2024 Nonprofit Cybersecurity Incident Report:
Emerging Trends, Practical Advice
View Video
Listen to Podcast
In pt 1 we explore a systematic approach to cybersecurity for your nonprofit, talk about the big picture trends, take a couple of audience polls on what type of incidents are common, and demystify some lingo. In pt 2 Matt goes into the report data and pulls out new and disturbing attacks, and finishes up with the best ways to protect yourself, especially from Attacker-in-the-Middle MFA attacks.
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Community IT CTO and cybersecurity expert Matt Eshleman delivers our report on trend lines and took questions live in this popular webinar.
Is your nonprofit prepared?
Drawn from anonymized data from the calendar year 2023 of cybersecurity incidents across end users in our small and mid-sized nonprofit clients, this report shows changes in attacks and emerging threats.
Using this real and timely data, Matt walks through recommendations and outlines the practical steps your organization can take to prevent the most frequent attacks.
He covers new threats and training best practices for your nonprofit staff around evolving cybersecurity issues, including AI-enabled scams, smishing, adversary-in-the-middle MFA attacks, fake in-person events phishing for credentials, and the return of popup malware, among other new and disturbing trends.
Download the webinar slides as a pdf: 2024 Nonprofit Cybersecurity Incident Report
You may also be interested in downloading the free Cybersecurity Readiness for Nonprofits Playbook to review a framework for focusing on your cybersecurity fundamentals, or using any of our free cybersecurity webinars and podcasts to learn more about specific protections you can take.
As with all our webinars, this presentation is appropriate for an audience of varied IT experience.
Community IT is proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community.
Presenters:

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 23 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at the Technology Association of Grantmakers, Jitasa, Nonprofit Learning Lab, NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert.
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response.

Carolyn Woodard is currently head of Marketing and Outreach at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She was happy to moderate this webinar and learn more from this nonprofit cybersecurity incident report with Matt Eshleman.
Transcription
Carolyn Woodard: Welcome everyone, to the Community IT Webinar, the 2024 Nonprofit Cybersecurity Incident Report with Matthew Eshleman. This is our 6th annual incident report, and a very popular webinar. Every spring, Matt studies the incidents that were reported at thousands of our client-users over the course of the year before, so in this case, 2023. He looks through and does analysis and determines the trends and changes that matter the most to nonprofit.
He’s going to cover
- best practices evolving around cybersecurity,
- AI enabled scams,
- smishing,
- adversary in the middle attacks,
- fake in-person event phishing,
- the return of pop up malware
- and a bunch of other new and disturbing trends.
My name is Carolyn Woodard. I’m the Outreach Director for Community IT. I’ll be the moderator today, and I’m very happy to hear from our cybersecurity expert, Matt.
Learning Objectives
At the end of the day, we hope that you will have learned
- our basic approach to cybersecurity,
- the trends in the attacks and the
- organization protections that we saw in 2023,
- understand evolving security best practices,
- and learn the role of governance policies and training in protecting your nonprofit from these common scams.
So, Matt, would you like to introduce yourself?
Matthew Eshleman: Great. Well, thanks for that introduction, Carolyn. And, yes, I am looking forward to the webinar today. As Carolyn mentioned, this is our 6th Annual Nonprofit Cybersecurity Incident Report, something that I created over six years ago.
I’ve been at Community IT and involved in the nonprofit tech sector for over 20 years and initiated this Nonprofit Cybersecurity Incident Report as a way to provide information that’s specific to the sector and the threats that are facing our nonprofit clients.
Carolyn Woodard: If you’re not familiar with Community IT, I wanted to tell you a little bit more about us. We are a 100% employee-owned managed services provider, and we provide outsourced IT support. We work exclusively with nonprofit organizations, and our mission is to help nonprofits accomplish their missions through the effective use of technology. So we are big fans of what well-managed IT can do for your nonprofit. And, of course, that includes cybersecurity.
We serve nonprofits across the United States. We’ve been doing this for over 20 years, and we are technology experts. We are consistently given the MSP 501 recognition for being a top MSP, and that’s an honor we received again in 2023.
I want to remind everyone that for these presentations, Community IT is vendor agnostic. We only make recommendations to our clients and only based on their specific business needs. We never try to get a client into a product because we get an incentive or benefit from that. But we do consider ourselves a best-of-breed IT provider. It’s our job to know the landscape, know what tools are available, reputable, and widely used, and we make recommendations on that basis to our clients based on their business needs, priorities, and budgets. You’ll probably hear us mention several tools today, and there are many other tools that are out there.
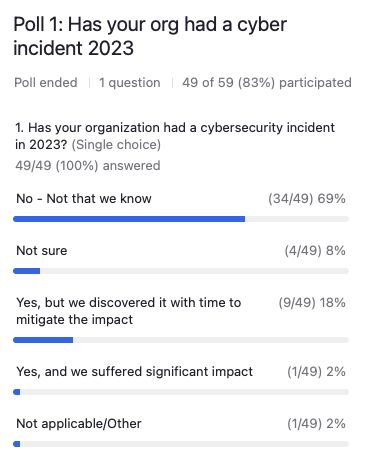
Poll 1: Has your organization had a cyber incident in 2023?
There’s a lot of stigma around having an incident, and it’s something that happens a lot.
Your options are:
- No, not that we know of.
- Not sure.
