Transcript below.
View Video
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Spotify, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
How to Secure Office 365
Do you have more staff working from home? Wondering about the cybersecurity of your Office 365 set up?
In this free video you will learn how to secure Office 365, troubleshoot the set up, how to communicate with your staff, essential security measures you expect them to take, and how to effectively share common hacking scenarios they can prevent.
In January 2020, Microsoft removed the 50 donated nonprofit licenses of their popular Enterprise Mobility and Security bundle known as EMS. Microsoft removed the 50 seat donation, but reduced the price for nonprofits from $2.50/license to $2.20/license per user per month.
You can read more updates on the changes to Microsoft 365 Security for Nonprofits here.
This webinar is appropriate for nonprofit executives, managers, accounting, development, and nonprofit IT personnel – and as with all our webinars, it is appropriate for a varied audience.
You may also be interested in downloading our completely revised 2021 Cybersecurity Readiness for Nonprofits Playbook, or seeing the webinar walk through of this Playbook.
You can find more resources on Cybersecurity for Nonprofits here.
Presenters:
President and CEO Johan Hammerstrom has always been interested in using technology as a force for good that can improve our world. In college, he pursued this interest through science, first studying Chemistry, Physics and Biology at Stanford University, graduating with Honors with a BS in Chemistry. He then studied Biophysics at Johns Hopkins University and received a Masters Degree.
The time spent in Baltimore convinced Johan that there were more pressing and immediate problems that technology could and should be used to address. He pursued a career in Information Technology, with the express goal of improving our communities and our world. He started at Community IT in 1999 as a Network Administrator. Since that time, Johan has been a Network Engineer, a Team Lead, the Director of Services, Vice President of Services, Chief Operating Officer, and beginning July 2015 President and CEO. Working directly with over 200 nonprofit organizations, to help them plan around and use technology to accomplish their missions, has been one of the most positive and rewarding experiences of his life.
As the Chief Technology Officer at Community IT, Matthew Eshleman is responsible for shaping Community IT’s strategy in assessing and recommending technology solutions to clients. With a deep background in network infrastructure technology he fundamentally understands how technology works and interoperates both in the office and in the cloud.
Matt joined Community IT as an intern in the summer of 2000 and after finishing his dual degrees in Computer Science and Computer Information Systems at Eastern Mennonite University he rejoined Community IT as a network administrator in January of 2001. Matt has steadily progressed up at Community IT and while working full time received his MBA from the Carey School of Business at Johns Hopkins University.
Matt is a frequent speaker at NTEN events and has presented at the Inside NGO conference and Non-Profit Risk Management Summit. He lives in Baltimore MD with his wife, daughter and son.
Transcript
Johan Hammerstrom: Hello, and welcome to the September 2018, Community IT Innovators webinar. Thank you for joining us for today’s webinar on Office 365 Security Best practices. My name is Johan Hammerstrom, and I’m the president and CEO of Community IT. I’m the moderator for this webinar series. And I’ll also be a co-presenter on today’s webinar.
Before we begin, we’d like to tell you a little bit more about our company. Community IT is a 100% employee owned company. And our team of nearly 40 staff is dedicated to helping nonprofit organizations advance their missions through the effective use of technology. We are technology experts. And we have been consistently named a top 200 North American managed services provider by MSP mentor. And it’s an honor we received since 2017.
Thank you for joining us today. And we’re looking forward to reviewing Office 365 Best Practices with you. I’ve introduced myself, I’d like to give my co-presenter a chance to introduce himself as well.
Matthew Eshleman: Great. Thanks, Johan. My name is Matt Eshleman. I’m the Chief Technology Officer at Community IT. Looking forward to talking about some security best practices in Office 365. And I’m actually looking forward to going to the Microsoft conference, which is going to be next week and learning, continue to learn more about this ever changing field.
Johan Hammerstrom: Great. So let’s take a look at the agenda for today’s webinar.
We’re going to start off by talking about the current threat landscape.
And I think one of the things that we’ve really noticed over the last 18 months or so is that the threats faced by organizations have really changed dramatically. And a lot of that has been a result of organizations moving to the cloud. But the nature of attacks and breaches is very different from just two years ago and the things that organizations need to do to protect themselves has also changed as a result of that. And so we’re going to talk a little bit about the current threat landscape and what the biggest threats are just statistically, for small and mid sized nonprofit organizations.
Today’s webinar is focused on Office 365.
And we are going to focus on the things that can be done in Office 365 to secure information and we’re going to talk a little bit about why that really is if you’re in Office 365 really the best place for you to focus, your security energy, your time and your priorities.
Specifically, because we’re talking about Office 365, we’re going to run through a lot of the features, the tools that Microsoft provides.
But we’re also going to talk about the licensing. And you really can’t talk about the tools that are available in Office 365 without also considering the licensing framework that Microsoft uses to provide those tools. It’s not simple, it’s not straightforward. But we’ve got some great resources that can explain how that all works that I think you’ll find really helpful.
From there, we have a security checklist that we want to walk through with you and this is a checklist that you can use at your organizations to start securing your information in Office 365 right away.
And then finally, we’re going to talk about some dashboards and some scorecards that Microsoft has provided that will help you to assess your own security readiness.
Changes in the Threat Landscape
All right. So without further ado, let’s talk a little bit about the changes that we’ve seen in the threat landscape. So what we’re seeing today is that these three types of information are the most targeted.
- So e-mail, and we’ve got some stats that we’re going to show you in a second. But e-mail, logins and files are the information that right now hackers are going after more than anything else. And this is why Office 365 has become such a big target. Because most organizations that have Office 365 are taking advantage of Exchange Online.
- They’re using some form of credential and login to Office 365, generally Azure AD, to access their information.
- And increasingly organizations are storing files in OneDrive for Business in SharePoint.
And so organizations are being targeted in these three areas. And so Office 365 itself has become a major target of hackers. It also has something to do with the fact that Microsoft has such a big market share. So it’s a huge surface area. And so hackers, instead of going after a smaller percentage of information that might be in third party solutions like Dropbox, if they just focus their efforts on Office 365, there’s just a huge amount of users and customers that they can go after.
So specifically, these are some current statistics that explain why attacks are so successful and there’s a whole another series of slides that we presented in a previous webinar that sort of talked about the mindset of hackers. And in general, most hackers are small time criminals, you may be in an organization that has enemies that are targeting you.
But in general, most of the attacks that occur on the internet in the cloud on Office 365, are the result of small scale criminal enterprise. And the reason they do it is because it’s successful and there’s a financial payoff for launching a successful attack.
Why are attacks so successful?
Well, 30% of users open e-mail from attackers that seems like a really high number. But that’s what the industry is noting right now. And so that could mean anything from a phishing attack, to one of the fake wire transfer attacks that I think we’re all familiar with, but 30% of those attacks are successful in the sense that the e-mails are opened.
