Preventing Wire Fraud at Nonprofits, Hosted by Jitasa University
Join Matt Eshleman, a cybersecurity expert, in a short presentation on preventing wire fraud at nonprofits, including the most common types of frauds and scams, what to look out for, some helpful resources, and prevention ideas.
In this video, you will learn to
- Understand the cybersecurity landscape for nonprofits
- Recognize wire fraud red flags and common hacks and scams patterns and examples
- The basic steps in cybersecurity and financial fraud prevention
This video is designed for financial professionals in nonprofits, from CFOs to accountants. Learn the warning signs and how to implement financial fraud prevention. This video is also helpful to anyone at a nonprofit who wants to protect your funding and sensitive data, and preserve your ability to focus on your mission.
View Video
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
What is Jitasa?
Jitasa is a network providing accounting services, CFO services, and nonprofit tax advice across the US. Jitasa partners with nonprofit associations and federations, to provide bookkeeping and accounting services to members of their network.
Jitasa also partners with vendors, consultants, and companies like Community IT to provide resources on financial topics and support to the nonprofit community, including a free resources area of their site.
Community IT is always looking for opportunities to provide nonprofits technical tips and insights from our 20+ years of serving this sector. Matt Eshleman was happy to sit down with Jitasa to go over cybersecurity basics for financial departments and CFOs and answer questions. Learn more on preventing wire fraud at nonprofits in the transcript below.
As with all our webinars, these presentations are appropriate for an audience of varied IT experience.
Community IT is proudly vendor-agnostic and our webinars cover a range of topics and discussions. Webinars are never a sales pitch, always a way to share our knowledge with our community.
Presenter:

As the Chief Technology Officer at Community IT, Matthew Eshleman leads the team responsible for strategic planning, research, and implementation of the technology platforms used by nonprofit organization clients to be secure and productive. With a deep background in network infrastructure, he fundamentally understands how nonprofit tech works and interoperates both in the office and in the cloud. With extensive experience serving nonprofits, Matt also understands nonprofit culture and constraints, and has a history of implementing cost-effective and secure solutions at the enterprise level.
Matt has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response. You can view Matt’s free cybersecurity videos from past webinars here.
Matt always enjoys talking about ways cybersecurity fundamentals can keep your nonprofit safer. He was thrilled to be asked to give this short presentation on preventing wire fraud at nonprofits for Jitasa.
Transcript:
Welcome to Jitasa University, where our goal is to empower nonprofits through free educational content. These short, 15 minute videos are all provided by trusted partners within our network as well, so each topic will be relevant to every organization, regardless of size. Let’s dive right in.
This month, we’re featuring Matthew Eshleman, the Chief Technology Officer at Community IT Innovators. As a 100% employee-owned and managed outsourced IT services provider, CIT exclusively assists nonprofit organizations in utilizing technology to accomplish their missions and have been doing so for over 20 years. Let’s pass things over to Matt and Carolyn, and get started with the content.
Carolyn: Thank you so much for that introduction. I wanted to go over our learning objectives for today as we learn about preventing wire fraud at nonprofits. We want to make sure that we
- understand the cybersecurity landscape for nonprofits.
- We are going to talk about wire fraud red flags and
- common hacks and scams.
- And we also want to make sure that we learn the basic steps in cybersecurity and financial fraud prevention.
Matthew Eshleman: Great. Carolyn, thank you for that introduction about what we’re going to learn today. My name is Matthew Eshleman, I’m the chief technology officer at Community IT. We’re a managed services provider that provides IT support to over 200 nonprofit organizations and about 7000 endpoints.
The information that I’m going to be talking about today is really informed by that base of clients that we’re supporting and the insights that we gain related to the cyber threats that we’re seeing across our clients, which are primarily small to mid-sized nonprofit organizations.
Preventing Wire Fraud at Nonprofits
The landscape, it really is lots and lots of automated attacks against an organization’s digital identity, also endpoints and lots of email threats in there.
Some trends that we are seeing are account compromises, that’s when a threat actor would get access to somebody’s account and not only their work accounts, but we’re also seeing personal accounts associated with individuals being targeted as well.
And then device compromises do seem to be ticking up as well. So while the primary focus of threat actors really does tend to be on an individual’s identity, device attacks are also common as well.