- Yes, but we discovered with time to mitigate the impact
- Yes, and we suffered significant impact from that attack
- Not applicable or other.
We’re not going to be able to see your names or that something happened at your organization. If you’re a little bit shy about putting that out there, I totally understand, but this is just a way to see how people are doing in general with being attacked. And, Matt, can you read the results?
Matthew Eshleman: Thanks to everyone for responding.
It looks like the majority of folks (69%) said no, not that we know of, with another 8% saying that they are not sure that they had an attack. The folks that said, yes, we discovered it, but with time to mitigate the impact was about 20%, and then a very small portion said, yes, we suffered significant impact. A handful of folks said, not applicable and other.
That’s good to see. Again, no organization is immune, right? Every organization would probably have some things maybe considered cybersecurity incidents, and we’ll actually talk about the definitions of what that is later on.
Community IT Approach to Cybersecurity Basics
Carolyn Woodard: We wanted to start out, Matt, with our approach to cybersecurity and lay some of the groundwork of how we think about it and how we advise our clients to think about it.
Matthew Eshleman: Yeah, a little bit more about how we think about our approach to cybersecurity at Community IT. If you’ve been attending these over the years, you may notice that we’ve got a little bit of a refresh into what this looks like.
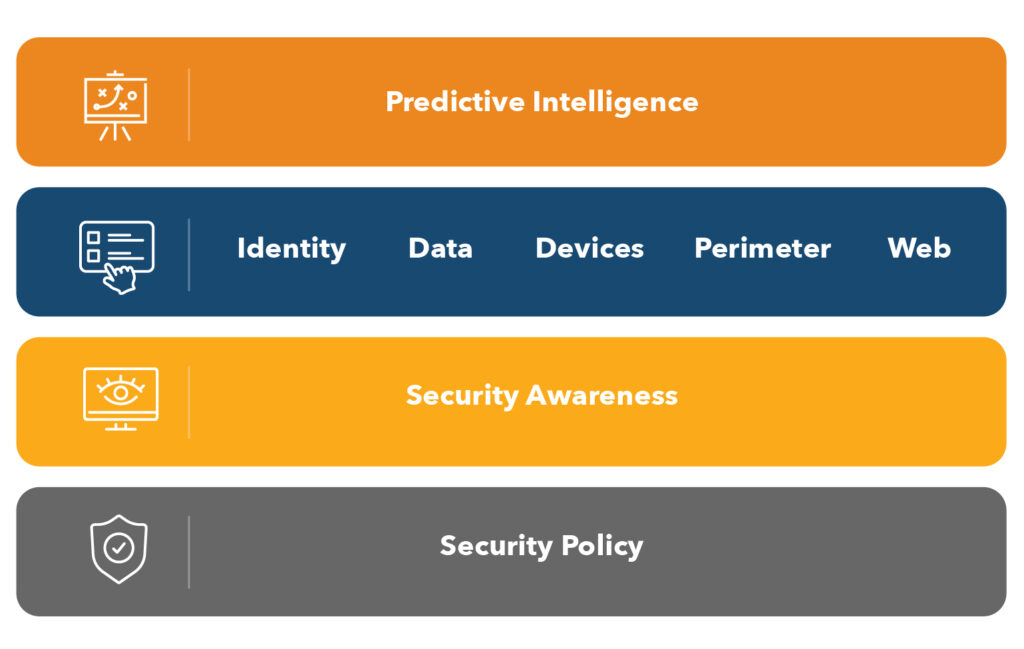
But I’ll also say that the core concepts around cybersecurity haven’t really changed much since we developed this model over six years ago.
Foundational concepts like rooting things in policy to provide guidance for technical solutions that can be built on top and adding in that layer of security awareness training so that we have staff who are educated and engaged about the very real risks that they face.
As most of the attacks that we see in this small to midsize nonprofit space that we work in, organizations that are between 15 to 50, maybe up to 200 or 300 staff, are really initiated by things as benign as clicking on a link in an email that they shouldn’t have, or being tricked into updating some payment information or buying gift cards, that kind of a thing.
So rooting the controls in policy, having an engaged and informed staff, and then we move up into the range of technical solutions that are really put in place to monitor and protect and recover when something does happen.
And then laying on top what we have called predictive intelligence, or perhaps AI driven tools. That’s certainly the buzzword now, and it’s relevant as these AI solutions are being incorporated into many of the tools that you already have or are looking at adopting.
So this model continues to provide a good framework for us as we talk about cybersecurity and building an effective cybersecurity protection plan at the organizations that we support and the organizations that are just looking for a way to figure out where to invest and what to focus on.
Carolyn Woodard: This graphic is in our Playbook for nonprofits on cybersecurity, which is a free download on our site. That download goes into more detail and action items as well as how you can manage cybersecurity at your nonprofit.
Current Cybersecurity Landscape
Before we get to the analysis this year, can you tell us a little bit about the bigger picture of what we’re seeing in cybersecurity these days?
Matthew Eshleman: Yeah, it is helpful to understand the overall cybersecurity landscape that we all operate in. Something that I like to reiterate at any opportunity I have is that cybersecurity risk really impacts every organization. Your organization is not too small or your mission is not too good to avoid or be immune from these attacks.
It’s helpful to understand that this is a cybercrime operation, and the cyber criminals really are going to work; it’s not a hobby.
