Transcript below
View Video
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Q&A Webinar: Cyber Insurance for Nonprofits — What You Need to Know
Join Jenna Kirkpatrick Howard from Lockton Companies, Matt Eshleman, CTO, and Carolyn Woodard from Community IT for a free expert Q&A on Cyber Insurance for Nonprofits, how the market is changing, and how to understand your application and controls and ensure you have the appropriate coverage.
Do you have questions about cyber insurance for your nonprofit?
Have you been asked to demonstrate IT controls like MFA or Single Sign On when applying for insurance coverage?
Do you know if your organization is in compliance?
Do you know if your policy includes exemptions that would prevent your claim from being paid, in the event you had an incident?
Do you know who to call first when you suspect a hacking attack or wire fraud? Do you know how to preserve the evidence, and what is needed by your insurance provider?
Learn in this Q&A webinar with an industry expert.
Jenna provides an overview of the insurance industry and will touch on the way cyber insurance works, what’s changing as IT hacks and scams grow in frequency and costs, and how to expect coverage to change in the next year or so. When claims go up, premiums will go up. What does that mean for your nonprofit?
This webinar is important for:
- the CFO who regularly deals with the insurance but doesn’t know the lingo about the IT controls you need
- the IT director who doesn’t usually have anything to do with insurance
- the Executive Director or Board member who wants to ensure everything is in place given how much premiums are rising and the growing risk of being hacked or scammed
- the accounting staffer who discovered a mysterious missed payment, suspects an email scam, and now doesn’t know who to tell first
Many people submitted real life questions in the webinar and at registration, and we did our best to answer these. Any questions we didn’t get to we will include at the end of the transcript, with answers.
In the second half of the webinar, Jenna and Matt build on the insurance overview and lay out practical steps for nonprofits of any size to connect the right CFO-insurance-IT people-leadership-budget departments to understand your coverage and ask for the coverage you need.
We walk through some basic application requirements and what the lingo means. You can find more information in the Guide to Basic Controls Demonstrating Cyber Preparedness available as a free download here.
We finish up with what to do when you have an incident, and learn what to expect from your insurance when you need it.
Community IT has done many webinars advising nonprofits to have a procedure in place to prevent an cybersecurity incident, and to know what to do if and when you have an incident. The first step we usually recommend is to contact your IT provider, your board, and maybe the FBI depending on the event.
We’re excited to bring you this expert Q&A to answer questions on what to expect from your insurance.
This webinar builds is an update and extension of our previous presentation on cyber insurance. Community IT and Lockton Companies can not and are not providing individual insurance advice; for individual and specific questions you should speak to your own broker and legal counsel. This webinar will cover cyber insurance as a general topic of value to nonprofits.
As the insurance landscape changes to adapt to emerging cybersecurity threats and risks, your nonprofit has never needed to understand your coverage more.
Presenters:

With her years of insurance industry experience and finance background, Jenna Kirkpatrick Howard is well-positioned to answer cyber insurance coverage questions from nonprofits. She began her career as an actuary study, an experience that prepared her to discuss total cost of risk, lead annual budget discussions, conduct risk assessments, and look at alternative risk finance mechanisms.
Jenna recommends this free download Guide to Basic Controls Demonstrating Cyber Preparedness from Lockton Companies as a first step to understanding the questions you should be asking your broker. To qualify for cyber insurance, insurers require organizations to have certain basic controls and be prepared to respond and bounce back quickly in the event of a cyberattack. This guide explains the major control categories that must be implemented to qualify for cyber insurance. These control categories are not an exhaustive list of all insurer requirements. Multiple factors are considered by each individual insurer when evaluating an organization. However, the consistent message from cyber insurers has been that the generic controls discussed in this guide are the ones they find most important.
Outside of her career, Jenna is actively involved in philanthropy working with groups that support families in the Washington DC community. She was previously the Board Treasurer for 826DC, a nonprofit dedicated to working with students to develop their writing skills and to helping teachers inspire their students to write. Jenna also is on the host committee for the 2020 Women on Boards Luncheon and the Annual Harvest for Hope Event for Volunteers of America Chesapeake raising funds to end homelessness in Northern Virginia. In addition, she joined the Finance Committee of Community of Hope, an organization that provides quality healthcare and stable housing to families in the DC Metro area.

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response.

Carolyn Woodard is currently head of Marketing at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She is happy to moderate this webinar Q&A on cyber insurance for nonprofits.
Transcript
Carolyn: Welcome everyone to the Community IT Innovators’ Q&A webinar on “Cyber Insurance for Nonprofits” with Jenna Kirkpatrick Howard from Lockton Companies and Matt Eshleman, the CTO and Cyber Security Expert from Community IT.
We’re going to talk about:
- how this type of insurance works,
- why nonprofits need it,
- what your nonprofit is going to be asked to show that you are doing in your cyber security policies
- practices in the event that you might ever need to make a claim.
So I just want to say at the outset that when it comes to insurance, we can’t make any recommendations really, on specific policies and specific amounts. I know that’s not totally helpful to hear in a webinar. You’ll need to speak with your own broker.
But we’re aiming today to give you familiarity with the issues, the lingo, the language that we use, and an understanding of large changes that are ongoing around cyber security and insurance. I know this is a topic that can scare a lot of nonprofit folks, both cyber security and insurance. So we really appreciate you being here with us today and take a deep breath – you’re in the right place and we’re going to get to it.
I just want to remind everyone to stay for the end because we will have a $25 gift certificate for one lucky winner who fills out the poll at the end.
I want to remind everyone that we’re vendor agnostic, so we’re just talking about this generally today.
Our learning objectives are, at the end of this session, you should be able to:
- describe cyber insurance for nonprofits including the landscape and history of this type of insurance and the upcoming trends that we expect.
- You should be able to understand the challenges nonprofits face with cyber insurance and describe some actions nonprofits can take and
- where to learn about available resources.
We encourage you to submit questions and comments through the chat feature today. We might not be able to get to all of your questions, but we’ll try to make some time at the end. And we did get some questions at registration that we’re going to try and answer as well.
If you happen to be watching on YouTube today, we encourage you to subscribe to our YouTube channel. So you’ll get the updates every time we post a new webinar. Also, we invite you to subscribe to the email list from our website, because then you would get an invite and be able to attend a webinar in person and ask your questions.
So I’ll introduce myself. My name is Carolyn Woodard, I am the Marketing Director and Outreach Director at Community IT. I’ll be monitoring the Q&A and chat and helping with the presentation. Next I’d like to introduce Matt.
Matt: Thanks, Carolyn. It’s great to be here on the webinar today. In my role as Chief Technology Officer, I get to work with a lot of nonprofit organizations on implementing their cybersecurity solutions and also helping them fill out their cyber liability insurance applications. So this is a webinar that I’m looking forward to, to get content from as well, as this is a really relevant topic for the clients that we’re working with. So, happy to be here today.
Carolyn: Great. And before we begin, if you’re not familiar with Community IT just a little bit about us. We’re a 100% employee owned, managed service provider. So we provide outsourced IT support, and we work exclusively with nonprofit organizations. Our mission is to help nonprofits accomplish their missions through the effective use of technology. We serve nonprofits across the United States, and we’ve been doing this for over 20 years. We are technology experts and we are consistently given the MSP 501 recognition for being a top MSP, which is an honor we received again in 2022.