In 10% of those attacks, they result in a link being clicked on or an attachment being opened. And, yeah, Matt, go ahead.
Matthew Eshleman: Yeah, I was going to say, this is the research for Microsoft. And I think our practical experience also bears this out, as we do security awareness training with our clients or we’re seeing these numbers as well kind of anywhere from 5%, if an organization has very attentive staff, I think on up into the 30 and even 40%, of people falling for a potentially malicious links, so I think the numbers are surprisingly high and again, it kind of points out why these attacks are so successful.
In addition I think the people clicking on links that they shouldn’t have, the research also shows that the vast majority of passwords themselves, 63% using text are either weak, they’re using the defaults or they’re stolen and other breaches. And this points to an issue of password reuse, that we really want to focus on helping our users make good decisions and choosing strong passwords that aren’t used for every single site that they go on.
And then finally, in terms of why attacks are so successful, is that in general, 58% of users share information inadvertently, I mean, it could be including the wrong person on an e-mail, maybe that contains sensitive board information or maybe attaching the wrong document that contains private information instead of the cleaned up version.
So there’s a couple of different ways in terms of how information can leave an organization, that you can also contribute to how data can be compromised and somebody who shouldn’t have access to information gains access to information.
Johan: And these numbers really emphasize why these attacks are so lucrative. And why many incentives that exist for hackers to pursue these attacks, if only you can imagine the millions and millions of e-mail addresses that are out there on Office 365. And, 10% of a million is 100,000. And that’s a huge payout. If you’re getting people to commit wire transfer fraud or if you’re able to install malware on their machines, or gain their credentials and therefore access to their systems, so, it’s these numbers and my guess is that in your organization, you’re going to see at least these numbers. But if your organization hasn’t focused on security, you probably see numbers that are higher than this, at least that’s been our experience. So there’s a big need out there.
We’ve become aware of incidents at our clients, when something dramatic happens. So either there is an illegal wire transfer, a fraudulent wire transfer that gets made, or someone’s e-mail has been hacked and is used to send out thousands of embarrassing e-mails. Strange things start happening with their documents or their e-mail. Those are how we and our customers sort of become aware that their systems have been compromised.
“…on average, it only takes hackers four minutes from launching an attack to access in network. But it takes over 99 days for businesses to discover that they’ve been breached.”
But in reality, the system has probably been compromised long before we became aware of it. And the industry sort of standard or the industry research shows that on average, it only takes hackers four minutes from launching an attack to access in network. But it takes over 99 days for businesses to discover that they’ve been breached. So the flip side of the high incidence of attacks being successful is that people don’t realize that they’ve been hacked, until it’s too late. And so it’s really important to pursue preventive security measures in advance. Don’t wait until you get hacked, because you may not know that you’ve been hacked, you may be hacked now and not realize it.
Matt: Yeah, it often happens if we respond to a breach, we have a known user account that’s been compromised and doing kind of the breach remediation response. It’s not uncommon to find another account or other accounts that have also been compromised, but maybe the user hadn’t quite realized it yet. So, yes, yeah, for all of this, you know, prevention is key, because the remediation and the follow up can take a lot of time and be rather kind of painful.
Johan Hammerstrom: Yeah. So, enough of the scare tactics. I mean, you are all on this webinar, you’re listening to this webinar, because you recognize the importance of security and probably share the concerns that we have around vulnerabilities.
So the good news is that Microsoft is also very aware of these vulnerabilities and has built and deployed a large number of tools that can be used to help secure your Microsoft Office 365 tenant.
And so the rest of the webinar, we could go through, we could spend an hour talking about scary things that happen with hackers on the internet, but we really want to focus on what you can do to protect yourself.
So we’ve really focused a lot of our attention on these tools, as opposed to third party tools, although we also avail ourselves of a number of third party tools, and they’re important to use. But if you’re going to focus in one area, at least initially, we really think that 365 security tools are the place to start for a variety of reasons.
One, it’s very simple, chances are you have a lot of different information systems, either in Office 365, or already connected to Office 365. And as a result, there’s a tight integration between your existing deployment and the tools that Microsoft provides. And also, makes it easier to use those tools. Generally, and this is particularly true for nonprofit organizations, the tools that Microsoft provides you with are going to be a lot less expensive and security software, the whole solution space of security solutions remains quite a bit more expensive. And I won’t go into the reasons behind that. But in general, you’re going to be paying a premium for security solutions.
And my sense is that Microsoft’s pricing is not out of proportion to the solution, just even for businesses and then when you add in a lot of the discounts that they provide to nonprofit organizations, it becomes very affordable. So in general, it’s a very cost effective way to deploy good security solutions. And then Microsoft kind of famously, is really in tune with the business needs of its customers. And they continue to refine and revise these tools so that they really align with the business goals of the organization. So for all of those reasons, we really have a lot of confidence in Microsoft’s Office 365 security tools.
So the two main things and we’re going to get into a lot more, we’re going to get into the weeds here shortly and talk about a lot of the granular tools that Microsoft makes available, but they also sort of fall into these two main categories of security and
- one is safeguarding your data.
- And the other is monitoring your data.
We have some more statistics here. Of course, Verizon does this amazing security. And it’s basically a breach investigations report every year and they basically compile all the information that they collect, in investigating breaches both their own and for their customers, and they sort of highlight common features of breaches.
And what they found is that 81% of all hacking breaches use compromised credentials.
I think the popular opinion of hacking is what you see in the movies. Some genius hacker has a special program and kind of runs through. it does a brute force attack. And in some clever way, it sort of hacks into the system, when the reality is most hackers are using compromised credentials. Credentials that have been revealed in some way, that are well known. And they can use those existing credentials to hack into the database. What that means is, if you are securing your credentials and keeping them safe, then you’re protecting yourself from 81% of all of the hacking that happens.
So it’s really important that credentials be kept safe that you limit the widespread use of credentials, but you use multi factor authentication. And we had a webinar last year that went into more detail on multi factor authentication. Quick sort of review of what it is, it’s something you know and something you have. So the password is something you know. And the second factor is something you have. And in general, these days, it’s either a code that gets texted to you or a code that shows up on an app that you have on your smartphone. The value of multi factor is that if someone steals your username and password, if they don’t have your phone, they’re not going to be able to log into your account, because they need that code that only exists with the thing that you have. And in general, most security professionals agree that multi factor authentication is the way to prevent credential related hacking.
So we’ll talk more about how to implement that in Office 365.
