Transcript below.
View Video
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Spotify, Google, Stitcher, Pandora, and more. Or ask Alexa.
10 Free Cybersecurity Tools for Nonprofits and 3 Worth Paying For
Join Community IT Innovators’ CTO cybersecurity expert Matt Eshleman for a video discussion of the 10 free cybersecurity risk-management tools available to nonprofits that want to increase security.
Matt covers free tools that your organization should be using, how they operate, how to set them up, and how to train your staff to USE them.
He also spends time discussing three security tools to pay for, what they do, and why they offer a return on your investment.
Community IT Innovators is vendor-agnostic and does not resell vendor services or tools. Join us for this webinar for our un-biased recommendations and overview of the growing market for free and paid security tools for nonprofits.
With the “price to hack” continuing to decrease, businesses, nonprofits, and individuals are seeing risks go up. Don’t assume your organization won’t be targeted – everyone is a target of multiplying hacks and scams.
There is a 15 minute Q&A following the webinar, with participant questions. As with all our webinars, this presentation is appropriate for an audience of varied IT and security experience.
Presenter:
As the Chief Technology Officer at Community IT and our resident cybersecurity expert, Matthew Eshleman is responsible for shaping Community IT’s strategy around the technology platforms used by organizations to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how technology works and interoperates both in the office and in the cloud.
Matt joined Community IT as an intern in the summer of 2000 and after finishing his dual degrees in Computer Science and Computer Information Systems at Eastern Mennonite University, he rejoined Community IT as a network administrator in January of 2001. Matt has steadily progressed up at Community IT and while working full time received his MBA from the Carey School of Business at Johns Hopkins University.
Matt is a frequent speaker at NTEN events and has presented at the Inside NGO conference, Non-Profit Risk Management Summit and Credit Builders Alliance Symposium. He is also the session designer and trainer for TechSoup’s Digital Security course.
Matt provides a free initial consult if you have cybersecurity questions for your organization.
Click here to schedule a consultation.
Tech Insights from this webinar
For a quick walk through of the resources mentioned in this webinar, Matt created a short article here.
Transcript
Matthew Eshelman: Thanks, everyone, we’re going to go ahead and get started for our October webinar, entitled 10 Free Cybersecurity Tools and Three Things Worth Paying For.
Before we get started a little bit about Community IT, Community IT is a 100% employee owned company that’s been focusing on helping nonprofits meet their mission through the effective use of technology since 1993. We’ve also been recognized as a Channel Futures top 501 MSPs, and we’re the top MSP nationally that focuses exclusively on nonprofits.
My name is Matthew Eshelman and I’m the Chief Technology Officer here at Community IT and in my role, I oversee strategy and technology as it relates to both the platforms that we use to support our over 5000 users and 150 clients and then also the tools, technologies and solutions that are implemented by our clients. I’ve also taken a lead role in developing our cybersecurity practice to ensure that nonprofits have access and implement the same types of cybersecurity tools that are available to enterprises as well.
So, as some of you or many of you may know, October is Cybersecurity Awareness Month. Not sure if that’s an official holiday or not. But that’s the month that we’re in now. And so you’ve probably been getting bombarded with a variety of cyber security resources and tools and webinars. So I’m glad that you’re joining me here today.
Today, we’re going to talk a little bit about the
- cyber security landscape,
- we’ll go into cybersecurity readiness and then
- we’ll spend the bulk of our meeting time going over 10 free tools that you can use to help your organization right now. There’s actually one more bonus resource that I’m going to go ahead and throw in here and let folks know about.
- And then we’ll talk about three things that I really think are worth paying for. There are certainly a lot of resources that are available for free or very, very low cost, but I think there are some things that are worth paying for. So we’ll go ahead and cover that.
And then we’ll have some time for Q&A. You can also feel free to ask questions throughout the webinar by using the chat feature or the question feature to go ahead and chat those questions in.
I am running solo today. So please bear with me as I review questions and I have a whole bunch of links that I will be chatting out as we go along. As always, this webinar is recorded and the slides will be made available, you’ll receive a follow up link to that in the next day or so. And then I’m also working on kind of a summary or Compendium blog post that will contain all the resources and then some of the additional content. So look for that coming soon so you can have that as a reference moving forward.
So, before we get started, go ahead and maybe just have a poll here to see how confident people are with their organization’s cybersecurity. So go ahead and chat that in. So very, very confident, somewhat confident, not at all confident, I think regardless of where you’re at, I think you’ll probably learn something today. And if you’re very confident, I’d encourage you to chat in or share the things that you found to be the most helpful in terms of improving your organization’s approach to cybersecurity.
All right, so let’s see where we’re at here. And looks great. So we’ve got about 75% of the audience here that’s somewhat confident, so I guess you’re in the right place and maybe a bit of a bell curve in terms of very and not at all. So I think everyone should find something that they can take away here. So again, there are the results that we have, in terms of the audience today.