And the final piece, which is maybe the most common, is email based attacks. Those are messages that you get that look like they might be coming from your executive director or finance person. Those are really common and a very cheap and easy way for threat actors to try to perpetuate what is fundamentally cybercrime and it’s financially motivated.
Cybersecurity Landscape
On the operational side, some things that we are really seeing is that the cyber controls are coming from the COO or the CFO side. And those requirements are driving a lot of adoption of cybersecurity controls, particularly as cyber liability insurance premiums continue to go up, the underwriting restrictions become more stringent and the controls that they’re asking to be implemented also become more strict.
Whereas five or six years ago, insurers basically didn’t have any requirements in place, now organizations are really expected to have
- multifactor authentication,
- they’re expected to have training programs in place,
- they’re expected to have endpoint detection and response tools
- and may be even required to have PEN testing.
All of these requirements are really driven from the compliance side and from the cyber liability insurance side. The good news is that we’re seeing those fundamental controls are easier and cheaper to obtain now. And so for organizations, it’s not a huge reach to implement basic cybersecurity controls to keep them safe as an organization.
And I would say the other things operationally that we are seeing is that we’re now firmly in kind of a post COVID era. But a lot of the things that impacted our work as part of this COVID and work from home phase have really not shifted back. While some organizations are returning to office in a hybrid model, many organizations are not getting 100% compliance on that. There’s still a lot of remote work happening, a lot of flexible work policies in place.
What we’re seeing is that organizations are really a little bit late to adopt the policies and procedures in order to make sure that their policy guidance is aligning with how their work style is actually occurring.
Operational Trends: Challenges
I would say the operational trends that we’re noticing is that wire fraud or financial fraud perpetuated over an electronic method continues to increase. While things like ransomware tend to grab the headlines whenever we’re looking at the news, what we’re seeing impact small to mid-sized nonprofits, who have largely moved to the cloud, is that they are being targeted by primarily email based campaigns that are, at the end of the day, having successful wire transfers out to external parties that aren’t who they say they are.
It’s a lot easier for a threat actor to ask to wire money and for that to happen than it is for them to write some sophisticated malware, get you to install that on your computer, have it encrypt files on the network, have you go through and find some cryptocurrency and then do a transfer. And so, it’s just a lot more efficient for criminals to say, hey, can you give me money, or trick you into giving them money and have that financial transaction occur right away.
On the technical side, spear phishing or spoofing targeting personal accounts, home networks, social accounts, that’s something we’ve seen in the last year or so, that we hadn’t seen before. It’s good for organizations to understand that cybercriminals don’t respect that work and personal life boundary.
If individuals in your organization are using personal accounts as backup accounts for social media or other online tools, that can actually be a threat to the organization. While maybe your organizational account has multifactor authentication, the personal account may not. That represents a softer target for the threat actor to attack.
We also noticed that finance teams are more vulnerable to fraud whenever they’re working remotely. We don’t have that same degree of human connection or interaction. You can’t just pop into your colleague’s office and say, hey, does this look strange, or did you make this payment change request? And so some of that in-person benefit that we had in the casual conversations or checking-in things don’t extend into our virtual workplace.
It’s important particularly for the finance department to follow established processes and procedures whenever making payment changes or confirming information because it’s more difficult when we don’t have that personal connection.
AI is certainly the big buzzword and we’re able to leverage that for protections against cybercriminals. But it’s also something that cybercriminals are using to make those emails more sophisticated, more accurate. So just as a nonprofit organization might be using AI to help them jumpstart their fundraising letters to get more clicks, the bad guys are doing the same thing in order to get us to click on messages that might be malicious or trick us into giving away passwords. Some of the old clues that we may have relied on in terms of poorly worded emails being a trigger to not click on them, we have to be a lot more critical when we’re evaluating those messages now.
On the positive side though, we are seeing lots of great tools and technologies in place to help support and protect remote workers. Many of the systems or all the systems that we’re using to support those 7000 endpoints are cloud managed and cloud centric. It doesn’t matter if an end user is in their office, working from home or working from the coffee shop, we can ensure that their device is up to date, that they’re secure. If there’s any issues, we’re alerted about it. There’s lots of great tools in place to protect staff, no matter where they’re working.