And then finally making sure that non compliant devices can’t access your overall system. So there’s all these things you can do in Office 365 to safeguard and protect your data. But then there are also some great tools for monitoring data. So you can monitor who’s logging in, where they’re logging in from, looking for logins that are suspicious in nature and responding to those quickly. And there’s one other statistic here related to the credentials: 75% of all individuals use only three or four passwords across all of their accounts.
That is a huge problem. And the main reason for it is that once those passwords are in a system that gets hacked, they’re released, if you will, into the wild, and they show up on the dark web. And there’s basically huge, huge databases of known passwords all over the internet. And it doesn’t take long for hackers to run through those known combinations.
We’ve seen firsthand a number of cases where the Office 365 account was protected. And no one hacked it. But someone was using a username and password that they were also using for their personal Yahoo e-mail that they were also using for their Dropbox account that they were maybe using in third party forums. And as we know, Dropbox, Yahoo and third parties have all been hacked over the last five or six years. And all of those hacked credentials are now available. And so if you were using the same username and password for Dropbox that you’re using for Office 365, you should probably assume that someone has found a way to log into it.
So some of this boils down to training and this webinar, again, is focused on tools. And that is not meant to downplay the importance of training. So training is critical in all of this. But many of the tools that we’re going to talk about can help alleviate some of the challenges that occur right now with credentials.
So let’s talk about those tools and no discussion of Microsoft and Microsoft software would be complete without a similar discussion of Office 365 licensing.
Matthew Eshleman: Thanks, Johan. Yes. So we’re going to take a look here at kind of the laundry list of different features and talk about the associated license that goes along with it.
Johan Hammerstrom: And actually, before we get to that, I’m going to do a quick sort of, visual glossary of terms that hopefully clarifies how all these things fit together.
So a feature is some software that Microsoft makes available. So for this example, I’m going to use Professional Plus, and it’s here in a box, although I don’t think anyone goes out anymore and buys boxes of software, you download it from the internet. But let’s say Office Professional Plus is the office suite of software. And that’s a feature that you want to avail yourself of, you want to use Microsoft Office on the desktop.
In order to do that, you have to purchase a license for it. And Microsoft includes the license for Office Professional Plus, with the Office 365 subscription. So if you have Office 365 E3, that subscription includes a bundle of licenses, one of which is Office Professional Plus. If however, you have office 365 E1, your subscription does not include that license.
But to make matters more complicated, you can go out and buy that license a la carte. So if you have E3, it includes this license, if you have E1, it doesn’t, but you can still go out and buy the license separately.
So Matt’s going to go through a list of the different features and features are basically different software solutions that are available in Office 365.
And then we’ll talk about which bundles, what the licensing that’s needed to run that feature. And then which bundles include that licensing.
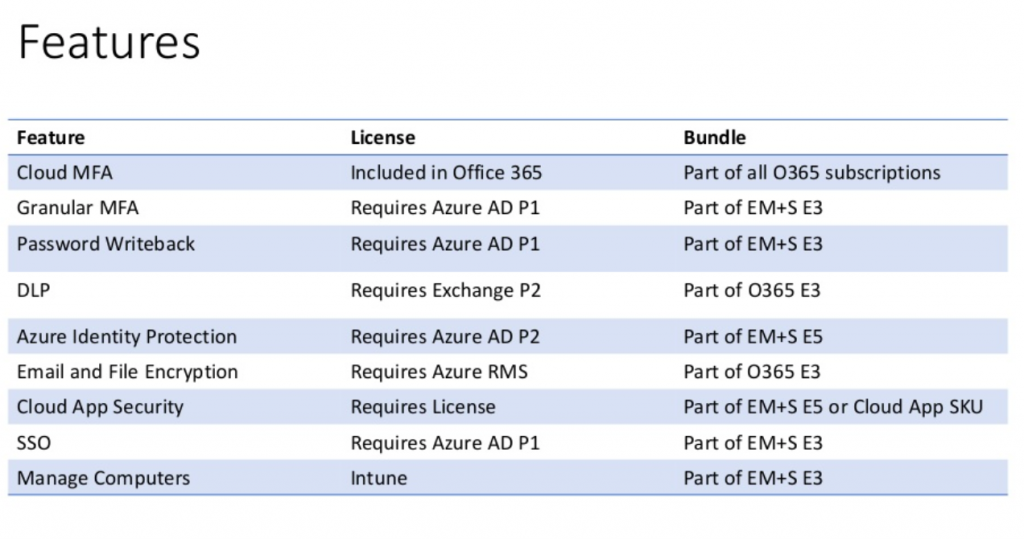
Matthew Eshleman: Great. All right. So this chart here represents a list of the features that we’re going to leverage in Office 365 to improve the default security settings. So for each feature, I’ve outlined the license that it requires and then what subscription bundle that it’s a part of. So Microsoft continues to evolve these solutions. And so while this list is accurate, as of September 2018, it certainly will change.
The other lesson that I’ve learned is that if there’s some new cool feature that you see, it’s likely going to require a new or a different license. So let’s just kind of talk through these features quickly. And I’ll provide an overview of them and some of the licensing.
So Cloud MFA, so that’s the ability from Microsoft’s perspective to log into Office 365, with multi factor authentication, that’s actually included in Office 365. It’s part of all Office 365 subscriptions. And so you could probably go ahead and turn that on now so that you can enable multi factor authentication for your office for that office suite.
What I’m terming granular multifactor authentication, where the ability to, for example, exempt having to use multi factor authentication when you’re in your office locations, where having some other controls, multifactor with single sign on, that requires Azure Active Directory P1, which is part of the EM+S E3 bundle.
If you want to be able to do password writeback. So for example, if you are using Azure AD Connect to connect your on-premises Active Directory to Azure Active Directory, you can actually turn on password writeback so people can do self service password resets through the cloud also requires Azure ADP1, part of the MSE3.
If you are interested in enabling some DLP or data loss prevention, so for example, you wanted to set a policy saying, Hey, we have HIPAA compliance, we want to make sure that we’re not sending any PII through our e-mail. That would require the use of a DLP feature. That’s part of exchange P2, which is part of that Office 365 E3 bundle. So again, it’s not available to E1.
If you are looking at some additional security around the identity, so turning on features like flagging logins from suspicious IPs or impossible travel times or some other advanced security features, that is a function of Azure ADP2, which is a part of the EMS E5 subscription.
If you wanted to turn on e-mail or file encryption, that requires Azure RMS or rights management service, that’s part of E3, Office 365 E3.
If you’re interested in Cloud App Security, that’s kind of a newer offering from Microsoft that looks at the applications that people are using on the web, some policies and user rights assignment or different features in terms of you know, how people are interacting with the systems, that requires a separate license. It’s a standalone license. But it’s also a part of the EMS E5 bundle.