There are certainly the opportunistic hackers that are kind of doing it for fun and entertainment, but for most organizations, you’re being targeted for financial gain of the people that are working. It’s a financially driven operation.
We know from the FBI, and the crime stats that the amount of revenue lost directly to financial fraud is pretty staggering. If you’re in a finance or operations role, you’ll notice that cyber liability insurance costs continue to get ratcheted up year-after-year. We are finally seeing this year that the cost increase associated with cyber liability insurance has finally started to level off a bit after having several years of 50% to 100% price increases. The actual cost of cyber liability insurance is going down. I actually had a client renew for less than they paid the previous year.
I think that’s still the exception rather than the rule, but cyber liability insurance providers are insisting on more and more serious and significant controls. But as a result, they’re also getting better results and having less payouts as a result of that.
Also, financial audits continue to expand their scope. It’s not just the financial numbers that they’re looking at, but insofar as this is a cybercrime, they’re also concerned about financial risk associated with lack of IT controls. And so we’re also seeing audits extend into the IT control world to say, hey, how are you protecting your organization? How are you making sure that we’re not going to be victims of fraud?
The other thing that is new this year is really the ubiquitous access to artificial intelligence; the election, deep fakes, all the things that can be put into place in support of that to trick people into believing something. There was an AI likeness of a CFO that was actually used as part of a digital meeting to facilitate financial fraud. These things are moving out of sci-fi and into real life.
Some of the traditional things that we have talked about in terms of how you can identify a scam email, may be poorly written. With how easy it is to go into ChatGPT and say, “Hey, write me a compelling fundraising email,” hackers are doing the same thing in order to create good copy to include in their messages. It just means we all need to be extra vigilant and continue to educate and look at additional solutions to help protect our organizations against that type of escalating fraud.
Cybersecurity Trends in 2023: Hackers
Carolyn Woodard: And I know we want to talk about some of the trends this year that we’ve seen.
Matthew Eshleman: There are a couple of new things that we identified in 2023, but there’s just massive amounts of generic and automated attacks. Adversaries are getting really good at using all the tools and automation to do this at scale. The volume and velocity of attacks continues to increase. We’ll see later in the data that spoofing and phishing attacks and even account compromise are still quite common, unfortunately.
In 2023, we saw some new technologies or new techniques being used by these hackers called Attacker-in-the-Middle or AitM, as a way to insert themselves between your computer and the destination website that you’re going to. Whether that’s Google Workspace or Microsoft 365, in order to steal not your password, but the little authentication token that is used to authenticate you as a user. That technique really contributed to a significant increase that we saw in compromised accounts, and had a pretty dramatic impact in the data that we saw.
Some other things that we saw with a lot greater frequency here in 2023 were the use of QR codes as a way to get organizations or an individual to move outside of an organization’s protected resource. The message that you get via email is pretty generic, but it has a QR code in it. If you scan the QR code with your phone, now all of a sudden instead of being on a protected work laptop, you’re on an unprotected or unmanaged phone and they’re going to ask you to log in with your credentials and that’s an opportunity for them to steal that access token. The use of QR codes as part of spear phishing messages was new.
The other thing that we saw, and this was really focused on some of our public sector clients that are doing government or government adjacent work, is the phishing schemes became really complex, including several cases where we had individuals that are clients interacting with adversaries that were inviting them to in-person meetings or conferences in D.C.
We had a case where somebody got an invite to go meet with some underlying government minister for lunch and they showed up, and there was nobody there. But they had the invite, they had the attachment with the talking points, and it’s all part of the ruse. When you boil it down, they’re trying to create an environment where you open up an attachment. That’s fundamentally what it comes down to. They incorporated a lunch meeting that was very close to the organization’s office.
We had another case where a person was invited to a small conference at a hotel, again, in the area. The person followed up because they thought it looked suspicious, and the hotel said they had no record of this meeting being on their books.
So, again, hackers are being very creative in inventing scenarios to elicit a response. It just means that we need to continue to be vigilant and exercise good judgment when figuring out, “Why am I opening up this attachment? This seems kind of unusual,” and trusting our instincts there.
Carolyn Woodard: Exactly. One of the things that we’ve been talking about is that AI makes social engineering more realistic. It’s no longer the Nigerian prince who wants you to transfer some money to their account. It can be very, very realistic. Just keeping that suspicious outlook is one of the most important things.
Cybersecurity Trends in 2023: Operations Response
Can you tell us more about these trends and what operations are trying to do to prevent it?
Matthew Eshleman: I touched on cyber liability insurance in regular audits and stronger controls. We do see that making a meaningful change for organizations. In the nonprofit space, investing in cybersecurity can seem like a daunting task. It requires additional financial investment, and if it’s not something an organization has to do they tend not to do it. So the fact that organizations are being required to make investments in their internal cybersecurity controls in order to be able to get cyber liability insurance, I view as a positive side effect, and it gives organizations a reason to invest. That’s a positive thing.
Audits are another reason why organizations are investing. They make that investment to require MFA, or that investment in additional security awareness training for staff, or pursuing endpoint detection and response technologies, or maybe even investing in a SIM, those are good steps for organizations to take.
I’d like them to do it in the absence of that external higher cyber liability insurance premiums, but I view that as a good thing, even if it’s a little bit after the fact.