It’s my great pleasure now to welcome Jenna Kirkpatrick Howard, who is our guest speaker and a cyber insurance expert. Jenna?
Jenna: Thank you. Thanks for having me. As Carolyn mentioned, I’m Jenna Kirkpatrick Howard, I work with Lockton Companies. I’ve been with Lockton for 11 years. I represent clients, typically nonprofits, but also some other real estate and construction clients.
I help clients understand
- how much insurance they should buy,
- what types of insurance they should buy,
- understanding their risk profile
- and how to manage risk for an organization to not only protect your balance sheet, but also to serve your mission.
And nonprofits are one of my favorite organizations to work with because it is so focused and mission driven. And I do understand that every dollar spent on premiums is a challenge, because that’s $1 less to serve on mission.
So I want to be very practical in the advice we give and understand and educate what’s happening in the insurance market where we’re seeing claims. And that’s what we’re going to talk about today around the cyber insurance role.
Poll: Does your nonprofit have cyber liability insurance?
Matt: Great. Well, let’s start off with a poll of the audience. You’ve learned a lot about us today, so now it’s our turn to get a chance to ask you some questions and so let’s start off with something that should be right up everyone’s alley.
I think regardless of where you’re at on the spectrum, I think you’ll find some really good content and resources that we’ll present here today.
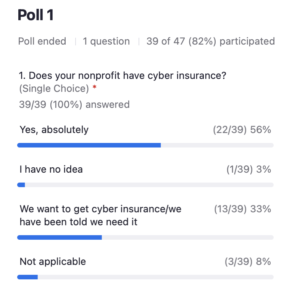
So a little over half say yes, they already have it. So that’s fantastic, with about a third of those folks saying, hey, we want to get it. We were told we should get it, what do we do? So and then a couple other folks are no idea or not applicable.
So we’ll see how those numbers change maybe over the course of the webinar.
Well, Jen, you want to talk a little bit about the threat landscape that’s out there from your perspective?
Jenna: Sure. So this slide is not meant to scare you, but this is information shared, and this is not-for-profit specific. This is across the U.S. it’s FBI data.
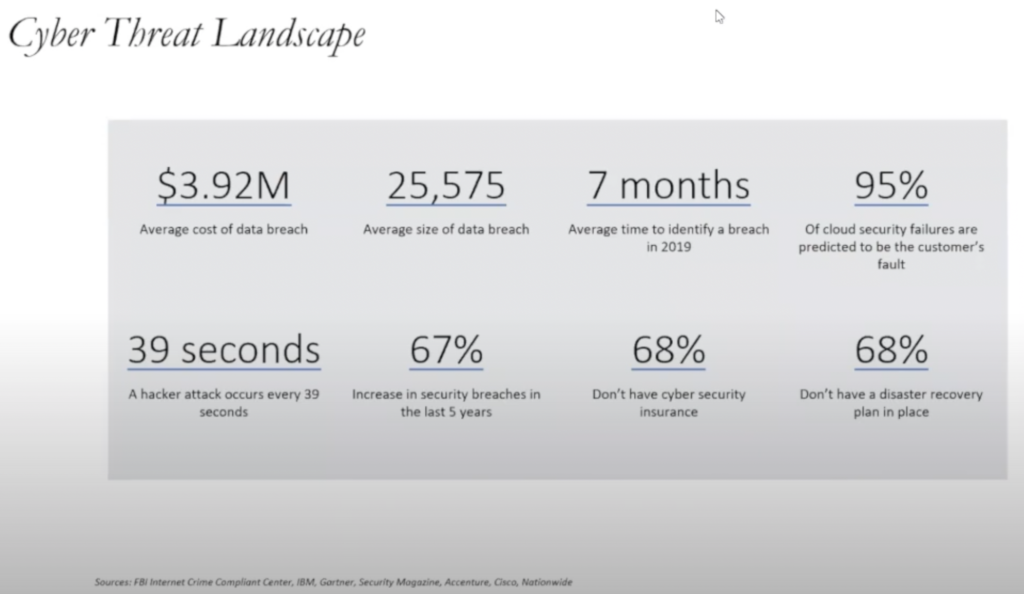
It talks about the cost of a data breach, the size of records that are breached, how long it takes to recover and identify that the breach is even happening, and what the causes are, how long it takes a hacker. This slide is useful because it really just says the threat’s real.
The threat’s real, regardless of size. When we started talking about cyber insurance, I don’t know, 15, 20 years ago, we were mostly talking about it with healthcare organizations or financial institutions or retailers because it was really industry specific. And now we see that we have claims at every size business, every industry class. It is truly a threat that transcends all sizes and missions. And unfortunately, we do see it in the not-for-profit space.
Coverage
So I want to talk a little bit about the groundwork. I know many of you already have cyber insurance coverage, but I’m going to demystify a little bit about what’s in the policy itself, and I will try not to be insurance lingo heavy.
There’s two sides to an insurance policy, a cyber insurance policy.
- First party coverage, which means money that you will incur as the organization that suffered the cyber breach or ransomware attack or phishing emails. This is the cost to reimburse you for the cost resulting from the event.
- And then there’s third party coverage, which is the cost to defend in case there was a lawsuit or damages that you owe to a third party because of the event.
So the two sides of the policy, the first we’re going to start with is that first party, these are your costs. It’s the breach response, any legal fees you would acquire for forensic costs. If you have to pay a cyber extortion or ransom payment, that is a first party coverage.
Any income you might lose with the system being down, if you have a donor link or you were in the middle of a fundraising effort and the system is down, if you could quantify the business interruption cost, that’s built into the insurance program or available on the insurance. Any data restoration cost to restore.
So all these things, if you’re thinking through all the things that your organization might need to pay for, if there was a data breach or ransomware attack, think of that covered under the cyber insurance as first party coverage. And there’s different limits that you can buy for first party coverage, but it is available on all cyber insurance programs.
Third party means if there is a privacy liability, if there’s regulatory fines, if there’s security requirements and payments, if you were sued by a group of customers or donors, or any sort of outside organization that you have then liability and settlements and that sort of thing. So there is third party.
We actually see in cyber insurance, there are less third party claims than there are first party. The majority of cyber claims, the amounts incurred are usually your first party. It’s far more common.
Cyber Loss Scenarios
Everybody tends to ask me, does this apply to my organization, and what are the potential events that could occur?
So we have at the very top of the list, those phishing emails; they come all the time. I get them almost daily. I’m sure you do, too.
You may even have phishing training for employees where you poach. You send out some potential phishing to see who would potentially hit the link or report it to the organization. The intent is to trick an employee into clicking a link that brings in and spreads malware or a payment is sent to a vendor to a wrong bank account. Those are sort of the phishing claims we do see, and there is some coverage for that. There’s a forensics investigation in the response.
Ransomware is the one you’re seeing all over the news today and has been a major driver of claims over the last few years. And this is where a nonprofit were to fall a victim to a ransomware attack. The entire system is down, and then you get an email and then you get notice that there is a demand for a ransom payment.
And the insurance policy will actually pay the ransom amount as part of the payment, as well as forensic investigation, any business interruption and extra expenses.
