Transcript below
View Video
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Spotify, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Encryption 101 for Nonprofits
Encryption is rapidly becoming the preferred method for securing information. In this webinar, Community IT Innovators’ CTO Matt Eshleman will cover the basics of encryption, how it is currently used in popular systems such as the web and email, and simple tools for using encryption to secure your devices and information.
Encryption isn’t something only “techies” need to worry about. As data vulnerabilities are exploited and the cost of hacking your password and credit card becomes more and more affordable to criminals, your email and devices are already becoming the next targets. Join us to learn the basics of how encryption works, how you can use it, and how to manage IT for security at all levels of your organization.
And if you’ve ever forgotten your password, this webinar will help you learn how to guard your communications while securely maintaining safeguards to allow access in the event of a human brain fail.
This webinar is appropriate for nonprofit executives, managers and nonprofit IT personnel – and as with all our webinars, it is appropriate for a varied audience.
Presenter:
As the Chief Technology Officer at Community IT, Matthew Eshleman is responsible for shaping Community IT’s strategy in assessing and recommending technology solutions to clients. With a deep background in network infrastructure technology he fundamentally understands how technology works and interoperates both in the office and in the cloud.
Matt joined Community IT as an intern in the summer of 2000 and after finishing his dual degrees in Computer Science and Computer Information Systems at Eastern Mennonite University he rejoined Community IT as a network administrator in January of 2001. Matt has steadily progressed up at Community IT and while working full time received his MBA from the Carey School of Business at Johns Hopkins University.
Matt is a frequent speaker at NTEN events and has presented at the Inside NGO conference and Non-Profit Risk Management Summit. He lives in Baltimore MD with his wife, daughter and son.
Matt enjoys presenting webinars on cybersecurity training for nonprofits. You can access more videos of his past cybersecurity presentations here.
Matt provides a free initial consult if you have cybersecurity questions for your organization. Click Here to learn more and schedule.
Transcript
Steve Longenecker: Okay, let’s get started. Welcome to the June Community IT Innovators Webinar. Thank you for joining us for today’s webinar, “Encryption 101 for Nonprofits.”
My name is Steve Longenecker. You’re used to hearing Johan Hammerstrom, President and CEO introduce this. I’m the director of IT Consulting of Community IT and I’m the guest moderator for today’s webinar. Before we begin, I would like to tell you a little bit about our company. Community IT is a 100% employee owned company. Our team of almost 40 staff is dedicated to helping nonprofit organizations advance their missions through the effective use of technology. We are technology experts and we have been consistently named a top 200, North American managed service provider by MSP mentor. And now it is my pleasure to introduce today’s presenter, Matt Eshleman, Community IT’s Chief Technology Officer. Matt?
Matthew Eshleman: Thanks Steve. Thanks for being able to moderate today. Steve mentioned my name is Matthew Eshleman and I’m the Chief Technology Officer here at Community IT. I’ve been with the company full time for actually a little over 16 years. And during my time at Community IT played nearly every technical role from desktop support to managing and directing our strategy, right to our clients’ IT Infrastructure Solutions and the tools that we use to manage over 4300 endpoints that are nearly 120 nonprofit clients. Over the past couple years, our work has really included a growing focus on IT security, particularly as it relates to nonprofits and their staff.
Today, we are going to cover a range of topics related to encryption as part of this webinar.
- We’re going to start off really with an overview of encryption and
- then spend the majority of our time reviewing some use cases for implementing encryption and
- then wrap up our time with Q&A at the end.
As always, this session is going to be recorded and will be sent out to all the registrants along with being posted to our YouTube channel, the slides will also be made available. Also, just putting a plug in for our YouTube channel, where past webinars that we have given are also available.
So let’s go ahead and jump in. If you have any questions you can go ahead and use the chat feature to chat them in. Steve will be moderating that portion and may respond to you or go ahead and just interject if we’ve got a relevant topic to discuss. So let’s go ahead and jump right in to talking about what is Encryption?
What is Encryption?
So encryption, fundamentally, is the Wikipedia definition here – “the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. So encryption itself does not prevent interference, but denies the intelligible content to it would-be interceptor.” Encryption is that process of encoding that message. So it’s helpful to look at the history of encryption.
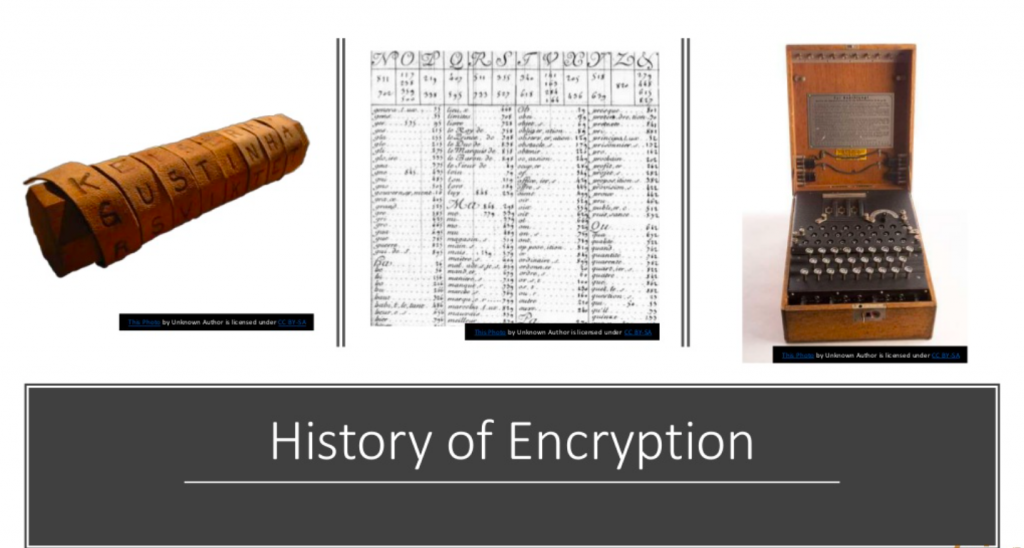
Here are three examples from the earliest days of encryption. The first image on the left is called a Scytale, I like to say that it rhymes with Italy. And this thing comes up in basically every encryption overview webinar. What this is, it’s basically a tool that’s used as a form of transposition cipher. So basically, there’s a baton or a cylinder in the middle. And then what would happen is that there would be a strip of parchment or leather wound around it on which is written a message. You can see the letters that are wound around it. So in order for this type of encryption to be meaningful, both sides have to have the same size cylinder.
