Transcript below.
View Video
Subscribe to our Youtube Channel here
Listen to Podcast
Like podcasts? Find our full archive here or anywhere you listen to podcasts: search Community IT Innovators Nonprofit Technology Topics on Apple, Google, Stitcher, Pandora, and more. Or ask your smart speaker.
Security Training for Nonprofit Grantees
Matt Eshleman and guest Jada Breegle from Legal Services Corporation hold a wide-ranging discussion of cybersecurity at nonprofits and how funders can work collaboratively with grantees to instill a staff culture of healthy skepticism as part of a strong cyber defense. Research shows that short, frequent and realistic trainings are more valuable than a once-a-year security video at creating an email safety culture at nonprofits. You can have all the correct security tools in place but the number one way a hack will happen is when someone on your staff clicks on the wrong link in a compromised email that looks real.
In this webinar, Matt and Jada answer attendee questions about working with funders to improve cybersecurity at nonprofits, including important security training for nonprofit grantees.
If you are a funder, you’ll learn how to work with your grantees to help them protect your financial investments in them and better ensure they are able to deliver their important nonprofit missions without the delays and financial burdens of being hacked.
If you are a grantee, we explore ways to approach your funders about cybersecurity training and support to help strengthen your staff and qualify for necessary cyber insurance.
Join us for this case study webinar from Community IT. For this cybersecurity awareness month, make a resolution to take steps to improve cybersecurity at your nonprofit.
Presenters:

Jada Breegle is the Chief Information Officer at the Legal Services Corporation (LSC), an independent nonprofit established by Congress in 1974 to provide financial support for civil legal aid to low-income Americans. In her role, Jada oversees the management of LSC’s day-to-day technology operations and leads the charge to provide technology to address LSC’s long-range objectives. Jada has more than 20 years of Federal technology experience. Before LSC, she worked at the Federal Retirement Thrift Investment Board (FRTIB), where she held a variety of leadership roles, including Executive Officer to the Chief Operating Officer and Deputy Chief Technology Officer for Infrastructure and Operations where she managed enterprise-level IT projects in excess of $50 million. Prior to the FRTIB, Jada held roles of increasing responsibility at the Defense Information Systems Agency (DISA), including roles in data center operations and strategic planning.
Jada received her B.A. from Marymount University and holds a Master of Public Administration from Bowie State University and a Master of Natural Resources from Virginia Tech University.

Chief Technology Officer at Community IT Matthew Eshleman has over 22 years of expertise in cybersecurity, IT support, team leadership, software selection and research, and client support. Matt is a frequent speaker on cybersecurity topics for nonprofits and has presented at NTEN events, the Inside NGO conference, Nonprofit Risk Management Summit and Credit Builders Alliance Symposium, LGBT MAP Finance Conference, and Tech Forward Conference. He is also the session designer and trainer for TechSoup’s Digital Security course, and our resident Cybersecurity expert
Matt holds dual degrees in Computer Science and Computer Information Systems from Eastern Mennonite University, and an MBA from the Carey School of Business at Johns Hopkins University.
He is available as a speaker on cybersecurity topics affecting nonprofits, including cyber insurance compliance, staff training, and incident response.

Carolyn Woodard (moderator) is currently head of Marketing at Community IT Innovators. She has served many roles at Community IT, from client to project manager to marketing. With over twenty years of experience in the nonprofit world, including as a nonprofit technology project manager and Director of IT at both large and small organizations, Carolyn knows the frustrations and delights of working with technology professionals, accidental techies, executives, and staff to deliver your organization’s mission and keep your IT infrastructure operating. She has a master’s degree in Nonprofit Management from Johns Hopkins University and received her undergraduate degree in English Literature from Williams College. She was happy to moderate this webinar on Security Training for Nonprofit Grantees.
Transcript
Carolyn Woodard: Welcome, everyone, to the Community IT Innovators’ Webinar on Security Training for Nonprofit Grantees. Whether you are a funder or an IT person or a grantee yourself, we’re glad that you’re here and we’re looking forward to sharing this case study about the Legal Services Corporation and their work over the past year to ensure their grantees have the training to spot phishing emails and be able to protect their organizations.
We’ve done a lot of webinars on cybersecurity and training over the years, but this is an interesting new conversation on that relationship between the funder and their investment in their grantees, and how to help protect the mission of nonprofits they fund by helping them learn to protect themselves from email scams.
Learning Objectives
Our learning objectives today are that after this session, you should be able to:
- describe the cybersecurity landscape for nonprofits,
- learn about compromised accounts and phishing risks, and
- understand what one funder did to promote email awareness training for their grantees.
I want to remind everyone at the outset that Community IT is vendor agnostic, and this presentation is to discuss how nonprofits are using common tools and what we are observing about them. We aren’t recommending any tools in general. We would only make recommendations to our clients based on specific business needs and nonprofit culture.