And finally, I would say organizations need to continue to work at policies related to acceptable use, particularly around bring your own device (BYOD). At the beginning of COVID, it was a little bit of a free for all. Any device you had to get your work done, that was okay. But now, organizations are realizing the potential impact of when they have a staff member who’s syncing the organization’s files on their personal computer, then that person leaves the organization. And now we have a situation where all of an organization’s files are on a device that they don’t control.
Working through some policy questions reflective of the new work environment that we’re in, is a really helpful exercise for organizations to go through to make sure that they have a good accounting of all of their data, where it lives, who has access to it, and how that’s going to be handled.
Financial Cybersecurity
Whenever we talk specifically about financial cybersecurity, we ask, does your nonprofit do any of these things?
- Do you process donations?
- Do you have event registration?
- Do you store any personal information?
- Do you collect any information about your donors, newsletter, subscribers?
- Do you pay vendors online?
I think every organization does one or maybe all of these things. What I hope people realize is that every organization is a target. It doesn’t matter the type of work that you’re in. The threat actors don’t really care about you or your organization or what you do operationally. They’re primarily motivated by finances.
This is a cyber-criminal enterprise fundamentally motivated by money. We may have a stereotypical view of a hacker, in their parent’s basement, just kind of doing things to cause mayhem. But the reality is, a lot of cybercrime is driven by finances. If they can get $600 in gift cards, that’s great. If they can get $10,000 in a wire transfer, that’s great. If they can get $300,000 in a wire transfer, even better.
Understand that this crime is financially motivated and it’s not really concerned about your organization, the mission, the great work that you do. It’s helpful to provide some grounding into ensuring that all organizations are implementing good cybersecurity controls to help protect their financial assets.
Email Fraud
We have an example of some of those messages that we’ve been talking about. Most of the threats that we are actually seeing that directly relate to financial crime start out as emails. They could be as basic as what we see here, which is a common request that I’m sure many folks have seen. “Hey Tim, I want to know if you can process a wire transfer today. Let me know, so I can send you the bank details. Regards, Tom.”
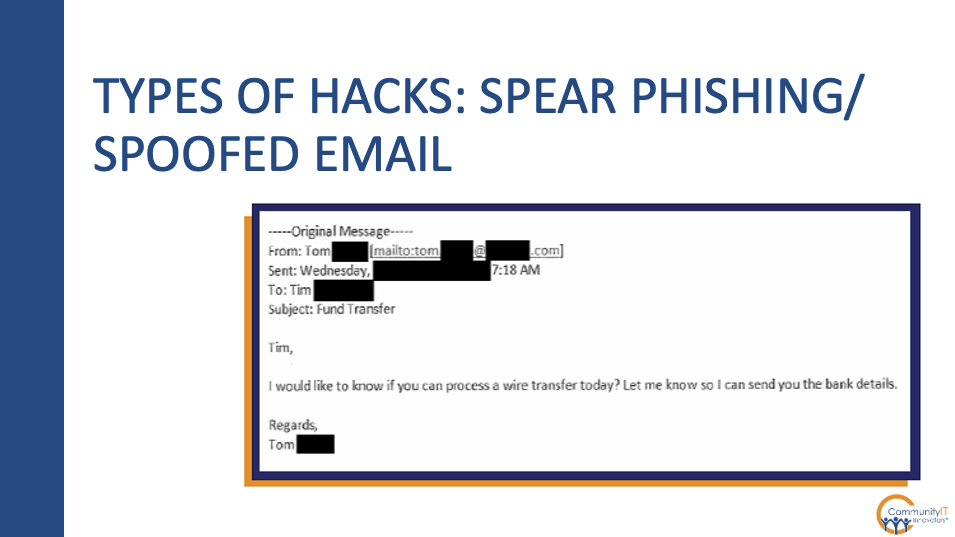
This is often targeted at people in the finance department as a way to start or initiate a conversation. There are often elements of spoofing the sender’s name. You may get an email with a display name that looks like it came from somebody in your organization. Upon further examination, looking at the reply to address may highlight that it is not indeed from your organization, but that information has been spoofed. But what we’re also seeing is that, you could be interacting with an account at a partner that may have had an account compromised.
And so while the email address itself is legitimate, the person that you’re actually communicating with is not who you think is sending the message. So again, a lot of fraud really starts off as an email and continues on from there. So that’s why you need to be very careful whenever you’re evaluating those links, taking those next steps, because the person that you’re communicating with may not be who you think it is.