You wrap the message around the cylinder, you write it out, you unravel it, you give it to the messenger. The messenger can’t read it because they’re not sure how these numbers relate or letters relate to each other. The recipient has the same sized cylinder as the sender, they wrap the leather around it and are able to read the message. So again, this is an early example of encryption. It’s a transposition method. From a physical space location, the messages are obfuscated.
That gets evolved here. In the middle we have what’s called the Great cipher. This was developed in 1626 by Antoine Rossignol and it wasn’t cracked until almost 1893, so almost 1900 about 250-some years and this code was basically a set of 587 numbers that stood for syllables. This is French.
And so E is the most commonly used letter in French. The cipher allocated the most code numbers to writing this val. So one nomenclature, one iteration of this code, 131 out of 711 code numbers stood for E.
So basically, you’d have this whole long series of numbers and the key that would correspond to a set of syllables. So that was in place for about 250 years.
The last example here on the right is the German Enigma machine. It was not a commercial success. But it was taken over in the early 1900s; it was taken over and improved. And this is basically the cryptographic workhorse of Nazi Germany and was broken by a Polish mathematician. Additional work was done during the war by Alan Turing and Gordon Welchman, others at Bletchley Park in England. And I think there was a movie about Alan Turing featuring this cracking in pretty gripping detail. So you know, encryption, it can be a pretty interesting and sexy topic.
These are some historical examples of encryption. We’ll move into some contemporary examples of encryption as we move along here.
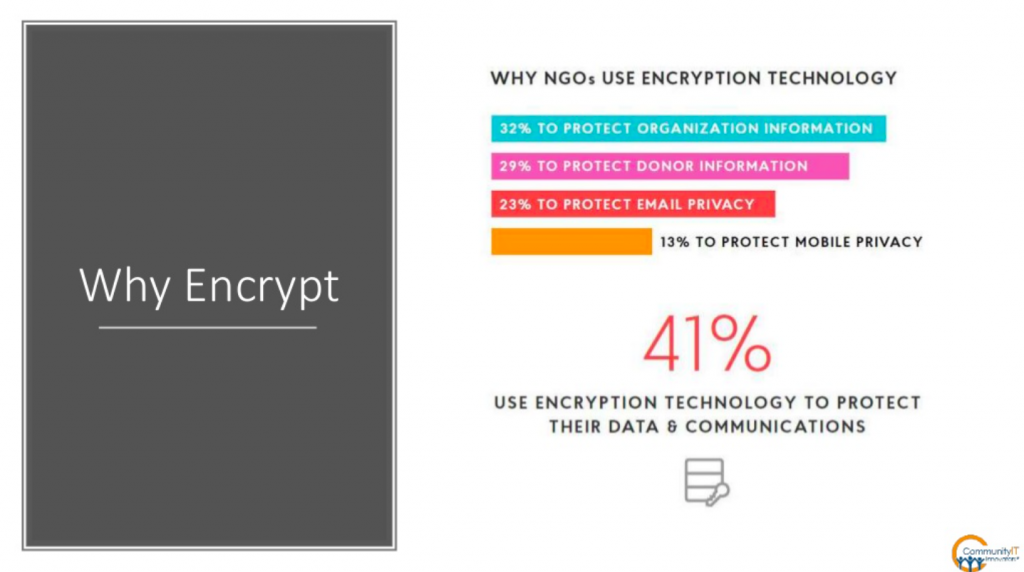
(7:24) Why in the world would anybody encrypt a message? This result is from the 2018 Global NGO report, which is a survey of NGOs and as represented here
- the predominant reason is to protect organizational information followed by
- protecting donor information and then
- e-mail and
- mobile.
I think that makes sense and it shows where organizations are at when it comes to securing their organizational data and assets.
About 41% are using encryption technology to protect their data. I would actually venture to guess that the number is probably higher just by some incidental use of encryption, the things that protect us and we aren’t even really thinking about it. Again, about 41% are explicitly using encryption as a way to protect their data and communications.
From our perspective, there are three primary reasons that would lead an organization to implement encryption and it’s very facet.
- The first one would be compliance where you have a requirement to take that action that could be related to your external factors such as HIPAA compliance or PCI compliance.
Both of those standards have pretty clear statements that sensitive data or PCI data or credit card information must be encrypted if it’s stored at rest, if it’s stored in transit. So you may have an explicit compliance requirement to implement encryption.
- It may come from more of a risk management perspective.
I think that’s what we saw a lot from the NGO survey. Maybe there’s not a compliant requirement to encrypt your donor information, but it’s really important that you make sure that that data is really secure. And so even though maybe there’s not a compliance requirement to encrypt it, we as an organization really value our information and just want to make sure that it isn’t easily made public if a laptop is lost or stolen or if a database is hacked or something.
It could come from a risk management perspective in terms of an organization’s perspective.
For us, as a service provider,
- we come at it from the perspective of good security practice. We don’t necessarily know an organization’s risk or compliance requirements, initially. But, we see implementing encryption as an overall best practice that more and more organizations are taking advantage of.