We encourage you to submit questions and comments through the chat feature today, and we probably won’t be able to get to everything, but you can always contact us after the webinar for follow-up.
And if you happen to be watching on YouTube right now, we encourage you to subscribe to our YouTube channel, so you’ll get all the updates every time we post a new webinar.
And we also invite you to subscribe to our email list from our website. We don’t send a lot of emails, we just send updates on the webinars that we offer every month so you can attend in real time and ask your questions at registration and during the webinar, live. If you stay to the end and take our survey, we will be awarding a $25 gift certificate to one person at random, because that survey really helps us improve our presentations.
Now, I would love to introduce Matt, one of our presenters.
Matthew Eshleman: Hi Carolyn. Thanks for the background and overview of the topic today. I’m really looking forward to this conversation. It’s a little bit of a departure from our usual webinar series, and I think this is going to be a great conversation.
As mentioned, my name is Matt Eshleman. I’m the Chief Technology Officer at Community IT. I’ve been at Community IT for a little over 20 years and in my role now, responsible for the overall technology and strategy work and cybersecurity work, working with clients and also overseeing our team where we manage about 170 different nonprofit organizations representing about 6,000 devices. So happy to be a part of this conversation today.
Carolyn, I guess you should introduce yourself as well.
Carolyn Woodard: Thanks, Matt. My name is Carolyn Woodard. I’m in charge of Outreach at Community IT. I’m going to be helping Matt today and monitoring the chat. I’m really excited to be sharing our expertise with all of you today.
I know there’s been a surge in email fraud where the email looks so legitimate, but then it turns out to be just another scam. So we’re happy to talk with you more about the tools that we use for training, how to spot those emails and what to do when you click on that link by accident. So I’m looking forward to hearing about this case study today.
But before we begin, if you’re not familiar with Community IT a little bit about us. We are a 100% employee owned managed services provider (MSP), and we provide outsourced IT support.
We work exclusively with nonprofit organizations and our mission is to help nonprofits accomplish their missions through the effective use of technology. We serve nonprofits across the United States, and we’ve been doing this for over 20 years. We’re technology experts. We are consistently given the MSP 501 recognition for being a top MSP, which is an honor we received again in 2022.
We have a lot of free resources on our website. We really feel that the more educated the nonprofit sector gets around technology, the better it is for all of us.
Since it is cybersecurity month, I want to point out that we have a lot of free resources on cybersecurity on our site.
And now it gives me great pleasure to introduce our guest speaker and practitioner, Jada Breegle from the Legal Services Corporation, Jada.
Jada Breegle: Hi, good afternoon everyone. Legal Services Corporation is the largest funder of civil legal aid for low income Americans in the nation. We were established in 1974. We operate as a nonprofit. We get an appropriation from Congress and we distribute more than $420 million annually to 132 grantees around the country. I have been the CIO at LSC for five years, and I’m thrilled that we are able to offer free cybersecurity training to our grantees and all of their staff and really look forward to the discussion today.
Agenda
Carolyn Woodard: Thanks. So we’re going to talk a little bit about the
- cybersecurity landscape for nonprofits and discuss a little bit the
- email phishing risks. What are phishing emails and how do they work for the bad guys?
- Then we’re going to do the case study with Jada in Legal Services Corporation.
- And I hope that we’re going to be able to leave a bunch of time at the end for a question-and-answer session with Matt and Jada.
Poll
But to start things out we always love to start with a poll.
What is your top cybersecurity initiative in 2023? What are you planning to do?
- security awareness training,
- multifactor authentication,
- password manager,
- endpoint detection and response,
- PEN testing,
- risk assessment,
- policy updates.
So what is your top initiative that you’re going to find the bandwidth for and make time around doing?
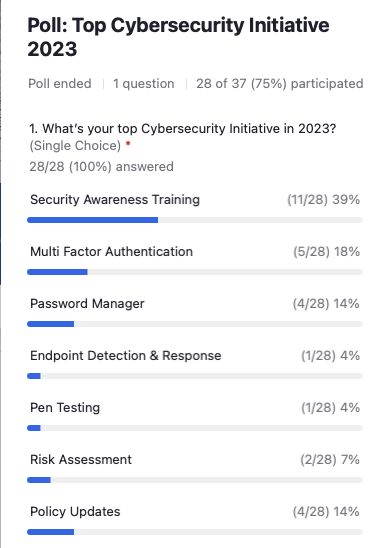
Matthew Eshleman: Thanks everybody for responding. It looks like of the options, the number one option is security awareness training. That’s fantastic. Love to see that and we’ll get into some of the reasons why; followed by multifactor authentication: 18% of respondents. About 14% of respondents say their top initiative is a password manager.
Then single digits down into implementing endpoint detection and response pen testing. And about 14% of folks saying policy updates is their top priority, which I would also say is a great place to start.