As we’ve talked about AI enabling new protections, it also enables new scams and these cons. Everything is just moving so quickly. It means you need to be all that more vigilant whenever making these evaluations.
On the good side of things, AI tools to improve security are not necessarily just being extra silo solutions that you need to add on. But vendors are really moving pretty quickly to add on additional capabilities within their existing toolset. And so, be patient and those improvements are going to come to tools that you already have. It is kind of an escalating arms race in terms of new and novel uses of AI tools to create new content and create new engagement, versus the tools that are designed to combat it.
We’ve seen that training and internal culture are still absolutely critical, and that’s why it’s still a foundational piece whenever we talk about cybersecurity. You get a really great return on investment of training and educating your staff. While you can do a lot and invest in tools, at the end of the day, they are technical and they’re also fallible. Things are going to get to your staff that make it through the best multilayered defense technology tools.
Engaging with your staff, training them, providing ways for them to interact with your IT or your security team, and creating a culture of learning as opposed to a culture of punishment and shaming is really important. That is why we say cybersecurity incidents are stuff that happens to everybody. And if you can be able to reflect that and say, “Hey, I looked at this. This looked weird or I clicked on it, and then I thought maybe it shouldn’t have,” talk to your IT team or partner as soon as you can as opposed to waiting until after the fact.
Landscape trends. I love to talk about policy and governance, right? That’s all really important. We cannot just drop in a technical solution and expect to solve all of our cybersecurity issues. It really involves the organizational element and the human element as well.
And so all of those policies in handling our data, adapting and using AI tools, our incident response, what are the processes in place? Where do we put our incident response plan? All of those are important for an organization to have, because they’re going to be called on when you do have that security incident.
And so, for the 2% that said they already had a cybersecurity incident, I hope those are in place. For the 98% that said, not this past year, your time is coming. It’s good to have those things in place, so that they’re available when you do need them.
Carolyn Woodard: I’m going to jump in and give a little plug for the May webinar that we’re doing. It’s going to be all about governance and policy documents. So if you have a policy that hasn’t been updated in a while or if you don’t have a policy and/or don’t know where to start to create one, we’re going to be talking about that in-depth in about a month. I hope you’ll come back and join us for that.
Cybersecurity: Definitions/Lingo
I know also, Matt, there’s a lot of lingo around cybersecurity. So I think before we go to our next poll, we are going to talk about some of the definitions for some of the things we’re going to talk about.
Matthew Eshleman: Yes. Thank you for that. I kind of pride myself on even though I’m a techie, I think I do a pretty good job of not talking in jargon, but I think this is a good reminder just to have some definitions and make sure that we’re understanding the different concepts.

One that we hear quite a lot in the cybersecurity world is MFA or multifactor authentication. If you’re in the Google world, it is sometimes referred to as 2SV or 2-step verification. But it’s this idea that we want to protect something that we know, which is your password. You know your password, along with something that you have, which is a multifactor authentication token. Sometimes that’s an app on your phone. It could be a physical security key. But the idea that there’s two steps to verify who you are, which means it’s harder for a hacker who is based somewhere else to get both of those things.
Multifactor authentication is a key piece around securing your digital identity. Single sign on is a concept that goes along with identity. So as we are now in this cloud first world, you no longer log in to the server and then have access to all the applications. Now we have our login for our email, our login for our file system, separate login for your voice over IP system, your CMS, your CRM, your ERP, right?
What single sign on does is say, “Hey, instead of trying to manage an audit and report on the 50, 75, 100, 200 different logins that you have in order to access applications in your organization. Now we’re going to really strongly protect that in one.” So we’re going to have a really good password, a really good MFA system, and we’re going to track, monitor, and audit all of that identity so that we can grant you access to those 10, 15, 20, 50 applications that you need there.
We’ll see in the data that credentials, or identity, is really where a lot of the issues are. That’s your username and password that you use to log in to systems. Make sure that that is really well protected, because your digital identity is then used in so many other areas and can be used by the bad actors in order to ultimately commit financial crime.
We have a fun new made up word, Smishing or text-based phishing. SMS combined with phishing gives us smishing. These are the things that we’re seeing a lot. I am getting a ton of these text messages. And they range from kind of pretty obvious, like, hey, click on this link to authorize this package.
Also, we’re seeing a little bit more long-term or long play campaigns where it may first appear like just somebody mistyped a contact, like, “Oh, are you Kevin?” But then the person will begin to interact, build confidence, and then use that as a way to say, “Oh, well, I need help, or can you click on this or open this for me?” And so, again, the best answer is just to delete those messages.
Spoofing, that’s whenever we’ve got messages that are appearing to come from somebody or the obfuscation of that sender, typically showing up as your Executive Director.
We have Ransomware. And while this tends to be pretty prevalent in the news, it tends to be focused really on traditional on-premises networks. So that’s when an on-premises network will be compromised and data encrypted. And then the threat actors are holding your data for ransom. MGM had a big case, it causes tremendous impact to businesses.
In the cloud-based, cloud first network, this is much less of a risk than it is if organizations have traditional server infrastructure where the risk is much, much more significant.
Threat actor is a generic term for a hacker. All these terms are pretty much interchangeable, all leading to wire fraud,which is a federal crime. If you’re a victim of this, it’s something you can report to the FBI. And that’s basically financial crime that occurs over the Internet or electronic means.