Now, it’s not always determined that the best course of action is to pay the ransom if there is access to backups, or you have the ability to get your system back up and running. So not every ransomware attack results in a ransom payment, but that is one option in terms of response to that type of claim.
There’s also dependent outage. We see this a lot around payroll providers, cloud providers, security providers. They fall victim to a breach or a ransomware event and you don’t have systems accessed because you’re dependent on them. So that is a fairly common claim scenario that we do see.
Prior to ransomware the number one claim driver was human error. It was the laptop left at the airport or in the rental car or left at the coffee shop, or they didn’t actually reboot, and something shuts down.
The human error element is a large driver of claims. The recommendation here, and you’ll see it further, is employee training around each of these things and how they can be diligent about how they manage their computers and software and access is really important and we’ll get to that.
And there’s some other things that you see here: stolen funds, unauthorized disclosure, and unsolicited communication. Less commons claim scenarios, but certainly scenarios that we have seen.
Matt, do you get a lot of questions around these scenarios as well?
Matt: Yeah, I think we get questions about, is this covered? Is this not covered? I think there’s also misconceptions around, well, I already have general business liability insurance. Isn’t cyber covered under that existing policy?
I think it’s helpful for organizations to understand those distinctions and then also, ask these questions or go down the scenarios so that whatever assumptions they have, like what happens in this case? If my computer’s stolen, is that covered under cyber or would that be covered under general liability? It’s helpful just to make it feel a little bit more real. Organizations can walk through those different scenarios to help understand, what am I actually paying for? What is this going to mean for me, practically speaking?
Jenna: We do see that; that question comes up a lot. I have a stolen laptop. Where’s this covered? Well, it’s a piece of property. So property insurance responds because it’s part of your business personal property.
But the question is, did this lead to a cyber event, was there a breach of data? Was there access to the system?
There’s also this concept of bricking that is covered under some cyber policies, meaning there has been malware put on a laptop or a computer that has rendered that computer to serve no other purpose than a brick. And so bricking is an ensuring agreement that is potentially covered under a cyber policy.
How Does Ransomware Work?
And I don’t want to spend too much time on the scare tactics around ransomware, but it is something that we’ve seen quite a bit of.
So I do want to include the typical three step process that we see around ransomware.
We see that there’s a
- compromise of a system and
- then there’s a deployment.
- And then there’s an extortion.
Oftentimes the hacker will start with the backups and you won’t necessarily know that the backups have been attacked first. And then when your system goes down and you receive the extortion demand, you’re like, well, I can go access my backups. And then you go to the backups and the backups were also taken down. That is a tactic that we’ve seen over and over again.
I would say, if we were doing this webinar in 2019, we would have seen that the ransom demands were in the $50,000, $100,000, $250,000 range. Ransom demands are significantly higher today, and oftentimes if the hacker has been in your system and you have a cyber insurance policy saved on your system, they could actually access the policy and see what your limits are.
And so “strangely enough”, we see some extortion demands to be equal to the amount of insurance you purchase.
So a couple side recommendations
- have your cyber insurance policy saved someplace special
- and have a printed copy of it. If there were an event and your systems were rendered useless, you’d know who to call.
We’ve had scenarios where we had a ransomware playbook or a cyberattack playbook, and our clients knew who to call and all our phone numbers. And that was all saved on their share drive, and they didn’t have access to it when the event happened. So they didn’t have a paper copy.
So maybe going back to paper for one or two things is a good suggestion.
Just a few snippets here about ransomware, because it’s a hot topic of conversation. We do see it some in the not-for-profit space, but more in some of the bigger names that you see on TV.
Matt: Yeah. And I would just say, all of this reinforces the fact that a lot of the cybercrime is financial driven, it’s a criminal enterprise, it’s a money making venture. The organization doesn’t necessarily care about you or your great mission. You, to some extent, just represent a financial target. And every nonprofit has some resources and so I think that’s why the drivers for both ransomware and also spear phishing and wire fraud, it helps to put that into context to understand it’s just about the money.
Jenna: Right.
Poll: Who deals with cyber insurance at your nonprofit?
Matt: Great. So let’s take another poll here,
Who deals with cyber insurance at your nonprofit?
So it’s either
- You,
- CFO,
- Executive Director,
- not sure,
- or if you’ve maybe outsourced that [to an IT Department or Outsourced IT Provider].
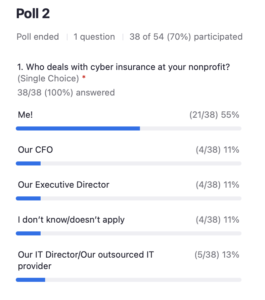
So looks like in terms of the results we’ve got, 55% of the people in attendance deal with cyber liability insurance. So good to have the right folks in the room.
About 11% have their CFO deal with it, 11% Executive Director, another 11% kind of don’t know, or and then about another 13% saying that their IT Director or Outsourced It Provider is also dealing with cyber liability insurance.
Jenna: Great. So from the polls, we have some of the buyers of insurance and we actually have a good portion of you that actually already purchased cyber insurance for your organization.
Cyber Market Update
So that probably leads to the question of:
- Why do the prices keep changing?
- Why has it gotten so expensive?
- And because it’s gotten so expensive, what limits should I really purchase?
Common questions, we see it all the time. And I will say the cyber market in particular has been a major area of disruption over the last two years. Last summer was really the biggest transition time.
Lockton data shows us that in the first quarter of 2019 of the cyber insurance renewals from our client base, which is quite large here in the U.S., the ranges that we were seeing were some clients were getting on the low end an 8% reduction year over year premium, and some were getting a 6% increase in renewal. This indicates a very stable market, very stable that for the large part, cyber insurance renewals were coming in similar pricing year over year.
And then you see by the second quarter of 2021 on the low end, clients were receiving a 9% increase year over year; on the high end, it was 67%.
A 67% year over year premium increase is significant for any client and that’s a large jump. And then you see by the third quarter we were seeing 130, 150% for the next two quarters. And even on the low end, the 28% or 51% year over year increase.
So this is the time where many clients were questioning: Can I afford cyber coverage? Should I even maintain it? Is it worth it? Should I cut my limits? Should I lower my limits because of the cost increase? And we were still seeing, at the start of this year, you’ll see April 2022 data that these were holding strong.
Now I will say, anecdotally, we haven’t released our next quarter results, we are seeing some stabilization. Unless there are controls concerns, and we’ll get to what that means in just a few minutes, we’re not seeing the 150% year over year increases as much as we once were. We’re seeing more in the lower end, the 30 to 50% year over year increases.
So I will not say this market has entered a soft market, but we are seeing some stabilization in pricing.
This is largely due to the start of ransomware. For the most part, cyberinsurance markets were pretty successful and they weren’t having as many claims payment as they were receiving premium. So they were profitable. And then in 2021, when the ransom payments started, when there were major ransomware events, there was not enough premium for the loss amounts they were paying. And so that’s why we see a large fluctuation over the last few years.
So the underwriters have taken a couple steps, not only is this premium piece at play that they’re looking for large increases every year, they’re also very, very, very focused on controls. [Controls: what actions you are taking at your organization to protect yourself; similar to having a sprinkler system to get fire insurance.] So at one time, if you’ve been purchasing cyber insurance for a while, you likely saw a two page questionnaire that asked a little bit about how many records you had and your address, and maybe some revenue information, and that was it.