If you wanted to enable single sign on so you could log in with your Office 365 credentials and then integrate other web applications like Salesforce or Dropbox or Box that requires Azure ADP1, which is part of EMS E3.
If you wanted to do some Computer Management, maybe enrolled devices and management set some different policies, force BitLocker, for example, that requires Intune and Intune is part of the EMS E3 bundle. So the short answer for all of this stuff is you need EMS E3 or E5 to enable a lot of these features.
Johan Hammerstrom: Yeah, and that’s also good news that a lot of these great features, the multi factor authentication, data loss prevention, which is a really cool feature that prevents credit card numbers and social security numbers from being inadvertently sent out through e-mail. Almost all of these features are essentially included in something you already have, or something that is very affordable to get, which is (dramatic reveal there), there we go. Yes, Yes, go ahead Matt.
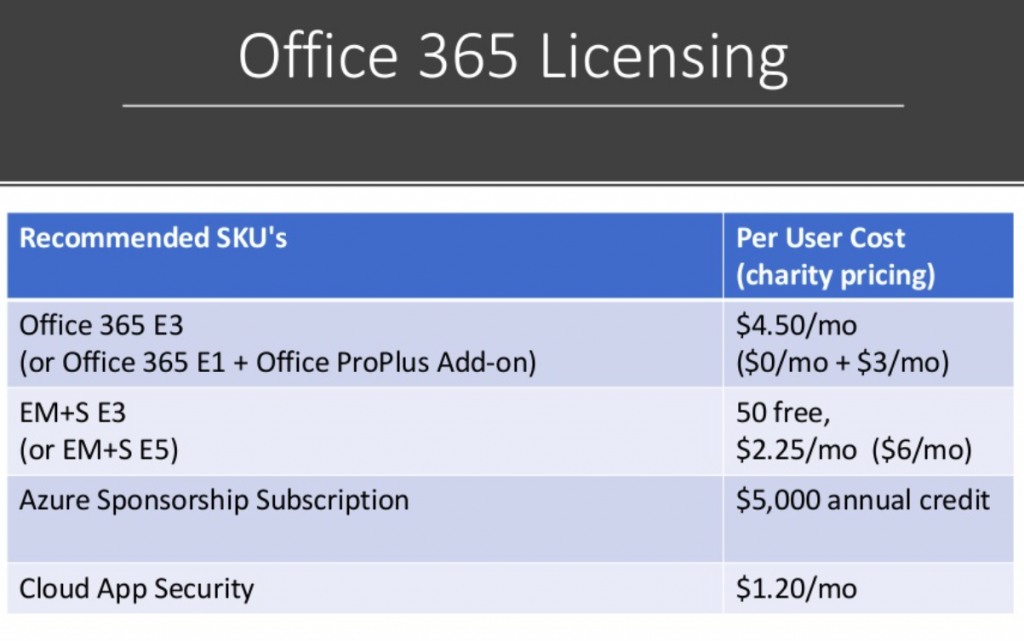
Matthew Eshleman: Yeah, our kind of recommended SKUs for getting signed up in Office 365. So ideally, you would have Office 365 E3. So the charity pricing for that is 4.50 a month per user. And that would include your Exchange Online, SharePoint, OneDrive, all the DLP features and your desktop office software for five devices. You would get EMS E3, which Microsoft has recently moved to provide 50 free licenses, which is fantastic. And then beyond that, it is 2.25 a month. The five subscription is kind of a relatively new addition for Microsoft and that is $6 a month per user account. We also as we’re kind of getting this stuff set up, encourage organizations to take advantage of the Azure Nonprofit Sponsorship Subscription, which provides an annual credit of $5,000 at Azure.
Now, a lot of the stuff we’re talking about is actually all kind of under the Office 365 umbrella, not the Azure umbrella. But you’ll still kind of log into Azure and access some reporting there. And it’s just kind of handy to have a subscription already in place so that you don’t have to set up a subscription and then apply for this later and then try to merge them. So it’s easy just to set it up at the very beginning. And then again, you could add in Cloud App Security again for either $1.25 a month or included as part of the EMS E5 license.
Johan Hammerstrom: So just a quick point of clarification, Matt, is Azure AD. So you see here, some of these require Azure AD. Is that part of Azure or is that- it looks like that’s part of EM+S?
Matthew Eshleman: Right. So I think that’s a good point of clarification. So there’s actually I think there’s four different tiers of Azure Active Directory. So any account that you have in Office 365, that account actually resides in Azure Active Directory. So if you just have Office 365, I think like the basic offering, that is what they call the free tier. Then if you have E3, that is what’s called the basic tier, which gives you some features or some capabilities.
So if you have E3, you could log in to Azure Active Directory right now and you would see a list of accounts. You wouldn’t be able to do much with it, but you would see the accounts there. Once you add on the Azure AD premium, that P1 license, so P1 is part of that EMS E3 bundle, then you can start getting some more security features and reporting. And then the P2 bundle, which is part of the EMS E5, then that kind of turns on even more security features. So you kind of go from like: Free, Basic, P1, P2.
Johan Hammerstrom: Mm-hmm. Thanks for that. Yeah.
Johan Hammerstrom: That could be a whole nother webinar.
Matthew Eshleman: “The finer points of Azure Active Directory?” Yes.
Johan Hammerstrom: Yes. And to be clear, Azure Sponsorship refers to kind of a different…?
Matthew Eshleman: See, I mean, as your sponsorship. Yeah, I mean, that covers things like if you were going to set up a virtual server, if you wanted to use some storage, if you’re going to build some web applications that would be the thing that would count against your Azure Sponsorship Subscription, from a cost perspective.
Johan Hammerstrom: Yeah. Yeah. Great, well, thank you for going into those details. So one option is to just go with Office 365 E3, and then get your EM+S E3, and the total cost there for 50 or less is 4.50 a month. Another option could be, you go with E1 and you get the Office ProPlus, for your desktop Office Suite, and EM+S and that’s going to be $3 a month. So you’re saving $1.50 per user per month.
There are some things that E3 provides, that would not be included in that scenario, aside from just the simplicity of getting the one, you know, the one SKU, and those include information protection, the data loss prevention that we talked about is not included in this bundle, this sort of homemade bundle.
E3 includes unlimited e-mail storage and you also have the option to put mailboxes on litigation hold, in case you have any sort of capstone staff that you need to retain their e-mail for a long time. So we tend to recommend just paying the extra dollar 50 per month, and going with E3. There’s some simplicity there in that approach and you also get these additional features.
Matthew Eshleman: Mm-hmm. Yeah. And then there’s a link here that describes all the plan options. And fundamentally, the difference between E1 and E3 is on the actual exchange package that’s included. So yeah, so there’s E3 straightforward, go for it.