So in terms of the overall cybersecurity landscape, something that we continually update and refresh and what we’re seeing is that, particularly in the nonprofit cybersecurity incident report space that
- we are seeing persistent and ongoing, brute force attacks, on identities that’s done in conjunction with some automated tools and then just the sheer number of data breaches that are out there. So these massive databases that contain usernames and password combinations and so threat actors are able to go through and just test lots and lots of username and password combinations. So we certainly see that a lot.
- We’re seeing sophisticated spear phishing that targets organizations, the attackers are getting very good at looking at your website and figuring out who your CEO or Executive Director is, and the Finance Director and your operations people and using spear phishing attacks to target them. And we’ll see that and some of the data I’ll share later on.
- We are also seeing organizations targeted because of the work that they do, particularly coming into the election year cycle, organizations that work in the areas of democracy or good governance are targeted. Organizations are also being targeted, particularly in the areas of foreign policy, they tend to attract a high profile and we’re seeing a lot of foreign adversaries attacking those organizations. So those are the top tiers that we’re seeing. But I think it is certainly more widespread that based on the work an organization does, they could also receive targeted attacks beyond just kind of the dull roar of attacks that are going on out there.
- And then we’re also seeing attacks targeting vendors like us as a managed service provider. So we are certainly aware of the data that we maintain and represent as a target for adversaries that would like to crack in our networks to then be able to impact the clients that we serve. So we are seeing, we are aware of that.
On the positive side, we are seeing there’s a lot of great new security tools available to combat these new threat types. And we’ll talk about these as part of our overview today. So, there’s lots of bad stuff going on. But there’s also some great tools that can help. We are also encouraged to see that organizations are starting to be proactive in terms of asking about where to start in improving their cybersecurity.
So I think, I’ve certainly felt a change from us feeling rather pushy or kind of always talking at our clients about that to organizations coming to us to ask about what they can do. And I think that’s a really great stat. As the next point shows, we still have a long way to go. This is from the NTen cybersecurity summary report that they put out last year, I think there may be an update coming soon. But 68% of nonprofits don’t have an incident response plan. So I think that just kind of shows that nonprofit organizations in general have been great at adopting cloud solutions and kind of adopting digital transformation. But they’ve been less apt to implement improved cybersecurity controls.
And we’re also seeing that the cost of responding to a cybersecurity or data breach is increasing. So these are real, direct dollar costs associated with a breach for small to mid sized business, this is put out by Kaspersky. So they’re saying, there’s direct costs about $149,000 associated with responding to a breach.
And that does not cover intangible things like staff time, loss of goodwill amongst vendors and partners. And so it is a significant cost that is associated with having a breach. So, cybersecurity threats are not something that happens to somebody else. It’s not something that only happens to big business or enterprise. This is something that affects all sizes of organizations and no one is kind of immune or can fly under the radar in terms of avoiding being a target for cyber security or for security threats.
So with that in mind, let’s do one more poll here, get a sense for who is responsible for cybersecurity in your organization? Is it you? Is it the IT department? Is operations responsible? Is nobody responsible for it, just to get a sense of who is here and who maintains ownership of that role.
I’ll leave this for a few seconds here. Thanks for all your responses. And we’ll go ahead and see that.
So for the majority of the attendees on the webinar here today, they’re the ones responsible (57%). Sorry for those 13% (No one is responsible), hopefully, you can figure out where that sits in your organization and get some attention on it. All right.
So let’s go ahead and talk a little bit and let’s get into the meat of this presentation. There’s a lot of content I want to get through and provide information about so I’m going to go right on into it. And if you have questions, as I said, go ahead and chat those in.
And so first off I think cybersecurity readiness, it is helpful to use this familiar framework of people, process and technology and that’s how I have the different tools aligned here. Yes, good cybersecurity is not just a shiny thing that we can buy off a box. But it involves these different elements.
There certainly are technology options. We have a lot of those to talk about.
But the people element and the process element is really important as well.
And so we are going to go ahead and talk about solutions in that area as well.
People
So, kicking it off, with people,
- first off, enabling MFA. So MFA stands for multi factor authentication. And this is the number one thing that you can do to protect your digital identity. So again, if you can log into your account online, so can everybody else.
So it is absolutely critical to incorporate multi factor authentication. And that can be done easily. And it’s free in both the Microsoft Office 365 platform and also Google or G Suite. So I’m going to go ahead and chat out the links for that.