If you have filled out a cyber insurance application in the last few months, they have gotten 10 pages long, and there’s maybe a supplemental for ransomware, and they’re going to dig in and ask many more questions.
So, Matt, since you had the luxury of filling out so many applications, in helping fill out these applications, what are you seeing the critical areas that they’re focused on?
Matt: Yeah, going back to the previous slide and seeing the price increases aligns 100% with our experience. In 2019 you could get a two-page application, put down any answer you want, you got a really affordable rate and you were covered and you could move on.
But this year, our experience has been multi-page applications. If organizations aren’t able to say that they meet the requirement for multifactor authentication for all systems, if they don’t have policies in place, if they don’t have disconnected third-party backups of their data, they’re either not getting coverage or they will maybe have a month or so to prove that they’ve implemented that control.
And so this has been really helpful for me to see, from the insurance perspective, what’s happening to impact the IT policy controls. Yes, two or three years ago, we’ve been preaching MFA for a long time now, once, we would say, hey, you really should have this. Now we’re seeing the cyber liability insurance policy say, hey, if you don’t have this implemented, you’re not going to get coverage at all.
That’s prompting a lot of the organizations we work with to implement some of those long-deferred cybersecurity projects, because now they’re faced with significant cost increases or maybe not even getting coverage at all, to implement some of those core controls.
As you’ve got here,
- multifactor authentication is a requirement,
- that third party backup in a disconnected system, as you identified the bad guys are in your network, and so you want to make sure that data is disconnected and somewhere else so that you can recover,
- and then also making sure that policies are in place to help guide those decisions
- and get ready for the next round of controls that are going to be asked for in next year’s application.
Jenna: Yeah. I will say that the applications are changing on a quarterly basis every time there’s the next event. So it started with SolarWinds. That was probably the major, first change of the cyber applications. Did you have any exposure to solar winds? Then it was Microsoft Exchange.
So each time there’s a big event, there tends to be more questions around what was the potential cause of that event, and did you have any exposure to it?
What we have found is the most recent control is training. Every insurer wants to see that you are doing employee training because that human error element is still at play.
You have multifactor authentication; it is absolutely required. Basically, you’re not insurable unless there’s MFA and then the backup pieces and in policies and procedures. So currently the carriers are really focused on training.
Security Training Requirements
And there’s a couple areas where we’re seeing training required.
It’s educating leadership teams on what to do if an event were to occur. Do you know who to call? Do you know who the vendors are? Do you know how to report it? So there’s an education on “What to do if.”
That can be solved in a tabletop conversation within your organization, bringing Matt in to have some of those discussions.
It’s also employee education around not to click links and open attachments and providing training and potentially your own phishing internal governance plans, and building a culture that it’s important to report if you clicked on that link.
So the first thing that employees do when they click the link is think, “Oh no!” and they don’t want to tell anyone. Well, there needs to be a culture of, “I did this and I need you to help me. I need you to investigate.”
There needs to be employee education around. It’s a culture that supports good governance and reporting and makes sure it’s good cyber hygiene that it’s done on a really regular basis. Underwriters will certainly ask on an annual basis about training, but they get even more excited if you do it more than just annually. [Community IT uses KnowB4 training but there are many products on the market.]
Peer Benchmarking
So this leads to the question: since prices are going up and controls are more scrutinized by underwriters of
- How much limit should I buy and how do you even know? We take a multi-prong approach when we get that question. There’s always good peer benchmarking. What does everyone else in my space do?
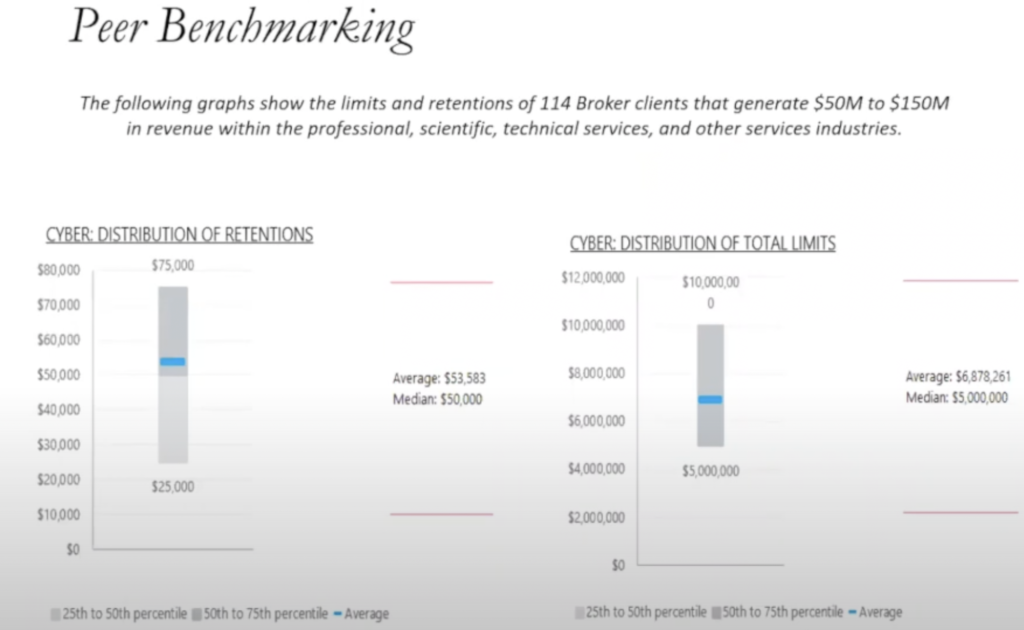
So in this particular case, it’s a nonprofit that does scientific research and their revenue band is between 50 and 150 (thousand dollars). I won’t tell you that all your peers know what they’re doing either, but at least you can sort of see where they’re at.
A big point of conversation among the cyber insurers today is they were raising retentions (the amount you are required to pay before the insurance company will start paying). At one time, cyber policies had a $1000 deductible or $5,000. We’re now seeing 25 (thousand dollars) being a standard of lowest retention available in the market. I have seen some lower, but $25,000, particularly in this revenue band, is certainly it. So if you see that here, between 75,000 of retention and 25,000 of retention, that we’re seeing a median is around 50. So in this peer group, that $50,000 retention is sort of the standard. And then if you average it among the client base.
And the second question is, well, what about limits? In this case on the low end of this revenue band, you see a $5 million limit being purchased. On the high end, you’re seeing 10. And the median is around five. The average is around 6.8.
Good data to have. I always tell clients, don’t bet on pure benchmarking because you don’t necessarily know if your controls stack up, if your training stacks up, if your revenue and your culture is not necessarily like your peers, but it’s good information to have, right?
One other area that I actually find more useful is, we party with someone called Cyber Cube and many brokers and insurers create partnerships with similar organizations. It’s an analytics tool that runs a Monte Carlo simulation of all different scenarios of cyber events, and this changes based on what’s happening in the marketplace. So if I ran Cyber Cube today and I ran it 30 days from now for the same organization, we’d get a different result.