Johan Hammerstrom: Alright, so let’s get into the practical. If you’re interested, if you’re like, this looks pretty affordable. I’m in Office 365. What can I do to get started securing my tenant, my implementation?
We’re going to talk about that in more detail. And kind of run through a couple checklists that we suggest you, you start to follow.
Security Checklist
Matthew Eshleman: Mm-hmm. Great. And as I go through these things, please feel free to chat in any questions, we’ll take them kind of as they come. And we hopefully will have a few minutes here at the end of the presentation as well.
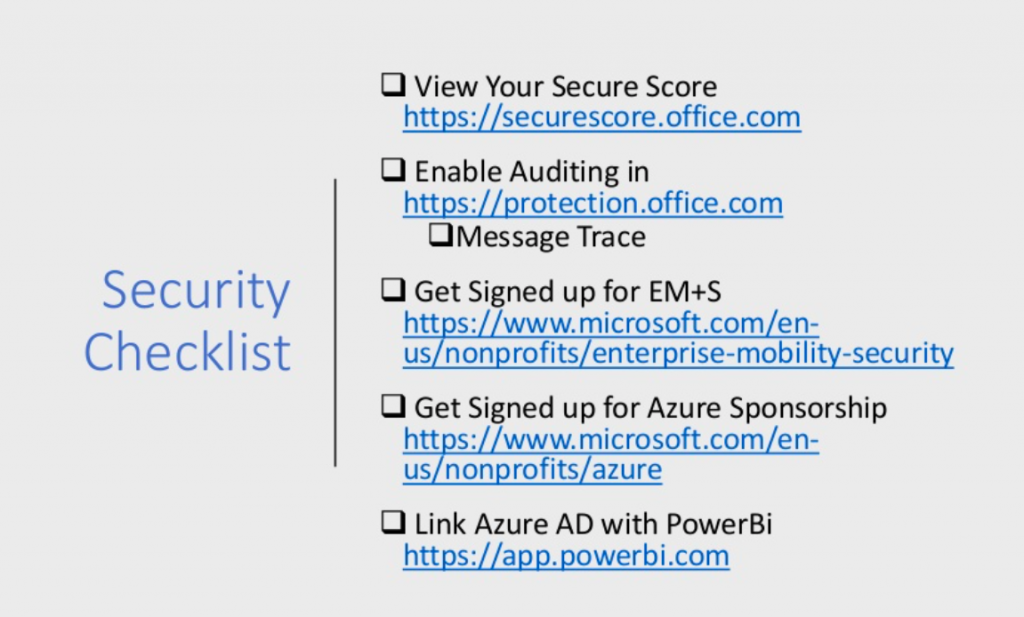
So in terms of security checklist, the very first place that I would recommend starting is with the Secure Score. So, Secure Score is an app that Office 365 has available that gives you kind of a baseline security score and our security checklist is rooted in this secure score.
So once you have taken a look at that secure score, the next step would be to go ahead and turn on auditing in the Office 365 Protection Center.
So Microsoft has a lot of content that it can collect, but it’s something that you have to enable, as part of their process.
Microsoft is really bringing a lot of reporting into the protection center, including that exchange message trace, again, if you ever needed to find out who messaged and didn’t get delivered, that’s actually being pulled into the security protection center. So now that you’ve looked at some of the built in features that you kind of already have, it’s time to add on some services.
So starting with that EM+S licensing. That pricing, as I mentioned, has now been updated to include 50 free licenses as a separate kind of standalone SKU. And additional licenses are 2.25 per user per month. And the link to that is actually at the end of the presentation, which has some additional details.
And then as I mentioned, the other service that we’d recommend signing up for is the Azure Sponsorship. And this is the annual $5,000 service credit for Azure Services. It is renewable. So it’s not a one time thing, but it is renewable. And as you said a lot of these security services are under this Office 365 umbrella, not Azure. However, it’s kind of convenient to have that Azure Subscription. Because as you look at some of the reporting and the integration with your on-prem directories, that’s kind of all on the Azure side.
And then finally, for some advanced insight, and that custom reporting, you can link your Azure Active Directory with Power Bi. So Power BI uses a free subscription. So there’s not actually an additional cost for that service. So I’m kind of talking about, check out the Secure Score, turn on some auditing, kind of get some of these other tools in place.
Johan Hammerstrom: Yeah, this is a great list. And this is a good place to start. And we’re going to go into some more detail on each of these to provide some more guidance on what to do.
All of our webinars slides are posted to our SlideShare account, and the links are posted on our website and also get sent out after the webinar.
So you can screenshot this, you can download the presentation from slideshare. And we’ll also include all of these web links in the show notes, as they say, on our SlideShare account. And just as an aside, the recording is also available on our YouTube channel. And that will get posted as well.
So let’s talk about Secure Score.
Matthew Eshleman: So Secure Score is an app that’s available to everyone. And it will provide you with a numeric score based on your currently configured environment. So it’ll also provide you with a detailed list of steps to implement. I really like Secure Score, because it actually shows your progress over time. And it also includes an evolving set of recommendations and settings based on the new features that Microsoft adds or new capabilities and then also the new threats that are identified. So this is kind of a good baseline and benchmarking tool. It’s available to help provide some guidance. There are lots of threads out there, what are the things that are important for me to do.
So here, we’ve got a screenshot of a Secure Score. And this is what it looks like. So for this organization, they have a score of 115, out of 360. I think most nonprofit clients we start working with, they’re kind of down in the 30s. That’s kind of where you start at.
And again, you can see here through the portal, it gives you a score for your Office 365 Environment, you can turn on and get some integration with desktop with Windows Defender, but then here we’ve identified some workflows and an updated risk assessment. So this organization has been identified as having a high risk of attack in the areas of account breach or privilege escalation, and also data exfiltration.
Johan Hammerstrom: That’s pretty scary. So yeah, this is a good tool that if you have Office 365, you have access to this tool. It’s pretty easy to set up and run. And it gives you a good starting point. Oftentimes you can run this prior to making these additional purchases. This can be a great tool for getting executive buy in, you turn this out. And if you are at around 30, you can say woof, we are at a pretty high risk of something happening. You can take it to your senior leadership and use it to get some support for some security initiatives.
All right. So once you have your secure score, you can move on to this checklist.

Matthew Eshleman: Yeah, so as I mentioned, the steps in our admin security checklist are kind of fundamentally rooted in that Secure Score roadmap. And these are, I think, what we found to be the most meaningful and relevant controls to implement. There’s a lot you can do in security, and it can kind of be daunting to start.
So these are the core steps that we would take whenever we’re setting up or securing an Office 365 tenant.
So the first is to
- have between two and five global admin. So these are the accounts that kind of have the keys to the castle, so to speak. So you want to have two have a backup account. And then the guidance is to not have more than five, just so you don’t have too many people with too much access to your system.
