in conjunction with spear phishing to obfuscate who’s sending it, make it appear like it’s coming from your own organization or a colleague to mask the identity of a sender.
We have ransomware, so that would be the attack where files are encrypted. Then to get access to that information, you need to pay a ransom. Comes back to financial motivation. Typically that’s paid in crypto currency because it can be anonymized. That’s why it’s a favourite of these threat actors is that they can anonymously get paid.
And then we have supply chain attacks. That can be an attack where maybe you’re doing everything right for your own organization, but you’re working with a partner or you have your data hosted somewhere, or you’re in a hosted system and that vendor is compromised and then you as a result are impacted. Particularly because we have a lot of cloud solutions in place there can be supply chain attacks that impact organizations, even if you, yourself have not been exploited, but maybe the vendor that you were using had a ransomware attack.
A lot of different acronyms and a lot of terminology that I think it’s helpful to define and understand. If there’s an acronym that you don’t understand, we’ll try to define it.
Carolyn Woodard: A lot of these terms are on our website as well, so you can look through our cybersecurity resources there.
2023 Nonprofit Cybersecurity Incident Report Summary
Report – Sample Size
Matthew Eshleman: Well, yeah, let’s dig into it. And we’ve been talking a lot about the big picture. And so, I think it’s helpful to understand the sample size that we are talking about. As I mentioned, Community IT at the end of last year had about 6,500 endpoints. So, we had about a 500 increase from our sample in 2021.
I think other interesting things to note, just kind of as an aside, we drop Windows servers. We continue to see organizations move to the cloud, and that’s been a big part of our work as organizations move to hybrid, migrate to other systems. The number of servers in play is really shrinking. Windows workstation’s growing/holding steady a little bit. We’ve had a lot of growth in our Mac support environment.
And so, we support Mac and Windows and whatever people feel most comfortable with to be productive. So, that’s our sample size that we are that we’re looking at.
What we didn’t include here is kind of all of the alerts that were blocked. If we would include all of the spam messages that our systems blocked or all of the suspicious threats that were blocked on the endpoint, it’d be hundreds of thousands of results. And so, we’re really focused on those security incidents where things caused us to take another look or were submitted to us by end users.
About 11,000 targeted phishing attempts were proactively blocked with some of our support tools. Over a thousand suspicious threats were detected and automatically eliminated. And so, we have a lot of those systems and processes in place to block and prevent things from even happening, so we can be efficient in our response.
When we look at the cybersecurity incidents, we kind of have broken this apart a little bit to provide some more context.
High Risk Threats
And so, here we can see high risk threats. So, whenever these kinds of tickets come into our system, they get a lot of attention. The first one there is what we call brute force attacks. This is something we added last year. That is a message to us that an organization’s typically on-premises resources are being targeted.
If you still have servers in your office and those are open to the world at all, even if it’s a remote desktop or you’re hosting a web page, those systems are being targeted all the time. And if you have a misconfiguration in your firewall or some other problem, that will show up as hundreds and thousands of failed login attempts. That really throws a lot of triggers for us in order to react and respond to make sure that we’re closing the door. Because threat actors are still relying on server infrastructure to initiate a lot of attacks. And so, whenever our monitoring systems detect that, lots of red flags go off and we have a quick response to identify the problem and put remediation in place.
The next highest number we had here was compromised accounts. And so you see that confirmed, right? Suspected in the medium risk, was over 250. This has become an area where we do a lot of investigation. This number’s relatively low, but again, it’s not zero.
Even with all the emphasis that we’ve had on implementing multi-factor authentication, organizations have not been able to do that 100%. And we are actually seeing cases where even with folks with multi-factor authentication, they can be tricked into giving away codes or finishing an MFA request in an interaction with a threat actor. So, we see compromised accounts still occurring at a relatively high rate because of the work that we do.
A lot of our clients are here in the Washington DC area. In our think tanks and policy area, we do see quite a few of those advanced persistent threat actors. And so again, those are typically nation state entities that are trying to get into policy organizations to figure out what people are doing and then gain information about the researchers or the individuals themselves.