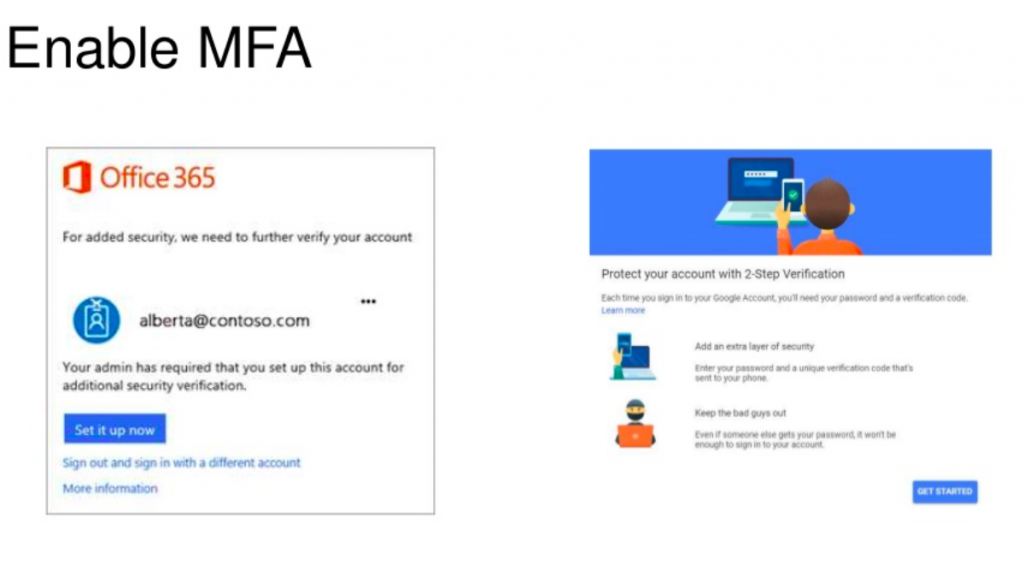
What you see on the left is an Office 365 MFA enrollment screen, where you can go and enable that on your account in Office 365. There’s a free authenticator app that you can install on your phone. And then that will require a second factor. Typically, we would recommend that to get triggered once every two weeks or so. We also try to make it a little bit easier to adopt and not having it triggered whenever people are in the office. So we want security to be easy to use and not be a huge barrier for staff when they’re using technology correctly.
And then on the right, again, G Suite, great resources. Also has free, 2FA enabled, so you can use a Google Authenticator or a one time passcode application to sign in there. So that’s a resource that is available for free for both of those platforms. And something that is easy to turn on. There’s great setup and documentation guides in both of those links that I chatted out. And as I said, this slides and recording will be available afterwards. And you can also keep your eyes open for a blog post that will have this maybe a little bit easier, clickable format.
So when thinking about protecting your identity MFA is the most effective way to do that, because it requires something, which is your password and then something you have, which in this case would be your authenticator or your phone to complete that authentication step.
So moving on to
- another set of some free resources to manage accounts is the password manager.
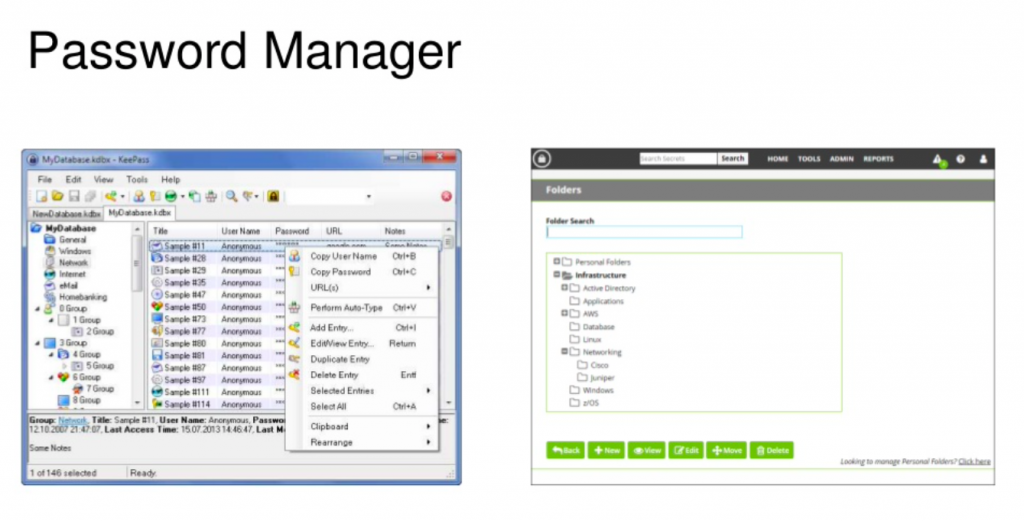
Ideally you have good strong passwords and passwords that are unique for each site that you are logging into. Because as we’ve seen in the news, one website can get compromised, those passwords are dumped. And if you’re using the same password across many different websites, then you know, you’re in bad luck. So if you had a password for LinkedIn as the same as your bank account is the same as your Office account. You could be in bad shape whenever a system gets breached. So it’s a great idea to have unique passwords for each application or website that you’re using. But that means it’s a major challenge to administer that. So there are some tools; there’s a number of great paid tools. And so you can look at some paid tools. But there are a couple of free options. So Keepass is one, it’s an open source, password vault manager. And so it’s a little application that you can run off a USB drive, it supports encryption. So you can just create, generate, store all of your secrets there.
And then the other tool, this may be more helpful if you are in the IT manager role and maybe share access for passwords amongst some IT department staff is Secret Server.
So that’s on the right, that’s the look at the UE. This is an application, we use the paid version, because of the number of accounts and complexity that we have. But they do have a free on premises version of their Secret Server program that is really fantastic. And you can use that to securely store, manage, audit, report on the credentials that are in use at your organization. So again, the first two free recommendations were around enabling multifactor authentication; that’s free in both G Suite and Office 365. And then also some tools around managing passwords and accounts across your organization.