- The second step would be to turn on multi factor authentication for everyone. This is an easy step to do and is really the best tool that we have in our arsenal to really combat this kind of raft of credential theft, and account compromise. Once you get MFA turned on, then
- we would recommend really focusing on encouraging and working with staff to create complex passwords. So these would be passwords, that would be at least eight characters, with Office 365, no more than 16. But something that is unique, not used somewhere else, not their name with a one added on to it. But something that’s easy to remember, that’s lengthy and is not reused.
The carrot, I think with the complex password can be the fact that once you’ve turned on multifactor, once you’ve implemented good passwords, then there’s actually not a need to change them on a regular basis. So security research has shown that whenever people are forced to change their password on a 90-day basis, or whatever, regular basis, they actually don’t choose new good passwords, they kind of just choose bad passwords or kind of modify existing bad passwords. And so this can be a little bit of a carrot with your staff, whenever they’ve been made to get through this multi factor authentication enrollment can be like, Hey, we do the multi factor, pick a good password, I’m not going to ask you to change your password again. So again, a little bit of a carrot-and-stick approach there.
Johan Hammerstrom: Yeah, and I think that’s a good point, that’s a great example of how the conventional wisdom is kind of changing. And, the previous conventional wisdom was, you got to change your password every 90 days for it to be secure. And I think, the studies and the analysis of incidents show that if you have a password that’s unique to Office 365, and you have multi factor, you don’t really need to change it that often.
Your staff should be changing it now, if they haven’t ever changed it or haven’t changed it in a long time, but once they do that, then they’re in pretty good shape. Now, these things are all simple to turn on, from a technical administrative standpoint.
There’s a whole change management aspect to implementing these changes that is not necessarily trivial. And that’s where that executive buy-in is critical. And that’s where this Secure Score report can really be helpful.
Matthew Eshleman: Great.
So once we’ve got the account set up, now we can talk about doing some security on the platform. So, one would be to
- turn on that DLP in Office 365. We found this to be really valuable to turn on some of the predefined templates that Microsoft has provided to flag and identify documents that contain personally identifiable information or financial information, bank accounts, credit cards, that kind of thing. And so those controls can be audited first just to kind of see what’s going on and then they can actually be activated so that it will proactively block that information and provide feedback to staff, if they’re found to be sending information that they shouldn’t be.
Moving on from enabling some of the DLP in Office 365, would be
- configuring some additional tools around securing e-mail. So SPF may be a familiar acronym, as a way to kind of validate and help cut down on spoofing and spam. The new acronyms of DMARC and DKIM are also kind of related to tools and techniques that can help provide domain verification and validation. So that the message that you receive is sure to be from the sender that you think it is. We’re all receiving messages that are spoofed that appear to be coming from someone within the organization, but it’s not. And it can be very tricky to determine. So DMARC and DKIM are additional tools in this regard.
And our admin security checklist, we will also have started to look at requiring
- disk encryption as part of our best practice. If you’re an organization, for example, that has PCI or HIPAA compliance, you may already be doing this and I’ll just kind of make a plug for the Intune portion of that EMS license really makes managing and rolling computers and disk encryption fairly straightforward. I actually just have a new computer, I turned it on, I enrolled in Azure Active Directory and then my computer kind of automatically configured disk encryption, stored my recovery key in my Cloud account, and I’m off to the races. So that’s a really powerful tool that can really provide a lot of security, particularly if you’re dealing with that personally identifiable information. It can really help cut down on that reporting requirement if a laptop gets lost or stolen. If it’s encrypted, it makes it a lot easier to deal with those requests.
And then finally, there’s lots of great security tools, we
- turn on lots of auditing. We’ve done all this other stuff, but it’s important to actually spend some time and focus on actually reviewing the audit data. It’s part of my daily security practice to review the reports and information to make sure that our networks are secure. And the tools are pretty powerful to make that meaningful and relevant. So it’s not hours and hours, looking through logs, but the security tools are really surfacing the relevant information.
Johan Hammerstrom: Great. So these are the things that you can start doing right away or plan to do once you basically obtain your EM+S licensing as a nonprofit.
We have some questions coming in, Matt, but I think we’ll wait till the end, we’ll have a Q&A time at the end, because we still have a number of important slides to move through. So we have some questions on this slide. But I promise we’ll come back to those at the end.
Matthew Eshleman: Great.
“…there was something really strange going on, but subtle.”
Johan Hammerstrom: All right. So these are what the admins can do. What about the staff and end users?
Matthew Eshleman: Mm-hmm. Yeah. So again, lots of this content is geared towards your IT managers.
If you’re not an IT manager, but you’re interested in good security for yourself,
I think the best thing that you can do is pick a strong password, and one that’s unique for each service.
Again, we’ve seen a lot of breaches probably starting three or four months ago, corresponding to a number of well publicized data breaches that included lots of passwords. And so it seems like those are out there. So pick a strong password, pick a unique password, using a password manager tool, like LastPass can really help with that in terms of generating unique passwords. You don’t have to really think about it so if your solution A gets compromised, that doesn’t then immediately provide access to solution B.
The only thing, as I’ll say, is just be cautious when clicking, as we identified at the very beginning, 10% of people are clicking on malicious links from people they don’t know. And so good browsing habits, and just smart IT habits are really helpful in reducing the risk of the organization.
Report suspicious activity to your IT team. I mean, this is kind of the rule of “an ounce of prevention is worth a pound of cure” is particularly apt in this situation. We encourage all of our clients, if you have a suspicious e-mail, forward it to the help desk. We’ll take a look at it and help you make that determination. If it looks suspicious, we’ll just delete it. And if it’s not, and we think it’s okay, hey, you had to wait a few minutes to validate an e-mail. But that’s a lot better approach than clicking on something, then asking if it was malicious.
Fortunately, with the tools we have in auditing, if somebody does click on something, we’re able to go back and audit and report on kind of what happened, maybe when the account was compromised, what steps need to be taken as part of a response? You know, but again, if you’re an end user, an ounce prevention is worth a pound of cure, in this case.
Johan Hammerstrom: That last point, we can’t emphasize enough. I think, in many of the situations that we’ve dealt with, the organization became aware that they were hacked, because something just seemed funny to one of the staff and they reported on it. But you know, ultimately, hackers are sneaky and their goal is not to attract attention. But there are a lot of amateur hackers out there that are also clumsy. And so you combine the sneakiness with the clumsiness, and you end up with just things that don’t seem quite right.
So that’s where training is so valuable, because if you’re training your staff, they have their antenna up for unusual things. And that’s how we’ve detected or found a lot of breaches, not because there was something really obvious going on, but because there was something really strange going on, but subtle.