Thanks for those responses and we’ll get into a little bit about why I think security awareness training is a great place to start.
Cybersecurity Landscape
Before we begin our conversation, I think it is helpful just to set the stage talking about the cybersecurity landscape that we’re all operating in.
And that’s one where we see persistent and ongoing brute force attacks against digital identities. As many organizations have really transformed and moved resources to the cloud, I think it’s been tremendously beneficial for nonprofit organizations to be able to work remotely to have access to the latest and greatest updated tools and platforms. And so that’s been a really positive evolution of nonprofit technology. But because you can log in from anywhere in the world, it also means the bad guys can, too. And so there’s just lots and lots of scams and techniques that are designed to attack your digital identity. That’s something that we see coming into our service desk. It’s something through the monitoring tools that we have that we can just see that there’s persistent and ongoing brute force attacks against that digital identity.
We also see quite a bit of really sophisticated spear phishing. Spear phishing is different from spam, right? Spam, it’s pretty clear that it’s just junk, the sender’s not really trying to obfuscate who they are. But with spear phishing, that’s when the sender is really obfuscating who they are. They’re pretending to be somebody else. They’re disguising their identity in order to get you to take some action. Click on a link that maybe takes you to a password harvesting site, maybe open up a password protected document that launches malware. Take some additional steps to get information about you or the organization in order to further perpetrate fraud or other cybercrime.
We see that organizations are targeted because of the work that they do. I think this is particularly applicable to organizations that are government and government-adjacent. The really well funded threat actors are particularly interested in organizations like that and will have sophisticated schemes targeting organizations where there’s some transfer between the nonprofit sector and government.
And then there’s also attacks that target vendors. As a managed service provider that works with a lot of different organizations, we’re certainly a higher value target for those threat actors. Other vendors in our place need to pay additional attention to the cybersecurity controls that we have to ensure the security and the integrity of the data that we are stewards of.
It’s not all bad.
There’s lots of great new security tools that are available to help combat all of these types of threats, particularly around email protection. There’s some really great evolutions of spam filtering that can apply some sophisticated AI and machine learning to identify messages that tend to evade traditional spam filters. There’s some API driven controls that are really great at identifying and removing those messages from folks’ inbox.
I also think it’s really great that organizations are starting to be proactive about improving their cybersecurity. Organizations are starting to make that transition from, cybersecurity is kind of a necessary evil, something they have to do, to cybersecurity is a good, proactive thing that they can implement so that they can protect the data that they have.
It’s clear that nonprofit organizations still have a long way to go. A survey from NTEN shows that about 68% of nonprofits still didn’t have an incident response plan. And so for all of you that said you’re going to work on policy work, that’s great. Incident response probably should be on your list.
The other thing to be attentive to is that, this cybersecurity landscape is really grounding the fact that we’re protecting ourselves from cybercriminals, right? This is a criminal enterprise that is financially motivated and financially backed. And while the big data breaches that get a lot of press in the news are multimillion dollar impacts, the fact is that it can be a very significant impact for a small to mid-sized organization.
There’s some industry research that says the breach response for a small to mid-sized organization is around $150,000. So again, certainly not a million dollars, but $150,000 can really have a significant impact for an organization’s overall operations.
Cybersecurity Readiness
Whenever we talk about cybersecurity readiness, this familiar rubric comes up:
- people,
- process and
- technology solutions.
We talk about these in a little bit more detail in our Cybersecurity Readiness for Nonprofits Playbook, which provides a list of foundational recommendations that nonprofit organizations can follow to make sure that they’re covering all their bases.
We talk about things under the people: specific things end users can do related to choosing good passwords and turning on MFA.
We talk about technology solutions, of which there are many and I love technology and there’s lots of great solutions out there related to system updating and antivirus endpoint protection and scanning and sophisticated email tools.
But there’s a lot of process changes, and that’s what we’ll talk about today in terms of the process of developing that policy and also the process of enrolling staff in training. It’s not something that’s just a set it and forget it approach, but really something that requires some intentionality and some planning and something that really needs to come from the organization and the executive leadership at the organization, as well.
Security Awareness Training
So, specifically about training. We know security awareness training works and it’s effective. This information is from KnowBe4, which is a security awareness training vendor. It mirrors some of the results that we see where we do initial baseline campaigns. Through these security awareness training tools, we can do some test phishing messages to see who’s clicking on what because if we don’t measure it, we don’t know the performance of staff.