But what I find interesting is that it runs all these scenarios. At the low end, you might have a $55,000 event, at the very high end, you may have a $40 million event. That’s a big, big delta. So it tells me, if you’re looking at percentages, in 85% of all of the scenarios run, an event would be less than two and a half (million dollars), right? So think of how risk tolerant your organization is, or risk adverse, and buy within the percentile for limits of where you feel comfortable.
For the most part, in my not-for-profit clients, I see limits purchased somewhere between 80 and 95%, depending on budget, depending on risk profile. But at an 80% chance, if you purchased a $2 million limit policy, you would cover 83-ish percent of all claims scenarios that we’re seeing in the current marketplace.
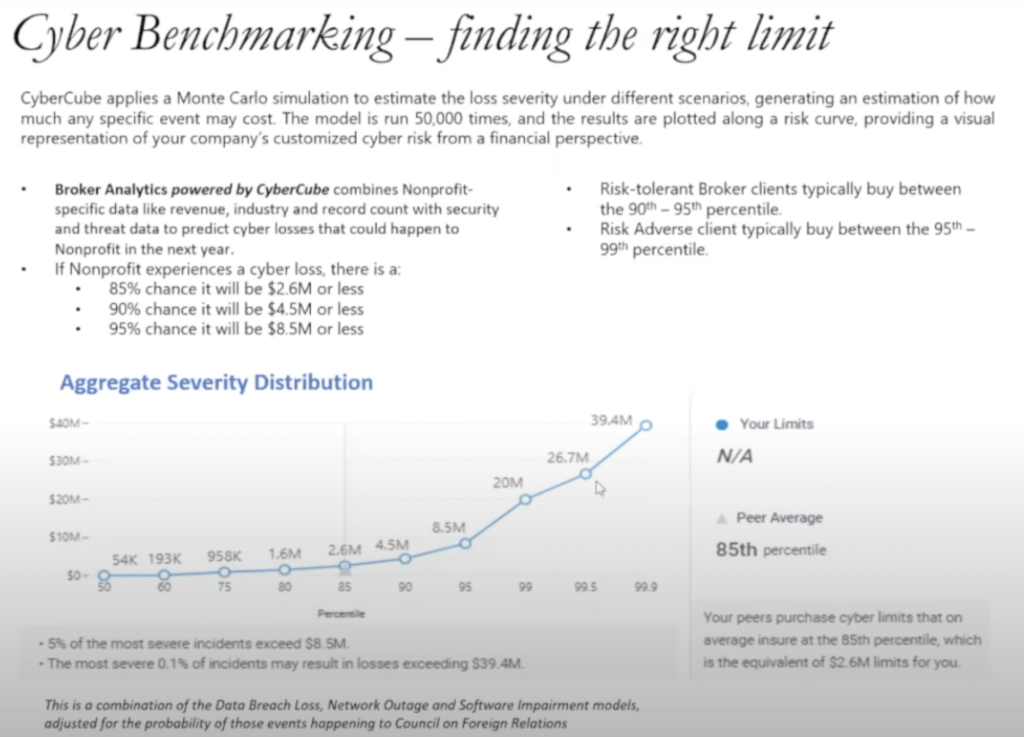
If you bought a $5 million, you’re covering 90 plus percent of all of the claim scenarios that we would run. So this is good information to have as you’re approaching your insurance renewal and seeing various limit options and the premium cost and what retentions. If you run the simulation of all the claims scenarios, where would I fall?
Overall Cyber Risk Score
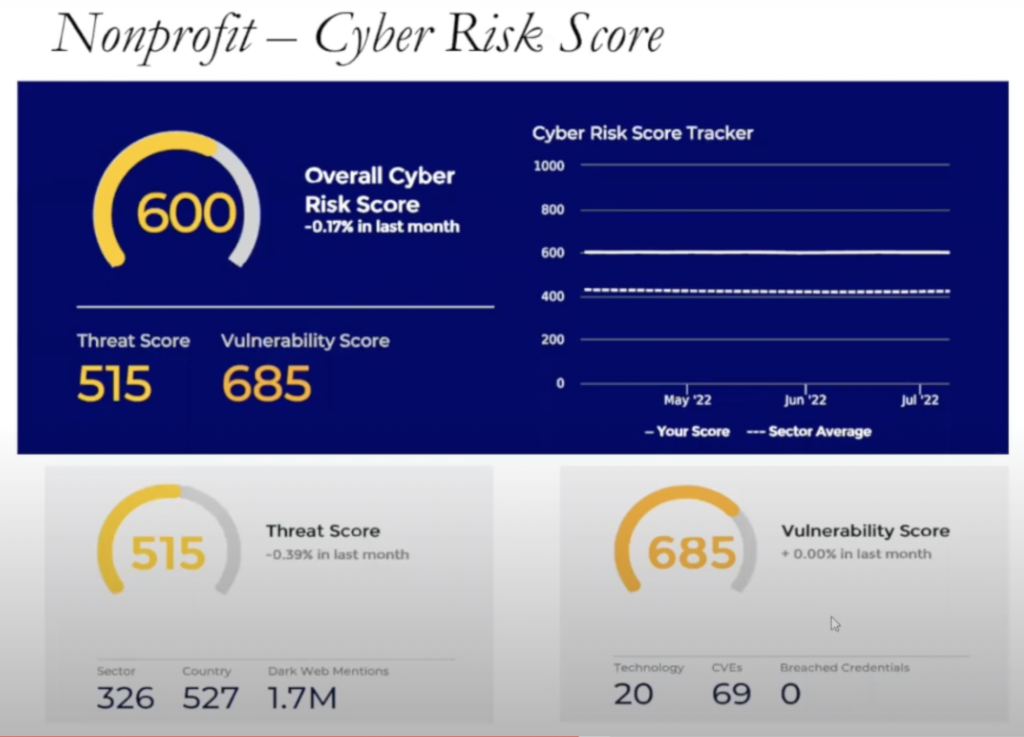
Another score that a lot of insurers use is that they will do a web test or vulnerability test. So they won’t actually go into your firewalls, but they will actually do their own sort of scan and test and provide a risk score. This is part of the underwriter’s review.
You fill out this great application; on the backside, they’re actually going to do their own scan and determine if they can find any vulnerabilities or threats and that will be part of their underwriting.
It’s always great to know what that score is. Sometimes you can ask your insurer; sometimes your broker might have access to something like this, but it’s another piece of the pie. Is my cyber score better than I’m seeing in other industry sectors? Am I above average, am I right at average, am I below average?
So in this particular case, this nonprofit had a 600 overall risk score and the average is just above 400. So they actually had a better cyber posture and network controls than some of their peers.
There might be lots of questions in the chat about all of that information, about what’s happening in the marketplace. What types of controls the underwriters are looking for? How do I even determine what limit I should buy?
Matt: Yeah, there was actually a good question about MFA that we’ll get to here as part of the next poll question.
Poll: How common is cybercrime?
But one thing I’d love to get a sense of, and this is a multiple choice question, is:
How common is cybercrime? In your organization in the past two years did you, or maybe an organization that you’re aware of, have any of these different events happened?
- Compromised account. That would be whenever somebody, other than a primary assigned user, had access. That could be also known as a hacked account.