Protection and Prevention
How to protect or how to prevent and detect those financial scams? I think it’s important to just start with a healthy dose of skepticism. If you’re getting a request to update payment information or buy gift cards, it’s a good time to ask, why? Is this something our organization would do? What does our organization’s policy say about making payments or buying gift cards or changing banking information? What do our pre-established policies guide us into?

The second step here is to insist on processes to verify that information changes. I would say that no payment information should be initiated solely on the basis of an email communication. There should be perhaps a phone call to the person requesting the change from a number that you’ve already established. In the case of interacting with a compromised account, what we’ve seen is that the hackers themselves will happily provide phone numbers for you to call them on, as a way to verify the transaction.
It’s important to have pre-established numbers for people that you’re interacting with, so that if there is a request to make a payment change, you have a good, known number that you can call back in order to make that payment change.
It’s also important to review and not click on the links that are in the message. If there’s banking information, that could be malicious or spoofed. If there’s ever any question, you can go to the website that you are intending to go to confirm that it’s the correct site as opposed to clicking on a link which again might be spoofed or may redirect you to a site that looks similar but isn’t actually a trusted location.
We keep going back to the topic of email, but look carefully at the email address. While it is very easy to fake the “from” name, you can change the from field to basically whatever you want, it’s very difficult to change the “reply to” address. So if you’re unsure of who a message is from, if you simply click on reply, then you’ll be able to actually see both the display name and the reply to email address and that can often give some clues as to who is actually sending the message. It may look like it’s coming from your executive director, but the reply to address could be something like a generic Gmail account. Using that as a visual cue to make sure you know who you’re replying to is an important step to ensuring the integrity of your communications.
I wanted to reinforce to always follow those internal best practices. Don’t use workarounds. As it’s often said, it’s never the crime, it’s the cover up. And so again, following established procedures and policies helps to protect you. It helps to protect your organization to make sure that all of those established processes and procedures that have been created to help the organization are still in place and still being followed. All these measures will help in preventing wire fraud at your nonprofit.
Cybersecurity Framework
At Community IT, we’ve developed an infographic as a way to help represent how we think about cybersecurity and where to make those initial investments.
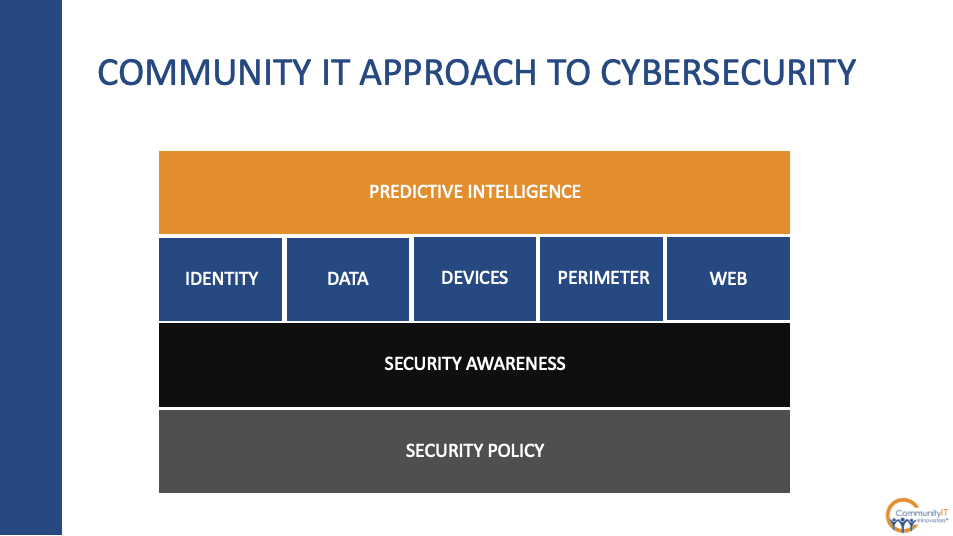
Fundamentally, we want to start with security policy. It’s a great way for the organization to really get on the same page in terms of what the organization’s expectations are around how data should be handled. How are we going to handle personal devices? What information do we have as an organization? Who needs to have access to that? All of that can help provide a foundation for making purchasing decisions or making other decisions later on.