It’s actually easier and easier to actually implement encryption. Three dimensions to this, you may be required to implement encryption, you may do it because it’s a good idea and you value security or you may just do it as part of a good security framework that you’re working through.
And we view security and use this framework in a number of our other webinars in terms of how we view security.
Security is made up of many different elements.
One that’s rooted in IT policy so that forms the foundation of how we make decisions, what security decisions we’re going to make.
Building on that is security training and awareness.
Then there’s little blocks of good passwords and antivirus and backups and patching,
then layered on top of that is encryption.
So encryption is an additive security practice. It’s layered on top of security approaches that are already in place at your organization.
From a structural perspective, encryption covers a wide domain and is often sitting on top of and an additive set of security measures.
Okay, so we’ve seen some historical examples of encryption. So what does a contemporary example of encryption look like?
So here, I’ve got the text, “Protect your data with encryption,” and if I transform that into PGP, PGP is a type of encryption, you can see that the text is really rendered illegible. So if I zoom in on that, yeah, it’s just a bunch of gobbledygook. That is what somebody would see if they intercepted a message.
If they hacked onto my computer and found this encrypted file, they would just have this information that basically says, “Oh, this is completely illegible and it doesn’t serve any value to the person who intercepts the message.” So that’s an example of a PGP encrypted message and that would be something that would apply to data at rest.
Unfortunately, for most of us, our experience with encryption is around Ransomware.
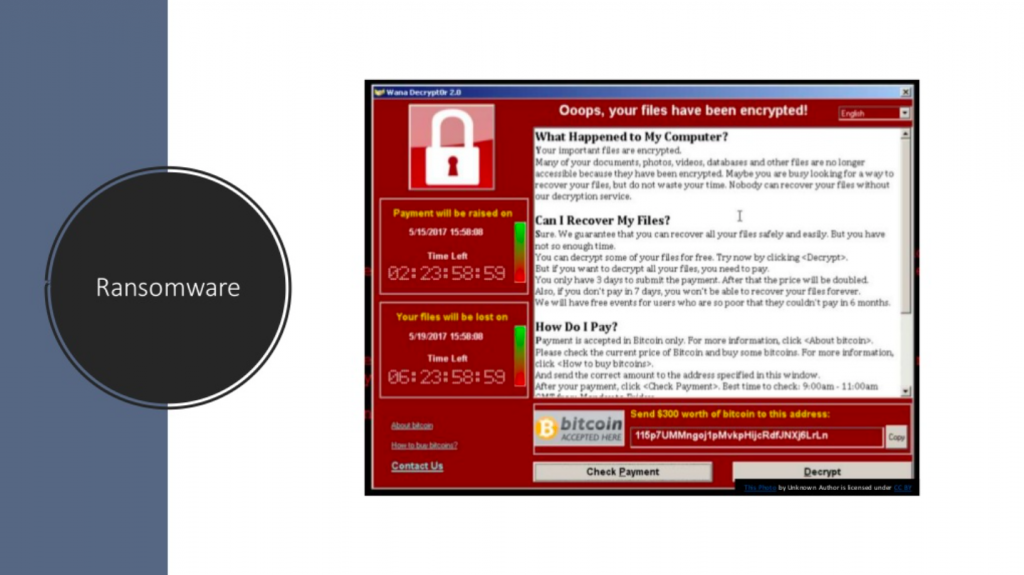
Here, we can see that virus writers basically figured out that they can extract value, not by stealing your data necessarily, but by rendering it unusable.
In the example of Ransomware, files are encrypted by the virus writer’s key and only they can unlock your files and restore the data. The data is encrypted; you can’t get to it. And only the person who encrypted the file can potentially decrypt it. However, in our experience, you’re better off not paying ransom and restoring from backup. But I think that’s another slide. I think it is a good example for how we can think about or understand the value of encryption.
(13:11) So encryption – there’s a whole glossary of terms that we can get into. And these are some really helpful ones.
Glossary of Terms
There are four top level concepts and these intersect as we think about where we are encrypting this data and how we interact with certain service providers.
- Encrypted at rest. That would be data being stored on a server is encrypted. If you are saving files in OneDrive or Box or Google Drive, or whatever, the data is being stored on the server in an encrypted format. So that means if somebody hacks Google and takes the data, all those files are going to be encrypted. So that data is encrypted at rest and if it’s stolen or taken, that data has been encrypted.
- There’s information that is encrypted in transit. That is data encrypted between the user and the server. I think the most common example would be an SSL website. We’ll talk a little bit about TLS, secure email. As data is moving from one place to another, that information is encrypted. This also may be an area where depending on the hosting company, would have access to the data. So again, a service provider may be able to decrypt that information depending on the environment that you’re working in.
- There’s this concept of end to end encryption. This is typically a communication encryption where only participating parties have the key. You need to be clear in terms of the service and where your concerns lie in the type of encryption that you’re using and how these methods are being implemented. End to end encryption typically is used in the context of communication software like Signal or Keybase where the message between you and the recipient is going to be completely encrypted from end to end and nobody else can see or decrypt that information.
- And then finally, is this concept of zero knowledge encryption. So, data is encrypted at all times and not even the platform or the hosting company that holds your data can access it. You can put anything you want on there and the hosting company cannot see it. An example is Microsoft or Google or Box, while the data is encrypted at rest, those service providers are actually providing the encryption keys to decrypt data to reveal it to you and to backup and do all of that stuff. So the encryption key management is actually happening by the service provider. In the example of zero knowledge that would be vendors like SpiderOak or sync.com, or Charizard, where they’re just providing you a solution and you bring your own encryption keys and all the encryption is handled by keys that you, as a consumer or business organization, maintain. It’s great from a security perspective because it ensures the integrity of your data. It’s not going to be visible.