- Maybe your organization experienced wire fraud. That’s when some banking account information was modified or changed without the organization knowing and funds were transferred out. Gift card fraud, maybe not as big of a financial loss, but still notable.
- We do see some nonprofit organizations deal with actors called advanced persistent threat actors. State sponsored well-resourced hacking groups that are interested in data exfiltration or spying and understanding what an organization is doing.
- Ransomware, which we’ve already talked a lot about.
- Our generic malware, viruses
- maybe that supply chain attack or compromise. As Jenna mentioned SolarWinds, Kaseya. These are all examples where a vendor was compromised and that led to data loss or data exfiltration for the companies that were using that vendor.
- Or catchall (other).
- Maybe you’re the person that hasn’t seen an incident yet.
There was a question around the MFA implementation and I’ll add on my own two cents here.
For a lot of the application questions, it’s often a binary. It’s like, yes, we have it, or no, we haven’t. But are there opportunities for organizations to have some gray areas? Maybe organizations that have a lot of kiosk users that don’t really have access to much, or maybe they can’t log in from outside of the organization. Do all those accounts have to have multifactor authentication as well? What’s the flexibility in terms of the application of some of those controls?
Jenna: Don’t use the application as the only communication to the underwriter. So if you answer something like, “Do you have MFA on every single account?” and you need to answer no, having a side answer of ”Here’s the reason why, because we don’t have the exposure. Our reason why is that we have a compensating security measure that we’re taking.” That matters, because the no answer triggers all sorts of red flags. And without any explanation beyond that, it creates the worst-case scenario with the underwriter. If you can create a narrative that explains why that answer is no, and it’s “We’re implementing it in the next 30 days, or it’s something we’re exploring, or we don’t have exposure to it,” that matters so much.
So don’t feel tied to the yes and no answers in the application. A narrative is always helpful, and we even find that an underwriting call may be worth it also to walk through an application. Underwriting calls, when you build that personal relationship with the person that’s going to need to offer you the quote, there’s often that human element of “I want to work with this organization because I love their mission, and I think they’re going to do the right thing, so I’m going to offer a quote,” where they maybe wouldn’t have, if they were only staring at a piece of paper.
Matt: Great. Thanks. That’s really helpful information to hear.
Poll: How common is cybercrime?
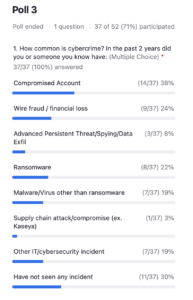
We can see from the poll results that cyber incidents are very pervasive.
We see 30% of respondents said they’d had a compromised account. With a quarter of people experiencing wire fraud or knowing an organization’s been a victim of wire fraud and ransomware again, being at about 22%.
We just can see that the adage of cyber incidents is not really a question of if you’re going to have something, but when, and that’s why these cyber controls are so important Being able to connect the dots between why the insurance company is asking for all these things, tying it back to the financial impact is really helpful and helps to build this story around why that’s important.
Jenna: Agreed. So we’ve talked about what the policy actually covers and why the prices have gone up and how much limit we should buy and how to analyze how much limit or set my retention.
What Happens When an Event Occurs?
So the next obvious question is: what happens when the event actually occurs and what does my staff need to know; who needs to know; who do I need to notify?
And it’s a really good question. And we oftentimes will have a flowchart that we share with clients that I think helps demystify the process.
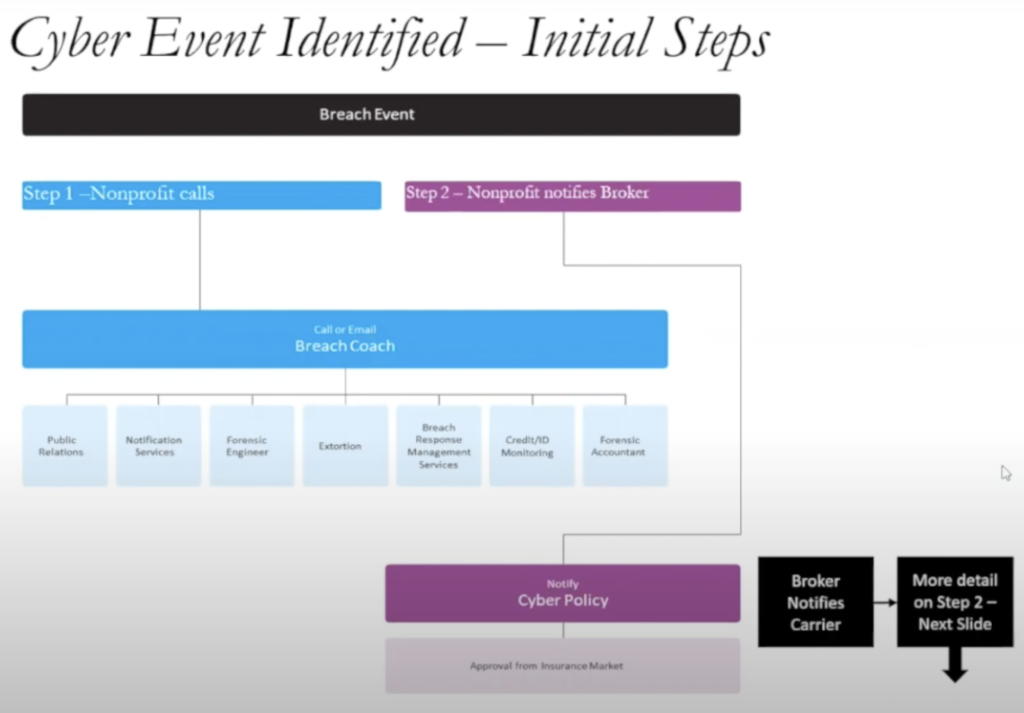
Every cyber insurance policy is going to have selected vendors, or you may have selected vendors that you notify your insurance carrier that you plan to work with.
The first call oftentimes needs to be to a breach coach.
So a breach coach, that’s oftentimes an attorney that you’ve worked with, someone that you need to notify when an event occurs so that everything is held as privileged and confidential in the process.
You also need to call your broker and notify the insurance carrier because the faster you can do that, that expedites access to all of those vendors that you’re going to need to help you mitigate the risk. So as soon as you find out, ideally within the first 24 hours, you make two phone calls: that breach coach, and if you don’t know who the breach coach is, certainly the broker in the cyber insurance market.
Now I will say that this is information that we share. We have a client, they’ll notify us and we will then help them notify the insurer.
And it starts that cascade of law firms, forensic advisors, any sort of monitoring services; that all happens very quickly.
We see the initial acknowledgement of claim and the investigation happen, and all that happens really fast in the first weeks, particularly if your network is down. The first goal is, how do we get the network up and running again? Everyone is focused on that, and so that happens very quickly.
Now the mitigation and the remediation, step three and four can take months and months and months and months, right? So you know what happened, you’ve maybe paid a ransom payment, or you’ve got your network back up and running because you had access to the backups.
Now, how do you mitigate this from ever happening again? How do you minimize the exposure then how do you mitigate it from ever happening again? Those can take months and months and months.
Oftentimes, people think, Oh, it’s a cyber attack. It needs to happen fast, and we need to be back up and running, and then it all stops. Well, the claims process and the incident process, it does not happen.