So, that’s what brings us in conversation with the FBI in order to respond to some of those events. Talking about wire fraud, we did have a number of cases this year amongst our clients where they were victims of wire fraud. Typically those are combined with a compromised account. So, if an organization has an account compromised in the finance department, typically the threat actor will then use that information to try to update payment information with the bank or even with other partner organizations.
Similarly, we are also seeing cases where maybe an organization is interacting with one of their partners who has been impacted by an account compromise. Maybe they don’t have a two-step verification process or independent channel to verify payment changes. And so, they will initiate a change in wire transfer information at the request of a partner. And it turns out that that partner account is compromised as well. So, that was something that we saw occur in a number of cases where there were deficiencies in both the organization’s controls and also at the bank as well.
And then the final high risk threat is ransomware, which for us was zero last year.
I think for organizations that do have on-premises server infrastructure, this is continuing to be a high threat. In the market in general, ransomware is still occurring at record levels. I think for smaller organizations that are largely in the cloud, this is probably not the highest risk that you face. But it certainly is of a high severity if it occurs.
That’s how we think about these high risk threats. It’s to provide a little bit of context. We look at the severity of a specific event multiplied by its likelihood of happening.
Low severity threats like spam have a high likelihood of occurring, but they’re not going to cause much impact and can easily be deleted or ignored, right? Other threats, like account compromise have a much higher risk level because of the severity. If your organization’s executive director’s account is compromised, then it effectively means that the threat actor has access to all the information in your organization, all the emails. That could trigger a cyber liability insurance claim and may require a lot of different reactions for the organization just to respond.
So, the things that are in that high risk threat really we treat with a lot of urgency because of the impact that it can cause.
- Brute force attacks typically mean your infrastructure is being actively targeted.
- Account compromise means that somebody other than the name or trusted user has access to that account.
- Advanced persistent threat actors, the bad guys are in your network and are really targeting you.
- Wire fraud, obviously with significant financial loss there.
So, those are the things that we view as really high risk threats.
Medium-risk area
We see things like those suspected compromised accounts and that can be alerts that we receive from our system. A suspicious login is detected or blocked and then we need to go and investigate, is that actually the user authenticating from a new location or a new device? So, that requires some investigation to rule that out.
And then the same thing here with business email compromise or spoofing. So again, those messages that I’m sure we’re all familiar with receiving. It looks like it’s coming from your executive director, Can you buy me gift cards? Or, hey, I need to update this wire payment information. Hey, can you update my payroll information? I just changed banks. It looks like it’s coming from a colleague. So, those maybe aren’t urgent or imminent threats, but if they turn out to be successful, then they can move into a different category.
Low-risk
And then finally, it’s interesting here in the low risk threats we have things like spam, which we already talked about being relatively easy to identify and also delete. But then we also have things like malware and viruses, which I would say for us and our customers, it looks like a relatively high rate.
I think most of those end up being popups, or maybe they’re the beginning of a scam to try to get you to call a support number and buy antivirus protection for your computer or something like that. But what we found is that they’re relatively easy to address and remediate and they often don’t turn into an actual, active wire fraud or something else.
And so, for as much buzz as viruses get in terms of the common security industry discussion, what we find is that for devices that are up to date, patched, have protection on it, the actual risk of viruses are relatively low.
While it’s important to have those good foundational tools in place, I like to really make sure that we’re focusing on email protection, identity and account management as strategies. That’s where we see the highest risk related to threats occurring. If your account is compromised, that’s really bad. And that happens a lot more often than we see for example, a virus getting on a computer or something like that.
Overall, we’ve categorized about 950 events across the organizations that we’re serving. And as we can see here those numbers are increasing over time. We’ve got a couple of different breakdowns of the account compromise from that historical perspective that we had.