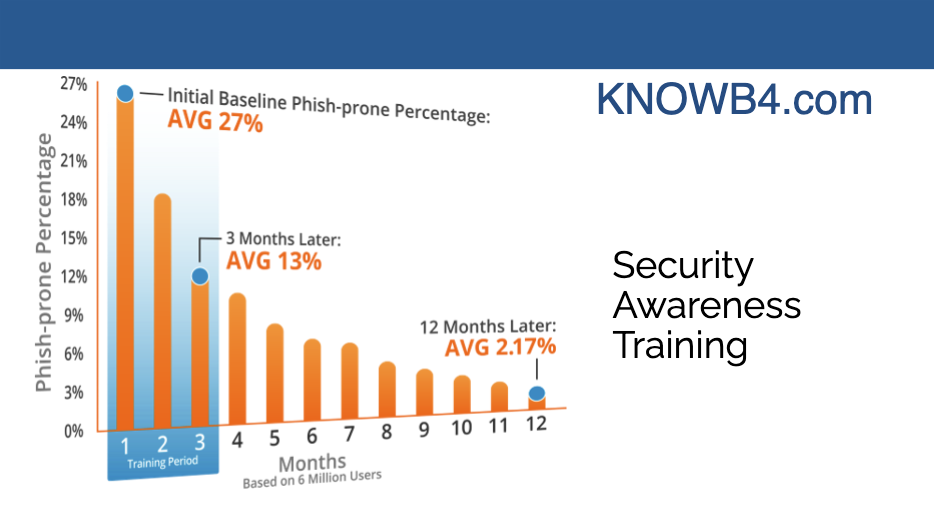
We can do some baseline phishing tests to see who might be clicking on stuff and then incorporate online training modules that users can complete on their own. And then we are doing ongoing training to gauge progress.
And this really does mirror our experience where we’ve got relatively high initial click-through rates, because it’s enticing – that shipping confirmation or the password reset email or the HR message that comes through really gets folks’ attention.
But once staff have some ongoing education, they learn some of the tricks and techniques that these threat actors are using. We really do see a pretty dramatic improvement in that click through rate. That reduces the risk quite a bit.
We go from a third of spam or phishing messages getting clicked on, down to the low single-digits. That really is a big reduction in the risk to organizations.
Case Study
As we talked about in the beginning, I’m happy to have Jada here to talk about how Legal Services Corporation made the decision to pursue providing security awareness training to their grantees.
And so I was wondering, Jada, if you could just talk a little bit more
- about Legal Services Corporation,
- the relationship that LSC has with your grantees,
- and then a little bit of why training?
You could have chosen policy, you could have chosen MFA, you could have chosen a lot of different security controls. What was it about security awareness training that made that the initiative to pursue?
And then just talk about some initial lessons learned. I know we’re not completely done with the process, but some initial lessons learned.
Jada Breegle: Very good. Sure. So let me go back to the beginning of this, which was:
Unfortunately in December of 2020, LSC had a business email compromise, and it was the typical thing. The scammer figured out who the accounting people were at one of our grantees and they figured out who the accounting people were within LSC.
They set up fake domains that looked like each of ours, and they started communicating. And their whole reason for doing that was to get us to change the banking routing information for this grantee. They were successful. An accounting tech on our side changed the routing information and they got a lot of money.
So that led us to do some really hard introspection. There were a lot of things we changed on our side, but we also realized that the security of our grantees directly impacts our security.
So while I would like to say that this is just altruistic, I just want to make everybody secure, I really want to make myself secure. It was a wakeup call.
We are a grantor. Our grantees don’t work for us. They just get money from us. They are nonprofits around the country. They have a business, which is providing civil legal aid to underprivileged folks.
So we thought long and hard about how we could influence their security. The only way we really could do that was to add a term in condition to our grants that said, we want you to do X, Y, or Z.
So honestly, we thought about a lot of stuff, and one of the things we thought about was requiring cybersecurity insurance. But then you talk a little bit about that and it’s so hard to get. I know what I go through every year, and I can’t require people to have that. There would be people that would never be able to get it.
So we thought we went back to the drawing board and we know that people are the weakest link in security. And one of the ways to educate people and to get them to stop clicking on stuff is to do cybersecurity training.
So we decided to make a term and condition of our basic field grant that our grantees have to provide cybersecurity training annually to all of their employees. And our VP of Grants Management knows that this can be expensive. She didn’t want to levy this on our grantees without paying for it. So she went to our board, she got money allocated for what we thought it would cost. It always costs a little bit more than what you’re thinking, by the way.
So we got the money allocated, and then I started with a request for proposal. I thought that the big cybersecurity training companies would come in and bid. And it was just a pipe dream. Because what I really needed was not just the training, but also someone to help set it up and to manage it and to help our grantees. Because the other thing is I don’t want access to their training. There’s some kind of line there that I don’t want to breach. So I don’t have access to their training. I needed somebody else to have that. And that’s when we found you all at Community IT.
We have potentially 13,000 plus employees at our 132 grantees. We have 9,000 users. You probably know the exact amount, Matt. We have just over 9,000 set up today.
And the feedback has been pretty positive. I think that people are happy that we’re willing to pay for this.
I’m trying to make it, and this is sort of for the other grantors out there, I don’t want it to be “big brotherish.” I don’t want to see what they’re doing. I just want to know that they’re doing it. So we have reports that come in from Community IT that just tell me that it’s done or not done. And that’s where we leave it.