And then we’ve got the QR code. Funny looking thing, but basically a way to generate a complex link. These things are everywhere, but also the threat actors are using them to get you to click on links.
And then finally, a malware browser pop-up. I’ll talk about this a little bit in the data as well, but this is part of a social engineering attack. It’s when something pops up and all of a sudden it’s claiming you have a virus or your computer’s under threat and it’s being encrypted and you need to call this number or not close your computer. It’s just messaging, right? But it really creates that sense of panic.
And again, the easiest thing to do is just close the tab and it’ll go away, but it can really lead to wire fraud and other cases of financial fraud.
Carolyn Woodard: I have a couple of friends whose parents have fallen for that. It really freaks you out to see that pop up, pop up. One friend’s mom called the number to get rid of this malware on her laptop. Of course, the number was the person who had put it there to begin with. And then they were, “helping her clean up her personal laptop.” I feel like I’ve seen it more recently.
Poll 2: If you ever had a cybersecurity incident that you know about at your organization, what kind did you have?
- None,
- Virus,
- Malware,
- A generic attack that wasn’t specific to your organization or you yourself.
- Ransomware, and a ransom was demanded and/or paid.
- Compromised account, so credentials were suspected or confirmed to have been hacked.
- Business email compromise, your email is used to target others. So you know that it’s been compromised.
- Advanced persistent threat, so that is precise and targeted. We sometimes see that with certain kinds of advocacy organizations or they’re working in countries where there is an advanced actor, foreign governments, state sponsored actors.
- Wire fraud. Money was sent to the hacker’s account. Somehow, they convinced you to click on something or change the bank numbers, or whatever it was.
- Other, if you feel comfortable describing it,
- and then not applicable.
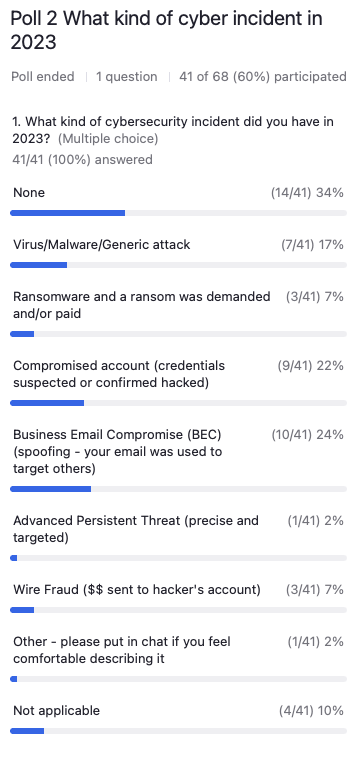
Matthew Eshleman: It looks like, again, a lot of folks saying no, with about 17% of respondents saying we had a virus or malware or some other device-based attack. A small percentage experienced ransomware and maybe even paid in cryptocurrency.
A reasonable chunk here, about a quarter of folks had compromised accounts. About a quarter of folks have experienced business email compromise and spoofing.
Again, a small percentage have experienced that advanced persistent threat, and I think that’s what we categorize as a state sponsored actor. They’re not necessarily looking for money. They’re looking for persistence and data and information about the organization, maybe the research. 7% of folks have experienced wire fraud. And again, I’m not surprised at that number.
I think from the hacker’s perspective, it’s a lot easier to scam you into sending them money than it is to deploy some sophisticated malware and get you to buy Bitcoin and then do all of that. So again, we’ve got a range of experiences, and I think we’ll see how that compares to the sample data that we have in our report here.
Carolyn Woodard: Someone did put in chat what had happened to them – that someone tested stolen credit card numbers via a Squarelink. And so they have now changed to PayPal, but were unhappy to find that Square tech support didn’t give them a lot of help when that attack was happening to them.
I’m really curious to hear about this new attacker in the middle attack. Because for years, we’ve been telling everyone in hearing, if you have MFA, you’re really protected.
Matthew Eshleman: I think we’ve covered a lot of the cybersecurity attacks.

I will say, I think phishing is more dangerous. That’s email that’s sent to the organization, and I typically am categorizing that as email that has some sort of obfuscated sender that’s hiding the identity. So it’s different from spam. Spam is just junk messages. It’s pretty easy. We don’t want this, right?
But phishing, again, is obfuscating the sender of the message. It’s including some links, something to click. It’s kind of that first step in what we’ll look at here, which could potentially be an attacker in the middle, where they’re going to be looking at stealing credentials and your MFA token as well.
We need to be aware of these as in-person and including a physical element into some of the attacks, as Carolyn shared. We’ve certainly seen that lots of these pop-ups leading to social engineering attacks are still quite common, and the rise of QR codes. It’s getting outside of the controls of your protected corporate IT environment to softer targets, maybe your home computer, your personal cell phone, that kind of thing. Text based attacks, all this building credibility to ultimately try to get some financial gain.