Process
Alright, so moving into the process section.
This is actually an area where we’ve got maybe the most free resources available and so let’s first start off with some resources actually.
- This is a government resource, it’s called Stop Think Connect. This is a great website that has a lot of free security training, resources, posters, some e-mail templates, and checklists and guides. This is really geared towards individuals and kind of small to midsize organizations. So as you can see, got a couple of screenshots here for some of the resources that are available on the Stop Think Connect website.
I’ll go ahead and check that link out. So you can follow up on that. But again, they’ve got I think some really well done, well articulated resources that are great to use. If you’re looking for some quick ways to get started or you need to provide a resource guide for staff, these are some great resources.
You can see here tips for a clean machine, keeping your software current, having software updates, making sure that you’re being aware of USB drives, there’s a great little technology checklist, this is just the first page. But there’s a lot further sections below that. So that’s a great resource. If you’re just getting started with some security awareness training at your organization or are looking for some basic how-to guides, Stop Think Connect is a great resource to get started with.
And I’ve been happy and impressed with some of the tools that they have there.
Moving on, to moving up the complexity scale a little bit is a resource from SANS.
So one of the things that we’re often asked about is, we talked about policy being important and a foundation of policy being important. And so the follow up question is
- “Where do I go to get a policy?” and I think SANS is a great place to start. These tend to be some smaller scale policy template documents, they have some definitional things.
So if you’re trying to understand the difference between a policy, a standard, a guideline, they have resources that can just help articulate some of that, you can see here that if you go to the website that I’m chatting out right now, that’ll take you directly to the policy template page.
And on their policy template page, they’ve got General policies, which are the IT acceptable use, they have some more specific things around network security or application security, service security, and that kind of delves into some of the specifics in terms of how long passwords need to be, was application patching schedule, what are some of the technical details around these areas getting started with a general IT acceptable use policy. I think it is a great place to start.
We’ve taken this and adapted it for the nonprofits that we work with. So if you work with us to do an IT policy refresh, we’re reading our policy documents in the resources that are provided by SANS. So again, I would think this is a great resource to go ahead and get started.
Great, you’re actually in one of our free resources!
- I do think our Community IT webinar series is a great resource to get educated on current trends in technology. We’ve had a big focus on cybersecurity this year. And then they have a range of topics, but not to toot our own horn a little bit. But all of our webinars are recorded as this one is. The slides are all published and made available. And so you can check all that stuff out.
So thank you for attending and I appreciate the interest. And also I appreciate the feedback that is provided at the end of the session. So again, thanks for attending, please keep subscribing. We want to hear from you in terms of how we can make these webinars meaningful and relevant for you so that they continue to provide a lot of value.
So we’ve kind of worked our way up from some basic resources from Stop Think Connect in terms of basic cybersecurity awareness.
We’ve talked about some policy work, talked about our webinar series that provides ongoing education. Now I’m going to provide access to a free resource that you can take advantage of.
- If you e-mail us at cyber security at CommunityIT.com. You will get access to this NIST cyber risk assessment tool. So this is an online web-based application that you can use for free to go ahead and fill out. And then it will automatically generate a report.
And it will generate this risk heat map and then identify top risk areas. So, I think there’s lots of free online resources. This is something that we’ve found and acquired, because I think it does a good job of being relevant to small and midsize organizations. It is a little technical, so if you’re very small organization it may be overkill, but if you’re 15 to 50 or even up to probably 200 staff, like this is a good foundation that has focused assessment questions, focused recommendations, and a little bit of a roadmap on what to do and what to prioritize.
So you can see here that you’ll get a heat map that will identify your top risk areas. So in this sample, it’s identifying all users informed and trained as critical, threat detection and analysis is also identified as critical. And then you can generate a PDF report and it kind of goes into the details of what are the cyber security controls that are important to help address these vulnerabilities. So I think the NIST assessment tool is really a great resource. And if you go ahead and send in an e-mail to cyber security Community IT, will go ahead and reply and get you access to this tool where you can fill it out at your own pace. Takes about 30 to 45 minutes to fill out. You’ll automatically get the report right away. And then you can actually follow up and if you want to take the assessment again, you’ll get to see your trending information over time.
NIST Assessment and Auditing Resources
So again, a great way to help baseline where you’re at right now and then go through and identify the next steps for your organization.
And then finally on
- one of the free tools is a website called Have I Been Pwned? And I put this on here, because I think this is a great educational tool, especially if you’re trying to get buy-in from leadership or get somebody’s attention. This is a great resource just to show them how widely available compromised credentials are out on the internet.
So you can see I filled this out to see if my account is out on the internet anywhere. And indeed it is. So, my account, [email protected] has been found on four breach sites. So that means that e-mail and password combination has been found, it could be the password has been published in plain text, it could be that it’s outing encrypted.