So again, the total number is here in the yellow; we’ve added in some of these newer lines. Account compromise suspected is something we’ve only started tracking relatively recently. Whereas, the blue account compromise continues at a low level. It’s interesting as MFA adoption here was maybe 10%, MFA adoption here, we’re probably at 70%. But we’re still seeing a similar number of account compromises occurring. So, I think this is an area that we need to continue to focus on improving protection on.
Carolyn Woodard: I’m sorry, Matt, to jump in, but I want to make sure that you get to some of the recommendations. I know we don’t want to run out of time. We also had a question that came in.
Do you recommend BitLocker used on end user computers to encrypt the hard drive, and are there risks to using BitLocker?
Matthew Eshleman: So yes, I think BitLocker encrypting your hard drive in a good way is a great security practice. It’s part of our standard computer setup. And effectively what that means is, if your computer is lost or stolen you don’t have to worry about reporting that as a potential data loss. BitLocker encrypts your hard drive., so if somebody else gets access to that device the data is effectively useless to them.
Here’s our kind of visualization, looking at the number of spam, malware, virus, ransomware, brute force attacks over time. You can see spam had a huge spike between 2018, 2019, whenever we first started doing the collection.
It started at a relatively high level, starting to tail off a little bit. I think that is due in part to just better security tools. We are deploying more third party spam filtering, which I think is really effective. I think also people are just acknowledging that, hey, I’m going to get some spam and I can just delete it and I don’t really need to worry about it.
As opposed to malware, we saw a little bit of a spike here. I think that was due to some tool changes that we were making. We had better tools in place to block and prevent malware from actually occurring. And so, it’s interesting, the increase in reported incidents, I think is an indicator that things are working as expected.
And then again, we’ve got some of our high priority, high threat issues here related to wire fraud, the advanced persistent threat actors or nation state actors increasing over time.
So again, the wire fraud one is the thing that really stuck out to me as an area that requires renewed focus. It’s not just a cybersecurity control, it’s a policy and it’s a process control. We did a webinar with YPTC, Your Part-Time Controller, about this. And that contained a lot of great information about organizations that are looking at how to protect themselves about this, because it’s clear that it’s a threat.
If a hacker can ask you to wire them $100,000, that’s way easier than writing crypto malware, sending it to emails, getting somebody to install it, having them follow up with you, getting Bitcoin, right? It’s just easier to ask for money.
And I think that’s why we’re seeing a lot of this focus and energy go into spear phishing with the ultimate goal of something as simple as gift cards or something as lucrative as updating wire payment transfer information, because it’s a lot easier to just ask for $100,000 than it is to get a ransomware award in that amount.
So, what do all these numbers mean, right? We got a lot of charts, a lot of tables, lots of different incident classifications. So, what do we do with all this information? And how do we take this from, we see these things happening to how we respond?
Analysis
A couple of big takeaways for me: number one, it’s really critical that organizational leadership understands the risks that they face. Cyber incidents are not something that happens to other people, every organization is at risk. And again, just because you’re a small organization or just because you have a fantastic mission does not mean that you’re going to be immune from these threats.
You may be more vulnerable to these threats because you haven’t implemented security awareness training or you haven’t implemented automated systems to update your computers and have endpoint protection and all of those things in place. A hacker is just looking at you as a dollar sign. And so if you can get tricked into giving them $500 worth of gift cards, they’re going to take that. If they can trick you into wiring them $50,000, they will do that. So, every organization needs to understand that they’re a target. It’s financially motivated, they don’t really care about you. It’s all about the money for most of these threat actors.
At the same time, it’s not all bad. We’re seeing many of the cloud vendors that we’re using enabling secure configurations by default. I think it’s taken a long time, probably too long for organizations to do things like enforce multifactor authentication and implement these other security controls. And so the vendors are leading the way to making organizations follow these best practices. So, we are seeing that happen. Salesforce requires MFA. Microsoft is enabling secured by default. There’s a lot of those other actions where the vendors themselves are saying this is important. We’re seeing our clients get exploited, and so we’re going to take some steps to help ensure that that doesn’t happen.
All that really is done in service of preventing account compromise because it’s really at the root of so many other bad things. If your account is compromised, then that threat actor has access to all of your data.
