The backdoor compromise of the SolarWinds Orion network management application is having a dramatic impact on the 18,000 organizations that installed the software with the malicious code in it. Already we know of at least 5 government agencies and a private company, FireEye, who have confirmed that their networks were compromised. According to Microsoft, a number of think tanks and NGOs were also impacted. Community IT Innovators is providing this SolarWinds Breach Updates for Nonprofits to start the conversation on next steps your organization may need to take as more information becomes available.
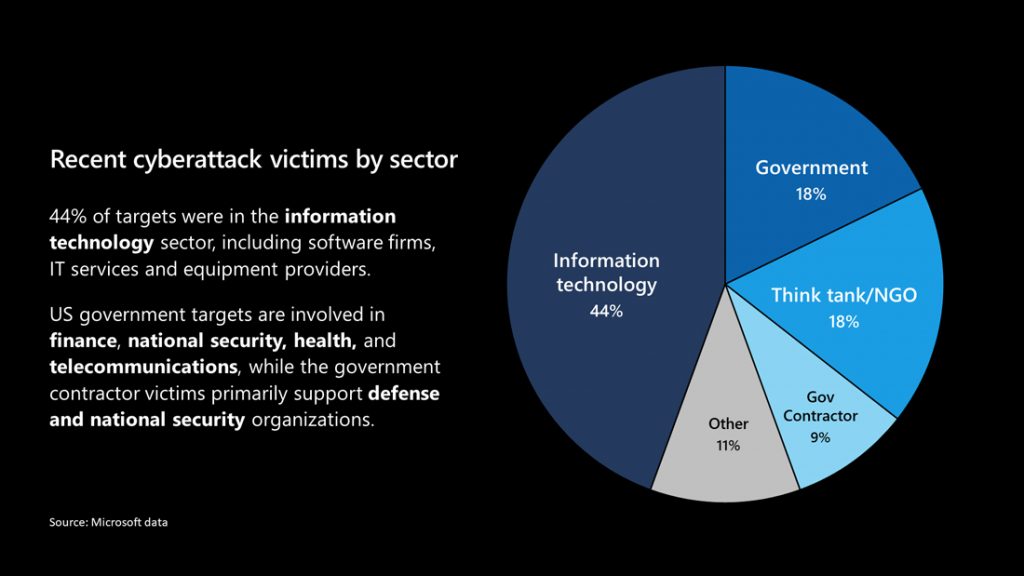
It is a sobering situation that an external threat actor gained persistent access to so many networks. Although the threat actors focused their espionage efforts on high value government and enterprise targets, it seems clear they had planned to maintain persistence in other networks for later exploits.
Unless you are a very large non-profit organization, it is unlikely that you have been directly impacted by this initial breach.
Nevertheless, there are important lessons to be learned from this incident and it is an important reminder of the importance of cybersecurity controls. If you do not have these controls in place at your own organization, we recommend implementing them as soon as possible.
Incident response plan
As this compromise shows, it’s not a question of if your organization is going to be attacked, but when. Do you know what your next steps are? Do you know what steps your IT provider (in-house or MSP) will pursue? Don’t wait to find out.
- Perform a review of your cybersecurity policies and incident response plan
- Review your plans with your leadership and with your IT support
- Review your cybersecurity training for your staff including their avenues to alert IT staff to suspicious issues
Talk to your vendors
It is nearly impossible to function as an organization without multiple vendors in many areas of tech. And your HR, database, cloud service providers, and other vendors also have a vendor supply chain. With so many systems in the cloud and supported by multiple third-party vendors, it is important to understand the protections your vendors have implemented to protect your data, and when and how they will communicate with you if you are exposed.
- The Cybersecurity Infrastructure Security Agency has a published alert from 2018 that details the threat against Managed Services Providers as a target of Advanced Persistent Threat actors.
- We only know about this attack because one of the initial organizations to identify the breach, FireEye, published their findings publicly and shared detailed information about how they were compromised.
Get cyber insurance coverage
Talk to your organization’s insurance broker to discuss what coverage you have and how to determine what coverage you need. If your provider does not offer cyber-specific insurance, look for an insurance provider who does.
- Purchasing cyber insurance will force your organization to review your risk profile. Leadership should lead this to ensure your executives have full understanding of the risks and ROI involved and can communicate that to your board and staff.
- Understand that cyber insurance is going to become more trendy as the ramifications of this breach continue to unfold. Watch out for the hard sell from brokers using fear tactics. You need cyber insurance but you might not need a platinum level policy or you might already have enough coverage.
- If you’re unsure of where to start you can enroll in this course on understanding cyberliablity insurance at TechSoup for a more thorough overview. If you haven’t explicitly purchased Cyber Liability Insurance it is unlikely that your existing General Liability Insurance will provide protection in the case of an attack.
Focus on the fundamentals
We’re seeing evidence that this is a very sophisticated attack that used a range of techniques to compromise a vendor’s trusted software. None of the controls in place at FireEye or Microsoft or the various government agencies were able to detect the initial compromise, which may have been in place since October 2019.
Nonprofit organizations often have a long way to go when it comes to securing their IT systems. That journey should focus on the basics. We detail a comprehensive list in our completely revised 2021 Cybersecurity Readiness for Nonprofits Playbook.
- Have an IT Acceptable Use Policy and Incident Response Plan in place
- Ensure that all systems are up to date with patches
- Have a backup of all data in a third-party system
- Implement multi-factor authentication on all user accounts in all systems
- Train your staff to identify suspicious emails or actions
Next Steps: SolarWinds Breach Updates for Nonprofits
We have found that non-profits have been quick to move data and processes to the cloud, but slower to implement cybersecurity controls. It is important to leverage this moment of heightened awareness to improve the protections in place at your organization.
While nonprofits were not the target of this specific breach, it is likely that some of the tools and techniques stolen in part of this attack will make their way into 2nd and 3rd tier hacking groups in the coming months. We expect to see an increase in much more widespread and damaging cyberattacks in Q1 and Q2 of 2021 as a result.
If you have questions about how to raise the level of cybersecurity protection at your organization, please reach out to us. Community IT provides a range of cybersecurity protections that are informed by our experience supporting over 140 non-profit organizations, representing over 5,000 staff.
Additional Notes
FireEye has released an initial write up of how the Orion platform has been exploited by leveraging the SolarWinds supply chain and compromising it.
Microsoft has released updated guidance on the recent cyberattacks.
Ready to reduce your nonprofit cybersecurity risk?
At Community IT Innovators, we’ve found that many nonprofit organizations deal with more cybersecurity risks than they should have to. As a result, cyber damages are all too common. Whether at a third party vendor or a phishing or ransomware attack on your own organization, you need to be prepared for cybersecurity risks and understand the SolarWinds incident nonprofits response options.
Our process is different. Our techs are nonprofit cybersecurity experts. We constantly research and evaluate new technology solutions to ensure that you get cutting-edge solutions that are tailored to keep your organization secure. We published our Nonprofit Cybersecurity: a Guide for 2020 to help our community understand the issues. And we ensure you get the highest value possible by bringing 25 years of expertise in exclusively serving nonprofits to bear in your environment.
We regularly present webinars at Community IT about cybersecurity issues, including a popular webinar on cybersecurity insurance options.
If you’re ready to gain peace of mind about your cybersecurity, let’s talk.