This is a free resource, it doesn’t give you all the details, there are some paid resources, where you can actually get the details of, which password has been compromised and location, the time and some other information, which is I think helpful from an educational perspective, but the Have I Been Pwned? website is good just to kind of keep up to date of what’s going on.
I think if you’ve already implemented good security controls like unique passwords at each site, implemented multi factor authentication, it becomes less alarming.
I think knowing that your password could get compromised, it’s not a question of if, but it’s a question of when. So it just helps to bring some education and awareness, just about the volume of password and data breaches that are out there.
So go ahead and check that out right now to see if your account is on there. I think there’s even some tools where you can check to see if your password has been used as well. So those are the resources or that’s the final resource I have here in the training awareness or the process tech process side. If you’ve got some other free resources that you have found helpful or interesting, you can go ahead and put those in the questions or chat and we will see if we can incorporate that into the session here as well.
Technology
All right, now we’re going to talk a little bit about some of the free technology tools that are available, there’s less of these available because often the manufacturers are, it’s a zero sum product and so they have to make money somehow, so there’s not as much free resources on the technology side. But there are some pretty good things that I think are worth looking into.
So the first area is actually in the area of updating and package management. So, if you’ve been on some webinars before, or you see even back at the very first resource in terms of the Stop Think Connect, keeping things up to date is a great way to make sure that you minimize your exposure from a cybersecurity perspective. So, if your apps are up to date and patched, then you’ll be less vulnerable to viruses or worms or attackers that are exploiting known vulnerabilities.
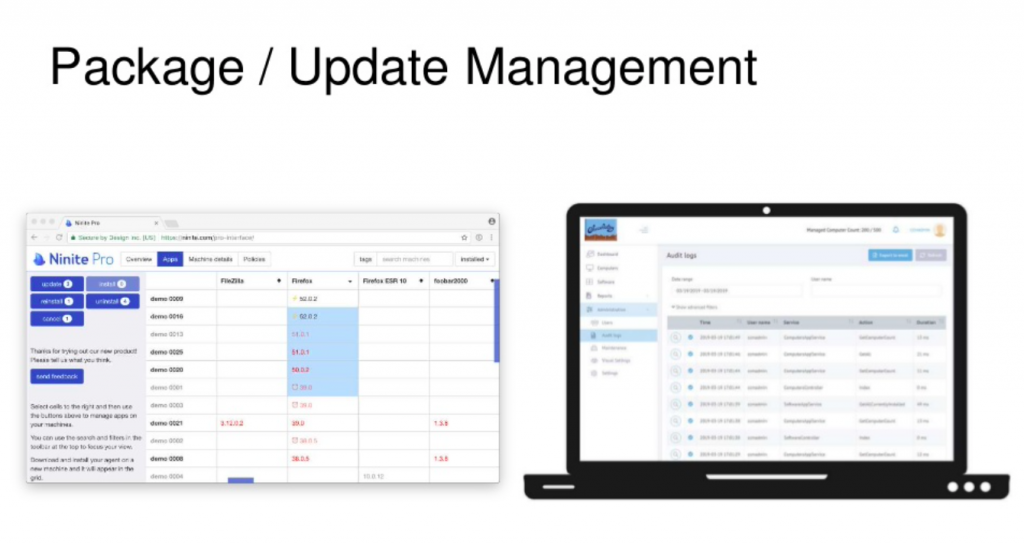
So there are two resources that I’ve got up here, the one on the left is actually called
- Ninite So it’s Ninite Pro. I think this does actually carry a cost. So maybe there needs to be an asterisk here in terms of a free* tool. It is relatively low cost.
It’s a tool that we used to use. And I was impressed with it, it did a great job of keeping those third party apps up to date. So I think what you’ll find is, if you are in the Mac world or in the Windows world, it is relatively straightforward to make sure that your operating system is up to date, it automatically updates, and just kind of let it roll. But it’s a bit harder to make sure that all those third party apps are up to date, all the Adobe stuff, Reader and Flash, Firefox, VLC, all those other applications also have vulnerabilities in them. And it’s, I think it’s getting better. A lot of the applications have adopted an automatic update process. But it’s not something that is the case for all the applications. So apps, Ninite Pro can handle that.
- On the right hand side is a product called Chocolatey. So that’s a package manager and is an open source tool. And so you can use that as a way to manage all of the packages that you have in your organization in terms of application deployments and you can use the tool to go ahead and update packages and push them out.
So again, this may be a resource for those folks that are on the more advanced side, that maybe have some expertise, but maybe not a lot of budget and maybe some time to go ahead and kind of figure out how to do third party patching updates.
We handle that all through our endpoint management system. So if for clients that we’re doing support for, we’re managing all the Windows updates, the OSX updates, and all the third party updates are kind of built into the platform tool that we have. So it could be if you’re working with a managed service provider, you may already be getting some of this. But if you’re doing it on your own, these are some tools to look at that may be a resource for keeping things up to date, which is always a big, a big goal when it comes to cybersecurity.
All right, here’s also a resource for vulnerability scanning. So again, if you’ve gotten things up to date. You are doing a great job for password management. Now you actually want to validate and test your systems.