We do other things to try and help improve security. We make sure at our annual tech conference that we have cybersecurity presentations. We do presentations at Equal Justice Conference and wherever we can possibly do them about the importance of all sorts of security things.
We had a conference of our executive directors last month; those are all the heads of our grantees. We had the FBI come in and talk to them about cybersecurity, which should show what importance we put on this. They had two days together and hadn’t seen each other for years, where they had to cram a whole bunch of important things in and we spent an hour on cybersecurity.
And I feel like it’s working, and a sort of amusing story. All of these Executive Directors were at this conference and they are starting to put in for their payments, for us to pay for their travel. We have a system, also because of the business email compromise, where we have to set vendors up and they started getting emails from this vendor portal. And so many of them started reporting them as phishing. It really warmed my heart that the message is out there, and people are looking at emails that closely. And that’s kind of the thumbnail sketch of the story.
Matthew Eshleman: Yeah. Well, it’s a really great story, and I think you’ve touched on a number of different themes that many, many organizations experience in terms of having a business email compromise scenario really reveal some process weaknesses and some training deficiencies in an organization.
Cybercrime, it’s a criminal enterprise. They don’t care that you’re funding legal aid. That’s not the point. It’s the fact that you’ve got financial resources and they can exploit that. I think the comment that you had about all the different things that you could do: requiring cyber liability insurance, certain security controls, then landing on security awareness training is effective.
As those organizations look for cyber liability insurance on their own, that’s certainly something we’re seeing. (Security training) is a required element of many cyber liability insurance carriers these days. And so, if those organizations are trying to find it, this does give them one more checkbox to put on the list of, yes, we’re doing that and including that as coverage.
So yeah, it checks off a lot of the boxes of why security awareness training is so effective and I think so valuable to implement.
Implementation Lessons Learned
I want to just talk a little bit about some of the lessons learned. As you mentioned, you’ve got about 13,000 grantee users all total. And we have a little over 9,000 users on the platform so far. So we’re making pretty good progress. There’s some organizations we still need to get onboarded, and there’s some organizations that already have security awareness training.
Jada Breegle: Some of our grantees have opted to use their own training, which is fine, because I just care that they’re doing it.
Matthew Eshleman: Yeah, there’s a couple of tools and obviously we picked one that we’re using for most folks. And the big lesson, especially as an implementer, is the platform that you use is important and you obviously want it to be effective, but the real investment, and this is a lesson that we’re continually learning, is really the training and the supporting processes around it.
We’ve worked with a number of organizations that maybe had it (KnowBe4) in place or they had purchased it already. And I think making that transition from just purchasing security awareness training to actually implementing it, that’s a big gap. Just because you have a product in place doesn’t mean that you’re using it effectively. And it really does require focused and expert attention to make the system work.
Some grantees already had it in place and were doing a really fantastic job with adopting the platform. But I think that’s the exception rather than the rule.
Through this process, the technical setup is very straightforward. There’s not many boxes to check, but it’s a lot of the back and forth – the training, the scheduling, the education and answering why, and how we’re doing it have been some of the lessons learned.
Jada Breegle: Some of our grantees do not have dedicated IT people. So I don’t want to put a burden on them that they need to assign someone and go out and learn how to implement this, which is why one of my lessons learned was it’s not just about buying the tool or the service. You also have to account for the implementation and the support.
Matthew Eshleman: Yeah. And I think that’s what we have up here, in terms of the challenges, right? Going and implementing a new training program at 132 different organizations, representing almost 13,000 users is a pretty big lift. I think we’ve been doing this for over six months now, and I think the success and the challenges there are balanced.
A lot of people are very excited to get this started. I think we saw from the poll earlier in the presentation, most people have security awareness training on their list of things to do. People were excited to get this done. I think they were excited to have it paid for.
But there’s lots of other competing priorities. I think IT at nonprofits is typically very resource constrained. There’s lots of competing initiatives and priorities that come down. And I know that’s something that we’ve really had to work around. Legal system migrations, file migrations, new phone systems, office moves. I mean, there’s just lots of things that IT has to tackle.
Security awareness training is not something that IT can just do in the background. They can’t install a new antivirus product that nobody really is impacted by. They’re asking their staff to take time out of their day to do this training. I think that’s been a challenge that organizations have had to navigate.
And as you mentioned, of the organizations, some are large and have in-house IT, but a lot of organizations have external IT partners, their analog to Community IT that’s providing service. And so that requires some navigation as well. Again, we want to make sure that we’re not viewed as a threat to those providers. And we’re here to support this training initiative from LSC.
I’ll say the other thing that I’ve noticed being in a lot of these conversations with organizations is the security awareness training, is a good opportunity for organizations to learn about some other technologies that end up being touched on as part of a training implementation.