They can impersonate you to your partner organizations, to your bank, to your vendors, to your funders. And that really is a massive risk to organizations. And taking the steps, all the steps available that you can to protect your organization or protect your account from that compromise is really the best thing that you can do.
Have a good managed IT system in place. Make sure that staff are trained and educated to identify these threats. And then finally, make sure that multifactor authentication is enabled not only on your work account, but also on your personal account as well. Just understand that that’s in play to be attacked as well.
Carolyn Woodard: Our learning objectives were to
- understand the cybersecurity landscape for nonprofits,
- understand Community IT’s approach to cybersecurity,
- be familiar with the incident types and data from the 2023 report,
- And then being able to take some basic steps to secure your nonprofit. We talked about some of those, but more of them are in the report as well.
So, Matt, if you want to linger on your contact information, I did put that in the chat. And that’s the way that you can get a hold of Matt. And we’re having some people in the chat going ahead and thanking you for sharing all of this information with us, Matt. Really, really appreciate it. I understand it’s like a ton of information, so we didn’t quite have time to hit everything. But really just thank you so much for your expertise and for answering our questions. And if you are in the webinar now and want to be able to follow up with Matt, his contact information is there to grab some time with him and just ask him your questions and talk a little bit more about cybersecurity, which I know he always loves to talk about.
Matthew Eshleman: Yeah, yeah, please feel free to reach out. I’ve been with Community IT for over 20 years. I really love the clients that we get to work with. And so, if I can help organizations improve their cybersecurity, that’s really what I’m here to do. And I really enjoy that. So, please feel free to reach out. Happy to answer any quick questions that you may have.
Q&A
Carolyn Woodard: We all have things to do, but Matt, can you stay on for a minute or two? There’s a question in here,
How do you deal with token theft? If you could take a stab at that.
Matthew Eshleman: I’m not sure if that’s token theft in terms of physical tokens being stolen or talking about the actual authentication tokens themselves being taken.
Looking at the data that we have, some of these techniques like token theft or zero day attacks targeting organizations, we’re not seeing it in the organizations where we are working. I think it is more likely that your organization is going to be a victim of a spear phishing attack that leads to somebody giving away their credentials, being tricked into entering in an MFA code and then compromising your data that way. So, I think for most organizations those are the types of threats that you’re going to be facing.
And unless you’ve already done everything you can to have good foundational controls in place, you’ve got MFA, maybe you’re using physical security tokens, the zero day attacks, these kinds of man in the middle/ token thefts are not the most likely thing to happen. So, I’d really want to understand your organization’s risk assessment to make sure that you’re designing the right solutions for the types of threats that your organization is going to face.
That being said, making sure that the organization is implementing good baseline security practices, making sure you’ve got good auditing and reporting systems in place to identify whenever you’ve got anomalous activity happening, are all different and important ways to ensure that you’ve got good visibility into identifying when you may have something like a token being used in a different location or a different context than you were expecting.
Carolyn Woodard: We’ve still got a few people on. I wonder if you want to flip back to the slide that had some more of the approach one.
Standard Cybersecurity – 3 Basics for All Nonprofits
Matthew Eshleman: This is the one that I feel I repeat on and on, and it’s worth doing because number one, establish an IT acceptable use policy, and why would you do that? And I think it’s because it protects against misguided and misaligned IT initiatives.
Sans has a good policy template library, good framework. We’ve taken that and revised and edited that over time. We’ve been able to understand what are the IT systems that you have in place, what data resides within them, who’s responsible for that? Where do they live? Who has access to all of that information?
All of those elements are important to be able to define so that when something bad does happen, you’ve got a little bit of a framework in place to say, oh, okay, so this system was compromised, it had sensitive data in it. Okay, we need to do these things.
Or, oh, maybe it just had sample data and we’re not really worried about that. And so it’s unfortunate, but we have a different approach.
So again, being able to clearly articulate what data do you have, where does it live? How are people accessing that information? How are we managing permissions, what devices are people authorized to use? How we enforce that control are all really important steps. And that, you need to have a policy document that can define all of that.