- Qualys has some free community tools. So they have, they’re a big vendor of IT security applications. So you can spend a lot of money on Qualys. But they also have some community supported additions that are great in terms of just getting started. And that’s the link that I have here. So they have their community edition of their vulnerability scanning tool, will do asset discovery, it will do scanning, you can scan your website, you can scan internal resources. It’s a little bit difficult to see here, let’s see if we can zoom in a bit. So you can see that it will do little scan and reporting on that asset distribution of the operating systems in the environment, reporting on the manufacturers and look at the different applications that are deployed, the version numbers.
So all of that is going to be available through the Qualys tool. If you’re using that, or another tool, I’d be interested, go ahead and chat that in. But that’s, I think, a great resource to make sure that you can verify that the things that you think are happening are actually happening. So it’s, there’s one thing that we spend a lot of time on is remanding updates. We’re also reporting and making sure that you know updates are happening in the way that we expect. So go ahead and check out that tool from Qualys, particularly if you have some on-prem server resources, it can be a great insight into seeing what’s going on your network.
And the final free tool that I wanted to let folks know about is actually the
- Barracuda threat scanner. We’ll hear more about them in a little bit. But they do have a free scanning tool, this is for Office 365 users, where you do have to grant access to the tool, so you would sign in to your Office 365 account, and you would permit the Barracuda e-mail threat scanner tool to scan the contents of your mail store. And then it will generate this report in about 24 to 48 hours.
So, as I mentioned, there’s some great cool new technology. And this is an example of that. So Barracuda through their API is different from traditional spam filtering that would go through the MX record. And the spam filtering tool is going to make that analysis when the message comes through.
The Barracuda threat analyzer connects into the backside of your exchange environment, your e-mail environment, and then is able to see relationships between users. And it’s also able to get some more information about the e-mails themselves, what spoofed and generate this report. So you can see, it detects how many mailboxes are available or on the system, how many fraudulent e-mails are going to be there, the users that represent spear phishing risks, how many domain fraud alerts are there. And so again, it’s a pretty cool tool. And then you can see here, it’ll actually go in and say, Oh, here’s the last time this employee received a message from this user and that appears fraudulent.
So again, it’s a great way to test to see if the things you think you’re being protected against, from your spam filter are actually working as you expect. And it’s a free tool, you get the report in about 24 to 48 hours. And it’s a great insider resource to make sure that you are being protected from the threats that you think you are.
What we’re seeing as an organization is that the number of account compromises that we see is holding steady when we compare it to where we were last year, even though a lot of organizations have implemented MFA. We’re also seeing the amount of spam reported and the spear phishing messages has just skyrocketed in 2019. So getting some tools in place to protect against that is, I think, really important.
So I think if you’ve been counting, we’ve got 10 different categories of free resources from enabling MFA, Password Manager Tools, security awareness tools, and technology tools.
Bonus Recommendation
So there is one more resource that I wanted to make sure that folks were aware of.
- And that is Microsoft’s Account Guard. This is free for organizations that qualify. So this is really geared towards those organizations that are working on good government, good governance, elections. I think if you’re in government, you could qualify for this.
But this turns on and makes available some additional security resources from Microsoft against your account. So it includes some additional account security and protections. Some additional, I think some back end teams are looking at this, to make sure that there’s no successful compromises of accounts related to organizations that are working with democracy, good governance, and some policy research.
So again, this is a free program, if you qualify. You do have to apply. But if you’re in those areas, this is definitely something that is worth checking out. Because, like I said, protecting your online identity is a really critical way to make sure that your organization isn’t compromised and you’re not losing data or being used to attack other organizations.
Resources Worth Paying For
All right. So now, those are the free recommendations. And so now we’ve got a couple things I do think are worth paying for.
- The first thing that I think is worth paying for is really good security awareness training. There’s a lot of free stuff out there. There’s also a lot of really bad security awareness training. And so what we found is that Know B4 is a really great online learning tool. I like it because it combines baseline phishing testing and includes online ongoing security awareness training. There’s lots of different resources from 45 minute, kind of deep dive trainings to five minute click on the phishing e-mail games. I think it’s really worthwhile, it’s really a great resource. That’s what we use at Community IT, we’re a partner. And it’s not that expensive – 20 bucks a user per year kind of a thing. So it’s not that expensive.
But this is some information about where they see organizations go. So the way that this is determined is that when you first start, you would do a baseline phishing test, just to see how many, what percentage of your users are clicking on links that they shouldn’t. They’re saying the industry baseline is 27%, I think in the nonprofit sector, you can baseline yourself against, it’s a little bit higher, it’s about 33%. That’s certainly within the realm of what we see, in the clients where we are deploying this. After a couple months of training and awareness, it does really drop dramatically. So staff kind of know what to look for, they’re able to identify those spoof links or those obfuscated e-mails. And so it’s a great way to both test and provide training and resources to staff.
So again, we think that this is an effective way to implement security awareness training, where it’s something that you are doing kind of constantly and at a relatively low level. I would say that having a once a year, big security training in the staff meeting for an hour and a half, not that effective.