For example, maybe you’re concerned about perhaps searches or government searches, requests and things of that nature. The downside is if you forget or lose your encryption key that data is gone. There are some trade-offs there, as it relates to managing the encryption key. So that’s some of the terminology and overview.
Technology Usage and Effectiveness
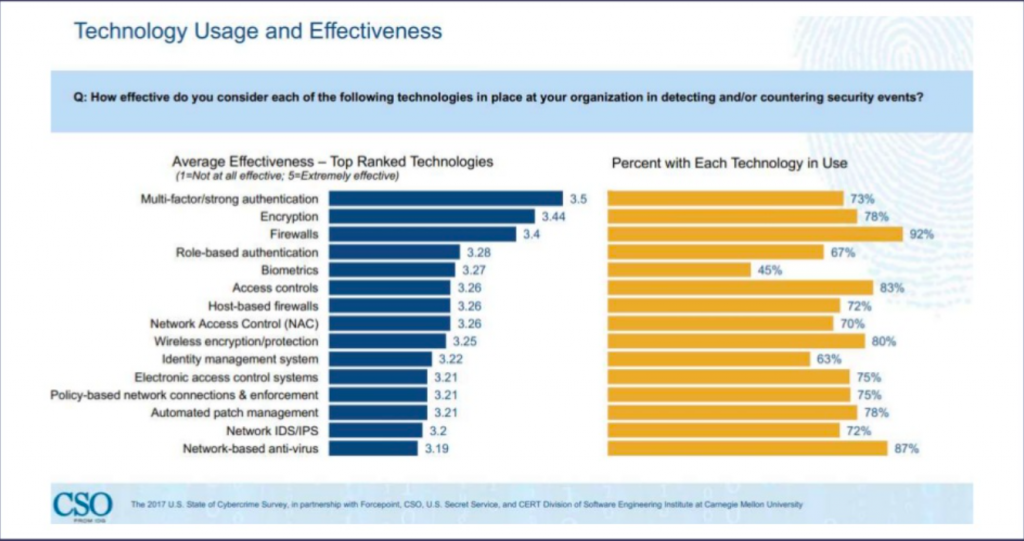
We’ll go ahead and talk a little bit about the effectiveness of it from a security perspective This was a survey of about 510 executives of US businesses of what’s going on in the world of cybersecurity.
You see, encryption here is ranked as the second most effective tool that we have as new security professionals in our arsenal of keeping information secure.
Multi factor authentication is the number one thing and that’s certainly something that we would strongly advocate for is turning on multi factor authentication. But after multi factor authentication, encryption is a great way to ensure that your information is handled securely. We can see from the organization’s perspective, MFA and encryption are implemented at a pretty high rate. This shows the difference between enterprise and nonprofits.
There’s a mandate often in forprofit and publicly traded companies to implement encryption in such a way that is not in the nonprofit sector. That’s an area for us to do a little bit of catch up on.
This is just to highlight the differences in the layers of effectiveness of encryption as a solution.
Let’s talk a little bit about what to encrypt.
So we’ve had a bit of background on encryption from history and contemporary examples and some different terms. Now, we can spend some time, for different scenarios, what to encrypt.
You chat in to Steve and we’ll take some Q&A questions as we go along or at the end, as well.
There’s four top level domains that I’ve included here that we think about encrypting.
- We think about chat programs,
- We think about full disk encryption for our devices.
- And then also we think about encryption within applications so primarily databases.
So that’s the overview. So let’s talk about email. And I’ll just put in a plug. I’ve actually gone into a lot more detail on the email encryption piece on a recent blog or interview that was just published at IdealWare. You can go check that out at idealware.org/email_encryption. I’ll see if I can check that link out. If you want to do a little bit more reading on email encryption that is going to be available there.
We’ll see if Steve can chat that out to everybody. And so we’ll talk a little bit about email encryption.
The first one here is TLS. TLS stands for transport layer security. This is coming back to that concept of saying, you’re probably actually using encryption in some form. You haven’t even realized it. This actually is an example of email encryption that doesn’t rely on you doing anything as the sender. It’s entirely seamless and transparent. Most large email providers, including Gmail and Office 365 have implemented Transport Layer Security encryption for messages in transit.
From a technical perspective, this is actually an evolution of SSL. You can think of this as SSL for email. You can look it up on Wikipedia; there’s a much more detailed explanation of the method if you want to geek out there a little bit.
Enabling TLS or using a TLS compliant email service ensures that no one can read your email as it’s in transit between another TLS compliant provider.
We used to use the analogy, and I always thought it was a great one, of basically thinking of email as a postcard. You put your return address, where you’re going to send it to, and the contents of your message. You drop it in the mailbox. The post office is going to make sure it gets delivered, but along the way somebody can pretty easily read it.
And then there was this idea of secure email or encrypted emails. You put a message in an envelope. Now, you know who it was from and who it’s to, but you don’t actually know the contents of the message.
So TLS is actually more analogous to the letter in an envelope. So, the contents of the message are actually secure and cannot be read by somebody as it goes from point A to point B. In this example here, you can see that I’ve received a message that was protected by TLS v1.2. You see it was received. And then there’s the TLS version 1.2 cipher. And that’s sending a message from Gmail to Office 365. That is a handoff that is handled securely between those two providers, because they have both implemented TLS.