Carolyn Woodard: You mentioned earlier that if you’re using your personal email on the Facebook account that’s managing your organization account, then having some policies around, well, you can do that. Facebook encourages you to have to be able to do that, but then you need to have MFA to log into Facebook even on your own personal account. And so, making sure to spell those things out, I think makes sense.
Matthew Eshleman: Yeah. And again, number two, we’ve talked about a security awareness training program. Again, I really like KnowBe4 because of those different elements. I like to be able to see who my users are that maybe need a little bit more training or support. I love the online training tools that are available.
Our approach, I like security awareness training to be something that’s built into the culture of the organization. It should be something that folks are doing quarterly in terms of online training, just to get familiar and just to keep up on the threats and to continue to have new opportunities to learn. Because it’s not something that you can really do effectively in one big training session once a year if you never really talk about it or think about it.
Quarterly trainings, monthly phishing, just kind of make it a part of the DNA of the organization to just be aware, be attuned to what’s going on. And then finally, MFA. I don’t think we can say it enough. Make sure that you’re using an appropriate MFA method.
I think physical security keys is where a lot of organizations are going to be moving to. They’re fast, they’re really secure, they’re hard to spoof. There’s a lot of great things to like about physical security keys. I think Microsoft is going to be pushing us in that direction. But, it still requires users to make that change.
Carolyn Woodard: I’m not sure if I remember who said it, I think it might have been Jaden on our other webinar who said that she’d rather have a staff person reporting something that was legitimate and just being careful and suspicious of it, and taking the time to fix that than to have them not be reporting something that they weren’t sure about. So, I thought that was a great attitude to take to it.
We have one more question and then we’re going to let everybody go.
What or how are you folks addressing zero trust models or implementations?
Matthew Eshleman: We could probably have a whole webinar just on zero trust.There’s some amount of jargon in what zero trust means. To me, what that means is fundamentally never really fully letting an account do whatever it wants without some kind of interrogation of it. In the old way, what wasn’t zero trust was in your server room, in your office. You’re in the office, you logged in your computer, done. You could get access to everything, you could access anything on the server. And there was that one control point, but once you passed it, nothing else really stood in your way.
Zero trust is this concept of continuous evaluation of risks and making sure that, before access is granted to any system, there’s some interrogation of your account. Does everything make sense? Are you still on a device that’s trusted? Have you recently authenticated? Have you passed an MFA challenge? And again, I think that is important because by default, out of the box, most cloud solutions, you can access any system from any device from anywhere, and there’s really no restrictions on cloud access at all. And that’s been great, especially as many of us over the last three years are all working in hybrid environments. We’re using cloud technologies that we’ve recently adopted. And so, that’s made it easy to adopt those solutions. But at the same time, it means that your attack surface area is enormous.
Because you can log in from Maryland, you can log in from Virginia, you can log in from Nigeria, you can log in from Thailand, all the different places. And your organization might not be in any of those locations. And so, having some zero trust tools in place can allow you to define more granularly where people can access from what devices.
And that’s probably the big area for organizations to be aware of. If there’s no BYOD policy at your organization and people can access and synchronize any work data to their personal device and then they leave the organization there’s no way to manage or control that, that’s a massive problem. So, I think a lot of organizations are just ignoring that the issue exists.
Carolyn Woodard: Well, and we talked in one of our other webinars about if you are working on a home network where the password is “password” and you’re in a condo, you’re essentially on an open network, or at a coffee shop or wherever it is that you’re working from. It could be in Maryland, but just not in a secure fashion.
We thank everybody so much for sticking with us for a couple of extra minutes here while we had Matt, we could ask him more questions. We do encourage you to get in touch with him. His contact information is on our website communityit.com, and we have a bunch more cybersecurity resources there. We have the playbook, we will have the incident report.
Matt, thank you so much for sharing your expertise for this. We really appreciate it. And we’ll let you go on your way. Thanks again.