Doing a baseline phishing test, having a 15-minute training and then testing people and doing some follow up trainings every four to six weeks, really effective.
So we are seeing numbers that would match this. So again, Know Before for security awareness training. There’s a whole bunch of other vendors out there. And so find something that works for you. But again, definitely invest in security awareness training, because you can have a whole bunch of technology in place, but if somebody’s clicking on something and entering their passwords, in a malicious site there’s only so much you can do to protect your organization against them.
The other resource here, it’s worth getting business e-mail compromise protection. And so that kind of builds off of the free, they have a free teaser, like, hey, look how much spam is getting through. That’s the teaser, and then you can buy ongoing protection from Barracuda using their Sentinel tool. We use Sentinel. I think it’s great. It’s really effective in targeting protection against those business e-mail compromise messages that come through. You know the ones: gift card fraud, wire transfer fraud, all of that stuff, account takeover, protection, DKIM, DMARC administration, it does all of that. So again, it’s a couple bucks a month, it’s pretty effective. Again, it’s not a perfect solution, but it is pretty effective. And so here’s a little bit more of the diagram in terms of how that works. So again you’ve got e-mails coming in from the internet. Sentinel is plugged in via Office 365 API. It’s reading that data. And then it’s kind of acting on the back end to go ahead and protect anything.
I’m just taking a minute here to look at some of the questions…
Yes, we will be doing the recording.
Some tips about the Office 365 MFA set up. I think once you get it set up, it does sound a little bit intimidating. There can be some issues just on enrollment and getting the authenticator app set up. But once it’s set up and tuned, I think it works pretty well. And it’s not that much of a distraction for what organizations can be aware of.
There’s some questions about other solutions from Qualys. I think Nessus also has some free options for vulnerability scanning. So again, some of the big players will do some free or discounted offerings for nonprofits. And so you can check that out.
And so on this tool, I will say this, I think it is Office 365 only. I’m not aware of third party API integrated solutions that target business e-mail compromise that work in G Suite. So again, if you are using one or no are aware of that, go ahead and check that in. But this is an Office 365 only solution. So again, if you have on-prem exchange, still, this is not for you, if you have G Suite, it’s not for you, this is if you’re in Office 365, you can go ahead and check that out.
All right. And then the final thing, I think it’s worth paying for, there’s a free kind of self assessment that you can go through that is really worth doing. So if you want to get started and just kind of have a baseline e-mail, we’ll get you access and you can have the free tool. The tools and the assessments and kind of all this stuff is only as good as your ability to take the information and then turn it into action.
I do think if you’ve done some of the basics, you kind of have a good baseline understanding of what you need to do, but then want some guidance on maybe prioritizing investments, understanding what makes sense for your organization, then paying for a cybersecurity assessment would be a good use of money.
If you haven’t implemented MFA, you’re not doing patching, if you haven’t updated passwords. If you don’t have a backup, those are things that you want to make sure you get done first. But once those basics are already taken care of and you want to go ahead and figure out what’s next or budget and plan out, then I do think paying for a cybersecurity assessment makes sense.
So here’s an example. This is our scoring framework that we use. So we do assessments in these, like 8 areas. And so we do a ranking. And then provide a list of recommendations that are qualified both on kind of the complexity of the recommendation, the urgency and kind of the level of effort, so that we can help to prioritize that investment. And also budget out, what it’s going to take to implement those various solutions.
So again, what we are finding is that a lot of organizations have not implemented that security awareness training, they don’t have a great IT policy. So that’s the first thing that we’re suggesting in many cases that you need to implement security awareness training, we need to start with an IT security policy so that we can make these judgments around the other areas.
So again, then we’ll look at areas such as device security, how are you protecting individual devices? How are you protecting your network and the overall network boundary? Looking at the identity and account management policy and practices, looking at all of these systems. How are you protecting that? Are you able to recover that data? How are you protecting the data, what protections are in place around e-mail and then also looking at the web and application?
So again, being able to connect the dots and build out a roadmap that’s relevant for organizations that are in that small to midsize group? There’s lots of great online assessment tools. They tend to be geared towards larger organizations and maybe presume a budget that isn’t relevant for most nonprofit organizations.
So, again, I do think, again, paying for some kind of cybersecurity assessment makes a lot of sense.
Q and A
All right. I think we’ve gone through some of the questions here. But if there’s anything else, go ahead and chat it out. One thing I did want to highlight thanks to Leah, for highlighting a resource to protect your website from denial of service attacks is called deflect.ca.
So let me see if I can chat that link out. I was looking at CloudFlare. I think they used to have a similar free offering, but that doesn’t seem to be available anymore [see pricing, as of March 2021 a free plan is available for individuals]. But again, using a resource like that, to protect your website, I think makes sense and kind of takes the benefit of resources in the cloud at the kind of scale that you can build on your own. So I would go ahead and yeah, thanks for sharing that resource.
Let’s see… CloudFlare still has it. So again, CloudFlare, Deflect have some resources, so go ahead and check those out. Thanks for sharing that link out.