For the process that we’re doing, we’ve got some automation that we’re building in with automatic group enrollment. If you’re an Azure user, you can use some built in Azure groups to automatically provision those users into the security awareness training tool and also use single sign-on. So that’s been a great tool for organizations to see how specific technologies like SCIM and single sign-on work. It’s a great tool to kind of roll out with a new tool that nobody else has really seen before.
So Jada, have there been some other lessons learned reflecting back that maybe we could have been done a little bit differently at the very beginning of this process?
Jada Breegle: I think some of our grantees probably would have wanted a little more information to start with, but I can’t think of other things. We had a couple webinars, we put together frequently asked questions. Yeah, I think we’ve hit a bunch of the challenges.
Carolyn Woodard: I have a question if you don’t mind. Was there something at the beginning that you thought was going to be a challenge that didn’t turn out to be one, or vice versa? Was there something that came out of the blue and turned out to be more difficult than you expected it to be?
Jada Breegle: I think for me, I’m always just blissfully happy that everything’s going to just work the way you expect it to. I think that it’s taken longer than I expected to get folks onboarded and ready to use the platform.
Matthew Eshleman: Yeah. I will say, I’m with you in terms of being very optimistic about how things will go. I think we had some sense, right?
We do security awareness training with a lot of our clients, and so we’ve got a pretty well defined process even coming into it and applying it to all of the grantees. But yeah, it has taken a lot longer to make those connections.
I think originally, because grantees have access to the whole KnowBe4 platform, we were really excited and showing off: “Hey, here’s all the things that you can do in here. It’s a very powerful platform. There’s lots of features and capabilities.”
But over time, we’ve really tried to focus that down to say: “Here’s just the requirements. LSC is saying, you have to do X and Y, and that’s it; we’re just going to focus on that. If down the road after all the requirements have been met, if you want to learn about Z, we can talk about it.” But trying to get that time with the grantees has been tough. I think people are very busy, especially if you have to work with third-party providers.
I think that’s the lesson that we’ve learned over time is to be very focused on what we’re doing to get that minimum viable requirement done so that we can get that completed. Then if we have other time, we can move on. But really focusing on getting as much done as we can when we have that meeting. We talked about competing priorities; there’s lots of other stuff that gets in the way. And if something’s on fire, it can be hard to get the appropriate attention. So I think that’s been a lesson learned for me as well.
Jada Breegle: My hope is that as folks start using this, they see all of the other things that they can do in there. It’s cybersecurity awareness month. Where do you think I got the information to send out my weekly annoying emails to everybody at Legal Services Corporation? I got them from KnowBe4, because they provide a whole package [including a knowledge base.] And so I’m hoping that folks, they had to get on the platform, because LSC said it was required. They needed to do something. But I’m hoping that as they look around in there, they can find all kinds of fun things.
Questions and Answers
Matthew Eshleman: Actually, one of the things that we often hear is,
How do you get executives to take this seriously?
It’s often viewed as security is something that I’m going to make other people do, but I — executives, I can’t get that done. How have you approached that, at your own organization? What is the expectation around training for your own staff?
Jada Breegle: The sad thing is when something like BEC (business email compromise) happens to you, everybody knows how important it is. When you start losing money, it’s just the forcing function. I had very good support before that, but it has even increased. In our world at LSC, we do phishing tests every month. If you fail, you get remedial training. It’s only 15 minute training, but it makes people sit up and say, Oh God.
I have a security person. And he tells them what they should have seen in that email, that they should have known it was phishing. Every year we do regular testing. You have to get it done in the month of October, or else I cut you off the network.
Matthew Eshleman: It’s amazing. It’s fantastic!
Jada Breegle: This is from my DOD days, we would totally do stuff like that. But our management is totally on board with this.
Matthew Eshleman: Yeah. I think that’s a great example because I think you set a very high but achievable bar to say, this is serious, this is important. And you do it internally and I think we have reasonable expectations for providing and expecting it to be completed by the organizations that you’re funding as well.
Carolyn Woodard: Those are great questions. We have some questions coming in from the audience as well.
Are there consequences if someone falls for a real scam?
You said, Jada, your organization had an actual business email compromise and I don’t know if he means are there consequences, do people get fired, or what are the other consequences that can happen?
Jada Breegle: I think it depends on your organization, and it depends on what happens. What happened at our organization, there was an investigation. How did this occur? Was the person negligent? That person no longer works at LSC. There were real consequences. And I don’t want everybody at LSC to be scared. I want them just to be heads-up aware. And I think they are.
I get 10 emails a day to my help desk saying, is this real? I don’t care if they send a 100. I want to see them all. We’ll tell you if they’re real. And so there are consequences, real consequences.
Matthew Eshleman: I would just add in. I know we did a webinar specifically on cyber fraud with Your Part-Time Controller. They shared a similar story where a targeted business email compromise took an organization for large sums of money.