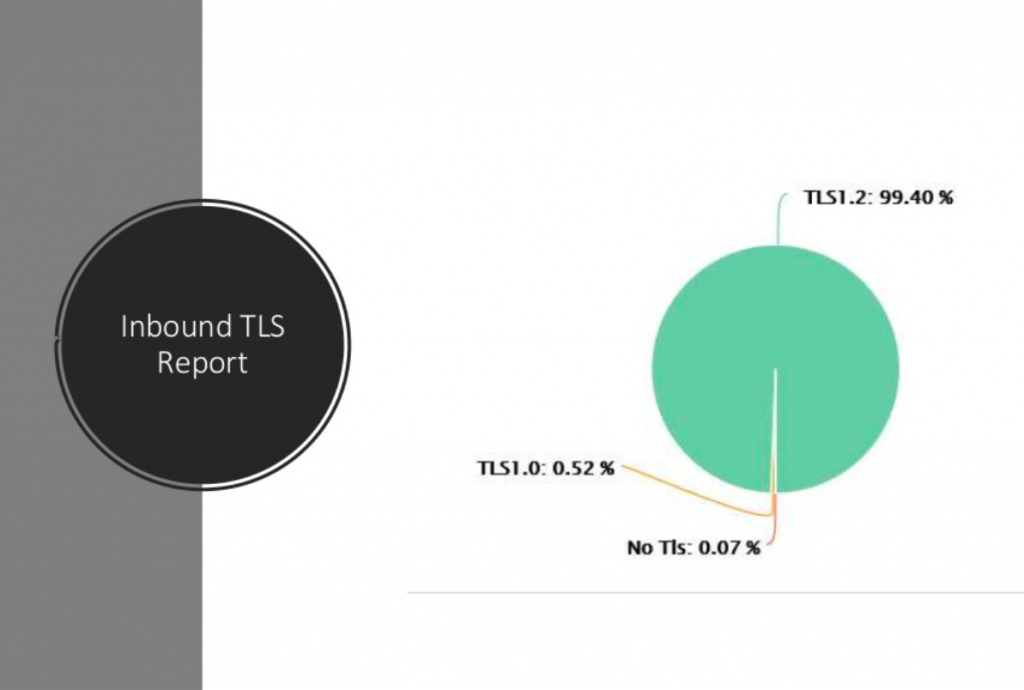
And, as an example, this is the inbound TLS report for Community IT. (22:29)
This is our office 365 TLS report. You can see that 99% of our messages were delivered with inbound TLS v1.2 which is the most current version. We did have a very small, small percentage of messages that were on TLS 1.0 which is going to be deprecated and then there’s probably a message or two that was delivered without TLS. In general, we’re seeing that most messages are being delivered with TLS. You can go into the Office 365 Security Center to check out or verify that.
I think we’re a little bit high. I was looking at another client and they were in the low 80s, which seems pretty good overall. We’re also starting to see some cases where you may have need to configure a specific connector to require TLS between providers.
Typically for organizations that are in the HIPAA space or compliance space, may need to require mandatory TLS connections to your healthcare provider or broker or something like that.
TLS is something that happens in the background, it’s great. And we’re starting to see moves for mandatory TLS compliance come in, specifically in the HIPAA case.
Moving on from the transport layer to email encryption that’s provided by the service provider.
This is something where you, as the end user, have to have to do something. You have to have something configured; you have to have something set up.
Moving up the stack in Office 365 with the addition of the Azure AD Premium P1 license, which is if you have E3 or EM plus SE3 gives you this ability, if you just have the regular Office small bit or the Office 365 business premium, it doesn’t have this feature. But it will turn on email encryption within Office 365, meaning that you can send an encrypted message to a recipient.
So the experience is that you would create a message. We typically would put a tag in the subject line, (encrypt) or secure. Then Office 365 would take that message, encrypt it, and then the recipient, instead of getting the whole email would actually just get an email with a link or an attachment saying “You’ve received a secure or encrypted message, please go follow this link to read the message.”
And then they would click on the link and get either a one time password or login with their Microsoft or Office 365 account and then be able to view that message in the window.
So this is helpful if you want to send somebody some secure or sensitive information and you don’t necessarily want it landing in their inbox and then just being available on their desktop. We often use it for sending passwords or asking for sensitive information. You can reply within the browser. You’re ensured that it’s only the recipient who is going to be able to get to it.
Office 365 includes this as an add-on feature. Google also has the same thing.
So if you’re in G Suite, they have an add-on called GAME, which I guess used to be Google Apps Message Encryption, but now there’s G Suite. It’s Google Apps Mail Encryption, but it’s actually built on a third party email encryption provider called Zix. If you have any online banking, you know Zix is a pretty popular tool for that.
We use Barracuda for spam filtering, and they have an encryption add on that’s rolled up into their solution. And Virtru is another popular tool for a third party encryption solution.
So all of these work in a similar way and that they provide an encryption framework. Encrypt the message and then send the recipient a note so that they log in to a walled garden to decrypt the message and read it and reply within there.
It’s pretty easy to encrypt and it’s a good next step to take, if you’re looking at providing a higher level of security or to address a specific compliance concern. This is the step that we most often see organizations take: we’re just going to implement this native encryption service in Office 365 or in Google, or whatever. And so you can do it through here.
It’s not quite as secure as what we’ll talk about next. It’s the client side because Microsoft has, in Office 365 example, both keys. Only the intended recipient is allowed to unlock the message. However, if the government subpoenaed it or something like that, you may be out of luck. But in general, it’s a good first step in terms of email security.
So the third topic in…
Steve Longenecker: If I can interrupt, obviously, we use this at Community IT. I shouldn’t say obviously, but we do use this at Community IT, the Office 365 version. For people who aren’t familiar with it at all, it is worth noting that the email is not encrypted on the sender’s side. So, if I copy and paste a password that a client needs into an email and then I send it with a tag (secure information), then the client gets that link. They log into the Office 365 world through a browser with a key that’s emailed to them and they can see the password. But meanwhile, in my Outlook, the password remains in plain text. I think that’s obvious, but at the same time, it helps people understand what’s happening and what’s not happening. Encryption happens after it leaves my Outlook and hits the Office 365 server.