All right, I did want to highlight. This was a quick overview today of some 10 free tools and a couple things that I think are worth paying for.
One of the other things that may be worth paying for is some additional security awareness training or work through TechSoup. So on TechSoup courses, you can sign up, I worked in partnership with them to develop a curriculum that includes both 101 Cybersecurity Awareness for individuals and a 201 course, which is directed at IT security for IT managers. And so those resources are available.
And then if you sign up, then tomorrow, I will be doing kind of a follow up on the 201 course, in terms of what has changed since that course was released about a year and a half ago. So if you’re interested, you can go ahead and register for TechSoup Digital Security 201 live event. So that’s going to be tomorrow afternoon, at three o’clock eastern. So that’ll be on October 17 (2019).
And finally, next month, the webinar will be presented by our colleagues over at Build Consulting. Peter Mirus is going to be talking about how data quality defines your organization. I think that should be a good session. I attended their session last month on CRM selection, I learned a lot. I think they really have a depth of understanding in that topic. So I’d encourage you to go ahead and register for that as well.
So thank you very much for your time, there are a couple of questions that are still coming in.
So one from Chuck here. What kind of common attacks are you seeing against our business? I think we’re seeing the common attacks related to kind of brute force identity and access account attacks. So as a policy, at Community IT we’ve gone through, and we have our security controls document. So again, if you are an organization working with a vendor, that’s something to ask for. You can ask what are their cybersecurity controls and if the vendor has done their work, they should be able to just kind of turn around and give you a document that they’ve already worked on.
So in our cyber security controls document we talk about all the things that are in place at Community IT to protect our data and the data of our clients. So, for example we require MFA access to any of our privileged systems. You don’t have any publicly exposed RDP ports. We have a backup and disaster recovery plan, we have a business continuity plan in place, we have IT policies in place, we audit and record all access to the systems that we support. So there’s kind of a long list of security controls that we have in place as a managed service provider, because of the risks that we face. And so I think if you’re working with an MSP, you should feel comfortable going and asking for that from them. In terms of the attacks that we’re seeing from against our clients, we’re collecting data and kind of getting updates for our incident report.
We released our first nonprofit cyber security incident report back in March. And we’ll be on track to release a refresh of that next year as well. And I mentioned it earlier, but I think what we’re seeing is that there’s been a big spike in spam and particularly in business e-mail compromise, that’s a new threat that just kind of skyrocketed this year, where adversaries are being really crafty in terms of spoofing messages and getting organizations to buy gift cards, do wire transfers, do all of that stuff. So again, we’re seeing that as a big risk for nonprofit organizations. And then, like I said, we’re also seeing a steady increase in the number of account compromises. So even as organizations implement and adopt MFA, we’re nowhere near 100% compliance. And so I would again, continue to implement MFA as the number one way to ensure the integrity of your organization’s data, because the attackers are out there and they’re getting good at breaking through on them.
So great, well, thanks everybody for attending. Make sure to e-mail cybersecurity at CommunityIT dot com to request access to the free NIST Assessment Tool. We’ll go ahead and turn that around, as our thank you for attending the webinar today. And I hope this is helpful. Please fill out the survey, provide any comments, feedback. It’s something that we do look at and use to incorporate to make these webinar events better and more relevant for you. So thanks very much. I appreciate it and enjoy the rest of your afternoon.
Slides:
- 10 Free Cybersecurity Tools and Three Things worth Paying for Monthly webinar Series October 2019
- About Community IT Advancing mission through the effective of technology. 100% Employee Owned
- Presenter Matthew Eshleman CTO
- Agenda Cybersecurity landscape Cybersecurity readiness 10 FreeTools Bonus Resource 3 PaidTools Q&A
- CYBERSECURITY LANDSCAPE Persistent and ongoing brute force attacks on identities Sophisticated spearphishing Organizations targeted because of the work they do Attacks targeting vendors
- CYBERSECURITY LANDSCAPE New security tools available to combat new threat types. Organization’s starting to ask about where to start in improving their cybersecurity. 68% of Nonprofits don’t have an Incident Response Plan Breach response for a small to medium business is $149,000
- Cybersecurity Readiness People •Passwords •MFA Process •Policy •Training Technology •Updates •Scanning •Email Protection
- People
- Enable MFA
- Password Manager
- Process
- STOP THINK CONNECT
- SANS
- Community IT Webinar
- NIST Risk Assessment Tool
- Haveibeenpwnd
- Technology
- Package / Update Management
- Vulnerability scanning
- Email Threat Scanning
- Bonus Recommendation: Microsoft Defending Democracy Program
- Resources to Pay For Security Awareness Training
- Resources to Pay For • Business Email Compromise Protection
- Resources to Pay For Cybersecurity Assessment
- Q&A
- Other Events TechSoup Digital Security 201 –new live event on Oct. 17!
- Upcoming Webinar How Data Quality Defines your Organization Wednesday November 12th 1:00 – 2:00 PM
- [email protected] © 2018 Community IT Innovators, Inc. All Rights Reserved. www.communityit.com THANK YOU!