And the fact that it was detected early meant that it wasn’t going to become a bigger issue.
Matthew Eshleman: Mm-hmm.
Johan Hammerstrom: So let’s talk about multi factor authentication, because that really is kind of the number one thing, every security professional will basically tell you that if you have multi factor and encryption, you’re pretty much you know, preventing yourself from being hacked. And so let’s talk about how multi factor works in Office 365.
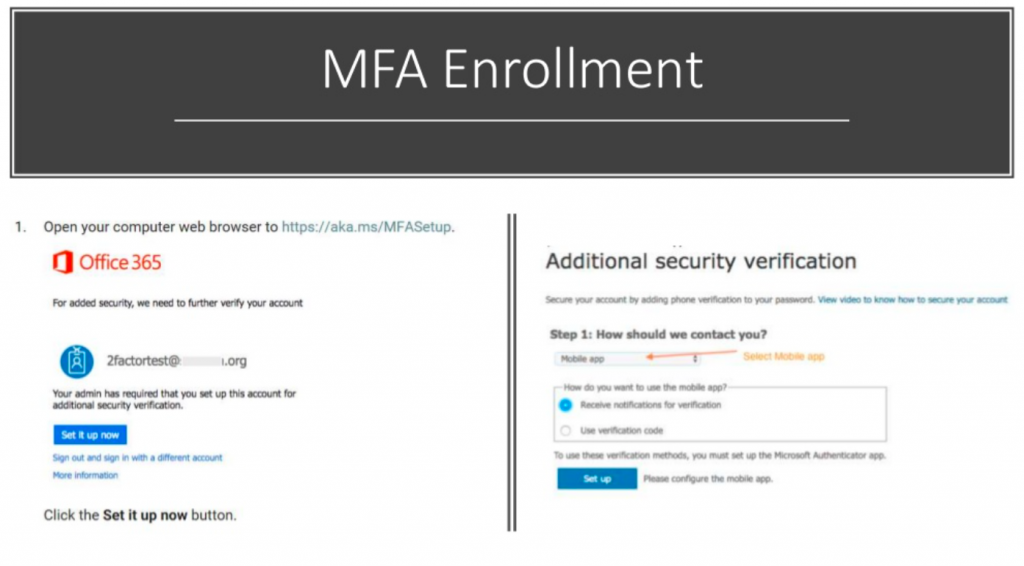
Matthew Eshleman: Mm-hmm. Yep.
So this is the end user experience once the administrator has enabled an account for Office 365 or multi factor authentication in Office 365. So there’s a prompt to open the web browser to go to HTTPS aka.MS/MFA setup. Go ahead and enroll the computer or enroll the device in multi factor authentication.
Our recommendation is that you use the mobile app. That is the most secure option. You can also choose to receive a phone call, maybe on your desk phone, for example, if you don’t have a mobile phone. You can choose to receive a text message. However, text messaging has proven to be susceptible to some other attacks. And so it’s not considered as secure as using the mobile app and Microsoft authenticator.
So once you go through the enrollment process of linking the Microsoft authenticator on your phone to your Office 365 account, then whenever you log into Office 365, you’ll go ahead and sign in. And then you’ll get a note saying, hey, we’ve sent a notification to your device, please respond to continue.
So the way I have it set up for myself is I received what’s called a push notification. My phone buzzes when I log in and says, “Hey, we’ve detected an authentication request, please verify,” and I can hit approve, or I can hit deny if I’m not in front of my computer. And if something seems strange, it’s in the middle of the night, I can hit deny, and it’ll block the request. So that’s how the end user experience is for completing the multi factor authentication.
Advanced Controls
So, we’ve talked about the fundamental controls, there’s a whole set of additional or advanced security controls that can be implemented as well. And I’d be happy to take questions about that. You can follow up outside of this format to talk about the advanced security controls.
But we are starting to see more organizations be interested in information rights management. So this is essentially like encryption or controls around files. So practically speaking, you could apply certain policies to certain sets of data. So that, for example, if it gets forwarded outside of the organization, it’s not available. If you don’t want something on the front page of Breitbart or the New York Times, you may want to put some controls on that data, as a way to put a fence around it so that only the right people have access to the information.
You can include controls around OneDrive and in terms of who and how, what IP addresses can access that information. So again, if you’re moving from an on-prem environment to the cloud, and you only want people to access files when they’re at the office on the network, you can put restrictions so that only approved IP addresses can access data, or only domain joined computers. You can sync files, so you don’t have to worry about people linking it on their home computer, and then what happens when they leave and that kind of thing.
With Intune, you can set a more robust set of policies around device access. So you could say, if you’re going to connect to our organizational data, we need to have a PIN code on your device. Your device has to be encrypted, we need to be able to wipe the data if you leave the organization. So there’s controls that you can have around devices.
And then finally, in that EMS E5 SKU, there’s the Microsoft Advanced Threat Protection and Advanced Threat Analytics, which is really a way to kind of unify all of the security logging and metrics into the Microsoft security graph, which is what they call their back end data collection AI system. So it can do event management correlation across all the endpoints.
Microsoft is uniquely positioned to be able to provide telemetry from your computer and what’s going on there, with login events on your identity and services that are connected to it.
So this would be some of the advanced security controls that could be implemented to provide greater insight and reporting. And again, I think this is a great example of kind of the power of the cloud. If you have this on-prem, your on-prem Active Directory, it’s very difficult or impossible to provide really clean reporting and management and auditing without an extreme amount of work. You can turn on and set up a lot of this stuff in a relatively short amount of time.
So let’s take a look. I think we have a couple more slides. And we can take a look at what some of the stuff looks like before we have a few minutes for questions.
Johan: Yeah, and I think one of the things we want to do is just we’ve talked a lot about safeguarding the data, but the monitoring of the data is also very important. So talk a little bit about some of the tools that can be used to monitor.