The initial response is fast, but then there’s a lot more that has to be uncovered and mitigated. And if you need to notify the FBI and local law enforcement, there’s a whole host of things that the breach coach and the insurer and all the panel vendors will help you walk through.
And they’re very, they’re really talented at this type of work. They have sadly lots and lots and lots of experience in this space. And even though you may have a pre-selected vendor of who you’d want to use for forensics or who you’d want to use as a law firm, oftentimes the insurer will say, “That particular vendor that we would’ve maybe used, we have overloaded them with other claims that are happening, and then for this particular scenario, we would recommend this one.”
So that access to the insurance carrier and who they would work with on your particular scenario is really important in the first 24 hours.
And then you also have that post incident consideration.
- So any sort of accounting fees,
- if there’s a business interruption that you’re going to need to quantify for reimbursement,
- improving your incident response, because nothing’s better at testing out your incident response plan than a real event. And you can maybe find where those holes are. Who’s hard to find on a Friday night when they always tend to happen?
- And so how do we keep backups and
- What education needs to come to employees and leadership
- and then any policies and procedures that you may want to approve and change?
It’s a very stressful time, but there are professionals and well-versed individuals that do this regularly that can walk you through this process.
Matt: Yeah, I think it’s great to have this communicated again. Community IT, we’re a managed services provider. We’re really good at day to day support. But when it comes to incident response, while your MSP might be able to help identify some things or put out the immediate fires, that first call going to the breach coach so they can bring in the big guns, so to speak, to really help provide those covered vendors, is a great step.
And I think a lot of organizations need to hear that again.
Your MSP might not be the first people that you need to call. If you’ve got cyber liability insurance, make sure that that’s clearly communicated. So when there is an issue you can bring in the resources that you already have access to.
Jenna: Right. The cyber insurance policy is set up for you to access those resources; make good use of it.
Ransomware Events – Do Not
I think it’s always important, particularly in ransomware, where there’s that “do not” list. Like, don’t go it alone.
Don’t try to negotiate with that threat actor alone. There’s a couple reasons not to do that.
- Number one, you’re maybe not qualified.
- And two, the team that will identify the potential threat actor, because the threat actor is not going to come out, necessarily give you their name and their group that they’re associated with. There needs to be an investigation. And there’s a whole list of OFAC Sanction Organizations and Groups that U.S.businesses don’t do business with, and so part of the investigation goes through is this particular threat actor on the OFAC list. So something you don’t necessarily need to do, but that is certainly part of the process.
We also don’t make hasty decisions around if an employee made a mistake or contributed to the incident and how you speak to the employee and how you communicate. Make sure that you don’t make some hasty decisions.
Really think through and communicate with your employees and customers. Make sure that you’re doing that in consultation with your legal and crisis communication advisors.
And make sure that you’re using the vendors that are available to you. It’s probably not best to start Googling “who helps me in a cyber attack.” Use your broker, use your insurer, use the partners that you’ve already identified. If you don’t know who those are as part of the cyber insurance, make sure that you vet that now, pre-event, so that you know who to call.
Carolyn: Can I just jump in with a quick question on a lingo that you just used of the OFAC, can you just let us know who that is?
Jenna: Office of Foreign Assets Control. So there is a list of terrorist organizations and nation states that U.S. businesses cannot do business with. This isn’t just an insurance thing. It’s an all-business transaction thing, but insurance carriers cannot do business or send ransomware payments to any organization on that OFAC sanctions list.
So that’s part of the investigation process, because sadly, a lot of the threat actors are in fact, terrorist organizations and organizations that are known. I am clearly not in forensics investigation, but there is a way based on the ransomware attack or how the information’s perceived that they can actually identify the threat actor and threat actor group.
Cyber Claims F.A.Q.
So I get this question a lot:
How quickly will a carrier engage?
I will say most cyber carriers have a reporting via email and oftentimes it gets called in because the site’s down. They will respond almost immediately. I’ve seen engagement within the hour it’s been reported just because of the need to quickly investigate and get the system back up and running and identify the threat actor.
The process to pay or not pay a ransom is one that has a lot to do with how quickly you can get your system back up and running. Do you have access to backup? Who is the threat actor? There’s a long decision tree that goes into pay or not pay that you will have lots of advisors to help you with as part of your cyber insurance vendor list.
The value of a cyber policy to a nonprofit is, I personally think, access to all of this expertise that you likely don’t have in house. Unlike other parts of insurance and other insurance policies that are really there to provide defense or settlement or pay for the fire loss, cyber has a whole host.
Many of the carriers have pre breach and pre response and training available and there’s resources available as part of that insurance policy. Then post breach or post attack that access to all the vendors. So there is value beyond the contract and the premium payment itself for a cyber policy that maybe isn’t available on some of the other insurances that are out there.
We talked a lot about the controls. Matt, do you want to talk about what you’re seeing as good cyber hygiene and first steps that you would recommend?
Matt: Yeah, I think we’ve talked about a couple of those resources already and also want to answer a question that came in:
What resources are out there for organizations that are looking to learn more and understand the landscape a little bit better?
So I will highlight the link to the Lockton free download Guide here.
In terms of the guide that Lockton had, I found it really helpful to kind of map, why is my application asking me to do this? And then map that to the cyber control.
I’ll also put in a plug for Community IT’s own Nonprofit Incident Report. We work with about 170 nonprofit organizations, so our service desk responds to hundreds and hundreds of tickets. We take all those security incidents and lift them out and then report them back as a way that helps us understand what’s happening with small to mid-size non-profit organizations and the security threats that they face.
And then coming out of that, I think really gets surfaced the controls that that organizations should have in place, because it represents a way to remediate the risk and also tie it back to some of the controls that we’re seeing on all these cyber liability insurance applications that we’re filling out.
Certainly MFA for everything now, the security awareness training, I’m really glad to see that on the list because while I love all the technical whiz bang tools that are out there, I think fundamentally, having trained and educated staff that are able to identify or not click on that link, be able to have a good security culture where people can share with the IT, hey, this looked weird or this strange thing happened, can you take another look at it?
I think building that culture is really important to having a secure organization. So again, it’s the fundamentals of backups and patching, multifactor authentication, combined with making sure that staff only have access to what they need.
I know that’s another challenge in the nonprofit world; everybody’s doing so much already, so it’s just easy to give everybody admin access. But really being attentive, particularly within the database world, everybody doesn’t need to have access to all the records in the system. People should just have access to what they need. Finally, rooting that all in a policy for the organization, so that it’s pretty clear and you can have a common set of understandings to build out all of these controls.
So again, there’s a couple of resources out there that I think are helpful to build your understanding and identify the good policies and procedures and technical controls to have in place.
Questions
Jenna: Okay. That leads us to a little bit of left over time for questions, which we promised we would do.
Matt: Great. Well, this has all been I think really helpful. Let’s see, there were a couple of questions.
Maybe clarify what would be covered or considered covered under third party loss.
In an example of an organization with a database of donors, that database is hacked. How far does that coverage go if the donors are then extorted or their information is used to target them as individuals? Is that something that’s covered or where is that boundary?
Jenna: It doesn’t even need to be a class action, but if a donor sues that they suffered financial harm because of your cyber event, that would be privacy liability.