Matthew Eshleman: Yeah, I think that’s a good thing to understand. As you’re thinking about what type of solution you would implement or what you are trying to protect against, it’s worth understanding in some detail where this data lives and how it’s encrypted.
The service provider side encryption is really great. If you want to control the messaging going outbound, you’re really protecting against the recipient handling it poorly. But what you’re not protecting against is yourself. So if Steve gets hacked, somebody has access to his email. That message is still going to be there in plain text.
With that understanding, then the final type of email encryption we’ll talk about is PGP.
So this is a form of encryption where it’s performed on the sender’s computer and it uses a public private key pair to encrypt the message. That was the example that I showed at the very beginning where the text itself in my Outbox or my Sent Items, looks like that, so it’s encrypted. If I just open up my mail, if my account is compromised, all the encrypted messages that I have are going to be unintelligible like that.
They require access to my private key, which has a separate password. In the PGP model, you’ve got the sender encrypting or locking the contents of a message with the intended recipient’s public key and also their own private keys. There’s some fancy math that like makes this all happen. But basically, it means that the PGP email requires both the sender and the receiver to have PGP configured so both players have to be on board with this system in order to receive encrypted messages.
It’s a little bit different than the other solutions, where you can receive an encrypted message from Office 365, without enrolling and generating a public key and doing all this other stuff. All you need to do is either have a Microsoft account already, or you can receive a one time passcode, which will allow you to log in.
You can see if someone has a PGP key already by looking it up at a key server. Universities maintain a lot of these. So, if you go to https://pgp.mit.edu, you can search for email addresses and it’ll return the public keys. If you are poking around over at the MIT’s PGP key server, you can see the public key address for me, so meshleman (at) communityit.com has a key ID that is 18ADAEAB. You can verify and you can be assured that whenever you send a PGP encrypted message, only I’m going to be able to decrypt that message. If you encrypt it and send it to me or you misspelled my name, like, it goes to the EL Eshleman, instead of the LE Eshleman, only the correct recipient is going to be able to decrypt that message.
Both the sender and the receiver have PGP configured and this is where a lot of the solutions that we’ve been talking about have really been focused on this centralized model control.
Office 365 is going to encrypt your messages or Google’s going to encrypt your messages. PGP is a decentralized web of trust model, which has been around for a long time and I think continues to be a good solution particularly in the security world. This web of trust model where there’s no central authority managing the encryption process. There’s a directory that says, hey, this is the public key for Matt, here’s a public key for other people. But the encryption is actually handled locally on your computer and doesn’t go beyond that. It doesn’t require anything beyond that.
Chat Programs
Moving beyond email, into chat programs.
Chat programs, or collaboration programs, we have been getting a lot of buzz lately. The big player, Slack is not on here because it doesn’t implement what would be called a true internal encryption. So while your connection to Slack might be over SSL, somebody sitting next to you in your office with a packet sniffer is not going to be able to read the contents of your messages, the actual contents of messages within Slack are not encrypted. So, other people other than the intended recipient of the message could go ahead and read those messages.
Solutions like Signal or Keybase down here are designed for security from the ground up. Those technologies have a very high degree of security and a robust implementation of encryption. Signal has implemented, I think it’s called Open Whisper, as the actual protocol. And so that protocol is also incorporated into the open source protocols included into WhatsApp, in terms of encryption to ensure that only the intended recipient can receive the message. That service provider can’t read your message. iMessage actually is also considered an encrypted communication platform and one where the service provider, Apple in this case, does not have the encryption keys to manage the server side decryption of the messages. So again, only the intended recipient can read those messages.
With a lot of these solutions, while the messages themselves are encrypted, if you lose your device or your device is compromised, your messages could be read. So, even if you’re using Signal, which is great from a security perspective, if you lose your device or you have weak device security and somebody gets it and is able to get on there, they can still read those messages. Some of these technologies have started to incorporate disappearing messages, so the entire communication or conversation thread disappears after a certain period of time. If somebody finds your phone or has access to your phone, they may not have access to all the secret messages you’ve sent back and forth to the recipients. They only may be seeing the last day or two or so. So that’s something to keep in mind.
Skype4Business here, internally the communication is encrypted. But once messages in this particular one as it applies to voice traffic, once it goes on the PSTN or the regular phone network, then it’s public. It can be sniffed and wiretapped and all that stuff. But if you’re making a Skype communication, that is an encrypted channel. But once you’re making a voice call to somebody on a regular phone, that actually is a nonencrypted communication at that point.
(Skype4Business was incorporated into Microsoft Teams)
(36:52) Steve Longenecker: Matt. Sorry, we had a question that I missed earlier. And I apologize for that. In terms of the Office 365 email encryption, I know that the regular E3 license allows that. Can you use an E1 license and then add the E3, the EM plus S to it?
Mathew Eshleman: Yes.
Steve Longenecker: Okay.
Matthew Eshleman: Yeah, you can add it. So yeah, so EM+S. We should probably do a webinar on this, because it’s a great product, a great platform, but there’s a lot of confusion about what it’s in. That’s actually one that there are overlapping skews in terms of what’s included.
E3 gives you Azure AD Premium P1. So that specific skew Azure AD Premium 1, is one of the key pieces of the EM+S bundle. So, yes, so you can do E1. So if you’ve got E1 for all your staff and you’re just getting email and SharePoint, OneDrive, and all that stuff, you’re licensing Office separately. And you really want to do email encryption. And also interested in security and maybe BitLocker, you could add on EM+S. It’s 250 a month, then you would have that feature available.