Through the investigation there, the problem is not with the user clicking on something and being scammed into it, it’s in not reporting it. The coverup is the crime.
In cybersecurity, as Jada mentioned, the ounce of prevention is worth a pound of cure.
And so if there’s ever any question, absolutely send it, ask for help. I think that’s part of building an effective cybersecurity culture. Just feel like you can ask your IT team or ask your IT provider or ask your colleague to take a look at it.
I know from reviewing the security tickets that we respond to, we can see pretty clearly where somebody submitted a message. They said, “I didn’t click on this, but it looks weird.” And then a week or two later we get an alert that their account has been compromised. If we would’ve known that they actually clicked on the link and entered their password, then we can take appropriate actions. Not being sure is not a bad thing.
Jada Breegle: We would so much rather someone call us and say, “I just clicked on something. I don’t know what’s happening, but I think something bad is happening,” because we know what to do. We had something happen a couple weeks ago. Once we figured out what had happened, “Turn your computer off. We’re changing all of your passwords. We’re going to send FedEx, we’re going to take your computer, we’ll get you a new one tomorrow.” It was that bad.
Carolyn Woodard: That’s something I think is so good about this kind of training is, like you said Matt, it kind of sensibilizes people to report it right away instead of being embarrassed about it and thinking, “Oh, I think I can fix this myself.” No, you need to bring it to people’s attention.
We have a bunch more questions coming in.
What do you think about using YubiKey versus the single sign-on method? So that’s kind of a specific one.
Matthew Eshleman: Yeah. YubiKey would be like a physical security token that would be part of multifactor authentication (MFA).
Multifactor authentication, something that you know, which is your password, along with something that you have, for most organizations it’s probably an app on your phone, maybe you’re using text messaging.
YubiKey, or FIDO security key, is a physical device. We’re in the technical weeds here, but single sign-on just means that you can get into multiple applications with one user credential. And as much as you can protect that user identity, the better off you are.
I’ve had physical security keys for quite a while. We’re now deploying those across our organization because they increase your level of security because they are nearly impossible to spoof.
If you were following the Uber hack, the way the bad guys got in there was to just keep trying to log in and the text phone kept going off with an MFA request. The hacker knew who they were and they called them on WhatsApp and said, “Hey, respond to this. We’re trying to test something.” And they clicked okay to finish the MFA request, and then the bad guys got in. So that’s an almost impossible thing to do with physical security keys.
If you’re going through a multifactor authentication project, yeah, I would totally look at incorporating FIDO keys or security keys as part of it because you get better protection than just a mobile app.
Carolyn Woodard: Thank you, Matt.
How about international organizations that are having difficulties in IT? Is there possibility or are there training processes to be able to understand which messages to respond to or not?
So I know KnowBe4 is a specific tool that you need to sign up for and have a license to. Do you know of any, maybe free versions, or just websites that have information on email phishing scams in general?
Matthew Eshleman: There are free resources available. Stay safe online (www.staysafeonline.org), which is a U.S. government resource, provides some good foundational information that organizations can get started with.
For organizations that are looking for paid training, particularly if you’re multinational, I do think KnowBe4, and I assume other security awareness training tools, have multilingual training and test phishing messages as well. So you can provide language appropriate stuff. It’s not all U.S. English-centric. There are platforms that will support and send those messages in whatever geographic location and language you need to use.
Carolyn Woodard: Sounds good. Thank you.
Someone asks, what is the number of clicks, phishing email failures, within a particular period of time that should be allowed? Is there a rule of thumb for this type of tool or for KnowBe4 specifically?
Jada Breegle: I was wondering if we were talking about for an individual or for the organization. For an individual, it’s zero. You click, you get more training. Because, in the real world, you click, you could be taken to all kinds of bad places.
For the organization, Matt, you probably know what sort of click percentage should be your goal.
Matthew Eshleman: Yeah, at an organizational level, we had the metric on earlier. I think we see high teens as where most organizations are whenever they come into a training. Again, between 10% and 20% of messages will get clicked on.
Over time, we are typically doing monthly test phishings ongoing and that rate typically goes down to the low single-digits.
Jada Breegle: I want mine around 5% or 6%.
Matthew Eshleman: Yeah. So that’s typically where organizations get to, after 90, 120 days in a training program: low single-digit percentage.
I think our goal is to provide training and education, so folks know what to look for. Again, this is not designed to be punitive, but designed to be educational.
But, you can identify those folks that are your frequent flyers and then require some additional attention beyond just some additional online training. If you’ve got somebody who’s perennially clicking on things, and also may be in a position where they have access to finance or HR type positions, I think we’d be particularly sensitive there.
Jada Breegle: Two more things that we do – we don’t require grantees to do this, but just internally – our accounting staff gets an extra training each year, because people go after your accounting team, anybody that can release money.