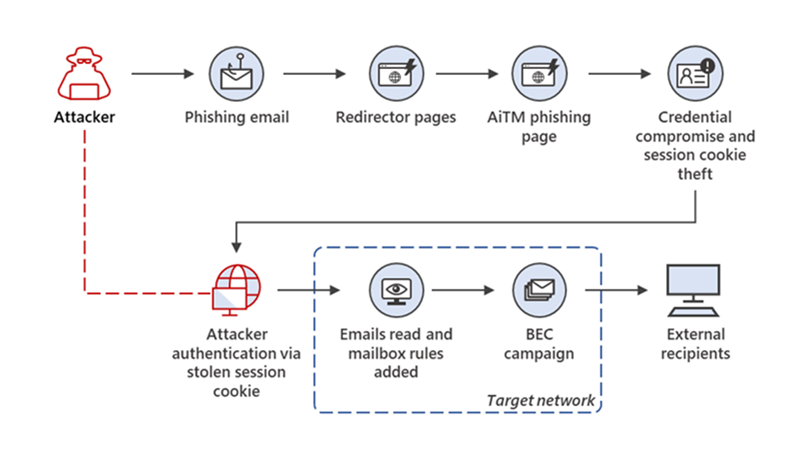
MFA enabled accounts can now be compromised by attacker in the middle attacks. I think this is the biggest significant change that we’ve seen in the past year, and it’s resolved some weaknesses in some authentication processes that exist with the authenticator app method.
With the attacker in the middle attack, it starts as a lot of attacks do: with email. In this case, we have an email message. It could come from an obfuscated sender. We’ve also seen this happen. If a partner organization has an account compromised, the adversary will then use that trusted account in order to send messages that include a link to be clicked on.
If we can help it, avoid just automatically approving and accepting messages from partner organizations because that could open up us to additional attacks if that attacker manages to compromise an account.
Microsoft has a really great overview of how this works in great technical detail. Starting off with an email from a legitimate source or perhaps an obfuscated source, but the idea is that we’re going to click on this link to open up the document that was shared with us.
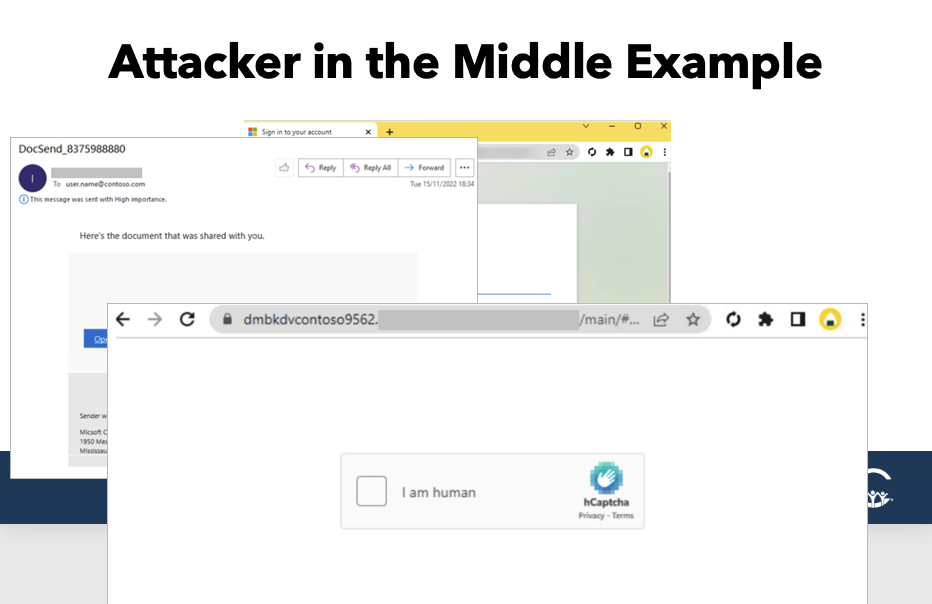
Now this is where we actually see the attack. Instead of going to the actual address, in the address bar is some variant. This is the actual proxy attack that the hacker has set up so that instead of going directly to your Office 365 login page, you’re going through a proxy. The proxy is in between your account and Office 365. What makes this so difficult to protect against is that everything that you are then going to see actually looks like your Office 365 sign in page.
If you have a customized sign in page with maybe your logo or some pictures, you would see that, but you have to be paying attention in this address bar, which is sometimes hard to do. And so, again, we have this proxy. It’s actually taking us to the real sign in page. So there’s just that brief moment where we need to acknowledge or look at the proxy as we pass through it. But from this point on, anything that the targeted user fills in is able to be stolen by the threat actor.
What we often will then see is the hacker will steal the session; they’ll log in or appear to log in as the user. They will add their own MFA method in order to be MFA compliant, and then they will lurk. Typically, at this point, they’ll work to build up into some sort of financial attack, monitor emails, and build the attack from there. But it all really starts with that malicious message, clicking on a link, taking them through a proxy where their session can be stolen.
So that’s the new thing that we’ve really seen and the impact has been significant.
If we look at the incidents that we have seen at Community IT, we have about 180 nonprofit clients. We’re supporting about 7,000 users, all over the U.S. We’ve categorized threats in a couple different areas, high risk threats, medium risk, and low.
You may be surprised by things down here: low, like viruses, malware, those pop-ups, and spam, again, can be ignored. And if we look at the relative rate, 12 viruses over 7,000 computers in a whole year. It just doesn’t happen that often.
But the things that do have a pretty significant impact when they occur are things like brute force attacks. These are attacks that are typically targeted towards on-premises network physical infrastructure. If you have any type of server with any type of access that is coming in from the Internet, that system will be attacked if there’s any misconfiguration in your firewall. That’s something that we see all the time. Whenever we’re onboarding new organizations, our system is especially tuned to look for this. It lights up all the time. That’s a cue for us to update firewalls or reconfigure things. So again, that remote desktop server tends to be targeted quite often.