Steve Longenecker: Got it. So there’s two ways to get there. And the cheapest way, if that’s the only thing you want, is to stick with the E1 user license, which is free to nonprofits. Then add the EM+, the cheapest of the EM+S add ons. Are those $3 per?
Matthew Eshleman: I think it’s $2 and 50 cents.
Steve Longenecker: $2 and 50 cents per user, per month, for charities. But then, if you just have E3 licenses, the E3 user licenses, which are 4.50 per user, per month, that would include the encryption. Yeah, got it. Got it. Thank you for clarifying that.
Matthew Eshleman: It’s good. It takes a while to wade through all this stuff. And things keep shifting and changing, especially with renaming and rebranding, and that.
(see our roundup of Microsoft Teams Pricing for Nonprofits)
Disk Encryption
We’ve talked about email encryption, we talked about chat programs and collaboration tools. Now we can talk about your devices, specifically disk encryption or full disk encryption for your Windows or Mac computers.
Full disk encryption has been around for a long time, but I would say, you know, we’re just now starting to see the adoption of this technology really increased. Full disk encryption is available for both Windows and Mac environments.
In the Windows world, the terminology, it’s called BitLocker. It’s available for Windows Pro and up, I think if you get Home there is some encryption that’s available. It could be more of a headache than it’s worth. So, if you’re an organization, you should be getting Pro or Windows Enterprise. And you can manage it discreetly.
If you just have your computer, you can just turn on BitLocker, if you want. If you’re an organization, you’re managing any significant number of computers, 10 or 15 or more, you can manage the encryption keys. Microsoft provides an on premises management utility called MBAM. I think it’s Microsoft BitLocker Administration Manager. That’s a console that includes a web page for self service user resets or somebody forgets their encryption key. That’s something that you can deploy on premises. I don’t think there’s any additional cost for MBAM. It’s just a management capability. But that’ll give you, as an administrator, the ability to centrally manage things and have a key if somebody loses their key or forgets it, or whatever, you need to get back in. You can do that.
We’ve actually also started using Intune for policy enforcement. Intune is a component of that EM+S skew that we talked about just a minute ago and that’s actually pretty handy if you’re in the cloud a lot. You’re using Azure AD. You can enroll devices.
Windows 10 computers can get enrolled in Intune. And then you can actually set policies on them that require the users to enroll in BitLocker. BitLocker is handy because then they can actually save a recovery key into their Azure Active Directory account. So you have a backup, if you need it Then it has some compliance and reporting stuff that you can do. It’s pretty straightforward to implement.
We’ve been using that Intune for policy enforcement and key management, I think it’s pretty handy. There’s a couple of different ways to do encryption.For most modern computers, or if you bought a computer lately, oftentimes, you can select if you want a TPM. That stands for Trusted Platform Module, maybe it’s like 15 or 20 bucks. If you have a TPM chip on your computer, you can actually use that to do the encryption and not require a pin.
So if you don’t have a TPM, you can still do BitLocker. But what it means is that whenever the computer restarts or reboots, the user will have to type in a PIN code, which is four to 20 characters long to basically decrypt the computer so that they can then log in.
It’s separate, so organizations sometimes choose, Well, hey, we’re just going to make everybody type in a pin, even though we have these chips on some computers to provide a consistent approach. Maybe you don’t want to implement encryption, but you want to stay out of your users’ way, you can make sure that you’re getting TPM chips as part of the computer purchase. It just makes the encryption process pretty seamless, because you’re just leveraging that Trusted Platform Module to hold the encryption keys. So in scenarios like, if somebody takes that computer, or removes a hard drive, then they’re not able to decrypt the information because that TPM chip is embedded in the device and is required to decrypt it.
That is the Windows world, which I think works well, from essentially a managed perspective.
Macs also include full disk encryption called FileVault. They don’t have the same free out of the box management. If you’re an administrator, they don’t have an available Management Console. There are a couple of third party management utilities that allow you to manage encryption keys for Mac. We use one, the CASPER suite from Jamp to provide management and a whole bunch of other stuff for Macs. It’s a really robust platform. McAfee has their endpoint policy orchestrator that will do encryption key management for Macs. But I think Casper is a big player in the SMB space, and is a way to really provide you the ability to backup and recover and help out users whenever they inevitably forget their key to unlock their hard drive. The encryption, it works. If you forget your key, you’re out of luck. There’s no back door, you can’t decrypt it. You’re out of luck. So I think it’s a good decision to make, but you need to understand the ramifications and the backup plan so that you can recover information if indeed it is lost.
Applications
The final area I want to discuss was actually related to applications and specifically databases.
I think most organizations have moved their production and system of record to commercial software like Blackbaud’s Raiser’s Edge, or Salesforce, or whatever. (learn about platform selections from our webinar on Microsoft Dynamics and Salesforce.)
That would include some compliance solutions and the ability to have encrypted fields within the database. Pretty sure that some of the folks that are listening today may have custom processes, or even old custom databases that include PII information that’s in plain text or social security numbers or credit cards. Those systems that would have that information in plain text are pretty high risk. It’s worth understanding that risk, then you understand how we’re going to address it. SQL includes the ability to encrypt columns within databases.
So the technology is out there. But again, I think we need to have a good understanding of, where do we have that personally identifiable information or credit card information? And how are we addressing the security of that? Even if you have good systems and controls in place, that may even be circumvented. What we would see is maybe the data is encrypted within the database, but then somebody exports information to run a report or do something else. Now you’ve got personally identifiable information in plain text on a laptop that’s not encrypted.
So I think that represents the area of risk for organizations. If you’re doing healthcare, health services, you have an export of data from a secure system on your laptop, which is law, which is not encrypted, and you lose your laptop. That actually represents a reporting obligation: “We lost a laptop that had PII information on it, and we have to now notify all those people that we lost a laptop that had their information.” If your laptop is encrypted, it’s like a brick. You don’t have to go through that same process.