And the other thing is, every so often you do get that person that clicks through. You do monthly testing like three times in a row. They’ve already gotten remedial training. Then I go to their supervisors and say, I need a little help here .I’m not sure what’s going on. If they have too much to do and they’re just rushing through things, but I need your help on mentoring and educating.
Carolyn Woodard: I think that was great, the way you put it, Matt, is that the first email, that link that you click on that goes to the wrong place. It’s not like it builds up and it gets worse over time. The first one can be the worst one.
Encouraging that community of reporting it, knowing who to turn to and who to report it to, what to do, I think is so great about some of these tools.
Will there be a move to Zero Trust? I’m not totally sure what that is. So Matt, can you explain that?
Matthew Eshleman: Zero Trust is one of those buzzy terms that gets thrown around a lot in the cybersecurity world. Essentially, Zero Trust means you’re always going to reauthenticate and verify the user is who they say they are.
In our old school, come into the office world, once you log into your computer, you’re in the office, you have access to everything in the office. Zero Trust would say there needs to be some kind of continuous evaluation process to verify that nothing has changed and you are the correct person that needs to have access to these systems or processes. Zero Trust is this framework that we’re always going to re-authenticate or re-verify the user is who they say they are.
Again, the Uber breach is a good example. They had VPN multifactor authentication that was able to be compromised. Then once the threat actor was on the local network, they were able to just get access to other systems because there wasn’t any additional verification. And they were able to find a network script that contained some embedded credentials. And there was no additional process to verify access on that system. And so the threat actor was able to get in.
Zero Trust, seems like a lot of marketing buzz. I think it’s helpful to think practically, what does that mean for your organization? How often are you going to reauthenticate people? What are the tools you’re going to give them to do that? What are the different checks that need to be in place?
Security is often about a balance. You could have a super secure system where you had a notepad in a closed room, right? Very secure, but nobody can really get to it. Can’t do much with that. So I think there’s that balance of providing authentication and making sure people can get access, and want to make security easy to use in its default configuration.
Jada Breegle: And from a nonprofit perspective, I have so many basics that I need to get better at and get in place and put money into. Zero Trust is this government wide very lofty goal that I can’t get to yet.
Carolyn Woodard: I have a little follow-on question though, because I feel like this part of the discussion touches on that tension between the convenience and the ease of using it for your staff to get their work done.
Matt, you talked at the outset about all the competing priorities, and maybe somebody’s just going really quickly and just has to answer all of these emails versus having that security in place.
Jada, maybe you could answer in your experience with this project.
How do you feel like you navigated that tension of making it easy to use, but making people have to use it?
Jada Breegle: I feel like there’s a base level of what you have to do. Cybersecurity training is a base level, and if you think about one hour a year that you’re spending reminding your users about the potential problems that are out there, and it’s not just for work, it’s for their personal life too. The stuff comes to you in your personal email too. I think it’s worth it.
You need executive buy in to say, yes, you’re going to do it. The first year I did it internally, there were people that were like, Oh, I’m really busy. I’m on all these trips.
We give you a month, you can take an hour out of your work days that month. So I think you just have to do it.
Carolyn Woodard: Thank you. Yes, I agree. There’s no silver bullet, easy pill. You have to just put the time in and realize how dangerous it is to your organization.
I want to make sure that we are mindful of people’s time. So I’m hoping Matt, if you could put up the slide with our webinar for next month, so I can just quickly tell people how exciting it is.
Next month, on November 16th, we’re having a webinar. I invite you back for Staffing IT Positions at Nonprofits. With the labor market the way it is, and with lots of nonprofits learning over the last two years what tech projects are working, and where they need work, staffing is just so difficult for nonprofit tech roles.
Our CEO, Johan Hammerstrom is going to be talking with Nura Aboki about finding those unicorns who have a tech background and understanding of nonprofit culture and budgets and who can take on a strategic role and really help your organization plan and budget for IT as a crucial part of your operations, which is a lot of what we were just talking about today.
It’s not just nice to have, it’s cybersecurity. Your IT working, being able to work in a modern office, or work remotely is all essential for your nonprofit to perform and staffing appropriately is part of that. When does it make sense to outsource that expertise and then how do you outsource it?
They’re going to be taking questions on that next month at 3:00 p.m. Eastern, noon Pacific on November 16th. So we invite you back for that.
And I just want to go quickly back over our learning objectives. I think we hit them.
You should be able to
- describe the cybersecurity landscape for nonprofits.
- Why cybersecurity awareness training is important, email training particularly, and the anti-phishing email, and
- how effective is security awareness training.
So we talked a lot about that. And we answered a bunch of Q&A from the attendees. Thank you all so, so much for joining us. We really appreciate it.
Thank you Jada, for sharing this case study with us and your experience. Thank you Matt, for answering our questions about how to do this training and how it was working in this project. And thank you again to all the attendees for joining us for this hour.