Also, if you have any regulatory fines as a result, you didn’t comply with certain unsolicited communications, in Europe, it’s the GDRF. California has a number of regulations. If you didn’t comply and there is a regulatory fine, that can be covered under the third party.
So think of it as if someone were to sue you because they suffered financial harm or you incur fines or penalties as a result of non-compliance to cyber security laws and regulations.
Matt: And is there any coverage that would be extended in the absence of a lawsuit, or is that the only way that these kinds of additional protections come into play?
Jenna: Well, you still have the first party, so anything that you incur in terms of cost, that would be covered on the insurance policy. But the most common way, particularly in the U.S., is a demand letter. You receive a demand letter from a donor that says they suffered financial harm. That would trigger the liability side. It doesn’t necessarily need to come in the form of a lawsuit, but there needs to be some sort of notification
Matt: Okay, great. Let’s see, we have another question and we see this too.
Where should nonprofit organizations go to kind of find a broker?
We get this question where it seems like the existing provider maybe doesn’t understand their needs, or maybe isn’t familiar with cyber. Where should nonprofit organizations go to make sure that they get the right coverage?
Jenna: Yep. So there’s a couple different groups that specialize in the not-for-profit sector and the brokerage community, Lockton being one. But we are one of many, so I’m not going to necessarily make a plug.
There’s also the Not For Profit Risk Management Institute, I believe is the name of it. It’s out in Leesburg, Virginia. They are a good resource for risk management tools, access to brokers, good questions that you should ask your broker, insurance questions in general. And they fully support the not-for-profit community. So they’re actually a really good resource and I can help link that organization, as well.
Matt: Let’s see, we have a question and we see it in the news as well.
The organization has cyber liability insurance, but whenever it comes time to settle a claim, the organization seems to get less than they were expecting or hoping for. Is there a way to anticipate that or what should organizations be aware of to make sure that they’re made whole whenever they suffer one of these attacks?
Jenna: Have a very strong advocate. Keep very good documentation of any cost that you may incur. Really work with forensic accounting to quantify a business interruption loss. That’s the biggest piece where we see arguments.
It’s easily quantifiable. How much was the ransom payment? How much did the legal fees come in? Because we have all the invoices associated with that.
The hardest part to quantify, and oftentimes what I see the biggest area of contention with insurers and policyholders, is around how did we get to the business interruption cost? How much did I really lose in income revenue or incur as additional expenses?
So make sure you’re working with an organization to help you quantify that through documentation that an insurance carrier will accept.
Because if I could write an email that says I lost $1 million, they’re going to want a decent amount of documentation to support that that is what that you would’ve actually received in revenue for the week that the system was down.
And if it was your busiest season of fundraising, you were in the middle of a capital campaign and you were on that final week, that week of donations would look different than the week prior.
So being able to create your business case is going to be really important and having the right advisors to do that, I won’t say it’s the only area, but it is the area we see the most amount of discussion of. Was I made whole from the insurance proceeds?
Matt: That’s very helpful. So we have another question. I think it’s great we have a lot of decision makers that are responsible for cyber liability insurance on the webinar, but then there’s also a big chunk of folks who I think maybe see the need to get this cyber liability insurance coverage, but maybe it’s not in place.
What are some ways that people can make this business case to organizational leadership, that this is something that is important and something that we should do as an organization?
Jenna: So that’s twofold.
The first is understanding the threat landscape where if your systems were down, what would be the repercussions and for how long could you go on with the system down? What does that look like?
So that is the number one value proposition for having the cyber insurance policy and all of the vendors that will support you after a cyber attack. So, understanding what your risk exposure is, understanding what your risk tolerance is for that event will help you either make the business case to buy cyber insurance or the business case for what limits in retentions you should buy.
Some organizations, they say, listen, we can do the small stuff. I’m willing to take a higher retention so that my premium’s lower, but I want to make sure I have access to all the vendors. And you’ll still get that even if you take a higher retention.
So knowing your threat landscape is certainly the most important thing. And then knowing if you have the controls in place to get a good insurance quote.
So going back to all the controls, the MFA and the trainings and everything we just talked about.
Making sure of those two: you understand your risk profile and that you have all the controls in place, that’s going to be the strongest submission to get a great quote from the insurance market.
Carolyn: I am so sorry to jump in because this has just been such a great hour and I feel like we could talk for a lot longer about this, but I want to make sure that we remind everyone what our objectives were.
I think we have hit a lot of these objectives.
We understand a lot more about
- cyber insurance,
- the landscape,
- the risks,
- some of the lingo,
- where to go for more resources.
I just want to thank you so much Jenna. I want to mention to everyone on the call right now that if we didn’t get to your question, we will try to answer as many of those as we can in the transcript.
I want to invite everyone next month to our monthly webinar series. We’re going to take a hard turn onto a different topic, SharePoint for Nonprofits. And this is a joint webinar with Build Consulting and Steve Longenecker, who is our SharePoint expert here.
And if you’re thinking: SharePoint? I don’t even know. Do I use SharePoint? If you use Microsoft and you are sharing your files, you are storing and sharing your files in SharePoint. So this is a great webinar for you to come back to and learn a little bit about setting up that architecture so you can find what you’re looking for and share it easily.
That’s going to be next month on September 21st, so you can register for that.
And I just want to thank you again, Jenna, for sharing all of your expertise and knowledge with us.
I actually was thinking when you were answering the question about how to convince a leader. Show them this webinar and show them that slide with the threat landscape. And I think this just helped me understand so much more about it.
And we just thank you again so much for spending your time with us and thank you again, Jenna and Matt.
Additional Resources
Lockton Companies has published a free downloadable Guide to Basic Controls Demonstrating Cyber Preparedness here.
“To qualify for cyber insurance, insurers require organizations to have certain basic controls and be prepared to respond and bounce back quickly in the event of a cyberattack. This guide explains the major control categories that must be implemented to qualify for cyber insurance. These control categories are not an exhaustive list of all insurer requirements. Multiple factors are considered by each individual insurer when evaluating an organization. However, the consistent message from cyber insurers has been that the controls discussed in this guide are the ones they find most important at this time.”
The US government has incident response plan templates and playbooks available here: https://www.cisa.gov/cyber-incident-response The Incident Response Playbook includes a checklist for incident response and another for incident response preparation, and both can be adapted for use by organizations outside the federal government. Jenna says, “A customized incident response plan is usually prepared for clients by their preferred law firm. Incident response plans vary widely based on the internal structure reporting and partnership with vendors, law firms, and the nonprofit client.”
Thycotic is a cyber security firm that provides a free Incident Response Plan template on their website. It can help enable your IT operations, security, and incident response teams to form a united front against an attack, coordinate a rapid response, and maintain your business continuity. The incident response plan template contains a checklist of roles and responsibilities and details for actionable steps to measure the extent of a cyber security incident and contain it before it damages critical systems. You can readily customize the template to match your incident response policies, regulatory requirements, and organizational structure. Thycotic has other templates and free resources available on their website.
SANS is a cyber security organization with many document templates, and although many are technical and oriented toward IT and security providers, there are several templates of governance documents that can be adapted to your organization, including incident response templates. Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cyber security professionals with the practical skills and knowledge they need to make our world a safer place.