Building on that, it’s important to invest in your people through security awareness training. I’m a tech person. I love all the whiz bang toys and all the cool AI tech, that’s all great. But fundamentally we’re dealing with people and if a person can get tricked into updating some wire transfer information that they shouldn’t, that can all be done regardless of how many technology tools are in place. Security awareness training is an effective way of educating and training your staff, so that they don’t fall prey to these schemes.
Then you can build lots of different technology tools and solutions on top of that. We typically think in areas of identity, data, the devices you have, the network perimeter and your web resources as well.
Once you’ve got all those things in place, then you may be ready for some more predictive intelligence or some AI driven tools that can provide some next level protections, but it’s important to start with the foundations and build up from there.
I also want to highlight some of the resources that are available and capabilities that are available from Community IT. As I said in the beginning, Community IT provides IT services to over 200 nonprofit organizations. We do that through a range of different services.
Community IT Cybersecurity Readiness for Nonprofits Playbook which contains this graphic, our philosophy of cybersecurity for all nonprofits, and guidance on implementing cybersecurity fundamentals.
If you’re looking for some additional help, we can provide assistance through some NIST based security surveys. We also have a variety of assessment methodologies and plans that we can work with for organizations to help understand their gaps in their protections and then provide ongoing managed services as a way to make sure that those protections are in place, so that your organization is covered from a range of the different threats that are out there.
Q and A
Jon Osterburg: Awesome Matthew, thank you so much for that really helpful content. A couple of things I thought of as questions along the way as you were presenting.
Around policies and whether or not you all recommend or if it’s even possible to include within the policies that staff members include multifactor authentication [MFA] with their personal accounts. I feel like that’d be easy to ask but hard to regulate. So how do you guys all stand on that as an option?
Matthew Eshleman: Yeah, I think you can ask for a lot in policies and as you said, it can be easy to ask but hard to regulate. But we’ve certainly seen organizations, particularly with heightened security risks, extend out training to partners of the organization. We’ve seen them extend antivirus protection to personal devices as a way of elevating cybersecurity. And then, asking for multifactor authentication by policy not only for work accounts, but also personal accounts is well within an organization’s right to do. It certainly makes a lot of sense understanding that the bad guys aren’t just observing that work personal boundary.
Jon Osterburg: Yeah, awesome. Thank you for that tidbit.
Another thing that I was thinking through was whether or not you have a recommended frequency or some locations or resources for that ongoing training, an education aspect around security awareness?
Matthew Eshleman: Yeah. At Community IT, we have a well-developed security awareness training practice and our standard practice revolves around quarterly trainings of staff.
I find it much more effective whenever staff are engaged in trainings more frequently but of a shorter duration.So our standard approach would be quarterly trainings of about 15 minutes using online resources. We’re a KnowBe4 partner and we run all our clients through that.
We combine the quarterly trainings along with monthly test phishings to gauge progress over time, identify any users that might need additional training or reinforcement and keep people on their toes. Security is not something that you can just do once a year. It’s something that really needs to be part of the organizational culture and it’s something that needs to come from executive leadership. Cybersecurity is something everybody needs to participate in. It’s not something for just the new people or just one department or the other, it’s really something that the organization needs to make a priority.
Jon Osterburg: Yeah, absolutely. And then my last question surrounds whether or not there are any recent tools that you all have found that you would recommend people take a look at. Obviously, people should come to Community IT as well because you have your own set of tools. But is there anything else out there or anywhere else out there you would direct people for some short and easy tools? Are there browser attachments within Chrome that people should download to protect themselves, or anything like that?
Matthew Eshleman: Yeah, I think a good resource, apart from Community IT’s own website, which has a lot of security resources, would be a resource called Stay Safe Online. That’s actually a federal government resource that is geared toward small and mid-sized businesses as a way to give them some foundational recommendations for cybersecurity. They have some basic training resources as well. So if an organization isn’t quite ready to take on a fully managed training program, there’s lots of free resources there that organizations can use to get started.
Jon Osterburg: Well, thank you for that. That’s all the questions that I have. Thank you, Matthew, and thank you Carolyn, so much for the time today. And we look forward to having you back again sometime.
Thanks for tuning into this session. We hope you took away some valuable information on how you can protect yourself and your organization from cyberattacks. If you had a question for Matt that didn’t get answered, feel free to email him or schedule a one-on-one meeting with him with the HubSpot link. Thanks again and we will see you next time.
Matthew Eshleman: Great, thank you.
Carolyn: Thank you.