Compromised accounts. We had 44 cases of compromised accounts at our clients. These were all accounts that didn’t have multifactor authentication. I think in 2023, that was not the case. We’ve done a really good job and had a big focus on enabling MFA. But because of this attacker in the middle approach and the ability to steal session tokens, those MFA controls can be subverted now and hackers are using that with pretty good success, I would say. I think that’s the big number that really jumped out at me for 2023.
Carolyn Woodard: The next slide has the increases, which I just was really stunned to see.
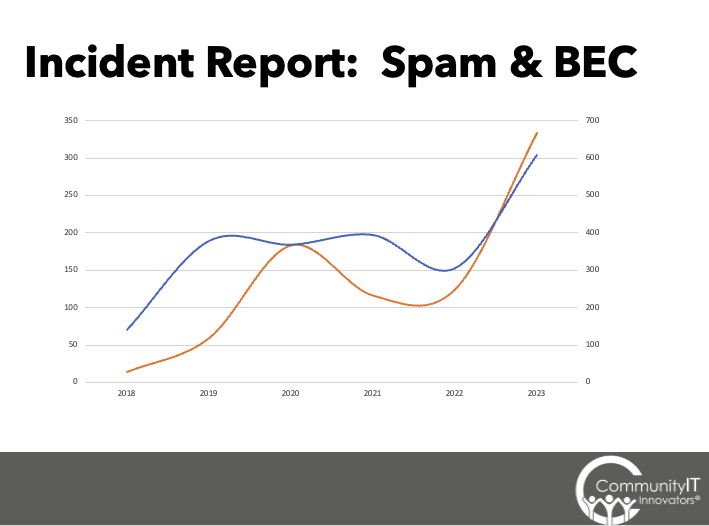
Matthew Eshleman: As we’ve been doing this for six years, I think the thing that really stuck out to me when I was looking at the data is the increase, particularly in compromised accounts. In 2022, we only had 17 compromised accounts. I guess we were feeling good, with the effects of implementing MFA widely. But now we’re up over 150% because of these new attack types being able to subvert that multi-factor authentication control.
In the same way, the brute force attacks are just an indication of how sophisticated and automated these attacks are. There’s just this massive online scanning. And as soon as there’s a vulnerability or a misconfiguration, that begins to be targeted. In previous years, it was only open RDP ports. Now it’s any open port to the Internet.
They’re finding new ways to target and launch large scale attacks to try to find and use credentials against the organization.
With the exception of some malware, in which we classify those browser pop-ups and unwanted things, they’re annoying, but not going to impact your computer and then spread to the computer next to you, like a virus would, the numbers are up overall.
Things that we would traditionally think of as really big cybersecurity issues, like viruses or ransomware, are still very, very low compared to attacks that are coming through email, and then ultimately following up and being realized as wire fraud and financial based attacks.
The other piece with a little bit more detail is the spam and the amount of spam and business email compromise or spear phishing that we can see over time. We want our staff to report things and our clients to report things whenever stuff looks strange. These are all client submitted issues. This doesn’t even include the thousands upon thousands of messages that the anti-spam systems are blocking. But at the volumes of email that we’re seeing, even if 0.1% of things were getting through, it still makes a big impact.
Again, just seeing the amount of spam and spear phishing messages that make it through and get reported highlights the scale of operations we’re dealing with and trying to fight against.
Carolyn Woodard: We’re all feeling it, right? We’re seeing more emails getting through to our inbox, and different ways to get you that are getting through, like the QR code or in-person.
How to Take Action to Protect Your Nonprofit
Matthew Eshleman: It’s not all doom and gloom. Again, I’m a big policy person.
Every organization really should make sure that they have these things in place:
- An IT acceptable use policy, that just frames the general usage of how IT is handled at your organization. Include things like, do you use MFA and a list of your information systems. Do you have any sensitive information in them? Who has access? Just a basic operating framework that forms the foundation of many other decisions. https://communityit.com/webinar-making-it-governance-work-for-your-nonprofit/
- An incident response plan. When something bad does happen, how are you going to respond? https://communityit.com/how-to-create-a-nonprofit-incident-response-plan/
- Disaster recovery that’s more of like a data loss,
- Circling back up to the new one this year, which is AI acceptable use. AI is a tremendously powerful tool that we have, but it’s also important that it’s adopted with great responsibility. As stewards of sensitive information, it’s really important to have a clear understanding amongst the staff, how we are going to use and adopt these tools. https://communityit.com/template-acceptable-use-of-ai-tools-in-the-nonprofit-workplace/
- Security awareness training continues to be a really important piece. I keep harping on it. We’ve talked about it in a number of different ways, but it’s true. Stuff is making it through even well protected networks that have lots of good anti-spam protections in place. The volume of this continues to increase. And so educating staff around how to identify these attacks. How we’d identify these spoof messages that are going through these proxies. https://communityit.com/webinar-nonprofit-it-staff-training-how-to-and-why/
https://communityit.com/webinar-security-training-for-nonprofit-grantees/
What are our policies and how do we handle financial transactions? So if you get a link or an email that says, please update my payroll, staff know the appropriate policy or procedure for updating payment information. Or if you change banks, how do you talk to HR about it? https://communityit.com/webinar-preventing-financial-fraud-at-your-nonprofit/
The final piece I would say is this: update and upgrade MFA. MFA is still important and I could only imagine what our stats would look like if we hadn’t had that big initiative on multi-factor authentication. https://communityit.com/nonprofits-should-require-multi-factor-authentication-mfa-three-reasons/
But we are now updating our best practice recommendations to include the recommendation to use physical security keys, which are as Microsoft says, phish-resistant: YubiKey or FIDO. These are keys that combine authentication that ties your login to your physical device that has this key.