I’m not a lawyer. You need to talk to your legal counsel for clarification on your own organizational policies. But implementing encryption on the disk or email, or whatever, is a piece of maintaining your HIPAA or PCI compliance. Just call again to check and understand your legacy, your custom solutions to make sure that they’re handling the data in a way that’s appropriate and that you would expect.
(more on Cybersecurity Insurance here)
I think we’re wrapping up the content here. Steve, are there any more comments or questions or things to clarify?
Steve Longenecker: Nothing else has been chatted in, that I’m aware of. I apologize again if I missed something, but I don’t think I’ve seen anything. I know how to look, now.
I had a question as you were talking about the full disk encryption. We’re familiar with the crypto locker type viruses where they’re encrypting individual files. If I were an end user who just wanted to encrypt individual files, is that something that Windows does,? Is that just handled by a password? Is it as secure as full disk encryption only just at the file level?
I know that sometimes on the projects team, we’re doing a file server migration and we need to migrate files from one server to another, this ends up being a real roadblock to an efficient process. We run into a folder here and there that has half a dozen encrypted files in it. And we actually can’t move those files even though we have permissions to the files at the Windows level; we can’t actually access the contents to move it. I was just curious if there was anything to think about that or if it’s just not a good idea. It just ends up being an administrative nightmare, and it’s better to handle the full disk encryption where you have an Intune platform managing it all.
Matthew Eshleman: Yeah, BitLocker encrypts things at the volume level, so you’re encrypting the whole drive. In the BitLocker boot process, what happens is, your drive is encrypted whenever you boot up your computer and you enter in that pin code, or you have a TPM chip, it decrypts the volume and unlocks the drive. Then you can log in and use it and access it. If somebody tries to access your volume over the network and goes to browse, they will be prompted for that BitLocker key, which they won’t have.
BitLocker is a full disk encryption. It’s not necessarily encrypting each individual file, it’s encrypting the volume.
In Windows, there’s encrypted file systems. You can encrypt folders and that may be appropriate for organizations where you need to store information that has credit cards or social security numbers or something like that; you may have a legitimate business need to do that. That information then should be stored on an encrypted folder within the file server.
It does make it more challenging. But again, the data that you have has a liability associated with it and I think we’re becoming more aware of it. So, yes, there may need to be a process in place to encrypt data at rest that is sensitive and it may make it a little bit more complicated to do those migrations whenever that time comes.
Steve Longenecker: I think my question elicited a good follow up question from the same person who asked the first question; it’s a good one.
(50:17) Have we had any issues with BitLocker causing trouble with Windows Updates?
Matthew Eshleman: It’s a good question. And the answer is yes, kind of.
Whenever you do a reboot in the BitLocker world, especially if you’re just using PIN code validation, the computer reboot process will not complete unless the end user has entered in their PIN code. So it could be the reboot process. In the non BitLocker world, you reboot the computer overnight, it comes back to the end user in the morning. To get to their login prompt, they just log in, and they’re in.
In the BitLocker world, with Windows updates, updates are still going to get installed, it’s going to reboot, then whenever the end user comes in the next day, instead of the user login prompt, they’re gonna be at the BitLocker prompt which says, enter your PIN code. You enter the PIN code. That probably is going to take a while for the updates to finish processing and then they’re gonna log in.
Steve Longenecker: So on the order of 15 minutes waiting for an update to complete rather than it being all completely done. I mean, not that I’m not trying to minimize that, but that’s what we’re talking about. Yeah, that makes sense.
Matthew Eshleman: Now, the other thing that BitLocker does make more complex is updating system drivers and particularly the BIOS. At Community IT for our clients, we’re actually going through an automated process to update the BIOS in response to the meltdown inspector updates. So for computers that are encrypted, we have to basically take the step of temporarily disabling the key protectors so that the BIOS can update the system on reboot.
So if your drive is encrypted, the BIOS update actually will not complete. You actually have to suspend the disk encryption. So, you’re not actually decrypting the volume, you’re suspending the key protection of the volume.
I know it’s a nuance there. You can suspend that, do the BIOS update and then it’ll complete as normal the next go around. So it does, again, introduce some additional complexity. But there may be some complexity that you need to actually have.
Steve Longenecker: Great. Great. Well, thanks, everybody for attending today and for the questions.
I did want to highlight that next month, Johan will be leading our webinar that’s going to be titled Building an Effective IT Function. Share some of the lessons learned for us as a managed service company managing a service desk and handling lots of support tickets and requests throughout the day. So put that on your calendar and that will be promoted in our newsletter, as well.
So coming out of today, again, I just think it’s worth always like having a little bit of follow up. I would encourage everyone to review your organization’s requirements related to encryption.
Do you have HIPAA compliance?
Do you have PCI compliance?
Do you handle sensitive information? Where do you stand?
Is your organization really risk averse? Are you concerned about the sensitivity of your donor information being compromised?
And then just take some time to explore how you can use one of the technologies here.
We talked about a lot of different tools. We talked about BitLocker, FileVault for your disk encryption and we talked about email encryption. We talked about some secure communication or collaboration tools like Signal and Keybase.
Explore how you can use maybe one of the technologies that we talked about today.
Then hey, maybe you can, if you’re on Signal, go ahead and find a buddy and send them an encrypted message. You can find me on Signal, you can find me on Keybase. You can find my PGP ID and send me an encrypted message. And I’d be happy to help you as you explore this security frontier.
So great. Thanks, everybody. And if there’s no more questions, I think we can go ahead and wrap up for today.
All right, I think that’s it. Thanks, Matt. Thank you.
photo credit: anunez619 Rusted Mailboxes via photopin (license)

