We’re proud to note that many nonprofits have done an admirable job of adapting to work in the wake of the COVID-19 crisis. Largely, that’s meant going remote, with nonprofits setting up systems allowing their employees to work from the quarantined comfort of their own homes. However, the impact of COVID-19 on nonprofit cybersecurity is clear.
The success of the quick switch has been encouraging to see – but there’s a dark side to the speedy transition, too. Rapid change, in combination with the emotive impact of the crisis itself, has opened up a world of opportunity for cybercriminals to prey on technical and social vulnerabilities.
As nonprofits weather the coronavirus crisis, it’s important that they continue to strategically minimize their cybersecurity risks.
To that end, let’s look at several of the ways that cybercriminals are seeking to take advantage of vulnerabilities related to COVID-19. We’ll present each in the hope that, with the knowledge in hand, nonprofits will be able to avoid being victimized by these methods.
Here’s the impact of COVID-19 on nonprofit cybersecurity.
Phishing attacks are capitalizing on the situation.
Phishing is an attack method that relies on social engineering to dupe users into compromising actions. These might include sending confidential data or downloading a malicious application.
The classic example is the scammer masquerading as an obscure foreign prince to ask for a large wire transfer of funds; while that approach has become laughable, modern phishing has become far more subtle. And the coronavirus is the perfect premise to encourage unusual actions.
This is already happening on a large scale through the most common vector of phishing attack: email. Messages on this channel – like the one below – are structured to capitalize on the climate of uncertainty, incentivizing recipients to take actions they might not under normal circumstances.
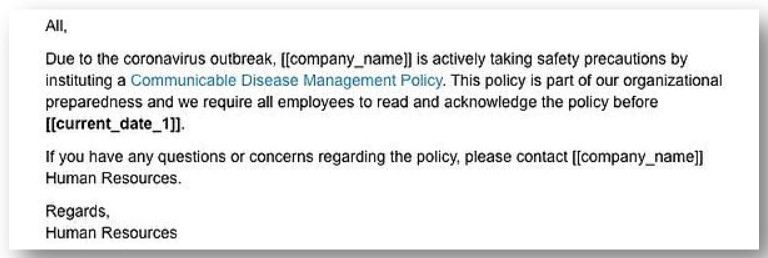
The request seems reasonable enough, but when users click the link to download, their computers are compromised with malware.
To avoid falling victim to a phishing attack, always check the email address of the sender. Many phishing efforts are sent from email domains that are close spoofs of a trusted sender with minor misspellings or different top-level domains (myorganizaton.com instead of myorganization.com, or nonprofit.co instead of nonprofit.com).
Helpful tools are being spoofed.
This technique, like phishing, relies on social engineering trickery to be effective. Spoofed tools are built to look like helpful and legitimate resources. However, on engagement, they’re designed to compromise users’ systems.
For instance, researchers have discovered an Android app that purports to track COVID-19 cases, but, on download, is actually a ransomware attack, locking users’ phones and demanding a payment of $100 in bitcoin.
Fake tracking sites have also been reported. These are designed to spoof existing sites (like the John Hopkins tracking page) while delivering malware via drive-by methods to site visitors.
As with email phishing, the best defense against these threats is vigilance. Check to make sure domains are legitimate before visiting. And only download applications from trusted sources.
The increase in remote work has opened new vulnerabilities.
Finally, the mass shift to digital work channels is making cybersecurity more difficult.
That’s because users who would normally be in-office have been forced to go remote, and many of these people aren’t trained in cybersecurity best practices. They’re likely to be using personal devices to access work systems and files, introducing entirely new sets of vulnerabilities into their organizations. The hardened network at the office means nothing if users are working from an unsecure network at home.
Additionally, many remote systems that nonprofits have set up were constructed hurriedly, with more attention paid to making work possible than to making things secure. That’s understandable, of course. But it’s important, once work-from-home is up and running, to take steps to reduce cybersecurity risks. There are technologies and trainings that can help – but strategic action is required.
The unfortunate reality is that the coronavirus situation is a boon for cybercriminals. Nonprofits should reconsider their approaches to cybersecurity in light of these changes and the impact of COVID-19 on nonprofit cybersecurity.
Looking for cybersecurity guidance in the midst of uncertainty?
As cybercriminals look for ways to take advantage of the chaos caused by coronavirus, take care to educate your personnel against these threats. Staying vigilant is a key in reducing risk. And if you have questions or concerns about your level of cybersecurity preparedness, we can help.
At Community IT, we’ve found that many nonprofit organizations deal with more cybersecurity risks than they should have to after settling for low-cost IT support options they believe will provide them with the right value. The problem is that these options don’t understand or address important vulnerabilities.
As a result, cyber damages are all too common.
Our process is different. Our techs are nonprofit cybersecurity experts. We constantly research and evaluate new technology solutions to ensure that you get cutting-edge solutions that are tailored to keep your organization secure. And we ensure you get the highest value possible by bringing 25 years of expertise in exclusively serving nonprofits to bear in your environment.
To increase cybersecurity preparedness in the midst of the current uncertainty, get in touch with us today.