That means even if you go through a proxy, the hacker cannot take that token because your authentication is now tied to the device that you are logging in from. So that’s the big recommendation. It can be a big change management exercise for organizations to go through. There is an additional cost. It’s not a free app that you can put on your phone. It might be a $20 security key depending on your organization type. There are vendors that will give donations of these physical security keys. But that really is important, I would say, especially for high risk positions.
Your IT, your executive team, your finance team, your operations, HR, those roles are really targeted. The bad guys are using their tools to figure out who’s in the HR position? Who’s in the finance department? Who are the accounts payable people? Let’s target them. And so those are the positions and roles that really should be looking at adopting physical MFA keys as part of their security protection approach, because if we can reduce risk in that area, then that helps the organization at large.
Carolyn Woodard: You can find more about what Community IT does around cybersecurity on our website; communityit.com/cybersecurity has all of our offerings there. And I did mention that there is a Playbook that you can download. We have just a ton of webinars on cybersecurity, training advice, AI. We’ve done a couple on those. So, there’s a lot of resources there that I hope you’ll look into.
Q and A
Carolyn Woodard: What should you do if you think you did click on something suspicious?
I think we’ve probably all been in that boat.
Matthew Eshleman: The first thing to do is talk to your IT provider if that’s in-house or you work with an MSP.
They should be able to look through the logs, and then see what’s going on. It’s really important and something that we do as part of our incident investigation, to establish the facts of what has happened. We may take a different approach depending on the situation, but ultimately, you may end up resetting your password, re-enrolling MFA methods, but it’s important to be really thorough. Your IT team or your MSP partner should have really good processes and procedures in place to identify if an account has been compromised and then remediate it.
It needs to be really thorough because the threat actors are finding all kinds of different ways to maintain persistence into cloud accounts. And so, just resetting your password or just enrolling in new MFA may not be enough if they’ve registered other applications or performed other actions. So talk to the IT team, and then do some logging and you’ll be able to identify what happened.
Carolyn Woodard: TELL SOMEONE. Tell someone right away. Don’t think that you can do it yourself. I actually have a friend who works in finance, and they had a wire fraud. People got fired not because they had clicked on the link and sent the money; they got fired because they had covered it up. So for about a week, they tried to fix it themselves without letting anyone know that the money had gone to the wrong account. You don’t want to be in that situation. Tell someone right away.
Is it dangerous to click on unsubscribe links? So when you get an email and it says you can unsubscribe from that mailing list, is that okay?
Matthew Eshleman: Yeah. In general, yes, it is okay, and it’s a good idea to unsubscribe from messages. For people who are running newsletters, the bar now is pretty high in terms of having good processes and good procedures to add people onto your list and giving them a way to unsubscribe. And so I think, yeah. If you’re getting emails from Macy’s and you don’t want to get emails from Macy’s anymore, yes, hitting unsubscribe is probably effective.
Now if there’s some dubious things and it looks pretty scammy, maybe you just end up blocking them.
Carolyn Woodard: If it’s like Macy’s with two y’s in the email, then you should block. But I think if it looks legit, you should be able to unsubscribe from it.
Matthew Eshleman: In general, if you can do that, that is preferred, as opposed to just blocking it yourself or forwarding to the IT team to block this. Then you get into a situation where somebody else in your organization may want to continue to get those emails from Macy’s. And if you block it, then nobody else can get it. So legit messages that are just unwanted, you should feel okay unsubscribing. Things that are of dubious origin use your judgment.
Carolyn Woodard: Matt, could you put up your link to make an appointment with you? You can also find that on our website, communityit.com/cybersecurity. It says schedule a free assessment. And that basically is a link that helps you get in touch with Matt so you can ask him your questions about your specific situation.
I want to make sure to mention our learning objectives. I feel like we covered this all pretty well.
- Basic approach to cybersecurity,
- learning the trends and attacks and organization protections,
- understanding this evolving security best practices, that MFA used to be enough, but now you need to take this extra step of having a physical key,
- learning the role of governance policies and training and protecting your nonprofit from common scams.
If you don’t have a policy, your staff aren’t going to know who they are supposed to talk to if they clicked on the wrong thing.
It’s always important to have those basic policies. If you don’t have those policies, you don’t know where to start, you want to make sure you revise them. Do you need to involve HR? Do they need to be in the employee handbook? How do you train your employees on those policies if they are new? So we’re going to be diving into all of that. We always say, you need to have policies. If you’re asking, but how? We’re going to talk about it next month. So I hope you’ll return for that.
Matt, I want to thank you so much for answering so many of our questions and just sharing your expertise and all this analysis with us today. It was just a pleasure to talk to you. It was very informative and very helpful.
Matthew Eshleman: Great. Well, thank you. I always look forward to being able to talk about this topic, because I think it’s so important. And the more education we can share about this, the better we’ll all be as a sector.