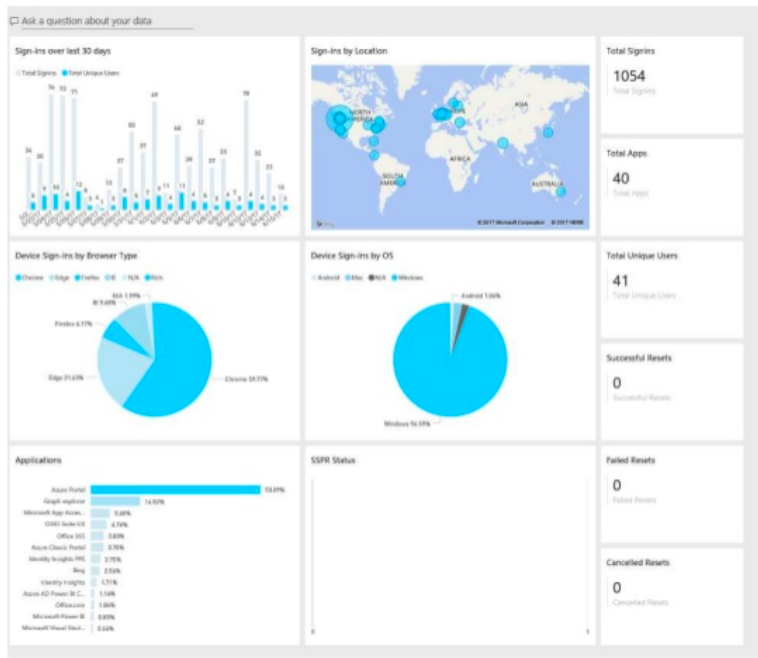
Matt: Like I mentioned earlier, once you have Azure Active Directory, that P1 setup you can configure monitoring and use Power BI so Power BI, this is a great use. So there’s a bunch of pre built content packs available. The one that’s really relevant is the Azure Active Directory logs. And so this provides insight into what’s going on with authentication requests. So in the next slide here, we have kind of the screenshot of the insight that’s provided. This is the big picture view, maybe we can zoom into some of these sections, but you get some insight into sign ins over the last 30 days, you can drill in and look to sign ins by location.
So, where are accounts logging into, device sign in by browser type, by OS type, the applications that people are using, here along the right hand side, we see the total number of sign ins, the total number of applications that are in use across the organization, how many unique users are there, who’s resetting their password, has anybody failed their password reset?
Again, so there’s a lot of insight that’s available, this is all, it’s pretty cool. You can kind of drill down into all these areas and do filtering. And it makes it a lot easier to try to figure out what’s going on as opposed to poring through an Excel spreadsheet and pivot tables and that kind of stuff.
I certainly appreciate this, it’s kind of my workflow as part of a breach response, I’m immediately turning this on, getting it connected, and using it to do incident reporting and analysis to try to figure out what accounts are accessing the system from an unusual location or a strange time frame or something like that. So, this Power BI content pack is really powerful.
And then another tool that we talked about the very beginning was the Cloud App Security. So this will contain some similar information as the Power BI content pack. But it kind of combines some of the static reporting of who’s accessing one application with some policies and kind of workflow and remediation response.
So again, if you have somebody login from a geographically distinct location, you can kind of trigger some workflow. Issue a multi factor authentication challenge or block that account or do something else. So it really provides some kind of actionable security response against information that’s available through the back end logging system.
You can classify risk levels for users, what IP addresses are people accessing? You know, which applications are folks using? Not just Office 365 apps, but also, hey, why is Dropbox being used at this organization? We’ve moved to Box or vice versa, as a way to provide some insight into the traffic and the files that are being used in the organization.
Johan Hammerstrom: All right. So we’re nearing the end of the webinar. But we do want to leave you with some links to additional resources that you can avail yourselves of, to pursue these tools to learn a little bit more about Microsoft’s approach to security as well as what they provide for nonprofit organizations. And we’ll include these with the notes as well.
So before we get to questions, and thank you all for your attention throughout this webinar, we want to highlight next month’s webinar.
It’s kind of a companion piece to this. If for whatever reason you find yourself in the unfortunate situation of having experienced a security incident, what’s the best way to respond to it? So hopefully, none of you have gone through that. And hopefully, none of you will. But in the vein of a disaster recovery plan, it’s great to have a playbook in place. So that having a security incident happened to your organization is very stressful.
And if you have a playbook, if you’ve done some preparation and planning in advance, you’re going to be in much better shape for responding to that security incident. So we’re going to talk through some of the things that you should do if you happen to experience a security incident. So that’ll be next month.
Q and A
All right. So with that, we will move on to Q&A. We have a few questions here. So thank you to everyone who submitted questions and I appreciate your patience and giving us time to respond to them.
With regards to passphrases, one of the things that you had mentioned was that the new sort of password Orthodoxy is that you use memorable passphrases that are long, somewhat unusual, rather than a complex string of characters and numbers.
And the question is: Can you use passphrases beyond Microsoft’s 16 character limit? What are some of the limitations that Microsoft places on passwords?
Matthew Eshleman: Yeah, and so I think this is a moving target and I’d actually be curious to see what they say at the conference next week about this. So currently, the restrictions, as I understand it, are there’s a minimum of eight characters, and a maximum of 16 characters. I think it may be a little bit different if you’re synching with your on-prem directory, but if you’re in Office 365, from a pure cloud perspective, that’s the limit. I’ve just started seeing, there’s some password rule previews, where you can block certain words or phrases in the password, so people couldn’t use your organization acronym, or certain things that you find people using on a regular basis.
So, that is the restriction right now, as a minimum of eight, maximum of 16. And, again, the goal here is longer is better, because we’re talking about brute force, trying random combinations. So, we want it to be easy for you to remember, hard for a computer to guess. That’s why the longer a password is, the more combinations theoretically that a computer has to try to guess it. So that’s some of the background thinking and analysis in terms of password length. And it is likely, I mean, there’s a big long feature request at Microsoft to extend that character limit.
NIST I think is saying you could do passphrases up to 64 characters or something, but that’s the Office 365 limit right now is 16.
Johan Hammerstrom: Okay, you’d mentioned DMARC and DKIM, the new DNS records for really verifying e-mail identity. If an organization has SPF records set up in their DNS, do they also need to configure DMARC and/or DKIM?
Matthew Eshleman: Yes, they do. And it’s pretty straightforward. Office 365, supports them as a service. So they will generate the records, you will then put them into your DNS host, there’s some special places to put those records that Microsoft provides. And there’s some kind of reporting or kind of action handling. So I think that also needs to be configured. So, right now, I would say, DMARC and DKIM are kind of in that same place as SPF where it’s a good idea. Adoption is improving, but we’re maybe still not at the place where you can turn it on fully to say, unless an organization has a valid DMARC and DKIM record, I’m going to reject it. We’re not quite there yet. But I think it’s going to be an important tool in the tool belt to help cut down on some of the spoofing that’s going on.
Johan Hammerstrom: Yes, Agreed. Agreed. All right. Well, thank you, Matt. I really appreciate your time and appreciate everyone who attended the webinar today. It was very informative.
As I mentioned before, we’re going to put the recording on our YouTube channel. And we’ll put the slides on our SlideShare site and the links will be on our website. And we definitely encourage everyone to join us next month for the Security Incident Response webinar. Have a great rest of your September, and then we will see you next month. Thank you, Matt.
Matthew Eshleman: Thank you. Take care.
You may also be interested in downloading our completely revised 2021 Cybersecurity Readiness for Nonprofits Playbook, or seeing the webinar walk through of this Playbook.


